you want to update all packages in your system as well as their dependencies. which command should you use?
Answers
To update all packages in your system as well as their dependencies. You can use yum update .YUM is a graphical-based package management tool for RPM
What is the yum update command?For Linux systems using RedHat Package Manager (RPM), YUM (Yellowdog Updater Modified) is an open-source command-line and graphical package management tool.On a system, it makes it simple for users and system administrators to install, update, remove, or search software packages. Red Hat Enterprise Linux uses YUM as its main package management tool for setting up, deleting, and managing software packages.When installing, upgrading, and uninstalling software packages, YUM resolves dependencies.YUM may handle packages from either the system's installed repositories or from. yum update will update all of the installed packages if you run the command without any packages.Yum will only update the listed packages when one or more packages or package globs are given.Yum will make sure that all dependencies are met while updating packages.To learn more about yum update refer
https://brainly.com/question/13107800
#SPJ4
Related Questions
true of false. the primary problem with a perimeter-based network security strategy in which countermeasures are deployed at a handful of well-defined ingress and egress points to the network is that it relies on the assumption that everything on the internal network can be trusted.
Answers
The correct is true. problem with a perimeter-based network security strategy is that it relies on the assumption that everything on the internal network can be trusted.
What is perimeter security?The idea behind perimeter security is to secure data and resources by installing practical equipment or methods at the network's edge.
It plays a unique part in the active system protection process and is a component of a larger security field.
Firewalls and browser isolation systems are examples of systems that are used for perimeter security.
Threat identification, surveillance detection, and pattern analysis are all examples of best practises in perimeter security.
In essence, perimeter security refers to the effort made by security experts to develop a perimeter-based strategy to protect networks and secure systems.
However, many sectors of the security business now think that perimeter security is only partially effective on its own. There are now many types of internal security that can be used with high-quality security procedures.
To know more about security, visit:-
https://brainly.com/question/19051933
#SPJ4
blank uses computer resources from multiple locations to solve a common problem.
Answers
Answer:
Grid computing
Explanation:
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
Set the Append Only property to _____ to allow users to add data to a Long Text field but not to change or remove existing data.
Answers
A computer data storage is made of many features. Set the Append Only property to YES to allow users to add data to a Long Text field but not to change or remove existing data.
Append-only is known to be a characteristic or component of computer data storage. It is where new data can be appended to the storage, but where existing data is said to be immutable.A field's data type is very essential property as it shows what kind of data the field can store.
Learn more from
https://brainly.com/question/24795103
A school uses a mobile phone app to allow parents to book appointments for parents' evenings.
Parents must log in before they can use the system. They then choose to book an appointment, view all appointments already made or update their personal details. If parents choose to view their appointments, they can either view them on-screen or print them off.
Each teacher has the assessment grades for each student. These grades are stored in numerical order.
(i) The grades for one student are shown:
2, 3, 4, 5, 6, 7, 8.
Show the steps that a binary search would take to check whether the student has achieved a grade 7 in any assessment.
Your answer must refer to the grades provided.
(ii) Explain how a binary search would determine that a value does not appear in a given array.
(iii) Give one advantage of a binary search over a linear search.
Answers
(i) To check whether the student has achieved a grade 7 in any assessment using binary search, the steps would be as follows:
1. Identify the middle value in the array of grades. In this case, the middle value is 5.
2. Compare the middle value to 7. Since 7 is greater than 5, we know that any grade 7 would be to the right of the middle value.
3. Discard the left half of the array, including the middle value.
4. Identify the new middle value in the remaining array. In this case, the middle value is 7.
5. Compare the middle value to 7. Since 7 is equal to 7, we know that the student has achieved a grade 7 in at least one assessment.
(ii) A binary search determines that a value does not appear in a given array by continuing to divide the array in half and checking the middle value until the value is found or until there are no more values to check. If the middle value is not the value being searched for, the search can discard the half of the array that does not contain the value and continue searching the other half. If the search reaches the end of the array without finding the value, it knows that the value is not in the array.
(iii) One advantage of a binary search over a linear search is that a binary search can be much faster for large arrays. A linear search must examine each element of the array in order until it finds the value being searched for, which can be time-consuming for large arrays. In contrast, a binary search can quickly discard large portions of the array and hone in on the value being searched for, making it much more efficient for large arrays.
Which tool is used if a client has asked for the mountain in the left side of the photo to be on the right side instead?
Question 15 options:
bucket fill
flip
airbrush
eraser
Answers
Answer:3
Explanation:
1. Sunday Times wants an analysis of the demographic characteristics of its readers. The
Marketing department has collected reader survey records containing the age, gender, marital
status, and annual income of readers. Design an application (Flowchart) that accepts reader
data and, when data entry is complete, produces a count of readers by age groups as follows:
under 20, 20–29, 30–39, 40–49, and 50 and older. Hint: Refer to the program discussed in
class Figure 6-15
2. Create the logic (Flowchart) for a program that calculates and displays the amount of money
you would have if you invested R10000 at 4 percent simple interest for one year. Create a
separate method to do the calculation and return the result to be displayed.
The main program (Flowchart) should prompt the user for the amount of money and passes it
to the interest-calculating method.
Answers
Answer:
GIRL
Explanation:
DALAGANG FILIPINA
14 YEARS OLD
NEED FRIENDS
While loop with multiple conditions Write a while loop that multiplies userValue by 2 while all of the following conditions are true: - userValue is not 10 - userValue is less than 25
Answers
This loop multiplies the userValue by 2 as long as userValue is not 10 and is less than 25. To create a while loop that multiplies userValue by 2 while all of the following conditions are true: userValue is not 10 and userValue is less than 25.
Once the userValue becomes 10 or greater than or equal to 25, the while loop will exit and the program will continue executing the next line of code. Here's a while loop that meets the given conditions:
python
userValue = int(input("Enter a number: "))
while userValue != 10 and userValue < 25:
userValue = userValue * 2
print(userValue)
To know more about loop visit :-
https://brainly.com/question/30706582
#SPJ11
1. In a 2D ordered array, is it better to represent independent records as rows or columns and Why?
2. Describe an example of data (you can make one up) for which an associative array structure is more convenient than an ordered array structure.
Answers
The choice between representing independent records as rows or columns in a 2D ordered array depends on the specific context and requirements.
1. In a 2D ordered array, whether it is better to represent independent records as rows or columns depends on the specific requirements and usage patterns of the data. Representing independent records as rows is often more common and intuitive. Each row represents a single record, and accessing data by row allows for easy retrieval of all attributes or properties associated with that record. It aligns well with how we typically think about data in a tabular format, such as in spreadsheets or databases. Additionally, operations like appending or inserting new records are generally easier to perform on rows. However, there may be cases where representing independent records as columns is more suitable. This can be useful when the primary focus is on the attributes themselves, and accessing data by column allows for easy retrieval of specific attribute values across all records.
2. An example where an associative array structure is more convenient than an ordered array structure is when dealing with a dictionary or glossary. Let's consider a scenario where we have a dictionary of words and their definitions. Using an associative array, we can associate each word with its corresponding definition. This allows for quick and efficient lookup of a definition by directly accessing it using the word as the key. In an ordered array structure, the data would need to be sorted based on the keys (words) to enable efficient lookup, which can be time-consuming and impractical for large datasets. With an associative array, we can directly access and retrieve the definition of a word without the need for sorting or searching through the entire dataset, making it more convenient for dictionary-like applications.
In conclusion, the choice between representing independent records as rows or columns in a 2D ordered array depends on the specific context and requirements. It is important to consider factors such as data organization, ease of retrieval, and the nature of operations performed on the data to determine the most suitable representation. Similarly, the convenience of an associative array structure over an ordered array structure depends on the specific data and the type of operations required, with scenarios like dictionaries or mappings being well-suited for associative arrays.
To know more about array visit :
https://brainly.com/question/13261246
#SPJ11
When schools use spy systems to see what you're doing, is it possible for them to see what you're doing connected to ethernet and not wifi?
Answers
Yes, if you're on a school network with a border firewall that records activity, they could see what you're searching for on the Internet.
What is “reasonable suspicion”?
They can search only under certain conditions. To begin, your school must have a "reasonable suspicion" that searching you will yield evidence of a violation of a school rule or law.
Unfortunately, no precise definition exists. A reasonable suspicion, on the other hand, should be founded on facts unique to you or your situation. It can't be based on a rumor, a hunch, or a whim.
A teacher, for example, cannot request a search for drugs based solely on the appearance of the bag.
Can my school conduct a random search of its students?
YES. These random searches, however, must be based on special, school-wide needs, such as ensuring school safety, and must be truly random. A random search cannot be used to target specific students.
To know more about ethernet, visit: https://brainly.com/question/26956118
#SPJ1
YOOO CAN ANYONE SOLVE THIS IN JAVA??
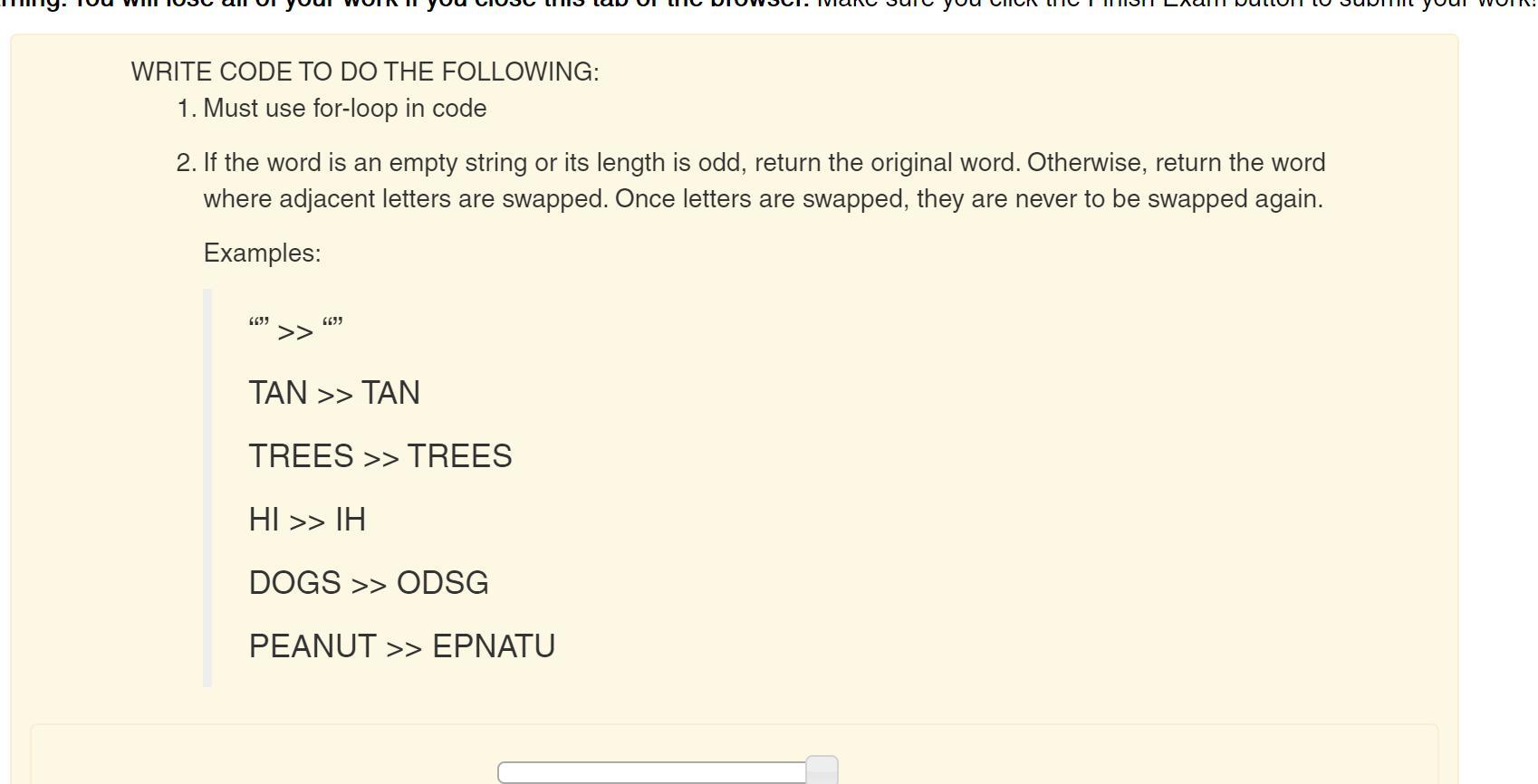
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
I'm skeptical about (b) , is this accurate or the ranges should be listed differently ?

Answers
Answer:
My guess would be C2-C11, But I may be wrong
Imagine a graph
Hope this helps....
____ are characterized as records or rundowns of individual's instruction, proficient experience, capabilities, and aptitudes utilized as a component of an employment form. Select one: O a. LINKEDIN b. c. RESUME O d. PROFILE API
Answers
The term that is characterized as records or rundowns of an individual's instruction, proficient experience, capabilities, and aptitudes utilized as a component of an employment form is c. RESUME.
A resume is a concise summary of an individual's education, work experience, credentials, and skills. It is a crucial document utilized by employers to evaluate job candidates. A resume should include information such as job history, educational background, and professional accomplishments. It should be tailored to the job for which the candidate is applying.
For writing a resume,
Pick the Right Resume Format & Layout.
Mention Your Personal Details & Contact Information.
Use a Resume Summary or Objective.
List Your Work Experience & Achievements.
Mention Your Top Soft & Hard Skills.
Include Additional Resume Sections (Languages, Hobbies, etc.)
Learn more about resume: https://brainly.com/question/862477
#SPJ11
state the difference between token and identifier
(computer)
Answers
i) What are Chronic Micro Traumas, and other physical injuries that gamers have faced?
ii) What are the mental/cognitive/emotional challenges that are mentioned in the article?
iii) Imagine a close friend of yours shares with you that they are facing the physical/cognitive/emotional challenges related to gaming/over usage of technology, what would you recommend for them to improve all forms of their health?
Answers
Some common physical injuries that gamers may face include:
Carpal Tunnel SyndromeEye StrainBack and Neck PainRepetitive Strain Injuries (RSIs)ii) The mental/cognitive/emotional challenges are:
Addiction:Social IsolationPoor Sleep PatternsAttention and Concentration Issues What are the mental/cognitive/emotional challengesChronic micro traumas are caused by excessive gaming/tech use, leading to repetitive stress injuries. Gamers may face physical injuries like Carpal Tunnel Syndrome, which causes pain, numbness, and tingling in the hand and arm due to repetitive wrist.
Common challenges related to gaming or excessive technology use include addiction, which interferes with daily life. Excessive screen time may cause social isolation. Late-night gaming or excessive screen time before bed can disrupt sleep, causing insomnia or poor sleep quality.
Learn more about emotional challenges from
https://brainly.com/question/26162044
#SPJ1
the dash area is used for typing and editing the text
Answers
Explanation:
document area is used for typing and editing the text
Identify and label the parts fo the audio mixer (use the provided list as a guide).
____________. Audio Input Knob Potentiometers
____________. Audio Input Slider Potentiometers
____________. Audio Mixer
____________. Main Output Control
____________. Sub-master Controls
____________. VU Meter

Answers
Input jacks. Audio Input Knob Potentiometers. Microphone preamplifiers. Audio Input Slider Potentiometers.
What is audio mixer?Audio mixer is defined as a device that accepts, combines, processes, and monitors audio as its primary function. Mixers are used for live sound reinforcement, streaming, and broadcast. They allow you to "mix" many sound sources together.
Equalization. Audio Mixer. Dynamics processing. Main Output Control. Routing, Sub-master Controls. Level-control faders. VU Meter are the parts of audio mixer.
Thus, the parts of audio mixer are as given.
To learn more about audio mixer, refer to the link below:
https://brainly.com/question/14299038
#SPJ1
1.
Why do you need to use sources of information when writing a formal business
document?
Answers
Answer:
You need sources of information when writing a formal business document because, if the person receiving the document would like to see the full source you got your information from it could help them understand better what they are reading. Also it looks more professional.
Explanation:
What will be displayed on the next line after you type the code below in IDLE and press ENTER?
>>>print(1 + 5)
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The correct answer to this question is given below:
This is a python code when you will write it into IDLE and press enter.
It will print six as a digit on the screen such as below:
>>>print(1 + 5)
6
Because, when you will give two integer parameters and a "+" operator, then the print function will add the two-parameter and print the result of the sum (5 and 1) on screen. So this code will print 6 as a result of this code on the screen.
help
If we are looking at the predictor "car type," which can take on the values "sedan" "coupe" "truck" "suv" "van" how many binary decision variables would we need to code this data into a usable format?
Answers
If we are looking at the predictor "car type," which can take on the values "sedan" "coupe" "truck" "suv" "van", we would need 4 binary decision variables to code this data into a usable format.
A binary decision variable is a variable with only two possible values: 1 or 0. The variable is referred to as a binary variable, a binary indicator, or a 0-1 variable .The binary variable is used to answer yes/no questions. the binary variable " the binary variable is set to 0.To code the car type data into a usable format, we can use the binary decision variables.
We can use four binary variables to code the data into a usable format. We can use one variable for each category of car type. The values of the binary variables for the different categories are as follows:Sedan - 1000Coupe - 0100Truck - 0010SUV - 0001Using this format, if a car is a sedan, its binary decision variable would be set to 1000. If a car is a coupe, its binary decision variable would be set to 0100, and so on.
To know more about sedan visit:
https://brainly.com/question/24286177
SPJ11
jow to Fix: Incorrect permissions on Windows Search directories issue?
Answers
If you are experiencing an issue with incorrect permissions on Windows Search directories, you can follow these steps to fix the issue:
The Steps to followOpen the File Explorer and navigate to the following directory:
C:\ProgramData\Microsoft\Search
Right-click on the "Search" folder and select "Properties".
Click on the "Security" tab and then click the "Advanced" button.
In the "Advanced Security Settings" dialog box, click on the "Change" link next to "Owner".
In the "Select User or Group" dialog box, type your user account name in the "Enter the object name to select" field and click "OK".
Check the box next to "Replace owner on sub containers and objects" and then click "OK".
Click "Yes" when prompted to confirm the action.
Back in the "Advanced Security Settings" dialog box, click on the "Add" button.
In the "Select User or Group" dialog box, type "SYSTEM" in the "Enter the object name to select" field and click "OK".
Check the box next to "Full Control" and then click "OK".
Repeat steps 8-10 for the following user accounts: "Administrators", "Users", and "ALL APPLICATION PACKAGES".
Click "Apply" and then click "OK" to close the "Advanced Security Settings" dialog box.
Restart your computer to apply the changes.
After following these steps, the incorrect permissions on Windows Search directories should be resolved.
Read more about Windows directories here:
https://brainly.com/question/28288938
#SPJ1
Choose which type of translator you would use to develop a program written in a high-level programming language. Give three reasons to support your choice.
Answers
Answer:
Compilers
Explanation:
A compiler takes the source code as a whole and translates it into object code all in one go. Once converted, the object code can be run unassisted at any time. This process is called compilation.
Compilers have several advantages:
-Compiled programs run quickly, since they have already been translated.
-A compiled program can be supplied as an executable file. An executable file is a file that is ready to run. Since an executable file cannot be easily modified, programmers prefer to supply executables rather than source code.
-Compilers optimise code. Optimised code can run quicker and take up less memory space
hope this helped :D
The type of translator that you would use to develop a program written in a high-level programming language is known as Compiler.
What is a high-level programming language?The high-level programming language may be defined as a significant abstraction from the details of computer operation. It is designed to be easily understood by humans and for this reason, they must be translated by another software
A compiler significantly accepts the source code as a whole and successfully translates it into object code all in one go through the process of compilation. Compilers have several advantages. Some of them are as follows:
It compiled programs that run because they are already being successfully translated.A compiled program can be directly interpreted as an executable file that typically executes all essential and necessary functions.These compilers optimize code which improves performance, Reduced system load, protection for source code and programs, and improves productivity and quality.Therefore, the type of translator that you would use to develop a program written in a high-level programming language is known as Compiler.
To learn more about Compiler, refer to the link:https://brainly.com/question/27049042
#SPJ2
Select the correct answer.
What is the coding process commonly also called?
A. testing
B. development
C. debugging
D. refining
Answers
Answer:
B.
Explanation:
Answer:
development
is the correct answer
Do network packets take the shortest route?
Answers
Answer:
The packet will take a shorter path through networks 2 and 4
Answer:The packet will take a shorter path through networks 2 and 4, but networks 1, 3, and 5 might be faster at forwarding packets than 2 and 4. These are the kinds of choices network routers constantly make.What is shortest path routing in computer networks?
The goal of shortest path routing is to find a path between two nodes that has the lowest total cost, where the total cost of a path is the sum of arc costs in that path. For example, Dijikstra uses the nodes labelling with its distance from the source node along the better-known route.
Explanation:
comple with correct answer

Answers
Simply select cell H2, click on the tiny square in its lower-right corner, and drag it down to cell H7 to duplicate the formula in cell H2 in the range H3:H7.
How can a formula from one cell be copied to a group of cells?To fill a formula, first pick the cell containing the formula, then select the cells below it, and then hit Ctrl+D. To fill the formula to the right in a row, hit Ctrl+R as well.
If you duplicate a formula What will Excel do when the formula is copied to a new cell?Using the mouse, select the formula in the cell, and then hit Ctrl + C to copy it.
To know more about cell visit:-
https://brainly.com/question/8029562
#SPJ1
FREE BRAINLIEST!!!
When recording a macro, the cursor will look like a _____ to indicate it is recording. A.microphone
B. Arrow
C. CD
D. cassette tape
Answers
Answer:
B
Explanation:
Answer:
When recording a macro, the cursor will look like a cassette tape to indicate it is recording. This answer has been confirmed as correct and helpful.
Explanation:
the correct answer is D
how do I get the bot token for discord? (scripting etc)
Answers
Answer:
1 Open your App on the Developer Portal.
2 Go to the Bot settings from the side menu.
3 Press the Reset Token button located under the Build-a-Bot section.
4 A pop-up window will show up asking you to confirm.
5 Your new token will now show up under the Build-A-Bot section. Make sure to copy and paste it into your code right away. Be sure to follow good token management security practices!
Who watches Riverdale ? if you do can we be friends(pLEASE DON'T DELETE) and also who is your fav character from Riverdale





Answers
Answer:
I have watched it before
Answer:
my fav is veronica lol
Explanation:
A customer seeks to buy A new computer for private use at home. The customer primarily needs the computer to use the microsoft powerpoint application for the purpose of practising representation skills. As a salesperson what size hard disc would you recommend and why?
Answers
Answer:
I think 128GB of storage would be fine.
Explanation:
It sounds like this person he's only looking to do basic tasks as you would still have room to do other things.
having multiple class methods of the same name where each method has the same number of or type of parameters is known as
Answers
A method that has multiple definitions is an overloaded method. The versions of an overloaded method are distinguished by the number, type and order of their parameters.
What is meant by Parameters ?
To describe the entire population under study, a parameter is utilized. For instance, we are interested in learning the typical length of a butterfly. This information about the total butterfly population makes it a parameter.a random constant whose value describes a system's component (such as a family of curves) also: a measurement that characterizes a statistical population (such a mean or variance).You can find 9 terms that are similar to parameter on this page, including criterion, framework, guideline, restriction, specification, and constant.Four parameters, referred to as hybrid or h Parameters, can be used to assess any linear circuit with input and output terminals. These parameters are one measured in ohm, one in mho, and two dimensionless.To learn more about Parameters refer to
https://brainly.com/question/28175212
#SPJ4