Which of the following statements is true about dictionaries?
A) Dictionary keys are immutable.
B) It is not possible to update the entries of a dictionary.
C) Keys can change, but values cannot.
D) One key can correspond to more than one value
Answers
The statement that is true about dictionaries is option A) Dictionary keys are immutable.
Do dictionaries change or remain the same?A dictionary is a changeable, unordered Python container used to store mappings between distinct keys and values. Curly brackets () are used for dictionaries, as well as key-value pairs with commas between them (,).
Note that A dictionary's keys cannot be accessed using its values, but its values can be obtained using its keys. Since dictionaries themselves are mutable, entries can always be added, deleted, or modified.
Therefore, an immutable type must be used for a dictionary key. An integer, float, text, or Boolean value, for instance, can be used as a dictionary key. However, since dictionaries and lists are both mutable, neither one can act as a dictionary key for the other.
Learn more about dictionaries from
https://brainly.com/question/896784
#SPJ1
Related Questions
When you touch a warm picnic table , your hand becomes warmer. Explain how energy conservation applies to this situation
Answers
When you contact a warm picnic table, this transfer occurs because your hand has a lower surface temperature than the table, which allows the heat to pass from the table to your hand. You can see how this procedure conserves energy.
Why should we conserve energy?Energy conservation is essential for limiting climate change. It helps to replace non-renewable resources with renewable energy. When there are energy shortages, energy saving is frequently more cost-effective and environmentally friendly than increasing energy output.
What kind of energy is that?There are numerous shapes that energy can take. Examples of these energies include gravitational energy, mechanical energy, electrical energy, sound energy, chemical energy, nuclear or atomic energy, light energy, heat energy, and so on.
To know more about conserves energy visit:-
https://brainly.com/question/13949051
#SPJ1
your computer appears to be correctly configured but the device or resource is not responding
Answers
Answer:
Oh no! You'll probably have to contact your teacher for help.
Explanation:
what is the full form of COF ?
Answers
Answer:
COF - Central Operations Facility
Explanation:
COF - Central Operations Facility
Answer:
Central Operations Facility
Explanation:
COF is a place where all facilities usually come from. COF is the biggest facility industry in the world. Nevertheless, it needs other industry to rely on.
Hopefully this answer helps you :)
Choose the term that best completes each sentence.
abstraction hides the details about a specific piece of information.
abstraction hides the details about a specific process.
data
procedural
Answers
Answer:
The answer to the above questions is given in explanation section:
Explanation:
abstraction hides the details about a specific piece of information.
The suitable match for this is Data
Because the word "Piece of information " can only be referred to data not to process.
Now look at the second
abstraction hides the details about a specific process
The suitable match here is procedural.
because specific process can only be referred to procedure not to data.
Answer:
The suitable match for this is Data
Because the word "Piece of information " can only be referred to data not to process.
Now look at the second
abstraction hides the details about a specific process
The suitable match here is procedural.
because specific process can only be referred to procedure not to data.
True or false
A compiler translates a source program one line of code at a time.
Answers
Answer:
True
Explanation:
yes It translates one line at a time to be able to confirm all information.
Answer:
True
Explanation:
I hope this helps you
Why are Quick Parts useful in an Outlook message?
Spreadsheet data sources can be hyperlinked to an email message.
Stored text and graphics can be quickly inserted into an email message.
A gallery of shapes will open up, and you can quickly choose one to insert.
Highlighted parts of Word documents can be inserted into a message body.
Answers
Answer:
I hope the picture helped

Answer:
B. stored text and graphics can be quickly inserted into an email message
Explanation:
Edge 2021
Collection Agency A retains 30 percent of the $6,000 it collects and Collection Agency B retains 10 percent of the $20,000 it collects. Which collection agency retains more money
Answers
Collection Agency B retains more money in this scenario
When comparing the two collection agencies, it's important to consider the percentage of the amount collected that they retain as their fee.
Collection Agency A keeps 30 percent of the $6,000 it collects, which equals $1,800. On the other hand, Collection Agency B retains 10 percent of the $20,000 it collects, which equals $2,000.
Therefore, Collection Agency B retains more money in this scenario. While the total amount collected by Collection Agency A may be smaller, they also charge a lower percentage fee, resulting in a lower amount retained.
It's essential to evaluate the fees charged by collection agencies when deciding which one to work with, as this can greatly impact the amount of money you ultimately receive.
Learn more about percentage at
https://brainly.com/question/29306119
#SPJ11
upon complete the step-3, type a tcp command (?) to show how many ips and their corresponding mac addresses of other nodes are fond at your pc?
Answers
An effective way to check the IP and MAC addresses of other devices connected to your network is by utilizing the "arp" command in TCP/IP.
What happens to the PC after the command is entered?By entering "arp -a" in a command prompt or terminal, you can access the ARP (Address Resolution Protocol) table that documents the IP addresses and correlated MAC addresses of all devices which have exchanged data with your computer.
It should be noted that the exact command and outcome may differ based on your network setting and the operating system you are using.
Read more about network configuration here:
https://brainly.com/question/29765414
#SPJ1
Which of the following is NOT TRUE about the information stored in a column-family database?
a) Column families are organized so that all information about each new record is stored close by on disk
b) Column family databases, like document databases, do not require all columns in all rows, making it flexible.
c) Column families are organized into groups of data items that are frequently used together.
d) Both column family databases and relational databases use unique identifiers for rows of data
Answers
The statement that is NOT TRUE about the information stored in a column-family database is (a) Column families are organized so that all information about each new record is stored close by on disk.
Relational databases use unique identifiers for rows of data, column-family databases use a different approach. In a column-family database, the row key is used to uniquely identify a row of data, while the column name identifies a specific column within the row. This allows for fast data access and retrieval.
Column family databases, like document databases, do not require all columns in all rows, making it flexible. This means that columns can be added or removed without affecting the entire database. Column families in a column-family database are organized into groups of data items that are frequently used together.
To know more about database visit:
https://brainly.com/question/30634903
#SPJ11
Using the flowchart below, what value when entered for Y will generate a mathematical error and prevent our flowchart from being completely executed? 3 0 1 None of these values will produce a mathematical error

Answers
Answer:
The answer is the last choice that is "None of these values will produce a mathematical error".
Explanation:
In this question, the above given choice correct because neither of the flowchart procedures could trigger a mathematical error. This error could not be induced by multiplication, addition and subtraction, and the only division by 15. It is the only divide by 0, that's why the above flowchart will produce a mathematical error.
the cost to ship a package is a flat fee of 75 cents plus 25 cents per pound. 1. declare a const named cents per pound and initialize with 25. 2. get the shipping weight from user input storing the weight into shipweightpounds. (remember %d is used to read in an integer from the user.) 3. using flat fee cents and cents per pound constants, assign shipcostcents with the cost of shipping a package weighing shipweightpounds. c programming
Answers
The price of shipping a package containing c programming that weighs shipweight pounds
const int CENTS_PER_POUND = 25;
int shipweight pounds;
printf ("Enter the shipping weight in pounds: ");
scanf ("%d", &shipweigh tpounds);
int shipcostcents = 75 + (shipweight pounds * CENTS_PER_POUND);
What is weight?It is a measurement of the heaviness of an object, and is determined by the gravitational pull of the Earth or other celestial objects on the object. Weight is measured in Newtons, kilograms, and pounds, depending on the system of measurement used. Weight is affected by the mass of the object, its location in the universe, and the gravitational pull of the Earth or other celestial bodies on the object.
To learn more about weight
https://brainly.com/question/28800918
#SPJ4
An object migration package is being imported. What must be selected in order to determine what will change in the system interface that is being importing into?A. "Include System and Object Data"B. "Include Object Data Only"C. "Include System Data Only"D. "Exclude System and Object Data"
Answers
To determine what will change in the system interface during the import of an object migration package, you should select option B. "Include Object Data Only". This will allow you to focus on the changes related to the objects being imported, without including system data that may not be relevant to the interface changes.
In order to determine what will change in the system interface being imported into when an object migration package is being imported, the option "Include Object Data Only" must be selected.
This will ensure that only the object data, which includes the changes made to the system interface, will be included in the import process. Selecting "Include System and Object Data" would import all system data along with the object data, which may not be necessary or desirable. "Include System Data Only" would only import system data and not the object data, which would not provide any information on the changes to the system interface. "Exclude System and Object Data" would not import anything at all.
Learn More about migration here :-
https://brainly.com/question/27938333
#SPJ11
why are my texts green when sending to another iphone
Answers
When you send a text message to another iPhone, the message bubble color can either be green or blue. The color of the bubble depends on the type of message you are sending and the recipient's device settings. If your text message bubble is green, it means that you are sending a traditional SMS text message rather than an iMessage.
This can happen when the recipient does not have an iPhone or has iMessage turned off on their device. When you send an SMS message, it is sent through your cellular network rather than through the internet. This can also result in additional charges if you are not on an unlimited texting plan. On the other hand, if your message bubble is blue, it means that you are sending an iMessage. iMessage is Apple's messaging service that allows you to send texts, photos, videos, and more through Wi-Fi or cellular data. This can be a convenient way to communicate with other iPhone users without incurring additional charges.
To ensure that your messages are sent as iMessages, make sure that the recipient has an iPhone and iMessage turned on in their device settings. You can also check your own settings to see if you have iMessage enabled. In conclusion, if your texts are green when sending to another iPhone, it means that you are sending an SMS message rather than an iMessage. This can happen if the recipient does not have an iPhone or has iMessage turned off. Make sure to check your settings and the recipient's settings to ensure that your messages are sent through iMessage.
Learn more about Wi-Fi here-
https://brainly.com/question/31457622
#SPJ11
A tornado destroyed many
CORRECT ANSWER GETS BRAINLIEST PLEASE HELP !
structures in a small Texas
town. Which type of engineer should be called in to collect
evidence in order to prevent this level of damage in the future?
A.chemical engineer
B.biomedical engineer
C.materials engineer
D.forensic engineer
Answers
Answer:
D is your answer because I'm an expert
Answer:
D. forensic engineer
Explanation:
Because I know the answer I got it right
ill give brainliest whoever does this fsteset.
an array has been created which stores names. write an algorithm which saves each name on a new line in a text file called student.txt.
names["jane", "Humayun" , "Cora" , " Astrid" , "Goran"]
Answers
The algorithm which saves each name on a new line in a text file called student.txt is given as follows:
names = ["jane", "Humayun", "Cora", "Astrid", "Goran"]
with open("student.txt", "w") as file:
for name in names:
file.write(name + "\n")
What is the rationale for the above response?Open the file student.txt in write mode.
Loop through each name in the array names:
a. Write the current name to the file followed by a newline character.
Close the file.
This will create a new text file called student.txt (or overwrite it if it already exists) and write each name from the names array on a new line in the file. The "\n" character at the end of each name ensures that each name is written to a new line in the file.
Learn more about algorithm at:
https://brainly.com/question/22984934
#SPJ1
Does anyone know the answer for 4.2 Code Practice: Question 1 on edhesive
Answers
Answer:
Question 1
sum=0
count=0
while(sum<=100):
x=int(input("Enter a nmber"))
sum=sum+x
count=count+1
print("Sum: "+str(sum))
print("Numbers Entered: "+str(count))
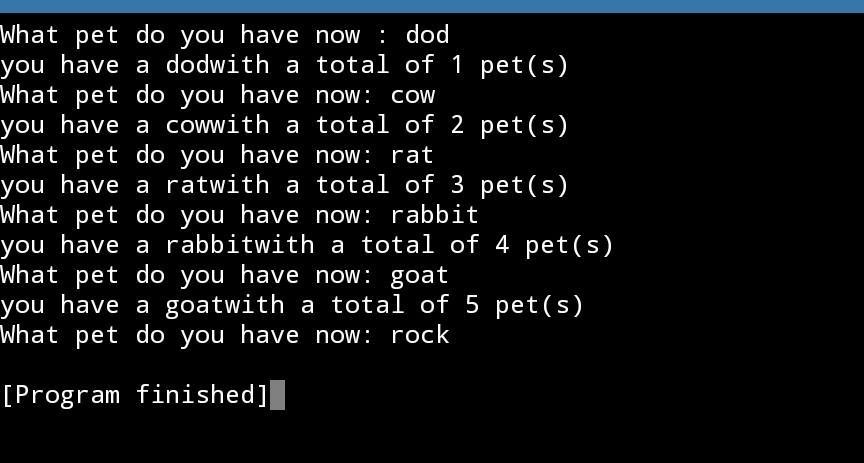
Question 2
count = 0
pet = (input("What pet do you have? "))
while(pet != "rock"):
count = count +1
print("You have a " + pet +" with a total of " + str(count) + " pet(s)")
pet = (input("What pet do you have? "))
Explanation:
The required program written in python 3 which continues to request user to input a pet name until a rock is entered is as follows :
pet = input('What pet do you have now : ')
#request an input from the user and store in the variable pet
total = 0
#initialize the total number of pets owned to 0
while (pet != 'rock'):
#while loop ensures that program runs until a rock is inputted by the user
total +=1
#adds one to the total after each loop
print('you have a ' + str(pet) + 'with a total of ' + str(total) + ' pet(s)')
#displays the formatted string using the total and pet variables which continues to update
pet = input('What pet do you have now: ')
#requests user to input pet name again as long as rock has not been supplied.
Therefore, an output of the program written is attached below.
Learn more on python programs :https://brainly.com/question/18685986
What is plagiarism give 5 examples?
Answers
Answer:
It's when you steal part of a person's work and mix into yours so no one will notice, getting credit for what they have invented or come up with.
Explanation:
Example:
Original song: Under Pressure (♫tututu tududutu, tututu tududutu♫)
Plagiarized song: Ice Ice Baby (♫tututu tududutu, tutututu tududutu♫)
As you can see they are almost 100% identical except ice ice baby has one "tu" plus, so Vanilla Ice can try to get away with this shameful behavior by saying they are not identical.
_______ can be used to flood a Web site with so much traffic that it can no longer provide its intended service.A. DDoSB. An AES service attackC. A Floodping attackD. All of the above
Answers
DDoS can be used to flood a Web site with so much traffic that it can no longer provide its intended service.
DDoS Attack means "Distributed Denial-of-Service (DDoS) Attack" and it is a cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites.Motivations for carrying out a DDoS vary widely, as do the types of individuals and organizations eager to perpetrate this form of cyberattack. Some attacks are carried out by disgruntled individuals and hacktivists wanting to take down a company's servers simply to make a statement, have fun by exploiting cyber weakness, or express disapproval.Other distributed denial-of-service attacks are financially motivated, such as a competitor disrupting or shutting down another business's online operations to steal business away in the meantime. Others involve extortion, in which perpetrators attack a company and install hostageware or ransomware on their servers, then force them to pay a large financial sum for the damage to be reversed.To know more about cyberattacks visit:
https://brainly.com/question/15051205
#SPJ4
Suppose an object-relational mapping (ORM) library syncs a database from source code models. What is an advantage of supporting migrations of existing tables? Select the correct answer: To allow additional constraints on the tables To guarantee test database schemas match the production schema To populate test fixtures Faster creation of test databases Select your answer
Answers
An advantage of supporting migrations of existing tables is that it allows for faster creation of test databases. The object-relational mapping (ORM) library can sync a database from source code models, making it possible to create new tables and modify existing tables according to changes in the source code.
However, when changes are made to the schema of an existing table, it can be difficult and time-consuming to recreate the test database from scratch. This is where supporting migrations can be useful, as it allows the ORM library to modify the existing table schema in place, rather than creating a new table. This can significantly reduce the time and effort required to create and maintain test databases.
Other benefits of supporting migrations may include:Allowing additional constraints on the tables: By modifying the table schema, it may be possible to add additional constraints or rules to enforce data integrity.Guaranteeing test database schemas match the production schema: By syncing the test database with the production database, it ensures that the test data accurately reflects the state of the production data.Enabling easier rollback of changes:
To know more about library visit:
https://brainly.com/question/31630680
#SPJ11
What are the three computer components that hold a dangerous amounts of electricity? Even when it’s unplugged.
Answers
The components of a computer that hold a dangerous amount of energy even when it's unplugged are capacitors, and inductor.
What is electricity?Electricity is the flow of charges in a closed system. Electricity is very important to run electronic devices, but electricity can damage the tissues of human body and cause heart attack if touch it with hands.
Thus, the components of a computer that hold a dangerous amount of energy even when it's unplugged are capacitors, and inductor.
Learn more about electricity
https://brainly.com/question/12791045
#SPJ1
Helppp me eeeeee eee

Answers
Answer:
a. taking risks
Explanation:
i hope this helps
Answer:
Most likely taking risks...but that is my opinion
Explanation:
hope I helped :]
_____ is the process of using procedures from statistics and computer science to extract useful information from extremely large databases
Answers
The process of using procedures from statistics and computer science to extract useful information from extremely large databases is called data mining.
Data mining is the process of utilizing techniques from statistics and computer science to extract valuable insights and knowledge from vast and complex databases. It involves applying various algorithms, statistical models, and machine learning methods to discover patterns, relationships, and trends within the data. By examining large datasets, data mining aims to uncover hidden patterns, identify anomalies, and generate predictive models for decision-making and future forecasting. This iterative process involves data preprocessing, exploratory analysis, model building, and result interpretation. Data mining plays a crucial role in areas such as business intelligence, customer segmentation, fraud detection, market analysis, and personalized recommendations, enabling organizations to derive actionable insights from their data.
learn more about procedures here :
https://brainly.com/question/27176982
#SPJ11
Your IT department would like to outsource the "service desk function" to a third-party service provider. The third-party service provider will have to provide 24/365 (hours/days) service for your global organization with offices in North America, Asia, Europe, Australia, and the Middle East. What service desk organization structure will you pick for this outsourced initiative, and how does it add value to the business? (You may consider hybrid architectures if you wish). Briefly describe a challenge you will face with a technology (technological management function) and a challenge with staffing roles involved with this outsource service during operation.
Furthermore, your IT department has decided to implement a custom application for the service desk staff to use to service global clients. Briefly describe what role application management and application development processes play in this custom application. List three (3) potential requirements you may want to include in your "Follow the Sun" SLA. Keep in mind that all offices may not use the same technology and do not speak the same language.
Answers
When outsourcing the service desk function to a third-party service provider, a suitable service desk organization structure would be a follow-the-sun model.
This model ensures 24/365 service coverage by establishing multiple service desk teams across different time zones. For example, you could have a service desk team in North America, another in Europe, and a third in Asia. This structure adds value to the business by providing round-the-clock support to global offices, reducing downtime, and improving customer satisfaction.
By including these requirements in the SLA, the business can ensure timely and effective support, language accessibility, and technical expertise for all global offices, thereby enhancing the overall service quality.
To know more about outsourcing visit:
https://brainly.com/question/32678766
#SPJ11
What Is Better, A GTX 1660 Or Radeon Rx 5500XT
Answers
Answer:
I say Radeon Rx 5500XT
Explanation:
30 pts!
Explain how Moore's law presumes everyone will have access to the Internet.
Answers
Answer:
Moore's law predicts that this trend will continue into the foreseeable future.
Explanation:
Moore's Law refers to Moore's perception that the number of transistors on a microchip doubles every two years, though the cost of computers is halved.
when using the command line tool tcpdump, the -x switch displays only the hex portion of the packets?
Answers
False, when using the command line tool tcpdump, the -x switch displays both the hex portion and the ASCII representation of the packets.
When running tcpdump with the -x switch, it displays both the hex portion and the ASCII representation of the packets. The -x option provides a detailed view of the packet contents in hexadecimal format, followed by the corresponding ASCII representation.
The hexadecimal representation shows the raw binary data of the packets, displaying the individual bytes in a readable format. The ASCII representation, which is displayed alongside the hex portion, shows the corresponding characters or symbols for each byte, making it easier to interpret the packet data.
By including both the hex portion and the ASCII representation, tcpdump offers a comprehensive view of the packet contents, allowing users to analyze the data and understand the communication happening over the network. This information can be valuable for network troubleshooting, protocol analysis, and security investigations, as it provides insights into the structure and content of network packets.
Learn more about ASCII here:
https://brainly.com/question/30399752
#SPJ11
you need to create a report to display the names of customers with a credit limit greater than the average credit limit of all customers. which select statement should you use? a. select last name, first name from customer where credit limit > avg(credit limit); b. select last name, first name, avg(credit limit) from customer group by avg(credit limit); c. select last name, first name, avg(credit limit) from customer group by avg(credit limit) having credit limit > avg(credit limit); d. select last name, first name from customer where credit limit > (select avg(credit limit) from customer); e. select last name, first name from customer where credit limit
Answers
The correct select statement to display the names of customers with a credit limit greater than the average credit limit of all customers is option (d): "select last name, first name from a customer where credit limit > (select avg(credit limit) from customer);".
This statement uses a subquery to calculate the average credit limit of all customers and then compares each customer's credit limit with the average using the "where" clause. Option (a) is incorrect because it does not calculate the average credit limit of all customers, but rather the average credit limit of only the customers who meet the condition. Option (b) is incorrect because it includes the average credit limit in the output, which is not necessary for the report. Option (c) is incorrect because the "having" clause is used to filter groups based on a condition, not individual rows. Option (e) is incorrect because it does not compare the credit limit with the average credit limit.
Find out more about subquery
brainly.com/question/29575628
#SPJ4
The speed of mainfarme computer is measured in...... fill in the blanks
Answers
Explanation:
Mainframe computers are huge towering machines with lots of processing power and are measured in MIPS (Million Instructions Per Second).3 days
give several examples where you need to use clustering instead of classification in business. what do you think the issues are in clustering algorithms? e.g., are they difficult to validate?
Answers
Classification techniques include support vector machines, naive bayes classifiers, and logistic regression. The k-means clustering algorithm, the Gaussian (EM) clustering algorithm, and others are instances of clustering.
Two methods of pattern recognition used in machine learning are classification and clustering. Although there are some parallels between the two processes, clustering discovers similarities between things and groups them according to those features that set them apart from other groups of objects, whereas classification employs predetermined classes to which objects are assigned. "Clusters" are the name for these collections.
Clustering is framed in unsupervised learning in the context of machine learning, a branch of artificial intelligence. For this kind of algorithm, we only have one set of unlabeled input data, about which we must acquire knowledge without knowing what the outcome will be.
Know more about machine learning here:
https://brainly.com/question/16042499
#SPJ4
http requests and responses answer the following questions about the http request and response process: what type of architecture does the http request and response process occur in? what are the parts of an http request? which part of an http request is optional? what are the three parts of an http response? which status-code number class represents errors? what are the two most common request methods for a security professional to encounter? which type of http request method is used to send data? which part of an http request contains the data being sent to the server? in which part of an http response does the browser receive the web code to generate and style a webpage? using curl answer the following questions about curl: what are the advantages of using curl over the browser? which curl option changes the request method? which curl option sets request headers? which curl option is used to view the response header? which request method might an attacker use to figure out what http requests an http server will accept? sessions and cookies recall that http servers need to be able to recognize and distinguish clients from one another. they do this through sessions and cookies. answer the following questions about sessions and cookies:
Answers
The client-server architecture is used for the HTTP request and response processes. Server-client architecture with regard to client-server architecture. Client-server architecture is used in the HTTP protocol.
How is the HTTP request and response process carried out in terms of architecture?The HTTP protocol is a client/server-based request/response protocol used by web browsers, robots, search engines, etc.
What happens during an HTTP request?A client sends an HTTP request to a named host that is on a server. The request is made in order to access a server resource. A URL (Uniform Resource Locator), which contains the data required to access the resource, is used by the client to submit the request.
To know more about HTTP visit:-
https://brainly.com/question/30175056
#SPJ4