Which routing protocol is considered a link-state protocol?A. RIPv1B. RIPv2C. EIGRPD. IS-ISE. BGP
Answers
IS-IS (Intermediate System to Intermediate System) is a routing protocol that is regarded as a link-state protocol.
IS-IS, Intermediate System to Intermediate System, is a routing protocol used in computer networking, specifically in Internet Protocol (IP) networks. It was developed by the ISO as a result of their work on the OSI protocol suite.IS-IS is a routing protocol that falls under the link-state category. Link-state protocols keep track of topology changes in the network by exchanging link-state advertisements (LSAs) among routers to form a complete picture of the network. The routing table on each router is then created from these LSAs.BGP (Border Gateway Protocol) is another protocol that is used in the internet to exchange information between autonomous systems.
IS-IS is the correct answer for the question "Which routing protocol is considered a link-state protocol?" and it is classified as a link-state protocol as it employs link-state routing technology to update routing tables.
To know more about protocol visit,
https://brainly.com/question/16224929
#SPJ11
Related Questions
You want to find the distance between two points.
Choose the correct lines of code to finish the task.
Output:
10.0
>>>
>>>


Answers
Answer:
For the first picture, choose the second pair, and for the second one, choose the first pair
Explanation:
Hardware failure, power outages, and DOS attacks will affect:
data confidentiality.
data integrity.
data verification.
data availability.
Answers
Answer:
The answer should be data availability
assignment 2: room area CS python fundamentals project stem
Answers
Answer:
side1 = float(input("Enter side A: "))
side2 = float(input("Enter side B: "))
side3 = float(input("Enter side C: "))
side4 = float(input("Enter side D: "))
side5 = float(input("Enter side E: "))
rect1 = (side1 * side2)
rect2 = (side4 - side2 - side5) * (side1 - side3)
tri = (side1 - side3) * side5 * 0.5
print("Room Area: " + str(rect1+ rect2+tri))
Explanation:
My teacher helped me and I got 100 so just copy and pate this
The template code provided is intended to check whether an integer entered by the user is outside of the range 20-29 (inclusive). If it is outside of this range the program should print a warning and change the number to 25. However, when using De Morgan's law to simplify this code, the programmer has made some mistakes. Can you correct the errors so the code functions as intended? code: Scanner scan = new Scanner(System.In); System.Out.Println("Enter a number in the twenties"); int num = scan.NextInt(); if(num < 20 && num > 30){ System.Out.Println("That's not in the twenties!"); num = 25; } System.Out.Println("Your number is " + num);
Answers
Answer:
Change if(num < 20 && num > 30)
to
if(num < 20 || num > 30)
Explanation:
The code has lots of errors most of which are as a result of case sensitivity of java programming language
The following errors were corrected.
All System.Out.Println were changed to System.out.println
scan.NextInt() was changed to scan.nextInt()
Now to the actual correction that needs to be made;
The programmer's error was in using the conditional statement.
The programmer used if(num < 20 && num > 30) as its condition which means that if num is less tha 20 and at the same time greater than 30
This is impossible because no number is greater than 30 and less than 20 at the same time.
So, the correction made was to change the && (and) to || (or) which means that numbers greater than 30 or less than 20.
This corrects the programmer's mistake
See attachment for complete code
Provide an example by creating a short story or explanation of an instance where availability would be broken.
Answers
Incomplete/Incorrect question:
Provide an example by creating a short story or explanation of an instance where confidentiality would be broken.
Explanation:
Note, the term confidentiality refers to a state or relationship between two parties in which private information is kept secret and not disclosed by those who are part of that relationship. Confidentiality is broken when this restricted information is disclosed to others without the consent of others.
For instance, a Doctor begins to share the health information of a patient (eg a popular celebrity, etc) with others such as his family members and friend
s without the consent of the celebrity.
List two rules of a data protection art.
Answers
Answer:
1 the data must be processed fairly, lawfully and transparently
2 the data must be processed only for specific, explicit and legitimate purposes and shall not be further processed in any manner incompatible with that purpose or those purposes
3 the data must be adequate, relevant, and not excessive in relation to the purpose or purposes for which they are held
Write a for loop to print the numbers from 35 to 45, inclusive (this means it should include
both the 35 and 45). The output should all be written out on the same line.
Expected Output
35 36 37 38 39 40 41 42 43 44 45
Answers
Answer:
for num in range(35, 46):
print(num, end=' ')
or
num = 35
while num <= 45:
print(num, end=' ')
num += 1
escribe un texto argumentativo donde expreses tu opinión acerca del acoso cibernético
Answers
El acoso cibernético es uno de los problemas menos tratados por la sociedad y a la vez uno muy recurrente. Este tipo de acoso rastrea a la persona a través de redes sociales y la investiga con fines degradantes para el afectado, sin embargo, para prevenir este se deben tomar medidas de seguridad como no compartir toda tu vida en el internet y así evitar estos casos que generalmente terminan con abuso sexual o secuestro.
PLEASEEEE THIS IS NEXT PERIOD ,,,,Software providers release software updates on a regular basis. However, most people feel that they are unnecessary. Discuss why it is necessary to apply software updates regularly and how these updates affect the performance of the software programs.
Answers
if you do not update a software the system will not work properly
Answer: all it wants is to you to do is write about why software updates are important. example, because the software has a glitch they need to patch. In the update they patched it.
Explanation: May i plz have brainliest?
wardialers are becoming more frequently used given the rise of voice over ip (voip). (true/false)
Answers
True. Wardialers are automated programs that scan telephone lines looking for modems or other devices that can be used for unauthorized access.
With the rise of Voice over IP (VoIP) technology, more and more phone systems are becoming computer-based, which means they can be vulnerable to wardialing attacks. In fact, many security experts consider wardialing to be a serious threat to VoIP systems, as it can allow hackers to gain unauthorized access to corporate networks and sensitive data.
Wardialers are not becoming more frequently used given the rise of Voice over IP (VoIP). In fact, wardialers, which are tools used to automatically dial a series of phone numbers to find open modems or vulnerable systems, have become less relevant due to advancements in technology and security measures.
To know more about telephone visit:-
https://brainly.com/question/30588697
#SPJ11
Write a program that asks the user for a positive 3-digit number. Then print the number in reverse mathematically
Answers
number = int(input("Enter a positive 3-digit number: "))
firstDigit = number // 100
secondDigit = (number - (firstDigit * 100))//10
lastDigit = number - ((firstDigit * 100) + (secondDigit * 10))
newNum = (lastDigit*100) + (secondDigit*10) + firstDigit
print(newNum)
I think this is what you want
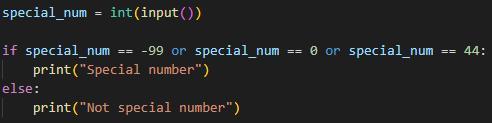
Can you solve this challenging activity?

Answers
Answer:
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
What is the danger of open-source software when it comes to military robotics?
Answers
Answer:
The issue with open source software is that it is usable (and editable) by anyone. When it comes to military robotics, the software that is used to run the robots must remain confidential. If it is not, anyone could take the software that the military is using to make their robots function and replicate it, which could be extremely dangerous.
Explanation:
Open source software is available to the general public.
Feel free to copy and paste this or put it into your own wording. Have a nice day!
You are now going to prepare some reports for the company. Measurements are in metres and volume
n cubic metres. Prices are per cubic metre. Mako sure al currency values are displayed with 2 decimal
places
20 -
Using a suitable database package, import the file M2017BOARDS.CSV
Use these field names and data types:
Field Name Data Type Description/Specification
Board ID
Text
This is a unique identification for each board
Tree_ID
Text
This code identifies the type of tree
Thickness
Numeric
Width
Numeric
Numeric
Length
Drying
Text
Ready
Sold
Boolean/Logical Display as Yes/No or checkbox
Boolean/Logical Display as Yes/No or checkbox
Numeric/Currency Currency of your choice
Price
.
Set the Board_ID field as the primary key.
[3]
Import the file M2017TREES.CSV into your database as a new table with appropriate data
types. Set the Tree_ID field as the primary key.
121
21.
12.
Examine the file M2017LOCATIONS.CSV and decide on appropriate data types for each field
Import the file M2017LOCATIONS.CSV into your database as a new table with appropriate
data types. Set the Location_code field as the primary key.
121
EVIDENCE 4
Place in your Evidence document screenshot(s) showing the field names and data
types used in each of the three tables.
23
Create one-to-many relationships as links between the three tables.
Use the Tree_ID field in the Trees table to link to the Tree_ID field in the Boards table, and
the Location_code field in the Locations table to link to the Location_code field in the Trees
table.
EVIDENCE 5
Place in your Evidence document screenshot(s) showing the relationships between
the three tables.
Answers
if you follow me and like and mark in brainliest answer only I will tell the answer
match the technology term with its definition
Answers
Answer:
there is no picture
Explanation:
You can create a _____ to define what data values are allowed in a cell. Question 5 options: custom error macro conditional formatting rule validation rule
Answers
You can create a "validation rule" to define what data values are allowed in a cell.
A validation rule can be created to define what data values are allowed in a cell. This is done by setting specific criteria that the data must meet, such as numerical values within a certain range or text that matches a specific pattern.
Validation rules are a useful tool for ensuring data accuracy and consistency within a spreadsheet. By defining what data values are allowed in a cell, you can prevent users from entering incorrect or inappropriate data. This can help to minimize errors and make it easier to analyze and interpret data.
To know more about validation rule visit:
https://brainly.com/question/14356883
#SPJ11
An energy source that is bought and sold.
Answers
1.)Name at least five things that are easier to do with fast internet access.
2.)If you had online homework, but did not have a computer, how would you go about completing this homework?
3.)If you needed a job and wanted to find places that were hiring, how could you do that without fast internet access?
4.)What do you think could be done to close the digital divide gap?
Can anyone help me please hurry
Answers
Answer:
#1) use streaming applications
Use on-demand applications
work from home
take an online course for personal or career-growth
Everyone in your family can be online at the same time
#2) Go to the library and use one of theirs or go to a friends house that does have access
#3) Either look in the classified ads of the newspaper or go to someplace that has fast internet like mcdonalds
#4) Make internet more affordable with better availability
Explanation:
The things that are easier to do with fast internet access include:
Using on-demand applications.Downloading movies.Streaming videos and songs.Watching a video online.Browsing on a computer system.If I have online homework, but there's no computer, in order to complete this homework, I'll go to the library or cafe.
If I needed a job and wanted to find places that were hiring, since there's no fast internet access, I'll look for advertisements in newspapers or magazines. I can also go to areas that have free and fast connections.
In order to close the digital divide gap, people should be taught about the importance of computer systems and the internet should be more affordable to people.
Read related link on:
https://brainly.com/question/9914557
((GUITAR))
What is the letter name for the note shown above?
D
E
F
G

Answers
Explanation: Took Guitar classes as a kid and memorized the letters.
Write a program that first reads a list of 5 integers from input. then, read another value from the input, and output all integers less than or equal to that last value
Answers
Answer:
integers = [int(i) for i in input().split()]
value = int(input())
for integer in integers:
--if integer <= value:
----print(integer)
Explanation:
We first read the five integers in a string. We can use the .split() method, which splits the string into separate parts on each space.
For example:
print(input())
>> "4 -5 2 3 12"
print(input().split())
>> ["4", "-5", "2", "3", "12"]
We cannot work with these numbers if they are strings, so we can turn them into integers using the int constructor. An easy way to do this is with list comprehension.
print([int(i) for i in input().split()]
>> [4, -5, 2, 3, 12]
Now that all the values in the list are integers, we can use a for loop to get each of the values and check whether they are less than or equal to the value.
Let's first get the value from the input.
integers = [int(i) for i in input().split()]
value = int(input())
print(value)
>> 4
Here, we have to pass the input through the int constructor to be able to compare it with the other integers. Let's now make a for loop to go through each integer and check if the integer is less than or equal to value.
for integer in integers:
--if integer <= value:
----print(integer)
The dashes are there to show indentation and are not part of the code.
lans form the building blocks for larger networks called internetworks.
Answers
Th statement "LANs form the building blocks for larger networks known as internetworks." is true.
1. A LAN, or Local Area Network, refers to a network infrastructure that interconnects devices within a limited geographic area, such as an office building or a school campus.
2. LANs serve as the foundation for constructing larger networks called internetworks, which are also known as wide area networks (WANs). Internetworks connect multiple LANs or other networks together, allowing for communication and data exchange across a broader geographical scope.
3. Internetworks facilitate the integration of diverse LANs into a cohesive network system, enabling seamless communication and resource sharing between different local networks.
4. By linking LANs together, internetworks enable organizations to establish efficient and scalable networks that can span across multiple locations, connecting employees, devices, and resources regardless of their physical proximity.
5. Internetworking technologies, such as routers, switches, and protocols like TCP/IP, play a crucial role in ensuring the smooth operation and interconnectivity of LANs within internetworks.
Learn more about internetworks:
https://brainly.com/question/12972464
#SPJ11
"3.24.2 Make Button"
Does anyone have the script for CodeHS Make Button? It may be different for you but mines is 3.24.2.
(I had to change some things so it all could fit)
Heres my code so far:
html
head
style
#textbox{
margin: 10px;
border: 1px solid black;
height: 200px;
}
style
head
body
div id = 'keyBoard'>
div
div id = 'textbox'>
div
body
script
//create function makeButton
//call makeButton twice to test.
script
html
Answers
Attached is an example code for creating a button using JavaScript in HTML, which you can use as a reference for your Make Button CodeHS exercise:
What is the script about?This code creates two buttons with IDs "button1" and "button2", and adds click event listeners to them using addEventListener(). When the buttons are clicked, the event listener functions set the content of the #textbox element to a message indicating which button was clicked.
Therefore, You can copy this code and modify it to meet the requirements of your Make Button CodeHS exercise.
Read more about script here:
https://brainly.com/question/26121358
#SPJ1
you work as a system administrator for a midsize organization. recently, some systems of your company had fallen a victim to a boot attack. although y
Answers
As a system administrator for a midsize organization, you have an important responsibility of maintaining the security and integrity of your company’s systems.
It’s crucial to take prompt action when your systems become vulnerable to cyber-attacks such as boot attacks.In the case of a boot attack, an attacker gains access to a system by exploiting vulnerabilities in the boot process of a computer system. There are different types of boot attacks such as bootkits, rootkits, and boot viruses. These attacks can cause damage to your systems by stealing sensitive information, disrupting business operations, and even rendering the system unusable.In order to prevent boot attacks, it’s important to take appropriate measures such as installing anti-malware software, keeping your operating system and software up-to-date with the latest security patches, and using a strong and unique password for each system. It’s also important to regularly monitor your systems for any unusual activity or unauthorized access. It’s important to take prompt action when a system becomes vulnerable to cyber-attacks such as boot attacks. The first step is to isolate the affected system from the network to prevent the spread of the attack. Then, you can use an anti-malware software to scan and remove any malware that may be present on the system. It’s important to ensure that the anti-malware software is up-to-date with the latest security definitions to effectively detect and remove any malicious software.Next, you should investigate the source of the attack to identify any vulnerabilities that may have been exploited and take appropriate measures to patch them. It’s important to keep your operating system and software up-to-date with the latest security patches to prevent any known vulnerabilities from being exploited.
In conclusion, boot attacks can cause significant damage to your systems and compromise the security of your organization. As a system administrator, it’s important to take proactive measures to prevent boot attacks and respond quickly when they occur. By implementing security best practices such as installing anti-malware software, keeping your software up-to-date, and monitoring your systems for any unusual activity, you can help protect your organization from cyber-attacks.
To learn more about system administrator visit:
brainly.com/question/30456614
#SPJ11
PLZ HELPP ME!!!
You are driving on a highway and your gas pedal gets jammed. You cannot reduce engine
power. You should keep your eyes on the road and
A: Stay in the gear you are in. Turn off the ignition, and remove the ignition key from the lock.
B: Shift into neutral. Then turn off the ignition without locking the steering, and use your brakes to
stop.
C: Shift your vehicle into top gear. Then apply the parking brake as hard as you can
Answers
Answer:
b
Explanation:
shift to neutral then use brakes
In pedal gets jammed, Shift into neutral. Then turn off the ignition without locking the steering, and use your brakes to stop.
What to do in the above case?If the vehicle that is its accelerator pedal is said to be stuck in case a person is driving, one can press the brake and also put their hands on the wheel and then shift the gear to neutral.
Conclusively, When your gas pedal gets jammed, by doing the above that is shifting your gear into neutral and turning off the ignition without locking the steering, one can use the brakes to come to a stable halt.
Learn more about highway from
https://brainly.com/question/2919240
#SPJ2
Whats the formatting of a letter to the editor?
Answers
Answer:
Date: Make sure to write the date below the sender's address excluding one space or line. Receiving Editor's address: You should mention the address of the recipient that is the editor's address. The Subject of the letter: It must convey the main purpose of the letter to the readers.
Explanation:
Hope this will help
Hurry answerrrrrrr pleaseee
Select the correct answer
Rick is teaching a photography workshop about design and color in an image. He shows the students a few images to teach them about
contrast. Which is the correct way to show color contrast?
A bright colors against bright surroundings
О В.
bright colors against dull surroundings
dull colors against dull surroundings
D.
dull colors against white-colored surroundings
Answers
Answer:
bright colors against dull surroundings im pretty sure
Explanation:
Answer:c
Explanation:
Do you believe the claims made in advertisements in the media? Give some examples of situations where you think media messages may be biased. Perform online research for solutions that will enable people to protect themselves from undue influences in the media. Describe any one such solution and provide a short outline of its proposals.
Answers
Sometimes I do believe the claims made in advertisements in the media because they may be true.
Can we trust social media as a news source for advertisements?The Reliability of news on social media is one that is often question daily.
Note that a lot of People do say that great power is as a result of great responsibility and as such, a lot of people who shared things do not know if they are facts.
An advert is one that is aimed at communicating a given message to the people about a particular product or services.
Hence, Sometimes I do believe the claims made in advertisements in the media because they may be true.
Learn more about advertisements from
https://brainly.com/question/1658517
#SPJ1
How do people get in your computer
Answers
Answer:
????
Explanation:
This is absurd, you cannot enter your computer. it is to tiny for you to fit in.
Answer:
Explanation:
I don’t know
What is the goal of destroying CUI?A. Make it unreadableB. Make it indecipherableC. Make it unrecoverableD. All of the above - Correct AnswerE. None of the above
Answers
The goal of destroying CUI is typically to make it unrecoverable, meaning that the information is permanently deleted or destroyed in a way that it cannot be reconstructed or retrieved.
What is CUI?
CUI stands for Controlled Unclassified Information, which refers to unclassified information that is sensitive and requires protection.
The goal of destroying CUI is typically to make it unrecoverable, meaning that the information is permanently deleted, destroyed in a way that it cannot be reconstructed or retrieved once deleted or destroyed.
This is usually done to prevent unauthorized access or disclosure of sensitive information. Therefore, the correct answer is C) Make it unrecoverable.
Controlled Unclassified Information (CUI) is unclassified information that requires safeguarding or dissemination controls and is governed by specific laws, regulations, and policies to protect it from unauthorized access or disclosure.
To know more about CUI, visit: https://brainly.com/question/29626718
#SPJ4