which statement describes a route that has been learned dynamically?
Answers
A dynamically learned route refers to a routing path that is determined and adjusted in real-time based on network conditions and traffic information.
In computer networking, a dynamically learned route is a routing path that is not preconfigured or statically set but is instead determined and adjusted dynamically based on current network conditions. This dynamic routing process involves routers exchanging information with each other to determine the most efficient paths for data packets to travel. One common dynamic routing protocol used in the Internet is the Border Gateway Protocol (BGP), which allows routers to exchange information about the best routes to reach different network destinations.
When a route is learned dynamically, routers constantly exchange routing updates to adapt to changes in the network topology, link failures, or congestion. These updates contain information such as network reachability, path costs, and available bandwidth. Based on this information, routers can make informed decisions about the best routes to forward packets. By dynamically learning routes, networks can be more resilient and adaptable to changing conditions, enabling efficient traffic distribution and improved overall network performance.
Learn more about traffic information here:
https://brainly.com/question/11104847
#SPJ11
Related Questions
If a change is made to the active
cell, what type of cell will also
change?
Precedents
Dependents
Answers
Answer:
precedents
Explanation:
Please! I need help matching this.
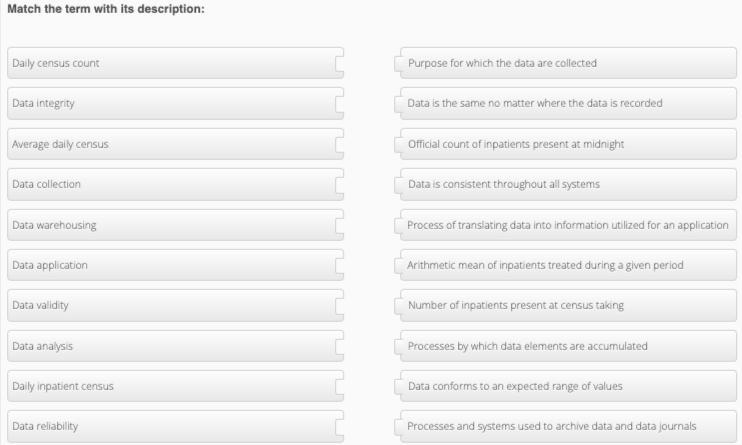
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
What is binary search tree?
Answers
The node-based binary tree data structure known as the "Binary Search Tree" includes the following characteristics: A node's left subtree only has nodes with keys lower than the node itself.
Only nodes with keys higher than the node's key are found in the right subtree of the node.
Binary Search Tree iterative search
a programme to determine whether or not a binary tree is BST
Conversion of a Binary Tree into a Binary Search Tree
Find the node in a binary search tree with the lowest value.
Verify whether or not an array represents the Inorder of Binary Search tree.
How can you tell if a binary tree is balanced in height?
Balancing Sorted Array to BST
Without creating the trees, check for identical BSTs.
Change a standard BST to a balanced BST
BST to Min Heap conversion
BST's second-largest component
Learn more about Binary tree here:
https://brainly.com/question/13152677
#SPJ4
DDL statement for adding a column to an existing table is
Answers
Answer:to add a column to existing table.
to rename any existing column.
to change datatype of any column or to modify its size.
to drop a column from the table.
Explanation:
hope this help
in the united states, the internet is currently diffused to what level? mcj 178
Answers
The answer to your question is that the internet is currently diffused to a very high level in the United States. This primary key means that the vast majority of the population has access to and uses the internet on a regular basis.
it's important to note that internet usage has become an integral part of daily life in the US. According to recent statistics, around 89% of adults in the US use the internet, and the vast majority of these individuals use it on a daily basis. This high level of diffusion is due in part to widespread access to broadband internet, which has made it easier and more affordable for people to get online.
However, it's worth noting that there are still some areas of the country where internet access is limited or non-existent, particularly in rural areas. Additionally, there are some demographic groups, such as low-income individuals, who may have less access to the internet than others. Nonetheless, overall, the internet is a highly diffused technology in the United States, with significant implications for everything from communication and entertainment to education and commerce.
To know more about primary key visit:
https://brainly.com/question/14011765
#SPJ11
Write a program that inputs the length of two pieces of wood in yards and feet (as whole numbers) and prints the total.
Sample Run
Enter the Yards: 3
Enter the Feet: 2
Enter the Yards: 4
Enter the Feet: 1
Sample Output
Yards: 8 Feet: 0
Hint: Change all of the inputs into feet first - remember there are 3 feet in each yard. Now that the wood is in feet, find the yards and feet similarly to the last practice, using regular and modular division.
Answers
A program that inputs the length of two pieces of wood in yards and feet (as whole numbers) and prints the total is given below:
The Programa_ft = int(input("Enter the Feet for the first piece of fabric: "))
a_inc = int(input("Enter the Inches for the first piece of fabric: "))
b_ft = int(input("Enter the Feet for the second piece of fabric: "))
b_inc = int(input("Enter the Inches for the second piece of fabric: "))
sum_inc = a_inc + b_inc
# select the whole and the fractional part
inc_to_ft = sum_inc // 12
rem_from_div = sum_inc % 12
sum_ft = a_ft + b_ft + inc_to_ft
print("Feet: {} Inches: {}".format(sum_ft, rem_from_div))
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
If Jake wants to find out if the size of a fruit has any effect on the total sales for the week of that particular fruit, what chart should he use?
Answers
Answer:
XY scatter
Explanation:
XY (Scatter) maps plot two sequence of data as one set of XY coordinates. XY charts demonstrate the relationship between two sets of data. Each indicator is a piece of data. Each data set should have two types of information: its XY coordinate. XY charts are capable of having more than one set.
henry already has installed red hat linux on his server but now needs to install virtual machines. what type of hypervisor package should he use?
Answers
Henry already has installed red hat Linux on his server, but now needs to install virtual machines. The type of hypervisor package he should use is Type II. The correct option is b.
What is a Type II hypervisor package?A Type 2 hypervisor, also known as a hosted hypervisor, is a virtual machine (VM) manager that runs as a software application on top of an existing operating system (OS).
An operating system is used to install the software. The hypervisor requests that the operating system perform hardware calls. VMware Player or Parallels Desktop are examples of Type 2 hypervisors. Hosted hypervisors are frequently seen on endpoints such as PCs.
Therefore, the correct option is b, Type II.
To learn more about the hypervisor package, refer to the link:
https://brainly.com/question/20892566
#SPJ1
The question is incomplete. Your most probably complete question is given below:
Type I
Type II
Type III
Type IV
Joe works with a client who has recently reported a problem with his Android smartphone. The client has only had the smartphone for a few weeks, but he has noticed that the phone has developed a very short battery life. The client acknowledges that he recently installed some new apps on the smartphone and that he attempted to remove some applications that were bundled with the phone.
Answers
Since the problem with his Android smartphone is short battery life. the right thing to do are:
Uninstall some applications on his phoneReplace the battery with a new one.What causes short battery life?The situations where a persons phone do overheat, when their battery is fully charged is known to be one that tends to often drain your battery drains a lot faster when it's hot.
Note that some things that is draining your battery so fast is that when your phone keeps a lot of applications.
Therefore, Since the problem with his Android smartphone is short battery life. the right thing to do are:
Uninstall some applications on his phoneReplace the battery with a new one.Learn more about Android smartphone from
https://brainly.com/question/14848412
#SPJ1
who sang devil went down to georgia
Answers
Answer:
Charlie Daniels sang that one for sure
How should an artist use the principles of design when creating artistic work?
follow them to the letter
let them come naturally
don’t think about them
experiment with them
Answers
Answer:
Let them come naturally
Explanation:
I think
Breakout:
I have my code, it’s all worked out, but my paddle doesn’t move. Where is it wrong?
/* Constants for bricks */
var NUM_ROWS = 8;
var BRICK_TOP_OFFSET = 10;
var BRICK_SPACING = 2;
var NUM_BRICKS_PER_ROW = 10;
var BRICK_HEIGHT = 10;
var SPACE_FOR_BRICKS = getWidth() - (NUM_BRICKS_PER_ROW + 1) * BRICK_SPACING;
var BRICK_WIDTH = SPACE_FOR_BRICKS / NUM_BRICKS_PER_ROW;
/* Constants for ball and paddle */
var PADDLE_WIDTH = 80;
var PADDLE_HEIGHT = 15;
var PADDLE_OFFSET = 10;
var paddle;
var setPosition;
var rectangle;
var BALL_RADIUS = 15;
var ball;
var dx = 4;
var dy = 4;
function start(){
drawBricks();
drawBALL(BALL_RADIUS, Color.black, getWidth()/2, getHeight()/2);
mouseMoveMethod(pad);
ball = new Circle (BALL_RADIUS);
ball.setPosition(200, 200);
add(ball);
setTimer(draw,20);
}
function drawBricks(){
for(var j = 0; j < NUM_ROWS;j++){
for(var i = 0; i < NUM_BRICKS_PER_ROW; i++){
var brick = new Rectangle(BRICK_WIDTH, BRICK_HEIGHT);
if((j + 1) % 8 == 1 || (j + 1) % 8 == 2){
brick.setColor(Color.red);
} else if ((j + 1) % 8 == 3 || (j + 1) % 8 == 4){
brick.setColor(Color.orange);
}else if ((j + 1) % 8 == 5 || (j + 1) % 8 == 6){
brick.setColor(Color.green);
}else if ((j + 1) % 8 == 7 || (j + 1) % 8 == 0){
brick.setColor(Color.blue);
}
brick.setPosition(BRICK_WIDTH * i + BRICK_SPACING * (1 + i), BRICK_TOP_OFFSET + BRICK_HEIGHT * j + BRICK_SPACING * (1 + j));
add(brick);
}
}
}
function drawBALL(BALL_RADIUS, color, x, y){
ball = new Circle (BALL_RADIUS);
ball.setPosition(200, 200);
add(ball);
setTimer(draw, 20);
}
function draw(){
checkWalls();
ball.move(dx, dy);
}
function mousemoveMethod(pad){
ball = new Circle (BALL_RADIUS);
ball.setPosition(200, 200);
add(ball);
setTimer(draw, 20);
}
function checkWalls(){
if(ball.getX() + ball.getRadius() > getWidth()){
dx = -dx;
}
if(ball.getX() - ball.getRadius() < 0){
dx = -dx;
}
if(ball.getY() + ball.getRadius() > getHeight()){
dy = -dy;
}
if(ball.getY() - ball.getRadius() < 0){
dy = -dy;
}
var elem = getElementAt(ball.getX(), ball.getY() - ball.getRadius());
if (elem != null) {
dy = -dy;
remove(elem);
}
elem = getElementAt(ball.getX(), ball.getY() + ball.getRadius());
if (elem != null) {
dy = -dy;
}
}
function pad(e){
paddle = new Rectangle(PADDLE_WIDTH, PADDLE_HEIGHT);
paddle.setPosition(getWidth()/2 - paddle.getWidth()/ 2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
mouseMoveMethod(pad);
add(paddle);
}
Answers
In your code, I can see a few issues that might be causing your paddle not to move correctly:
In the mousemoveMethod(pad) function, you have defined pad as a parameter, but you're not using it within the function. Instead, you should use the e parameter, which represents the mouse event. Modify the function to use e instead of pad.
You are calling the mousemoveMethod(pad) function inside the pad(e) function. This creates an infinite loop and may cause unexpected behavior. You should remove the mousemoveMethod(pad) function call from the pad(e) function.
The mousemoveMethod(pad) function is creating a new circle and adding it to the canvas, which is unnecessary for moving the paddle. Instead, you should update the position of the existing paddle based on the mouse movement. Modify the mousemoveMethod(pad) function as follows:
javascript
Copy code
function mousemoveMethod(e) {
var x = e.getX();
paddle.setPosition(x - paddle.getWidth() / 2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
}
Make sure to update all the function calls and event listeners accordingly.
By making these changes, your paddle should move correctly based on the mouse movement.
I apologize for the confusion. It seems that there was a mistake in my previous response. In the provided code, the mouse event parameter is not being passed correctly to the mousemoveMethod function. To fix this issue, you can modify your code as follows:
In the pad(e) function, change the line mouseMoveMethod(pad); to mouseMoveMethod(e);. This will pass the mouse event parameter to the mousemoveMethod function correctly.
Modify the mousemoveMethod function to access the mouse coordinates correctly. Use e.getX() and e.getY() to get the current mouse position. Update the paddle position accordingly:
javascript
Copy code
function mousemoveMethod(e) {
var x = e.getX();
paddle.setPosition(x - paddle.getWidth() / 2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
}
With these changes, the paddle should move correctly based on the mouse position.
The mouseMoveMethod function is not correctly defined. The parameter "pad" is not necessary and should be removed. Instead of calling mouseMoveMethod(pad) inside the pad function, you should call the mouseMoveMethod function directly.
Here's the corrected code for the pad function:
function pad(){
paddle = new Rectangle(PADDLE_WIDTH, PADDLE_HEIGHT);
paddle.setPosition(getWidth()/2 - paddle.getWidth()/2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
add(paddle);
mouseMoveMethod();
}
The mousemoveMethod function is unnecessary and can be removed. It is also misspelled, as the correct name is mouseMoveMethod (with a capital 'M'). You can directly include the code to handle the mouse movement inside the pad function.
Here's the corrected code for the mouseMoveMethod:
function mouseMoveMethod(){
onMouseMove(function(e){
paddle.setPosition(e.getX() - paddle.getWidth()/2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
});
}
By making these corrections, your paddle should now move according to the mouse movement.
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Fill in the blank. Do not use abbreviations. What is the missing command on router R2 to establish an adjacency between routers R1 and R3? [blank_start]network 172.16.10.0 0.0.0.255 area 0[blank_end]
Answers
The missing command on router R2 to establish an adjacency between routers R1 and R3 is network 172.16.10.0 0.0.0.255 area 0.
This command is used to advertise the network 172.16.10.0/24 in OSPF area 0, which allows R2 to establish an adjacency with both R1 and R3. The network command is used to specify the networks that should be advertised by OSPF, and the area parameter specifies the OSPF area to which the network belongs.
By advertising the same network in the same area on both R1 and R3, R2 can act as a transit router between them and allow them to communicate with each other.
Learn more about command here:
https://brainly.com/question/14548568
#SPJ11
Instruction The students work in a group and write a report for the given project. (See the team information). Using Matlab or Python to solve the following problems and write a report. The report must have 3 parts: i) The theory and algorithm (as your understanding); ii) The Matlab or Python commands (explain important steps); iii) The results and conclusion. Project 1 Problem 1. Write a program to find the reflection of an polygonal object (for example, input a triangle or a rectangle) in R3 with the standard inner product. about a given plane ax +by+cz = d. Problem 2. Write a program to input any number of vectors in R" and return the orthogonal basis and orthonormal basis of the subspace spanned by these vectors. (Use Gram - Schmidt process) Problem 3. Given a square matrix A that is diagonalizable, find A" using the diagonalization technique. (It isn't allowed to use any direct command of Matlab or Python to find the eigenvalues and eigenvector of A)
Answers
The students are required to write a report for the given project, which includes solving three problems using Matlab or Python, and documenting the theory, algorithm, commands, results, and conclusions for each problem.
What are the three problems that need to be solved in the given project, and what programming language (Matlab or Python) should be used for the implementation?In this project, the students are required to work in a group and write a report. The report should consist of three parts:
i) The theory and algorithm: Explain the theoretical background and algorithm for each problem, demonstrating a clear understanding of the concepts involved.
ii) The Matlab or Python commands: Provide the commands used in Matlab or Python to solve each problem. Explain the important steps in the implementation of the algorithms.
iii) The results and conclusion: Present the results obtained from running the program on different inputs. Discuss the implications of the results and draw conclusions based on the findings.
Project 1 - Problem 1: Reflection of a polygonal object in R3
- Explain the theory and algorithm for reflecting a polygonal object in R3 about a given plane ax + by + cz = d.
- Present the Matlab or Python commands used to implement the algorithm.
- Discuss the results obtained and draw conclusions.
Project 1 - Problem 2: Orthogonal and orthonormal basis of a subspace
- Explain the theory and algorithm for finding the orthogonal and orthonormal basis of a subspace spanned by given vectors in Rn using the Gram-Schmidt process.
- Provide the Matlab or Python commands used for the implementation.
- Discuss the results obtained and draw conclusions.
Project 1 - Problem 3: Diagonalization of a square matrix
- Explain the theory and algorithm for finding the diagonal matrix A' of a square matrix A that is diagonalizable.
- Present the Matlab or Python commands used to implement the diagonalization technique.
- Discuss the results obtained and draw conclusions.
Learn more about includes solving
brainly.com/question/32688993
#SPJ11
consider a full-duplex 256 kbps satellite link with a 240 millisecond end-to-end delay. the data frames carry a useful payload of size 12,000 bits. assume that both ack and data frames have 320 bits of header information, and that ack frames carry no data. what is the effective data throughput: when using stop and wait?
Answers
The effective data throughput when using Stop-and-wait is 41621.05 bits/s.
In order to calculate the effective data throughput when using stop and wait, first, the total time required to transmit one frame must be calculated.
Data rate of satellite link = 256 kbps Payload size = 12,000 bits.
Header information in both data and ACK frames = 320 bits
End-to-end delay = 240 milliseconds
= 240 x \(10^-3\) seconds.
Total number of bits in one frame = Payload + Header
= 12,000 + 320
= 12,320 bits.
Total time required to transmit one frame = Time to transmit payload + Time to transmit header + End-to-end delay.
Time to transmit payload = (Payload size) / (Data rate)
= (12,000) / (256 x 10³)
= 0.046875 seconds
Time to transmit header = (Header size) / (Data rate)
= (320) / (256 x 10³)
= 0.00125 seconds
Total time required to transmit one frame = 0.046875 + 0.00125 + 0.24
= 0.288125 seconds.
Now, the useful data transmitted per unit time must be calculated.
The formula for effective data throughput can now be written as: Effective Data Throughput = Useful data transmitted per unit time / (time required to transmit one frame + time to receive ACK frame).
In the Stop-and-wait protocol, the sender can send only one frame before receiving an ACK. Hence, the useful data transmitted per unit time = Payload size. In addition, since the ACK frames carry no data, the time required to transmit the ACK frame can be neglected.
Therefore, Effective Data Throughput = (Useful data transmitted per unit time) / (Total time required to transmit one frame)
= 12000 bits / 0.288125 seconds
= 41621.05 bits/s.
Therefore, the effective data throughput when using Stop-and-wait is 41621.05 bits/s.
Learn more about data throughput visit:
https://brainly.com/question/30226000
#SPJ11
technical communication includes digital media such as podcasts and online videos.T/F
Answers
Technical communication includes digital media such as podcasts and online videos is true.
What is the technical communication?Technical communication involves diverse types of media, including modern digital forms such as online videos and podcasts. Technical writers employ media to communicate information, instructions, or ideas pertaining to technical subjects.
Podcasts are a type of digital media that use spoken content as a means of sharing information. Various technical subjects can be communicated through them such as interviews, discussions, etc.
Learn more about technical communication from
https://brainly.com/question/14617967
#SPJ4
Define cell in MS-Excel.
Answers
Answer:
The intersection of rows and columns in a worksheet is called a cell
Complete the method/function so that it converts dash/underscore delimited words into camel casing. The first word within the output should be capitalized only if the original word was capitalized. Specifications Challenge.toCamelCase(str) given a string with dashes and underscore, convert to camel case Parameters str: String - String to be converted Return Value String - String without dashes/underscores and camel cased Examples str Return Value "the-stealth-warrior" "theStealthWarrior" "A-B-C" "ABC"
Answers
Answer:
I am writing a Python program. Let me know if you want the program in some other programming language.
def toCamelCase(str):
string = str.replace("-", " ").replace("_", " ")
string = string.split()
if len(str) == 0:
return str
return string[0] + ''.join(i.capitalize() for i in string[1:])
print(toCamelCase("the-stealth-warrior"))
Explanation:
I will explain the code line by line. First line is the definition of toCamelCase() method with str as an argument. str is basically a string of characters that is to be converted to camel casing in this method.
string = str.replace("-", " ").replace("_", " ") . This statement means the underscore or dash in the entire are removed. After removing the dash and underscore in the string (str), the rest of the string is stored in string variable.
Next the string = string.split() uses split() method that splits or breaks the rest of the string in string variable to a list of all words in this variable.
if len(str) == 0 means if the length of the input string is 0 then return str as it is.
If the length of the str string is not 0 then return string[0] + ''.join(i.capitalize() for i in string[1:]) will execute. Lets take an example of a str to show the working of this statement.
Lets say we have str = "the-stealth-warrior". Now after removal of dash in by replace() method the value stored in string variable becomes the stealth warrior. Now the split() method splits this string into list of three words the, stealth, warrior.
Next return string[0] + ''.join(i.capitalize() for i in string[1:]) has string[0] which is the word. Here join() method is used to join all the items or words in the string together.
Now i variable moves through the string from index 1 and onward and keeps capitalizing the first character of the list of every word present in string variable from that index position to the end. capitalize() method is used for this purpose.
So this means first each first character of each word in the string starting from index position 1 to the end of the string is capitalized and then all the items/words in string are joined by join() method. This means the S of stealth and W of warrior are capitalized and joined as StealthWarrior and added to string[0] = the which returns theStealthWarrior in the output.

you select a file that you want to move from its original folder to a new folder. which of the following commands will you choose from the organize menu in this case?
Answers
When you want to move a file from its original folder to a new folder, you would select the "Cut" command from the organize menu.
How can you initiate the file transfer process by utilizing the organize menu?To move a file from its original folder to a new folder, you would select the "Cut" command from the organize menu. This command removes the file from its current location and places it on a clipboard, ready for relocation. After cutting the file, you can navigate to the desired destination folder and use the "Paste" command to complete the transfer.
By doing so, the file is effectively moved from its original folder to the new folder, updating its location in the file system. The "Cut" and "Paste" commands provide a straightforward method for organizing and managing files, allowing you to efficiently arrange your data according to your preferences.
Learn more about command
brainly.com/question/32329589
#SPJ11
Thinking back on Big Data, why would users give up ownership of their data?
Answers
According to the World Economic Forum, this is because individuals find it challenging to possess. It can't be traced or kept an eye on because it's not a tangible object.
What is World Economic Forum?World economic forum is defined as a global non-governmental organization with headquarters in Cologne, canton of Geneva, Switzerland. Klaus Schwab, a German engineer and economist, created it on January 24, 1971.
Your privacy is not yet sufficiently protected by the rights that come with data ownership. Prior to any data collection, a data subject should clearly given the option to decline data transfer, with no impact on their ability to access services. This is necessary to respect their right to privacy.
Thus, according to the World Economic Forum, this is because individuals find it challenging to possess. It can't be traced or kept an eye on because it's not a tangible object.
To learn more about World Economic Forum, refer to the link below:
https://brainly.com/question/29353435
#SPJ1
anyone who like memes? IG= mdkmdk1911
Answers
Answer:
I love them so much, they are the best
12. after converting the erd to a table design, what fields will be present in the contracts table? indicate the primary key of the table by underlining the appropriate field(s).
Answers
The primary key is a candidate key that is selected by the database designer to be used as an identifying mechanism for the whole entity set
What is the main key?The main key is a candidate key chosen by the database designer to serve as the entity set’s identification mechanism. It must not be null and must uniquely identify tuples in a table. In the ER model, the attribute with the primary key is highlighted.
The designer chooses a candidate key to uniquely identify tuples in a table. It cannot be null.
The database designer selects a key to be used as an identifying mechanism for the entire entity set. This is known as the primary key. In the ER model, this key is indicated by underlining the attribute.
To learn more about primary key to refer;
https://brainly.com/question/10167757
#SPJ4
What percentage of cyber stalking cases escalate to real-world violence?
A. 90% or more
B. Less than 1%
C. 25%
D. About 19%
Answers
The percentage of cyber stalking cases escalate to real-world violence is D. About 19%
What is cyber stalking?
The percentage of cyber stalking incidents that lead to physical violence as there are multiple barriers such as scarce data and underreporting. Furthermore, there is a scarcity of research regarding this particular subject matter.
Hence, It is commonly recognized that even though a few instances of cyber stalking could lead to actual violence, the majority of such cases do not end up with physical harm.
Learn more about cyber stalking from
https://brainly.com/question/27995900
#SPJ4
James entered into a public cloud computing arrangement without reviewing the standard contract carefully. What problem is he most likely to face as a result?
a) Unexpected cloud downtime
b) Insufficient storage capacity
c) Inadequate data security
d) Inflexible pricing structure
Answers
Unexpected cloud downtime is the most likely to face as a result.
Thus, A disruption in cloud-based services is known as cloud downtime. The migration of more businesses to the cloud means that any disruption in cloud services might be expensive.
According to Gartner, the average cost of cloud downtime is $300,000 per hour. Major cloud service companies appear to routinely report disruptions. These interruptions can endure for a few hours or several days. Three outages affected AWS in a single month in 2021.
An outage of any length can have a negative impact on the bottom line for businesses that are still working to incorporate cloud technology into their business strategy.
Thus, Unexpected cloud downtime is the most likely to face as a result.
Learn more about Downtime, refer to the link:
https://brainly.com/question/28334501
#SPJ4
Demonstrate an understanding of net neutrality (pages 327-328) and how it affects the home, education, and work environment. Your post should contain a reflection of these topics.
Answers
Net neutrality is a principle of the internet that states that all data transmitted over the internet should be treated equally by Internet Service Providers (ISPs).
The home environment is where the debate around net neutrality began, and it is also the most affected environment. Since the home is where the majority of people access the internet, net neutrality can have a significant impact on their internet experience.
Finally, the work environment has also been affected by the net neutrality debate. Companies that rely on the internet to conduct their business may be affected if net neutrality is not respected.
In conclusion, net neutrality is a crucial principle that must be respected to ensure that the internet remains an open and free space where everyone can communicate with each other.
To know more about debate visit:
https://brainly.com/question/13308791
#SPJ11
write a function called remove duplicates that accepts a list and returns a list containing the same elements in the same order but with duplicates removed. for example, if the argument is [7, 4, 2, 7, 2, 2, 9, 4], the returned list would be [7, 4, 2, 9].
Answers
The function that called remove duplicates that accepts a list and returns a list containing the same elements in the same order but with duplicates removed is def remove_duplicates(lst).
The method of obtaining the unique list from a list that may contain duplicates is the subject of this article. Remove duplicates from list procedure has a wide range of uses, thus understanding it is beneficial.
This is the simplest and quickest way to complete a specific activity. After eliminating the duplicates, it returns a dictionary that must be transformed into a list.
List in the beginning: [1, 2, 4, 2, 1, 4, 5]
[1, 2, 4, 5] is the list after deleting duplicate elements.
Depending on the elements contained in the list, its size, whether or not the element order should be retained, and the effectiveness of the removal method, duplicates can be removed from Python lists using a variety of techniques. These processes might be iterative, implement themselves using built-in functions, or import functionality from modules.
To know more about duplicates click on the link:
https://brainly.com/question/28609285
#SPJ4
what would be needed to implement hard links with consistency in a windows-style file system?
Answers
To implement hard links with consistency in a Windows-style file system, the file system should support features such as reference counting, file system journaling, and proper handling of file metadata.
Hard links are file system links that point to the same physical file on disk, allowing multiple directory entries to refer to the same file. To ensure consistency when implementing hard links in a Windows-style file system, several key factors are needed. First, the file system should support reference counting, where each hard link maintains a count of the number of references to the file. This helps prevent accidental deletion or modification of the file when multiple links exist. Additionally, the file system should employ mechanisms like file system journaling to ensure proper handling of metadata updates and maintain file system integrity. By combining these features, hard links can be implemented with consistency in a Windows-style file system.
Learn more about Hard links here:
https://brainly.com/question/32268391
#SPJ11
state two other ways gaming company cloud use cookie
Answers
Answer:
1. to track user activity
2. to track user preferences
True/False? you use the cars checklist to determine whether a website is current, appealing, relevant, and sophisticated.
Answers
The given statement "you use the cars checklist to determine whether a website is current, appealing, relevant, and sophisticated" is false.
The CARS checklist is a critical assessment tool that examines an article's credibility, reliability, relevance, and support (University of Alberta Libraries, 2017). CARS stand for Credibility, Accuracy, Reasonableness, and Support. It's a checklist designed to help readers assess the quality of a website's information. As a result, the CARS Checklist has nothing to do with the design and appearance of the website.
The CARS Checklist's specific features are:
Currency: The timeliness of the informationAccuracy: The reliability, truthfulness, and correctness of the contentReasonableness: Fairness, objectivity, and absence of biasSupport: The source of the information and the supporting evidence given by the creatorWhen assessing an article or website, the CARS Checklist may help users to distinguish between accurate, reputable, and trustworthy sources and those that are unreliable or lacking in credibility.
You can learn more about the website at: brainly.com/question/2497249
#SPJ11