What type of data is INTEGER?
Answers
Related Questions
when they are supported, run __________ from the hard drive or usb key since they are very robust and include more comprehensive tests.
Answers
When they are supported, run full system diagnostic tools from the hard drive or USB key since they are very robust and include more comprehensive tests.
1. When it comes to diagnosing hardware issues on a computer system, utilizing full system diagnostic tools is highly recommended. These tools are designed to thoroughly test various components of the system and provide a comprehensive analysis of their functionality. Running these tools from the hard drive or a USB key offers several advantages.
2. Firstly, full system diagnostic tools are known for their robustness. They are specifically developed to perform extensive tests on hardware components such as the CPU, memory, storage devices, graphics card, and more. By running them from the hard drive or a USB key, you ensure that the diagnostic tools have direct access to the system resources without any limitations or dependencies on the operating system or other software.
3. Secondly, full system diagnostic tools provide a wide range of tests that cover different aspects of the computer system. These tests include stress tests, temperature monitoring, benchmarking, error checking, and performance analysis. By running these comprehensive tests, you can identify potential issues such as faulty hardware, overheating, instability, or performance bottlenecks.
4. Running the diagnostic tools from the hard drive or USB key also offers the advantage of convenience and portability. You can have the diagnostic tools readily available on a bootable USB drive or stored on the hard drive, making it easy to access them whenever needed.
To learn more about hard drive visit :
https://brainly.com/question/10677358
#SPJ11
The fireworks were a lantern in the sky
Answers
Answer:
So your saying thst when a firework blows then it is a big lantern in the sky???
Which of these plays an important role in keeping attack traffic off your systems and helps to protect users? check all that apply
Answers
Answer:
Antivirus software
Antimalaware measures
The things which play an important role in keeping attack traffic off your systems and helping to protect users are antimalware measures and Antivirus software. The correct options are a and b.
What are antimalware measures and antivirus software?Antimalware can assist in the prevention of malware assaults by checking all incoming data and preventing malware from being installed and infecting a computer.
When the operating system is unable to communicate with a mouse, the solution is to update the mouse device driver. This is because the mouse driver is frequently and always required to assist the motherboard in interacting with the device.
It is also a software that works between the Operating System and the Mouse because it can effectively and efficiently translate the signals to the motherboard appropriately or ways, which is why Microsoft's generic driver is used.
Therefore, the correct options are a and b.
To learn more about antimalware measures, refer to the link:
https://brainly.com/question/27994271
#SPJ2
The question is incomplete. Your most probably complete question is given below:
Antimalware measures
Antivirus software
Digital attack surfaces
cybersecurity
what is the function of filters?
a. forwarding mails
b. compose mails
c. block mails
d. send mails
Answers
Forwarding mails is the function of filters.
Thus, Electronic mail, or simply "email," is a form of communication that employs electronic devices to send messages via computer networks. The term "email" can apply to both the method of delivery and the specific messages that are sent and received.
Since Ray Tomlinson, a programmer, invented a mechanism to send messages between computers on the Advanced Research Projects Agency Network (ARPANET) in the 1970s, email has existed in some form.
With the introduction of email client software (like Outlook) and web browsers, which allow users to send and receive messages via web-based email clients, modern versions of email have been widely accessible to the general public.
Thus, Forwarding mails is the function of filters.
Learn more about Emails, refer to the link:
https://brainly.com/question/16557676
#SPJ1
PC A sends a request to Server B. What IPv4 address is used in the destination field in the packet as the packet leaves PC A?
Answers
The destination IPv4 address used in the packet as it leaves PC A will be the IPv4 address of Server B.
When a packet is sent from one device to another over an IP network, the packet header contains the source and destination IP addresses. In this case, PC A is sending a request to Server B, so the source IP address in the packet header will be the IPv4 address of PC A, and the destination IP address will be the IPv4 address of Server B.
Assuming that PC A knows the IPv4 address of Server B, it will use that address as the destination IP address in the packet header when sending the request. If PC A does not know the IPv4 address of Server B, it may need to perform a DNS lookup or consult a local hosts file to determine the address before sending the packet.
Learn more about IPv4 address here:
https://brainly.com/question/15074281
#SPJ11
can someone helpp what is this?

Answers
Answer:
How about:
if a person is cute and not in a relation, and if it is friday or saturday, ask the person out on a date.
I highlighted the gates in the text.

What is a search engine?
A) A program to build websites and web pages
B) A system that locates information on the World Wide Web.
C) The way people interact with the internet
D) The way e-mail is located and delivered
Answers
is lyin 2 me by cg5 a good song
Answers
Answer:
In my opinion no, but it could be good to u
Explanation:
Answer:
yea! it's the best of the best :D
hope this helps! <3
How can I see my question posts? I can't find them after asking one.
Answers
Answer:
maybe it's a glitch or smth, try restarting the app if you haven't already, kinda the only thing I can think of
Assignment 4: Evens and Odds
Instructions
Write a program that will ask a user for how many numbers they would like to check. Then, using a for loop, prompt the user for a number, and output if that number is even or odd. Continue doing this as many times as the user indicated. Once the loop ends, output how many even numbers were entered and how many odd numbers were entered.
Hint: For a number to be even, when the number is divided by 2, there should be no remainder - so you will want to use the modulus (%) operator.
Hint: You will need two count variables to keep track of odd and even numbers.
Sample Run 1
How many numbers do you need to check? 5
Enter number: 20
20 is an even number.
Enter number: 33
33 is an odd number.
Enter number: 4
4 is an even number.
Enter number: 77
77 is an odd number.
Enter number: 8
8 is an even number.
You entered 3 even number(s).
You entered 2 odd number(s).
Sample Run 2
How many numbers do you need to check? 3
Enter number: 10
10 is an even number.
Enter number: 3
3 is an odd number.
Enter number: 400
You entered 2 even number(s).
You entered 1 odd number(s).
Sample Run 2
How many numbers do you need to check? 3
Enter number: 10
10 is an even number.
Enter number: 3
3 is an odd number.
Enter number: 400
You entered 2 even number(s).
You entered 1 odd number(s).
Benchmarks
1. Create and initialize two count variables - one for odd and one for even.
2. Prompt the user to answer the question, “How many numbers do you need to check?"
3. Based on the previous input, create a for loop that will run that exact number of times.
1. Prompt the user to “Enter number: “
2.If that number is even, output “[number] is an even number.”
3.Update the even count variable.
4.Or else if the number is odd, output “[number] is an odd number.”
5.Update the odd count variable.
4.Output “You entered [number] even number(s).”
5.Output “You entered [number] odd number(s)."
Answers
A user finished working on a computer in the lab. What should the user do so
that their work is safe and others can use the computer?
Answers
Answer:
Explanation:
The best thing to do in this scenario would be to save all of the work that the user has just finished on a personal data USB drive and then delete any of his work off of the computer. Also, if the user entered into the computer using their own account they should also log off from the computer. The next individual can log in with their own account if they need to use the computer. This would make sure that their work is safe and with them, as well as making sure that no other individual can see, take, or modify the work that they have done.
An end-user license agreement protects _____.
both the owner and the purchaser of the software
purchasers of the software
any user of the software, even if it has been altered
the owner of the software
Answers
Answer:
Both the owner and the purchaser of the software
Explanation:
Just completed the test (2022)
Answer:
both the owner and the purchaser of the software
Explanation:
i took the test
The _____ is the part of a computer that executes the instructions of a computer program.
Answers
Answer:
Central processing unit (CPU)
Hope you have a great day :)
Where do you find the degree symbol on your computer?.
Answers
Explanation:
Press the 123 icon in the bottom-left corner of your keyboard, and then press and hold your finger on the zero key (0). 3. After a moment, a small pop-up will appear with the degree symbol in it.
I like helping
( BRANLIEST)
Compare different types of (monitors). Mention advantages and disadvantages of each types.
IF ANYONE ANSWER IT I WILL GIVE **BRAINLIEST**
Answers
Answer:
A monitor is an electronic output device that is also known as a video display terminal (VDT) or a video display unit (VDU). It is used to display images, text, video, and graphics information generated by a connected computer via a computer's video card. Although it is almost like a TV, its resolution is much higher than a TV. The first computer monitor was introduced on 1 March 1973, which was part of the Xerox Alto computer system.
Older monitors were built by using a fluorescent screen and Cathode Ray Tube (CRT), which made them heavy and large in size and thus causing them to cover more space on the desk. Nowadays, all monitors are made up by using flat-panel display technology, commonly backlit with LEDs. These modern monitors take less space on the desk as compared to older CRT displays.
Answer:
I think answer is
Explanation:
Type of monitor
I.Touch screen monitor
II.LED Monitor
III.DLE Monitor
Advantage
i.Energy Consumption
Ii.Multipule Screen
Disadvantages
i.Screen Flicker
radiation
How globalization is related to communication technology?
Answers
Answer:
hey mate there is your answer

The reason preventive controls are preferred over detective controls is:
a. Preventive controls are less costly
b. Detective controls do not actually stop unwanted activity
c. Detective controls require more resources
d. Preventive controls are do not detect unwanted activity
Answers
The reason preventive controls are preferred over detective controls is that preventive controls can stop unwanted activity before it occurs, whereas detective controls only identify unwanted activity after it has occurred.
This is option (b). Preventive controls are designed to prevent or deter unwanted activity, such as fraud or cyberattacks, by implementing measures such as access controls, security training, or encryption. In contrast, detective controls are designed to identify and respond to unwanted activity, such as monitoring logs or conducting audits. While detective controls are still an important part of an overall security strategy, preventive controls are preferred because they can minimize the impact of unwanted activity and potentially prevent it from occurring altogether. Additionally, preventive controls may be less costly and require fewer resources than detective controls in the long run.
To learn more about preventive click on the link below:
brainly.com/question/31055913
#SPJ11
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
1. 2. 3 Units
Assuming an optical disk has a capacity
of 25GB, how many 60 minute HD videos
of 3. 9GB each could be stored on the
disk?
Answers
Approximately 6 videos, each has 60 minutes duration and 3.9 GB capacity can be stored on a 25GB optical disk.
In this question, it is asked to calculate how many videos can be stored on a 25 GB optical disk. So, the calculation is given below:
The optical disk has a capacity of 25GB.
Each video's required storage is 3.9 GB which has 60 minutes in duration.
First, we calculate how many videos can be stored on an optical disk that has 25 GB capacity.
For this purpose, we need to divide the capacity of each video by the total capacity of an optical disk which is 25 GB.
So,
25/3.9 = 6.410 number of videos (~ 6 videos)
Therefore, 6 videos of 60 HD minutes can be stored on the 25 GB optical disk.
You can learn more about optical disk at
https://brainly.com/question/28066311
#SPJ4
The main reason for formatting message style and theme is that it can be useful for making your message
more entertaining to the reader.
easier to send and receive.
professional in appearance.
top priority for the reader.
Answers
Answer:
The answer is C
Explanation:
CCCCC
Answer:
C
Explanation:
Answered myself.
The average numbers of shares a piece of content receives is known as its:
Answers
Answer:
Amplification.
Explanation:
Social media publishing can be defined as a service that avails end users the ability to create or upload web contents in either textual, audio or video format in order to make them appealing to a target audience.
Thus, these web contents are generally accessed by end users from time to time through the use of various network-based devices. As users access these contents, they're presented with the option of sharing a particular content with several other people a number of times without any form of limitation.
Hence, the average numbers of shares a piece of content receives is known as its amplification. The higher the average numbers of shares a particular content receives, the higher the number of traffic it generates for its publisher.
When you begin designing a program, you work from a ____, a description of what your program should do.
Answers
Answer:
This is usually called a brief (you will also hear this in the design industry, as well as other places)
The set of analytical techniques that yield a best course of action is _____ analytics.
Answers
The set of analytical techniques that yield the best course of action is prescriptive analytics.
What is Analytics?This refers to the systematic computational analysis of data or statistics that is used to interpret data and find patterns in the data.
Hence, we can see that The set of analytical techniques that yield the best course of action is prescriptive analytics.
This is because when the best course of action is taken into consideration, it has to do with finding the best solutions.
Finding the best solutions also has to do with finding best courses of action and this type of analysis is known as prescriptive analytics.
Read more about analytical techniques here:
https://brainly.com/question/28139087
#SPJ1
16. aw computing would like to improve its case lightning record page by including: --a filtered component to display a message in bold font when a case is saved as a critical record type. ---a quick way to update the account status from the case layout. which two components should an administrator use to satisfy these requests? choose 2 answers
Answers
The administrator should use a Quick Action Component to provide a button for altering the account status and a Record Detail Component with Conditional Formatting to display a message in bold font for key.
How can I link a lightning record page to a certain record type?Choose a list item by clicking it. From the left-hand panel, select Lightning Record Pages. On the upper right, select the See Page Assignments button. Choose a value from the App, Record Type, and Profile picklists in the Look Up an Assignment box.
What do Salesforce Lightning Record Pages mean?A compilation of several elements on a single web page is known as a Lightning Record Page. Each object, such as Accounts.
To know more about administrator visit:-
https://brainly.com/question/30206212
#SPJ1
What are two reasons a network administrator would use cdp.
Answers
Answer:
To obtain VLAN information from directly connected switches. To determine the status of network services on a remote device. To determine the status of the routing protocols between directly connected routers .
Explanation:
1. An Expert System Mimics human expert in a particular area and as an example of making decision for credit card approval True or false 1. Heuristic means Rule of Thumb; meaning intution and gut feeling and human can earn it by experience and it is difficult to formulate it for a computer. True or false 1. There was a software crisis in 1968, as result of programming abilities, due to the invention of integrated circuits (chips). True or false 1. The way a program is proceed is know as control flow and are :Sequence(one line after the other), Decision-making(either this or that), and Repetition( going back and start again). True or false
Answers
Expert systems are often used in fields where there is a need for highly specialized knowledge or expertise, such as medicine, finance, and engineering. They can be an effective way to provide expert-level guidance or support to people who may not have the same level of knowledge or experience in a particular domain.
Learn more about expert system, here https://brainly.com/question/29978704
#SPJ4
The Griffin family lives in multiple states, so they decide to use an online collaborative website to create their annual photo book. The website lets each of them upload photos from their computer, and then they can all arrange the photos into pages. What valid privacy concerns might the family members have
Answers
A privacy concern the family may have is IP tracking, and unless they have a good VPN is location tracking since they are all uploading pictures to this website.
Check ALL of the correct answers.
What would the following for loop print?
for i in range(2, 4):
print(i)
2
2
3
4.
1
Help now please
Answers
Answer:
2,3,4
Explanation:
Starts at two, goes to four. Thus it prints 2,3,4
It is early in the season and the night of the big football rivalry game, and you are so excited to spend time with friends and watch your boyfriend play ball. However, you are assigned to one of the football spreads and must take pictures. What do you do?
Answers
Answer:
take the pictures while watching him play
Explanation:
What is output by the following code?
C = 1
sum = 0
while (c 4 10):
C=C+2
sum = sum + c
print (sum)
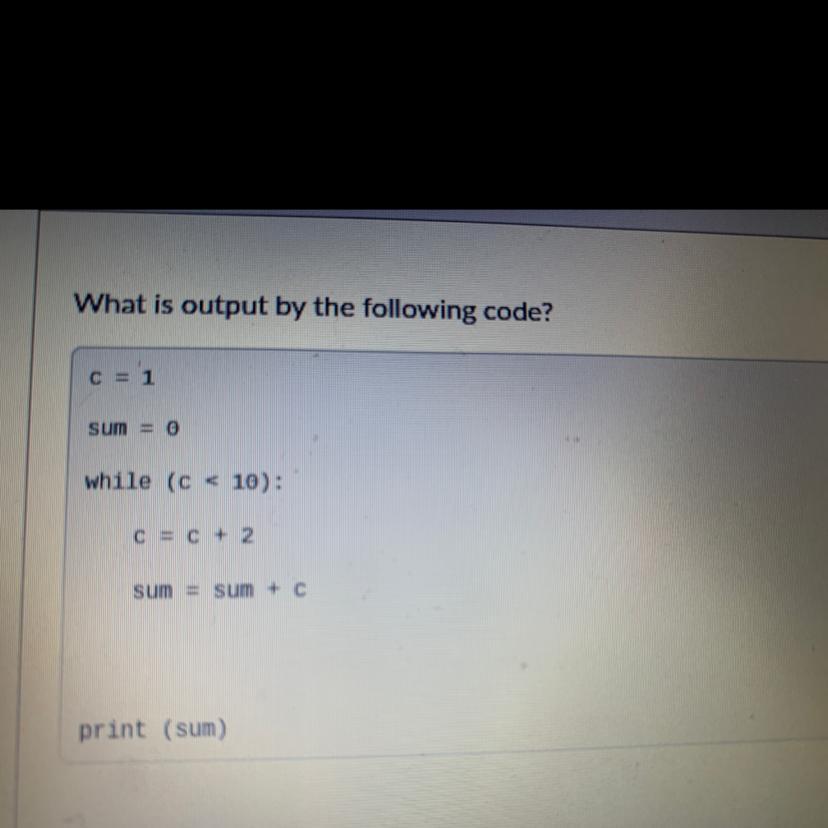
Answers
Answer :
Sum = 3,8,15,24,35
Steps :
Initially, c = 1, so
while (c=1 < 10)
c= 1+2 =3
Sum = 0 + 3 = 3
while (c=3 < 10)
c= 3+2 =5
Sum = 3 + 5 = 8
while (c=5 < 10)
c= 5+2 =7
Sum = 8 + 7 = 15
while (c=7 < 10)
c= 7+2 =9
Sum = 15 + 9 = 24
while (c=9 < 10)
c= 9+2 =11
Sum = 24 + 11 = 35
Therefore, Sum = 3,8,15,24,35
You can learn more about while loop from the given link:
https://brainly.in/question/16569909
#SPJ13