Python code:
Problem Description A two-dimensional random walk simulates the behavior of a particle moving in a grid of points. At each step, the random walker moves north, south, east, or west with an equal probability of 1/4, regardless of previous moves. Your program shall use the turtle module to trace the steps of a random walker starting at the origin (i.e. position 0, 0). The random walker shall take as many steps till it gets to get to a world boundary. Use a step of length, = 25 and a world with dimensions 500 × 500 (i.e. 10 successive steps in one direction from the origin will get to a boundary). A program run shall implement an experiment entailing exactly 10 trials of the random walk with each trial recording the number of steps taken. Your program shall minimally define the following functions. The function descriptions are given in the attached template script: • setup(width_ratio: float=0.8, height_ratio: float=0.8, speed=0, win_title: str='2-D Random Walk') • draw_boundaries(pensize: int=1) • step() • trial() -> int • experiment() -> list • write_results(data:list)
Answers
Here is the Python code that meets the requirements mentioned in the problem description:The solution contains the following function definitions:
setup(): This function is used to set up the Turtle window.draw_boundaries(): This function is used to draw the boundaries of the world using Turtle graphics.step(): This function is used to move the turtle one step in a random direction.trial(): This function is used to perform a single trial of the random walk and return the number of steps taken.
experiment(): This function is used to perform ten trials of the random walk and return a list of the number of steps taken in each trial.
write_results(): This function is used to write the results of the experiment to a file.## Importing turtle module import turtle import random
## Global variablesSTEP_SIZE = 25WORLD_SIZE = 500## Function definitionsdef setup(width_ratio=
ORLD_SIZE) turtle.left(90) turtle.penup()def step(): """ Move the turtle one step in a random direction. """ angle = random.choice([0, 90, 180, 270]) turtle.setheading(angle) turtle.forward(STEP_SIZE)def trial(): """ Perform a single trial of the random walk and return the number of steps taken.
""" turtle.home() steps = 0 while abs(turtle.xcor()) < WORLD_SIZE/2 and abs(turtle.ycor()) < WORLD_SIZE/2: step() steps += 1 return stepsdef experiment(): """ Perform ten trials of the random walk and return a list of the number of steps taken in each trial. """ return [trial() for _ in range(10)]def write_results(data): """ Write the results of the experiment to a file. """ with open('results.txt', 'w') as f:
f.write('Results of 2-D Random Walk Experiment\n') f.write('------------------------------------\n') for i, steps in enumerate(data): f.write(f'Trial {i+1}: {steps} steps\n') f.write(f'Average: {sum(data)/len(data):.1f} steps')## Main programif __name__ == '__main__': setup() draw_boundaries() data = experiment() write_results(data)
Know more about Python code here,
https://brainly.com/question/33331724
#SPJ11
Related Questions
What is the size of 5th generation of computer and what language does they use??
Answers
Answer:
The period of fifth generation is 1980-till date. In the fifth generation, VLSI technology became ULSI (Ultra Large Scale Integration) technology, resulting in the production of microprocessor chips having ten million electronic components
Fifth-generation languages are used mainly in artificial intelligence research. OPS5 and Mercury are examples of fifth-generation languages. as is ICAD, which was built upon Lisp. KL-ONE is an example of a related idea, a frame language
Explanation:
1980 until the present is the fifth generation's time frame. When VLSI technology evolved into ULSI (Ultra Large Scale Integration) technology in the fifth generation, microprocessor chips with 10 million electronic components were created.
What is 5th generation computer?Artificial intelligence research is the principal application for fifth-generation languages. Examples of fifth-generation languages are OPS5 and Mercury. ICAD, which is based on Lisp, is also. KL-ONE is an illustration of a frame language, a related concept.
After the creation of the fourth-generation computers, the fifth generation was introduced. Modern computers, also referred to as fifth-generation computers, are currently under development and are based on artificial intelligence.
In 1982, the FGCS was developed in Japan (Fifth Generation Computer System). This generation of computers uses parallel processing and microelectronic technology, which has a high processing capacity.
Therefore, 1980 until the present is the fifth generation's time frame. When VLSI technology evolved into ULSI (Ultra Large Scale Integration) technology in the fifth generation, microprocessor chips with 10 million electronic components were created.
To learn more about computers, refer to the link:
https://brainly.com/question/21080395
#SPJ2
Although redundant links between switches is a desirable design element, what problem does this pose in layer 2 switched networks?
Answers
While redundant links in layer 2 switched networks are a desirable design element for improving network availability, they can introduce the problem of broadcast storms. By implementing protocols like STP or RSTP, network administrators can avoid these storms and maintain a stable and efficient network.
In layer 2 switched networks, redundant links between switches can lead to a problem known as "broadcast storms." When redundant links exist, it means there are multiple paths for data to travel between switches. This redundancy is typically desired as it improves network availability and fault tolerance. However, it can also create a situation where broadcast frames are continuously circulated between switches, resulting in an increased volume of network traffic.
A broadcast storm occurs when a broadcast frame is continuously forwarded by each switch in the network, causing the frame to be endlessly replicated and flooded throughout the network. This can severely degrade network performance and consume significant bandwidth, leading to slower communication and potential network congestion.
To better understand this, let's consider an example. Imagine a network with three switches connected in a loop configuration, where each switch has redundant links to the other two switches. When a device connected to one switch sends a broadcast frame, it is replicated and forwarded to the other two switches. Those switches, in turn, forward the frame back to the original switch, creating a continuous loop of broadcast frames.
To mitigate this problem, network administrators implement techniques such as Spanning Tree Protocol (STP) or Rapid Spanning Tree Protocol (RSTP). These protocols dynamically select a loop-free path in the network, effectively disabling redundant links to prevent broadcast storms. By doing so, only one active path remains, ensuring that broadcast frames do not endlessly circulate.
In conclusion, while redundant links in layer 2 switched networks are a desirable design element for improving network availability, they can introduce the problem of broadcast storms. By implementing protocols like STP or RSTP, network administrators can avoid these storms and maintain a stable and efficient network.
To know more about STP visit :
https://brainly.com/question/30031715
#SPJ11
You are designing a simple calculator program for young children to use. Right now, if they do something that the program didn’t expect, a message appears that reads, “User input deemed invalid.” What changes could you make so that the message would be more suitable for this audience?
Answers
The change you could make to make the message more suitable for this audience would be to identify a suitable message so that the children understand that they made a mistake using the program. For example: You made a mistake, try again.
What is a user input?A user input is a term that refers to the action performed by a user of a digital system or a specific program. This message has been standardized to indicate to the user that he has made a mistake in pressing buttons or in handling a program.
How to modify the message?To modify the message we must edit the base font of the program so that the message that we want to appear on the screen is different. On the other hand, we must identify a message that is simple and direct so that the children understand that they made a mistake when using the program.
What message can we put for the children?The right message for children should clearly communicate to them what has happened without discouraging them. So a suitable example of a message would be:
You've made a mistake, try again.Learn more about user input in: https://brainly.com/question/8789964
#SPJ1
Marking brainlyest look at the picture

Answers
Some one help pls will mark brainless !!!!!
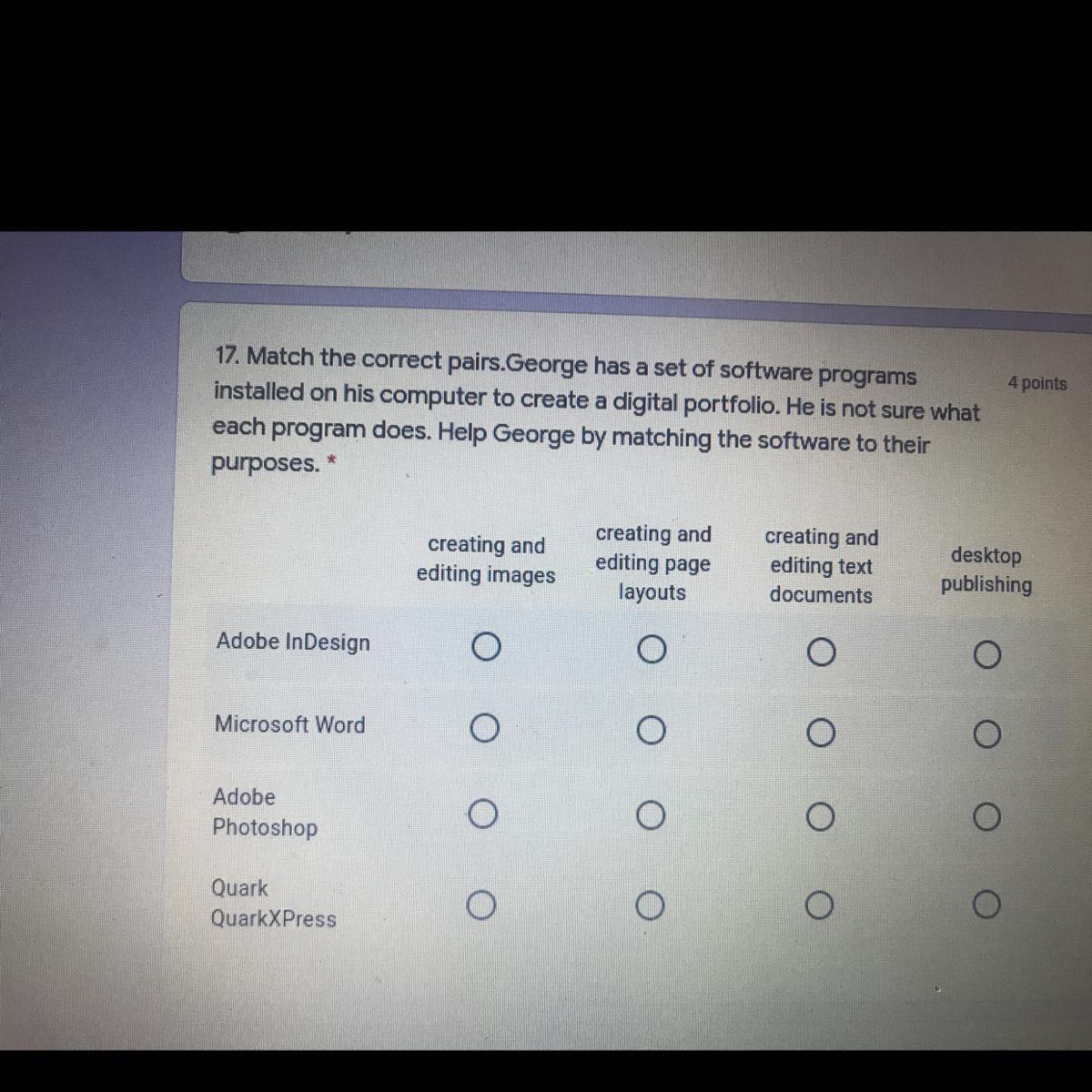
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
When Tomohiro Nishikado invented Space Invaders® in 1978, the microcomputers available in Japan could not handle its initial complexity which led Nishikado to import a CPU from the United States that was integrated into a microprocessor. This is a classic example of what?
A. innovating to overcome a technical challenge
B. the need to import items for any technology to really work
C. how the U.S. is better with technology than Japan
D. quitting when technical challenges arise
Answers
Answer:
The answer is A. Innovating to overcome a technical challenge!
hope this helps! <3
Im building my first gaming pc, got any part suggestions or tips?
Answers
Answer:
You should find a good game engine that is not hard. Unity and Unreal are some good ones.
You should also search for the programming language you like the most, and use engines that use that specific language.
Answer:
When building your own gaming pc make sure to make it uniqur since it's going to be an original. I would recommend makeing a design that makes it "you" to say. Make the design likable, not too complex. Make the color a color that is neutral, not everyone likes a neon color. I'm not very familiar with many gaming parts but, you can search up simple pc parts online and dig into gaming PCs being sold.
Explanation:
Hope this helps! UwU
Project: Math Tutor Program with Error Handling
image of a man sitting on a branch he is about to cut off
Sawing off the branch you are sitting on can only end badly (Imagery supplied by photoschmidt/iStock via Getty)
Unlike the man in the picture, you already know how to plan for and handle errors before they happen. You know how to create and use lists. You know how to use loops. You are going to put these abilities to work in this project. You are going to write a program to help young children with their arithmetic skills.
Objectives
Plan and create a program to practice math facts with error handling.
Your Goal
Your users are young children learning their arithmetic facts. The program will give them a choice of practicing adding or multiplying.
You will use two lists of numbers.
numA = [4, 1, 6, 10, 2, 3, 7, 9, 11, 12, 5, 8]
numB = [2, 12, 10, 11, 1, 3, 7, 9, 4, 8, 5, 6]
If the user chooses adding, you will ask them to add the first number from each list. Tell them if they are right or wrong. If they are wrong, tell them the correct answer.
Then ask them to add the second number in each list and so on.
If the user chooses multiplying, then do similar steps but with multiplying.
Whichever operation the user chooses, they will answer 12 questions.
Write your program and test it on a sibling, friend, or fellow student.
Errors
Think about the types of errors a user can make. Add at least one kind of error handling to your program.
What to Submit
Save your program with a .txt extension. You cannot upload a .py file.
Before you turn your project in, read the rubric.
I need this to be original work
Answers
Answer:
finished = False
numA = [4, 1, 6, 10, 2, 3, 7, 9, 11, 12, 5, 8]
numB = [2, 12, 10, 11, 1, 3, 7, 9, 4, 8, 5, 6]
while True:
pick = input("Would you like to practice addition (+) or multiplication (*)?")
if pick == "+":
for o, k in zip(numA, numB):
ans = input(f"What is {o} + {k}?")
if ans == str(o + k):
print('Correct!\n')
else:
print(f"Incorrect! The correct answer was {o + k}\n")
finished = True
elif pick == "*":
for o, k in zip(numA, numB):
ans = input(f"What is {o} * {k}?")
if ans == str(o * k):
print('Correct!\n')
else:
print(f"Incorrect! The correct answer was {o * k}\n")
finished = True
else:
print('Incorrect Input!')
if finished:
print('Thanks for playing!')
break
Explanation:
aduhhhh
which dimension of data quality is the main benefit of the primary key and foreign key relationships in tables?
Answers
The main benefit of primary key and foreign key relationships in tables is in improving the accuracy and completeness of the data. The primary key serves as a unique identifier for each record in a table, ensuring that there are no duplicates or missing values.
The main benefit of the primary key and foreign key relationships in tables is accuracy and consistency, which are two important dimensions of data quality. A primary key is a unique identifier for each record in a table, while a foreign key is a field that links two tables together by referencing the primary key of another table. By establishing these relationships, data can be accurately linked between tables, preventing duplicate records and ensuring that data remains consistent and up-to-date. For example, a foreign key in a customer orders table could reference the primary key in a customer table, ensuring that customer information is consistent across both tables. This helps to eliminate errors, inconsistencies, and inaccuracies in the data, improving the overall quality of the information stored in the database. By establishing these relationships, the accuracy and consistency of data can be maintained, which is essential for effective data management and decision-making.
To know more about Primary key Please click on the given link
https://brainly.com/question/20905152
#SPJ4
Messing around is driven by the user's:
A. need to have friends.
B. love of fighting games.
C. initiative and interests.
D. obsession with a project.
Answers
Answer:
The answer is C
Explanation:
I hope that the answer
Joe always misspells the word calendar. He types the word as calender but the correct spelling appears on the document. Which feature of the word processor corrects this word?
Answers
Answer:
Auto correct feature
Explanation:
It corrects word written wrongly automatically
The FCC began assigning TV station licenses in the
1940s
a. To raise money for the war effort
b. To avoid signal interference among stations
c. To allow nonprofit groups to have access to TV
d. To ensure that elections were covered fairly
Answers
The FCC began assigning TV station licenses in the 1940s to avoid signal interference among stations. The Federal Communications Commission (FCC) is an independent agency of the United States government that regulates interstate communications by radio, television, wire, satellite, and cable.
The FCC was created by the Communications Act of 1934, which established the framework for the regulation of electronic communications in the United States. In the 1940s, the FCC began assigning TV station licenses to regulate the use of the broadcast spectrum and prevent signal interference among stations. This helped to ensure that television broadcasts could be received clearly and without interference, which was essential for the growth and development of the television industry. By assigning licenses, the FCC also established a framework for the regulation of television broadcasting that continues to this day, including rules regarding the ownership and operation of TV stations, and requirements for public service and educational programming.
To learn more about licenses click here : brainly.com/question/19477385
#SPJ11
A camera detector has an array of 4096 by 2048 pixels and uses a colour depth of 16.
Calculate the size of an image taken by this camera; give your answer in MiB.
Answers
The size of an image taken by this camera is approximately 16 MiB.
How to calculate the size of an image?To calculate the size of the image taken by the camera, we need to know the total number of bits in the image.
The number of pixels in the image is:
4096 pixels × 2048 pixels = 8,388,608 pixels
The colour depth is 16, which means that each pixel can be represented by 16 bits. Therefore, the total number of bits in the image is:
8,388,608 pixels × 16 bits per pixel = 134,217,728 bits
To convert bits to mebibytes (MiB), we divide by 8 and then by 1,048,576:
134,217,728 bits ÷ 8 bits per byte ÷ 1,048,576 bytes per MiB = 16 MiB (rounded to two decimal places)
Learn more about cameras at:
https://brainly.com/question/26320121
#SPJ1
___________ is the number of pixels per inch
Answers
Answer:
Explanation:
What ever the number is inches is divide it by pixels
Formulas can be enter in the formula bar.
True or False?
Answers
Answer:
The Formula Bar is where data or formulas you enter into a worksheet appear for the active cell. The Formula Bar can also be used to edit data or formula in the active cell. The active cell displays the results of its formula while we see the formula itself in the Formula Bar. Expanding Or Contracting The Formula Bar
Explanation:
Hope this helps :)
the flow capacities on each street are determined by the number of available lanes, the use of traffic police and lights, and whether any lanes can be opened or closed in either direction. the flow capacities are given in thousands of cars. use the ford-fulkerson algorithm to determine the maximum traffic flow the streets can accommodate and the amount of traffic along each street. will the streets be able to handle the expected flow after a game?
Answers
Based on variables including the number of available lanes, the presence of traffic cops and lights, and lane openings and closures, the Ford-Fulkerson method is used to calculate the maximum.
traffic flow capacity of roadways. This technique may be used to determine the volume of traffic on each street as well as the maximum traffic flow that the streets can support. The maximum traffic flow that the algorithm predicts and the actual traffic volume will determine if the roadways can accommodate the anticipated flow following a game. The roadways would be able to manage the anticipated flow if the predicted traffic volume is less than the maximum traffic flow capacity of the streets. Nevertheless, if the anticipated traffic volume exceeds the permitted traffic.
learn more about traffic here:
https://brainly.com/question/17017741
#SPJ4
You have just plugged a USB hard drive into an older laptop and the disk has not appeared as available. You are concerned that the hard disk hardware has not been recognized by the computer. What utility would you use to verify??
Answers
Answer:
Device Manager and Disk Management
Explanation:
There are two main utilities that can be used to solve this problem. The main one being device manager. This utility will show you any and all devices connected to the computer. This includes USB hard drives. If it is detected and has a driver installed it will show up in Device Manager. From here you can also change the drivers, disable/enable it, etc. If the device is not listed in Device Manager then you can use the Disk Management utility to check if it is listed there. This can sometimes happen when the disk does not have a proper drive letter, which can be adjusted in Disk Management. Both of these utilities are built-in to windows operating systems.
Who runs the Web? Who controls all these protocols? Who's in charge of all this?
Answers
Answer:
...Multiple people. But the person who created the internet was Vinton Cerf.
an error occurred while loading a higher quality version of this video
Answers
Answer:?
Explanation:?
Which force is exerted on an object by a person or another object
Answers
Define the terms of data and information .
Answers
data is a collection of facts such as numbers words measurements observation or just description of thing. information is facts provided or learned about something or someone.
The students start the school year with the same number of crayons and markers in their supply boxes. They count the number of these supplies remaining at the end of the school year. Here is a bar chart showing the data the students collected. Predict the three colors of crayons and markers the class will use the most next year.

Answers
Answer:
Hello :P AAAAAAAAAAAAAAAAAAAAAAAAA
is willingness to be held accountable for your actions
Answers
Answer:
Responsibility.
Explanation:
Responsibility is the willingness to be held accountable for your actions.
A responsible person would always take measured and careful step or engage in well-thought-out actions that will add value to their lives and positively impact their immediate environment.
This ultimately implies that, responsibility is an individual characteristic which typically involves acting in a positive manner and owning up to any of your actions.
In a nutshell, responsibility requires that an individual does the right thing, the right way, at all times.
Which of these is a common problem with data transmission? a.File format b.Network Speed c.File size d.Data routing
Answers
Answer:
Answer is b
Explanation:
a. File format had nothing to do with the data transmission
c. File size matters only if the network speed is low, so, it again a fault of network speed.
d. Data routing has noting to do with data transfer, only network routing is required.
What documents are needed for real id in california.
Answers
When applying for a REAL ID, the document needed are:
A Proof of your identity (such as U.S. birth certificate, valid U.S. passport, permanent resident card, etc.An evidence of Social Security number ( such as Social Security card, W-2 form, etc.).What is an ID?An Id is known to be a tool or something that is often used in the identification of a person.
Therefore, When applying for a REAL ID, the document needed are:
A Proof of your identity (such as U.S. birth certificate, valid U.S. passport, permanent resident card, etc.An evidence of Social Security number ( such as Social Security card, W-2 form, etc.).Learn more about ID from
https://brainly.com/question/16045720
#SPJ1
50 points Describe the environmental impact of hydro and wind energy and why your choice is better than the other
Answers
The environmental impact of hydro and wind energy is that Flooding land to create a hydroelectric reservoir has a severe negative impact on the environment since it damages beautiful grounds, agricultural land, and wildlife habitat while wind leads to the loosing of top soil. Hence hydro is better.
What effects does hydropower have on the environment?Neither the air nor the water are contaminated by hydropower. However, hydropower plants have the potential to significantly alter the environment, as well as homes, land usage, and natural habitats near the dam.
As it affects a wide variety of plant and animal life, the deterioration in the quality of water that flows through hydroelectric dams and is stored in hydroelectric reservoirs is of great concern. Water pollution generally refers to the various detrimental effects that hydroelectric installations have on the environment.
Therefore, Electricity can be produced by hydropower without releasing any greenhouse gases into the atmosphere. However, it can also result in risks to the environment and society, including ruined habitat for wildlife, deteriorated water quality, impeded fish migration, and reduced recreational value of rivers.
Learn more about wind energy from
https://brainly.com/question/2031508
#SPJ1
write steps to convert data into table
Answers
Answer:
write steps to convert data into table


Microcomputer other device on the network that requests and utilizes network resources Hub Switch Client Server
Answers
Answer:
Client.
Explanation:
Cloud computing can be defined as a type of computing that requires shared computing resources such as cloud storage (data storage), servers, computer power, and software over the internet rather than local servers and hard drives.
Generally, cloud computing offers individuals and businesses a fast, effective and efficient way of providing services.
Cloud computing comprises of three (3) service models and these are;
1. Platform as a Service (PaaS).
2. Infrastructure as a Service (IaaS).
3. Software as a Service (SaaS).
A client can be defined as a microcomputer or other device on the network that requests and utilizes network resources.
These network resources that are being requested by the client (client computer) are typically made available by a dedicated computer on the network known as a server.
The list blocks that allow for storing and accessing a list of numbers and strings is called.
String manipulation
Arrays
Variable
Random
Answers
Hey so the answer to this is a variable because variables can store text and numeral values when an array can only store numbers
hope this helps
have a great day
-scav aka Toby
Answer:Array is the right option because array accessing the list of variables and integers like 1,2,4..etc variables just hold the data.
the best answer it requests services, data and other resources available on the server
Answers
Answer:
Explanation:
?