Write a program that dynamically allocates an array, on the heap, large enough to hold 200 test scores between 55 and 99.
Answers
The program dynamically allocates an array on the heap to hold 200 test scores between 55 and 99. By dynamically allocating the array, the program ensures that the memory is allocated at runtime and can be accessed and resized as needed.
To allocate an array on the heap, the program can use dynamic memory allocation functions such as malloc or new. In this case, the program needs to allocate an array capable of holding 200 test scores within the specified range of 55 to 99.
The first step is to calculate the size of the array based on the number of elements and the size of each element. Since the test scores are represented as numbers, typically taking up 4 bytes each, the array size would be 200 multiplied by the size of an integer (4 bytes).
import ctypes
def allocate_array(size):
# Define the data type for the array elements (we'll use integers for test scores)
ArrayType = ctypes.c_int * size
# Allocate the array on the heap
array = ArrayType()
return array
def main():
min_score = 55
max_score = 99
num_scores = 200
# Allocate the array on the heap to hold 200 test scores
test_scores = allocate_array(num_scores)
# Initialize the array with random test scores between 55 and 99
for i in range(num_scores):
test_scores[i] = ctypes.c_int(random.randint(min_score, max_score))
# Print the test scores
print("Test Scores:")
for score in test_scores:
print(score)
if __name__ == '__main__':
main()
Next, the program uses the appropriate dynamic memory allocation function (e.g., malloc) to allocate the required memory on the heap. The size of the array is passed as an argument to the allocation function, and the returned pointer is assigned to a variable.
After successfully allocating the memory, the program can access the array using the allocated pointer. It can then iterate over the array to store or retrieve the test scores as needed.
Once the program is finished using the dynamically allocated array, it should release the allocated memory using the corresponding deallocation function (e.g., free). This ensures proper memory management and prevents memory leaks.
In summary, the program dynamically allocates an array on the heap to hold 200 test scores between 55 and 99. By using dynamic memory allocation, the program ensures flexibility in memory management, allowing for efficient utilization of memory resources.
To learn more about array: -brainly.com/question/33609476
#SPJ11
Related Questions
Select the correct answer.
Which option should you select to accept a tracked change?
O A.
Accept
Reject
O C. Review
OB.
O D. Delete
Answers
Answer:
Explanation:
Which option should you select to accept a tracked change?
A. Accept
which technology can prevent client devices from arbitrarily connecting to the network without state remediation
Answers
The technology that can prevent client devices from arbitrarily connecting to the network without state remediation is Network Access Control (NAC).
Network Access Control
NAC verifies the state of client devices before allowing them to connect to the network. It ensures that the client device meets the organization's security policies and standards before granting access to the network. NAC can also enforce state remediation, which means that if a device is not compliant with the security policies, it will be isolated and remediated before being granted access to the network. NAC helps organizations maintain network security by controlling who can access the network and enforcing security policies for client devices.
To know more about Network Access Control visit:
https://brainly.com/question/30198778
#SPJ11
advertising, like any part of the promotional mix, can be managed by following several steps, including which of these? multiple select question. isolating executing predicting evaluating measuring
Answers
Advertising, like any part of the promotional mix, can be managed by Executing & Evaluating.
What is advertisement in promotion mix?Advertising is the practice of marketing a company's goods or services by the use of paid advertising in mass media, such as banners, radio, television, newspapers, billboards, and digital media.The role of promotion in the marketing mix is crucial since it increases consumer awareness of your company's name and its goods by focusing on the correct demographic of customers. Consequently, there will be more demand in the market, which will enhance sales for your business.The combination of many communication strategies and techniques you employ to introduce your business, goods, or services to your target market makes up your promotion mix. Since it aids in client attraction, effective advertising is a crucial element of the marketing mix.To learn more about Advertising refer,
https://brainly.com/question/1658517
#SPJ1
A team of scientists is designing a study to examine factors that affect
people's enjoyment of video games. Which statement best represents a valid
hypothesis for the study?
A. More people enjoy role-playing games than platformer games.
B. Action games are better than role-playing games.
C. The graphics in console games are cooler than those in PC
games.
O D. Video games are fun.
Answers
Answer:
A. More people enjoy role-playing games than platformer games.
Explanation:
It is A because the genre of game is a factor of a video game.
B is trying to state an objective truth that one genre is better than another but not giving a reason (like it being more enjoyable).
C isn't even really game related, that would be a study on which gaming platforms are more enjoyable and why.
D has already been established. The current study is to determine what makes them more or less enjoyable.
Answer:
B. Action games are better than role-playing games.
Explanation:
In my opinion I like to do roleplay's I don't know why but I just do, but this is the correct answer.
how has the ietf come up with ways to extend the life of ipv4 addresses?
Answers
The Internet Engineering Task Force (IETF) has come up with several ways to extend the life of IPv4 addresses. One such method is Network Address Translation (NAT), which allows multiple devices to share a single IPv4 address.
This is accomplished by assigning private IP addresses to devices on a network, and then translating those addresses to a public IP address when traffic leaves the network. NAT effectively allows a single public IPv4 address to represent an entire network of devices, thus conserving addresses.
Another method is Classless Inter-Domain Routing (CIDR), which is a more efficient method of allocating IP addresses than the original class-based system. CIDR allows for more flexibility in address allocation, and allows for smaller blocks of addresses to be assigned to networks as needed. This reduces waste and allows for better utilization of the available address space.
The IETF has also developed Engineering for conserving IPv4 addresses through the use of address reuse and renumbering. Address reuse involves reclaiming unused addresses and assigning them to other devices as needed. Renumbering involves reassigning addresses to different devices or networks as needed, allowing for better utilization of the available address space.
To know more about Engineering visit:
https://brainly.com/question/31140236
#SPJ11
the unix operating system started the concept of socket which also came with a set of programming application programming interface (api) for 'socket level' programming. a socket was also uniquely identified as
Answers
TCP sockets.
whether they are distributed across a local system or a TCP/IP-based network environment, are provided by a socket programming interface.
What is a TCP socket?The routines needed for interprocess communication between applications, whether they are distributed across a local system or a TCP/IP-based network environment, are provided by a socket programming interface.Three components make up a socket: protocol, local address, and local port. The two processes that make up a connection are fully described by the term "association": (protocol,local-address,local-port,foreign-address,foreign-port).TCP offers dependable data stream delivery between hosts on the Internet. Similar to UDP, TCP supports the block transmission of a nonstop stream of datagrams between process ports and makes use of Internet Protocol as the underlying protocol for datagram transport. TCP offers dependable message delivery in contrast to UDP.To learn more about : TCP socket
Ref : https://brainly.com/question/14280351
#SPJ4
An organization-wide function that oversees the development and the enforcement of data policies and standards are an important role in ________.
Answers
Answer:Data Administration
Explanation:
please help
suppose you work for a large company create a short memo letting your coworker know that July 3 is also a paid holiday
Answers
From: Tom Pearson, Manager, District Five
Regarding: New Incoming Manager, Geraldine Hines
Dear Comstock Staff: Beginning March 15, 2018, you will have a new District Five Regional Manager. After 35 years of continuous service, I am leaving all of you to pursue an exciting future.
It has been my pleasure to train my successor, Geraldine Hines, this past year. Geraldine has demonstrated that she shares the company vision to be the employer of choice here in the Valley of the Sun. I am confident that she will lead all of you into the stratosphere as we merge our call centers and expand our donor site availability.
Please give Geraldine the same level of excellence you have given to me, to our staff and to our donors.
Sincerely.
Tom Pearson, Outgoing Manager, District Five
what server is contacted to retrieve the uri http://www.amazon/zero-day-threat-cyberspace-ebook/dp/b00b05mqgu/?
Answers
The server contacted to retrieve the URI http://www.amazon/zero-day-threat-cyberspace-ebook/dp/b00b05mqgu/ is the Amazon server.
The URI or Uniform Resource Identifier is a string of characters that are used to identify a name or a web resource in the internet domain.
An example of URI is URL or Uniform Resource Locator. A URL is used to specify a particular web page on the internet. The URL in the given question belongs to Amazon, a popular online shopping website. The URL http://www.amazon/zero-day-threat-cyberspace-ebook/dp/b00b05mqgu/ specifies the location of a particular e book titled "Zero Day Threat: The Shocking Truth of How Banks and Credit Bureaus Help Cyber Crooks Steal Your Money and Identity" which can be found on Amazon's website. The server contacted to retrieve this URI would be Amazon's server since the resource requested is present on Amazon's website. I hope this answer helps you.
To know more about Amazon visit:
https://brainly.com/question/30086406
#SPJ11
Which of the following should you NOT do when using CSS3 properties to create text columns?
a. Make the columns wide enough to read easily.
b. Justify the text in the columns.
c. Include the property prefixes required to display the columns in browsers that support this
feature.
d. Code the columns in an article element.
Answers
The answer is d. Code the columns in an article element. When using CSS3 properties to create text columns, it is generally a good practice to use appropriate column widths, justify the text, and include the necessary prefixes for browser compatibility.
However, the choice of HTML element to contain the columns is not directly related to the use of CSS3 properties.
Therefore, option d is incorrect as it suggests that the columns should be coded within an article element which is irrelevant and does not have any bearing on the CSS3 properties used to create the columns. The choice of HTML element should be based on semantic meaning and hierarchy of content rather than simply to contain text columns.
So, to summarize, you should NOT code the columns in an article element when using CSS3 properties to create text columns.
Learn more about CSS3 here:
https://brainly.com/question/31851771
#SPJ11
To create a pie chart, Maria selected the data she wanted to represent, selected the inset tab and Pie Chart command. What is the last step she needs to complete to create a pie chart?
A: Select 2-D Pie Chart from the Chart tab
B: Select 2-D Pie Chart from the data ribbon
C: Select 2-D Pie Chart from the drop-down menu
D: Select 2-D Pie Chart from the survey group
GIVING THE BRAINLYEST
Answers
What are three ways of verifying legitimate right of access to a computer system?
Answers
Three ways of verifying legitimate right of access to a computer system are,
Something you know (such as a password) Something you have (such as a smart card) Something you are (such as a fingerprint or other biometric method)What are the 3 methods of authentication?A fingerprint is an impression left by the friction ridges on a human finger. A critical forensic science technique is obtaining partial fingerprints from a crime scene. Moisture and oil on the finger leave fingerprints on metal or glass surfaces.There are three types of fingerprints. The three types of fingerprints are whirls, loops, and ridges. The loops were the most common, with a prevalence of 60% to 65%. Furthermore, we discovered that whirls, which account for between 30% and 35% of all fingerprints, are the second most common. Factor of knowledge: One of the three authentication factors is something you know, such as a password.To learn more about Fingerprints , refer
https://brainly.com/question/5628467
#SPJ4
cmu 2.5.4 scoreboard i need help with all of cmu 2.5.4
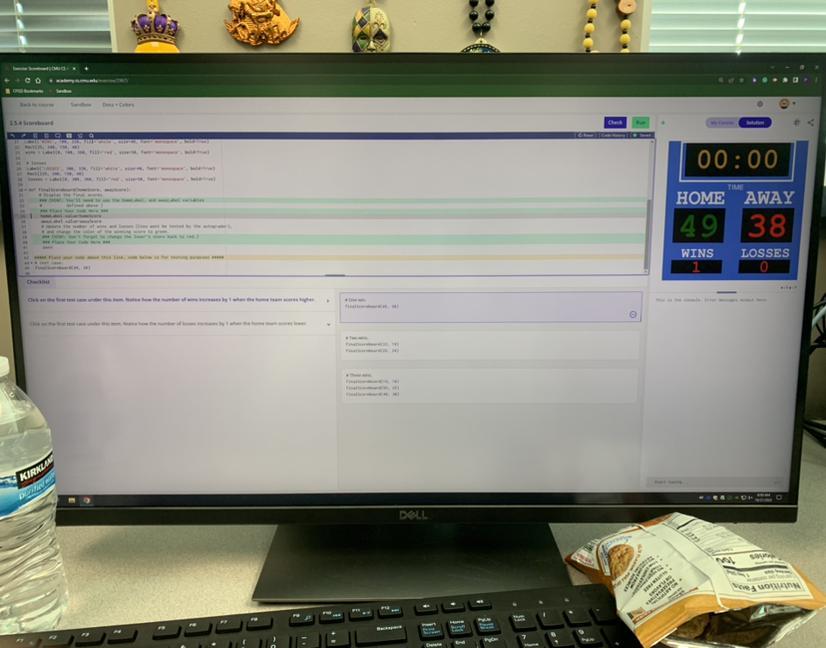
Answers
Answer:
Explanation: i can not see your sreeen
b
Simeiry: Wit Cenfirm orapticiy that the ecuation is anticentiv
Answers
The equation is not inherently anticentive.
Anticentive refers to a situation where individuals or entities are disincentivized from taking certain actions or pursuing certain outcomes.To determine if the equation is anticentive, we need to assess the incentives or disincentives it creates for different actors or scenarios.The equation itself does not possess a built-in disincentive; it is a neutral mathematical expression.The determination of whether an equation becomes anticentive depends on the context in which it is applied, the associated costs or benefits, and the preferences of the actors involved.If the equation is used in a specific scenario where the resulting outcomes or costs create disincentives, it can be considered anticentive in that particular context.However, it is important to note that the equation itself is not inherently anticentive but rather its application or the consequences it implies can lead to such effects.The equation itself is not anticentive, as it is a neutral mathematical expression. The anticentive nature of the equation arises from its application in specific contexts and the resulting costs or outcomes. Assessing the incentives or disincentives requires a thorough analysis of the associated context and the preferences of the actors involved.
Learn more about Equation :
https://brainly.com/question/29797709
#SPJ11
you are using the vi editor to manage a text file on a linux system. you want to type new text into the file. when you type, you want the existing text that comes after the cursor to be pushed down. which mode provides this function?
Answers
Insert mode in the vi editor provides the function to type new text into the file, pushing existing text that comes after the cursor down
In the vi editor, there are two main modes:
command mode insert mode.In command mode, you can perform actions on the file such as saving, quitting, or moving the cursor.
In insert mode, you can type new text into the file. When you are in insert mode, any existing text after the cursor will be pushed down as you type new text.
To enter insert mode in vi, you can press "i" or "a" or "o" key, depending on where you want to insert the text (before the cursor, after the cursor, or on a new line below the cursor).
To exit insert mode and return to command mode, you can press the "Esc" key.
These commands can only be executed in command mode and are not available in insert mode. It is important to be familiar with the different commands and modes in the vi editor, as it is a powerful tool for text editing in a Linux environment.
To know more about vi editor, click on the link below:
brainly.com/question/17193196
#SPJ4
Choose the words that complete the sentences.
A_______
is used to edit raster images.
A_______
is used to edit vector images.
A_______
is used to control a scanner or digital camera.
Answers
Answer:
A paint application
is used to edit raster images.
A drawing application
is used to edit vector images.
A digitizing application
is used to control a scanner or digital camera.
Explanation:
got it right on edg
Question 1 of 10
What did Yanek do the first night he slipped from the flat with his father?
А
He fed the fires at Uncle Abraham's bakery to help make bread.
B.
He started a fire in the trash can behind the German SS headquarters.
С
He attached messages to the legs of Mr. Immerglick's pigeons.
D
He led the Rosenblums to the gate at Zgody Square, so they could escape.
Answers
The phrase "premeditated" in the passage's fourth sentence ("I moved... step") denotes the narrator is being very cautious as he navigates the fire escape.
What best describes the narrator?The first person point of view is used by the narrator. His character is a straightforward narration of his narrative. First-person pronouns are used to describe the thoughts, experiences, and observations of a narrator in first-person point of view stories.
It wasn't planned to end up at Concordia after a childhood spent traveling between Europe, Africa, and the United States. He had plenty of time to consider how terrible his acts were and change his ways because it had been carefully thought out and premeditated.
Therefore, The phrase "premeditated" in the passage's fourth sentence ("I moved... step") denotes the narrator is being very cautious as he navigates the fire escape.
To learn more about Narrator here:
brainly.com/question/12020368
#SPJ1
What should Iris obtain from the client in order to display the work in her portfolio?
Answers
Answer:
depends on the laws of the country in which you are working
Explanation:
This is very vague and usually depends on the laws of the country in which you are working. In some cases, Iris would need permission from the client in order to display the work. In other cases, Iris would not need anything because she is the original creator of the content. This mostly depends on the laws of the country and whether or not a specific contract was created between Iris and the client, stating if the content rights where transferred or not.
Tim has several workbooks open in the Excel application. He would like to view them all at the same time, so he should use the ______ command.
Answers
Answer:
Arrange All
Explanation:
For him to to view them all at the same time, so he should use the Arrange All
command. To do this, you will need to
Open the workbooks that is needed to arrange, in this case at least two workbooks are to be opened, then make selection of the worksheet in each workbook that is needed to be displayed, then on the view tab, you can make selection of "Arrange All button" in the Window.
What would happen if you fake a credit card number online on a website.
My 13 year old friend did that months ago and now he got a message saying his “chase account was locked due to suspicious activities”
I’m only asking because he’s freaking out
Answers
Complete the work by inputting the right answers. #1,#2,#3and #4


Answers
Based on the given information, the appropriate function for cell E7 would be the SUM function.
What is the SUM function?The SUM function is used to add up a range of numbers. In this case, cell E7 is intended to display the total cost of all the classes offered during the summer, which is the sum of all the costs in the table.
Therefore, the SUM function is the appropriate function for this purpose. The formula for using the SUM function would be "=SUM(D3:D6)". This formula will calculate the sum of the values in cells D3 through D6, which represent the costs of the individual classes.
Learn more about Sum function on
https://brainly.com/question/29478473
#SPJ1
Social perceivers are more likely to form accurate judgments of others if they... Group of answer choices Rely exclusively on cognitive heuristics Make broad, global judgments Are motivated to be accurate Ignore logic and trust their instincts
Answers
Social perceivers are more likely to form accurate judgments of others if they rely exclusively on cognitive heuristics.
Cognitive heuristics refer to mental shortcuts or simplified strategies that individuals use to make judgments and decisions. By relying on cognitive heuristics, social perceivers can efficiently process information and form quick judgments based on limited cues or information available.
These heuristics can include stereotypes, schemas, or previous experiences that help categorize and understand others. However, it is important to note that relying exclusively on cognitive heuristics may lead to biases and inaccurate judgments if they are not based on accurate or updated information. Therefore, a balanced approach that combines cognitive heuristics with open-mindedness and considering additional information can enhance accuracy in social judgments.
Learn more about cognitive heuristics here:
https://brainly.com/question/29545194
#SPJ11
please answer ASAP!!!!!!

Answers
Answer:
the first constructor invocation will work.
pet temp("mouse", 5.99);
Explanation:
This will create a pet object on the stack, using the constructor.
If you want to create an object on the heap, you would use the new operator:
pet* pTemp = new pet("mouse", 5.99);
I need help please hurry!!!!!!! jay works in the it department. his main responsibility at work is to keep all equipment working. he needs to know what maintenance to perform and when. he should _____.
inventory all equipment
copy the user's manual and distribute it to all the employees
read the manuals
update the software in the office
establish the frequency of maintenance tasks
identify individuals to complete the tasks
set up auto reminders
list the maintenance tasks
create a log to document maintenance
Answers
Jay is employed with the it division. Maintaining the functionality of all equipment is his primary duty at work. He must understand what upkeep to execute and when to decide to perform maintenance.
He needs to decide how often to perform maintenance. The number of jobs that must be completed in a certain amount of time is referred to as maintenance frequency. Its periodicity can also vary based on the set time, from daily to weekly. Work equipment comprises a working platform, fall arrest devices, and any gear, computers, apparatus, tools, or installations used exclusively or mostly for work-related purposes. Task analysis examines how a task is carried out and includes a thorough description of both manual and mental processes, the lengths of the task and its elements, and task frequency.
Learn more about computers here
https://brainly.com/question/20414679
#SPJ4
Utility software as a service giving programs. Explain. Give me the answer please coming Sunday my homework will be check.
Answers
Answer:
Explanation:
Utility software is software designed to help to analyze, configure, optimize or maintain a computer. It is used to support the computer infrastructure - in contrast to application software, which is aimed at directly performing tasks that benefit ordinary users.
The value 8/10 in a cell refers to which of these?
Question 1 options:
Aug-10
August 10th
all of these
October 8th
Answers
The value 8/10 in a cell typically refers to D. October 8th, as it is common for dates to be represented in the format of "month/day" in the United States and many other countries.
How is this format used in a cell?In the format of "month/day", the first number represents the month and the second number represents the day. In this case, 8 would represent the 8th month (August) and 10 would represent the 10th day.
However, it is also important to consider the context in which the cell is being used, as well as the culture or country where the information is being used or collected. In some countries, the format "day/month" is used, in that case, the value 8/10 would refer to 8th of October.
Read more about date formats here:
https://brainly.com/question/29406774
#SPJ1
Question 7 of 10
Charts are most useful for which task?
A. Removing data that is not useful from a spreadsheet
B. Organizing data into a new spreadsheet
C. Creating more columns in a spreadsheet
D. Creating visual displays of data for presentations
Answers
In order to make it simpler to understand enormous amounts of data as well as the relationships between various series of data, series of numeric data are displayed in charts in a graphical manner.
What is Charts?A chart, also known as a graph, is a graphic representation for visualizing data in which "the data is represented by symbols, such as bars in a bar chart, lines in a line chart, or slices in a pie chart." A chart can show functions, some types of quality structures, or tabular numerical data and can convey a variety of information.As a graphic way to convey data, the word "chart" can mean several different things:An example of a diagram or graph that organizes and depicts a collection of quantitative or qualitative data is a data chart.Charts, such as a nautical chart or an aeronautical chart, are oftentimes referred to as maps that are embellished with additional information (map surround) for a particular purpose and are typically distributed across multiple map sheets.A record chart for album popularity or a chord chart in music notation are examples of other domain-specific constructions that are commonly referred to as charts.To Learn more About charts refer To:
https://brainly.com/question/25032284
#SPJ1
english journal needed 300-400 word
The veldt: Do you think that science fictional stories are a useful way for understanding contemporary issues with technology? How might projecting technology into the future, amplifying its effects, help us achieve a better understanding of our relationship to it?
Answers
Answer:
Explanation:Science fiction stories can help us understand contemporary issues with technology by projecting its potential implications in the future. By presenting extreme scenarios, science fiction can help us reflect on our relationship with technology and recognize its potential dangers. For example, "The Veldt" is a cautionary tale that warns us of the dangers of becoming too reliant on technology and losing touch with our humanity. As we continue to advance technologically, it is important to reflect on our relationship with technology and use stories like "The Veldt" to navigate ethical and moral issues that arise.
Yes, science fictional stories can be a useful way to understand contemporary issues with technology, as projecting technology into the future and amplifying its effects can help us achieve a better understanding of our relationship to it.
Science fiction often explores the potential consequences of technological advancements and their impact on society. By extrapolating these advancements into the future, science fiction can provide insights into how technology might shape our lives and the world around us.
This can help us better understand the potential benefits and risks of new technologies and how we might navigate their impacts. For example, Ray Bradbury's "The Veldt" explores the dangers of technology when it replaces human connection and creates a destructive dependence on virtual experiences.
Through science fiction, we can explore complex issues in a way that is engaging and accessible, providing valuable insights into our relationship with technology.
For more questions like Technology click the link below:
brainly.com/question/30004991
#SPJ11
Unit 6: Lesson 2 - Coding Activity 3 for projectstem. Org coding thing
Answers
Project Stem was founded as a 501(c)(3) non-profit corporation. Its goal is to help students get the confidence they need to participate, learn, and continue in the subject of computer science.
What is a Coding Activity?A coding activity refers to activities that help the students learn to code. Some of the activities are designed as:
GamesPuzzles and Actual assignment.Examples of coding activities could be:
To guide a Jupiter RoverTo create a pixel puzzle etc.Learn more about Coding Activities are:
https://brainly.com/question/25250444
Five senders share a 10 mbps channel using code division multiplexing. each sender will have a sending bit rate of about ________ mbps.
Answers
Five senders sharing a 10 Mbps channel using code division multiplexing will have a sending bit rate of about 2 Mbps each.
Code division multiplexing (CDM) allows multiple senders to transmit their data simultaneously by using different codes to differentiate their signals. In this scenario, with five senders, the available channel capacity of 10 Mbps is divided equally among them.
Since each sender shares the channel, the sending bit rate for each sender will be approximately the total channel capacity (10 Mbps) divided by the number of senders (5). Hence, each sender will have a sending bit rate of around 2 Mbps. This means that each sender can transmit data at a rate of 2 megabits per second over the shared channel, allowing for concurrent transmission without significant interference or loss of data.
To learn more about code
https://brainly.com/question/30130277
#SPJ11