what is a predefined list of values? group of answer choicesa. lookup field b. input field c. lookup maskd. input mask
Answers
A lookup field is a list of predetermined values.
Why would you use an input mask?A string of characters known as an input mask serves as a format indicator for valid input values. Table fields, query fields, and buttons on forms and reports can all employ input masks. One object property that is stored is the input mask. When it's crucial that the format of the input values be consistent, you employ an input mask.
What does Access mean by a default value?When you want Access to automatically enter a value in a new record, you set a default value to a table field or form control. You could, for instance, instruct Access to add the current date to all new orders. Usually, you give your table fields a default value.
To know more about lookup field visit:-
https://brainly.com/question/25698028
#SPJ4
Related Questions
Liz's meeting is scheduled to end at 9:30. It is 9:20 and team
members are still discussing the last point on the agenda.
What should Liz do? (Select all that apply.)
Dismiss participants.
Help the team members wrap up their conversation
Start a debate over the one item no one agreed on
Discuss action items and next steps.
Highlight the good that came from the meeting
Tell the team to be quiet so she can end the meeting.
Answers
Answer: help the team members wrap up their conversations, dismiss participants, tell the team to be quiet so she can end the meeting
Explanation: starting a debate nobody agrees on could last hours, highlighting the good would start up a new conversation,discussing action items and next steps is starting a new conversation
i finished all my final exams 100 on math 100 on science and 94 on language arts.
Answers
Answer:
GOOOD JOBBB !! congrats :D
Explanation:
Answer:
hmmm
Explanation:
I think 294 cause it makes since
c) From this group, you can crop images in PowerPoint. (i) Adjust (ii) Arrange (iii) Edit (iv) Size
Answers
Under the picture format tab
ball.setSize(25, 75);
What does 25 represent in the example above?
1. The SPEED of the ball
2. The WIDTH of the ball
3. The HEIGHT of the ball
4. The 'X' coordinate of the ball
Answers
Answer:
2
Explanation:
Ed says that no matter how carefully he checks his CSS code and HTML markup, and has validated his document at the W3C Markup Validation Service Web page, the document doesn’t render as expected in his Web browser. Some of the flexbox properties simply don’t work. What do you tell Ed?
Answers
Answer:
Try another browser
Explanation:
Some browsers do not support advanced features like flex box.
Explain in a paragraph how the spectre malware exploits speculative execution in the cpu.
Answers
Spectre malware exploits speculative execution in the CPU by tricking it into speculatively executing instructions that should not have been executed.
How does the Spectre malware exploit speculative execution in the CPU?The Spectre malware exploits a weakness in CPUs that use speculative execution, which is a technique used to optimize the performance of processors.
Speculative execution allows a CPU to anticipate the outcome of a branch instruction and execute code before it knows for certain which path the code will take. The Spectre malware takes advantage of this by tricking the CPU into executing malicious code that it shouldn't have access to.
By using speculative execution to read data from memory, the malware can potentially access sensitive information, such as passwords or encryption keys.
This is accomplished by manipulating the CPU's branch prediction mechanism and exploiting timing differences to leak information.
Spectre is considered a significant security threat because it can affect a wide range of CPUs and is difficult to detect and prevent.
Learn more about malware
brainly.com/question/30926112
#SPJ11
Please! I need help matching this.
Answers
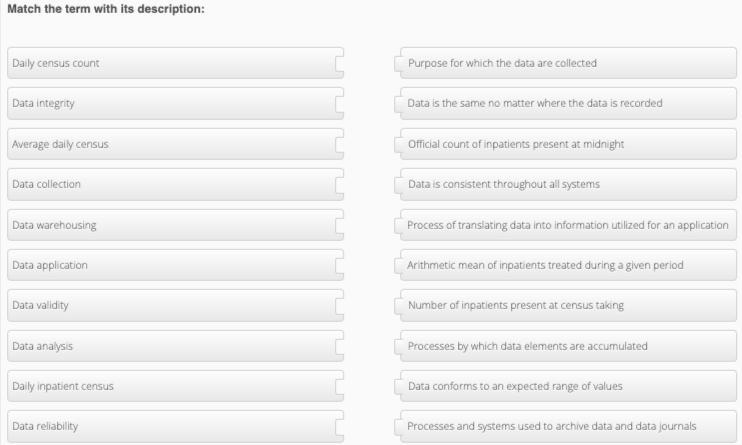
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
In what situations might you need to use a function that calls another function?
Answers
Answer:
Explanation:
It is important to understand that each of the functions we write can be used and called from other functions we write. This is one of the most important ways that computer programmers take a large problem and break it down into a group of smaller problems.
Assume the maximum segment size used by the TCP connection is 1000 bytes.
Answer the following question.
How many bytes would be the congestion window after it sends out 2 segments and receives acks for all of them if the connection is in slow-start and MSS is 1000 bytes.
Answers
In a connection that is in slow-start and has an MSS of 1000 bytes, after sending out two segments and receiving acknowledgments for all of them, the congestion window will increase to 2000 bytes.
This is because in slow-start, the congestion window is increased by one MSS for each successful transmission until the threshold is reached, at which point it enters congestion avoidance. In this case, the threshold is not specified, so we can assume it to be infinite. Therefore, after sending out two segments, the congestion window increases by two MSSs (2000 bytes) and this process repeats as long as acknowledgments are received for each transmission.
It is worth noting that the congestion window is used by TCP to regulate the flow of packets on a network. It represents the maximum number of bytes that a sender can transmit without receiving an acknowledgement from the receiver. This mechanism is designed to prevent congestion on the network and ensure reliable packet transmission. Slow-start is a TCP mechanism that is used to avoid network congestion when a connection is first established.
Learn more about receiving acknowledgments: https://brainly.com/question/15059697
#SPJ11
What is the output of the following code fragment? int i = 1; int sum = 0; while (i <= 11) { sum = sum + i; i++; } System.out.println("The value of sum is " + sum); The value of sum is 65. The value of sum is 66. The value of sum is 55. The value of sum is 56.
Answers
Answer:
The value of sum is 66
Explanation:
i = 1
sum = 0
while (i <= 11) {
sum = sum + i;
i++;
}
i = 1
sum = sum + isum = 0 + 1sum = 1i = 2
sum = sum + isum = 1 + 2sum = 3i = 3
sum = sum + isum = 3 + 3sum = 6i = 4
sum = sum + isum = 6 + 4sum = 10i = 5
sum = sum + isum = 10 + 5sum = 15i = 6
sum = sum + isum = 15 + 6sum = 21i = 7
sum = sum + isum = 21 + 7sum = 28i = 8
sum = sum + isum = 28 + 8sum = 36i = 9
sum = sum + isum = 36 + 9sum = 45i = 10
sum = sum + isum = 45 + 10sum = 55i = 11
sum = sum + isum = 55 + 11sum = 66i = 12 --> does not comply with the condition "i < = 11", the while loop is over
how is a trade off best described ?
dilema
compromise
demand
complication
Answers
The __________ vulnerability assessment is a process designed to find and document selected vulnerabilities that are likely to be present on the organization's internal network.
Answers
The intranet vulnerability assessment is a process designed to find and document selected vulnerabilities that are likely to be present on the organization's internal network.
What is vulnerability assessment?Vulnerability assessment is a systematic and methodical evaluation of assets' exposure to attackers, natural forces, or any other entity that could cause harm.
A vulnerability assessment is a systematic examination of an information system's security flaws.
It determines whether the system is vulnerable to any known vulnerabilities, designates severity levels to those security flaws, and recommends remediation or mitigation when necessary.
A Hazard Vulnerability Analysis (HVA) would provide the Coalition with a shared understanding of the hazards it faces and aids in the prioritization of issues for the EMP to address.
The intranet vulnerability evaluation is a procedure that seeks out and documents specific vulnerabilities that may exist on the organization's internal network.
Thus, the answer is intranet.
For more details regarding vulnerability assessment, visit:
https://brainly.com/question/1395802
#SPJ6
1. Which of the following is not a feature of utility theory: A. utility is the benefit or satisfaction that a person gets from the consumption of a good or service. B. marginal utility gained from consuming additional units of a good is expected to decrease if consumption of the good occurs within a given time period. C. each additional unit of consumption sometimes yields additional utility. D. If the next unit of a good consumed has a marginal utility of zero then total utility will be constant. E. a demand curve can be said to slope downwards because of the law of diminishing marginal utility.
Answers
The main answer to your question is option D, which is not a feature of utility theory. According to utility theory, utility is the benefit or satisfaction that a person gets from the consumption of a good or service (option A), and marginal utility gained from consuming additional units of a good is expected to decrease
if consumption of the good occurs within a given time period (option B). Additionally, each additional unit of consumption sometimes yields additional utility (option C), and a demand curve can be said to slope downwards because of the law of diminishing marginal utility (option E).However, option D is not a feature of utility theory because if the next unit of a good consumed has a marginal utility of zero, it does not mean that total utility will be constant. In fact, total utility may continue to increase even if the marginal utility of additional units of the good consumed is zero. This is because total utility is the sum of all the marginal utilities of each unit consumed, and even if the marginal utility of the last unit consumed is zero, the total utility may still be increasing due to the previous units consumed.
In summary, the long answer to your question is that option D is not a feature of utility theory, as the total utility may still increase even if the marginal utility of the last unit consumed is zero.The main answer to your question is that option C, "each additional unit of consumption sometimes yields additional utility," is not a feature of utility theory.To provide a longer answer, let's briefly discuss the other options : The utility is indeed the benefit or satisfaction a person gets from consuming a good or service .Marginal utility is expected to decrease with additional consumption within a given time period.XIf the marginal utility of the next unit consumed is zero, then total utility remains constant.XThe downward slope of a demand curve can be attributed to the law of diminishing marginal utility . Option C is incorrect because it contradicts the principle of diminishing marginal utility, which states that as more units of a good or service are consumed, the additional satisfaction gained decreases.
To know more about benefit visit:
https://brainly.com/question/13067827
#SPJ11
A ____ may be used to filter data that may be undesirable.
O ports
O firewall
O updates
O security hole
Answers
A firewall may be used to filter data that may be undesirable. The correct answer is Firewall.
A firewall is a network security device that acts as a barrier between an internal network and the external network (typically the Internet). It monitors and filters incoming and outgoing network traffic based on predetermined security rules.
One of the primary functions of a firewall is to filter data and prevent unwanted or potentially harmful traffic from entering or leaving a network.
By setting up appropriate rules and configurations, a firewall can block specific types of data or connections that may be deemed undesirable or pose a security risk. These rules can be based on various criteria such as IP addresses, ports, protocols, or specific patterns in the data payload.
Firewalls play a crucial role in network security by acting as the first line of defense against unauthorized access, malicious activities, and potential threats.
They help protect sensitive data, prevent unauthorized access to internal resources, and ensure the confidentiality, integrity, and availability of the network.
While other options mentioned in the question (ports, updates, security hole) are also relevant in the context of network security, a firewall specifically serves the purpose of filtering data and controlling the flow of network traffic to prevent undesirable or malicious data from entering or leaving a network.
Therefore, the correct option is Firewall.
Learn more about firewall:
https://brainly.com/question/13693641
#SPJ11
You are the administrator for a small network with several servers. There is only one printer, which is centrally located. Although indications are that this printer is over-utilized, there is neither space nor budget to add additional printers at this time.
There are often cases where a document is needed urgently, but when it is printed, it goes into the queue and is printed in the order received, not the order of the document's priority. You would like to allow Gladys, the administrative assistant, to have the ability to maintain the print queue. Specifically, you want her to be able to alter the order of printing for the documents waiting to be printed.
You need to permit Gladys to make this change without adding her to the local Administrators group or making significant changes to the way your office operates.
What should you do?
Answers
Answer:
The answer is "Allocate permission for managing documents to the Gladys printer."
Explanation:
In the given scenario, we allow permission for managing the documents to the Gladys printer. It should enable Gladys could continue these trends by bringing something into the community of local administrators and introducing major changes to wherewith your office operates. In especially, they need her to modify its printing process regarding documentation requiring printing.
Jane’s company is seeking to raise their brand profile. They want to connect with an organization with a large fan base without directly promoting their products or services. Jane is looking to improve her company’s reputation through
Answers
Jane is looking to improve her company’s reputation through brand marketing/ social media marketing.
What Brand marketing?This is known to be a process of setting up and growing a relationship through a brand and consumers.
Fanbase is known to be a free and monetized social network that gives anyone the right to make money through content.
Learn more about Brand marketing from
https://brainly.com/question/25754149
mobile users tend to give much more attention to top search results that desktop users. True or False
Answers
Mobile users tend to give much more attention to top search results that desktop users.
The given statement is False.
There is no evidence to suggest that mobile users tend to give more attention to top search results than desktop users.
Both mobile and desktop users typically focus on the top results of their search query, although the specific behavior may vary depending on the context and user intent.
Additionally, factors such as the size of the screen and the ease of scrolling may play a role in how users interact with search results on mobile devices compared to desktop computers.
For similar question on desktop users.
https://brainly.com/question/29921100
#SPJ11
An article in the Transportation Research Part E Journal ["Arc Routing Problems to Restore Connectivity of a Road Network" (2016)] considered ways of re-establishing the connectivity of road networks after a natural disaster − earthquake. Estimates of the probabilities of a randomly chosen road being under light debris, moderate debris, and heavy debris conditions after different disaster magnitudes are shown in the following table. Disaster magnitude is equally likely to be low, moderate or high. Given that a road had light debris after an earthquake, what is the conditional probability that the disaster magnitude was low? Round your answer to two decimal places (e.g. 98.76). P=
Answers
The conditional probability that the disaster magnitude was low, given that a road had light debris after an earthquake, is approximately 0.33.
It applies Bayes' theorem to calculate the conditional probability of the disaster magnitude being low, given that a road had light debris after an earthquake.
Here's a summary of the solution:
Let P(A) be the probability that the disaster magnitude was low, and P(B) be the probability that a road has light debris.
P(A) = P(disaster magnitude is low) = 1/3 (since disaster magnitude is equally likely to be low, moderate, or high)
P(B) = P(Light debris) = 0.2 (given in the table)
The conditional probability P(A|B), which represents the probability of the disaster magnitude being low given that a road had light debris after an earthquake, is calculated using Bayes' theorem:
P(A|B) = P(B|A) * P(A) / P(B)
Where:
P(B|A) is the probability of light debris given that the disaster magnitude was low (from the table) = 0.2
Substituting the values:
P(A|B) = (0.2 * 1/3) / 0.2
P(A|B) = 0.33 (approximately)
Note: The solution provides a clear explanation of the steps involved and uses Bayes' theorem to calculate the required conditional probability.
Understanding the concept and applying the formula correctly is crucial in solving such probability problems.
To know more about magnitude visit:
https://brainly.com/question/31022175
#SPJ11
Dining Philosophers problem in class uses a monitor. Implement the same solution (simulating monitors) using semaphores
monitor DiningPhilosophers
{
enum { THINKING; HUNGRY, EATING) state [5] ;
condition self [5];
void pickup (int i) {
state[i] = HUNGRY;
test(i); // Tests if chopsticks are available
if (state[i] != EATING) self[i].wait;
}
void putdown (int i) {
state[i] = THINKING;
// test left and right neighbors
test((i + 4) % 5);
test((i + 1) % 5);
}
void test (int i) {
// both chopsticks must be available
if ((state[(i + 4) % 5] != EATING) &&
(state[i] == HUNGRY) &&
(state[(i + 1) % 5] != EATING) ) {
state[i] = EATING ; // Gets chopsticks
self[i].signal () ;
}
}
initialization_code() {
for (int i = 0; i < 5; i++)
state[i] = THINKING;
}
}
Answers
Here's an implementation of the Dining Philosophers problem using semaphores instead of a monitor:
```python
from threading import Semaphore, Thread
THINKING = 0
HUNGRY = 1
EATING = 2
class DiningPhilosophers:
def __init__(self):
self.num_philosophers = 5
self.state = [THINKING] * self.num_philosophers
self.mutex = Semaphore(1)
self.s = [Semaphore(0) for _ in range(self.num_philosophers)]
def pickup(self, philosopher):
self.mutex.acquire()
self.state[philosopher] = HUNGRY
self.test(philosopher)
self.mutex.release()
self.s[philosopher].acquire()
def putdown(self, philosopher):
self.mutex.acquire()
self.state[philosopher] = THINKING
self.test((philosopher + 4) % self.num_philosophers)
self.test((philosopher + 1) % self.num_philosophers)
self.mutex.release()
def test(self, philosopher):
left_philosopher = (philosopher + 4) % self.num_philosophers
right_philosopher = (philosopher + 1) % self.num_philosophers
if (
self.state[left_philosopher] != EATING
and self.state[philosopher] == HUNGRY
and self.state[right_philosopher] != EATING
):
self.state[philosopher] = EATING
self.s[philosopher].release()
def philosopher_thread(philosopher, dining):
while True:
# Philosopher is thinking
print(f"Philosopher {philosopher} is thinking")
# Sleep for some time
dining.pickup(philosopher)
# Philosopher is eating
print(f"Philosopher {philosopher} is eating")
# Sleep for some time
dining.putdown(philosopher)
if __name__ == "__main__":
dining = DiningPhilosophers()
philosophers = []
for i in range(5):
philosopher = Thread(target=philosopher_thread, args=(i, dining))
philosopher.start()
philosophers.append(philosopher)
for philosopher in philosophers:
philosopher.join()
```
In this solution, we use semaphores to control the synchronization between the philosophers. We have two types of semaphores: `mutex` and `s`. The `mutex` semaphore is used to protect the critical sections of the code where the state of the philosophers is being modified. The `s` semaphore is an array of semaphores, one for each philosopher, which is used to signal and wait for a philosopher to pick up and put down their chopsticks.
When a philosopher wants to eat, they acquire the `mutex` semaphore to ensure exclusive access to the state array. Then, they update their own state to `HUNGRY` and call the `test` function to check if the chopsticks on their left and right are available. If so, they change their state to `EATING` and release the `s` semaphore, allowing themselves to start eating. Otherwise, they release the `mutex` semaphore and wait by calling `acquire` on their `s` semaphore.
When a philosopher finishes eating, they again acquire the `mutex` semaphore to update their state to `THINKING`. Then, they call the `test` function for their left and right neighbors to check if they can start eating. After that, they release the `mutex` semaphore.
This solution successfully addresses the dining Philosophers problem using semaphores. By using semaphores, we can control the access to the shared resources (chopsticks) and ensure that the philosophers can eat without causing deadlocks or starvation. The `test` function checks for the availability of both chopsticks before allowing a philosopher to start eating, preventing situations where neighboring philosophers might be holding only one chopstick. Overall, this implementation demonstrates a practical use of semaphores to solve synchronization problems in concurrent programming.
To know more about Semaphores, visit
https://brainly.com/question/31788766
#SPJ11
If you receive the "Cannot display the folder. Microsoft Outlook cannot access the specified folder location" error, you typically need to rename or delete your .ost file. In Outlook, click File > Account Settings > Data Files to find the location of your OST file. Then close Outlook.
Go to the path of OST file, delete or rename the OST file.
Restart your Outlook client, a new OST file will be created.
Typically this file is in C:\Users\YourName\AppData\Local\Microsoft\Outlook
Find your .ost and rename to .bak or .old
Answers
Answer:
what is the question??? as if ur answring
Explanation:
If you encounter the error "Cannot display the folder. Microsoft Outlook cannot access the specified folder location," it usually means you need to modify your .ost file.
To do this, follow these steps:
1. Open Outlook and click on File > Account Settings > Data Files to locate the path of your .ost file.
2. Close Outlook and navigate to the .ost file's location, typically found in C:\Users\YourName\AppData\Local\Microsoft\Outlook.
3. Rename or delete the .ost file, such as changing the extension to .bak or .old.
4. Restart your Outlook client, which will create a new .ost file automatically.
By following these steps, you should resolve the error and regain access to your Outlook folders. Remember to always keep a backup of your files before making changes.
You can learn more about Microsoft Outlook at: brainly.com/question/30311315
#SPJ11
why is life so boring and why can´t life just be fair and why is life so short and why do all these bad things happen to good ppl like why do bad things happen period
Answers
Answer:
To be honest i wonder the same thing all the time. I wish i knew the answer to all these questions as well.
Explanation:
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Question 4 Fill in the blank: To keep a header row at the top of a spreadsheet, highlight the row and select _____ from the View menu. 1 point Set Pin Freeze Lock
Answers
To keep a header row at the top of a spreadsheet, highlight the row and select Freeze from the View menu.
Keeping the header at a place on a spreadsheetA spreadsheet is a software program that helps a user to perform
mathematical calculations on statistical data Arrange raw numbers when assigned operations like total, average Generate data visualizations eg chartsWhen working with a long spreadsheet and you want the header to stay at a place, you can freeze the header row or column as the case may be , this is done by:
Going to the View tab, Windows GroupClick the Freeze Panes drop down arrowSelect Freeze Top Row or Freeze First ColumnA thin line is indicated to show where the frozen pane starts.
See related answer on Freezing header row:https://brainly.com/question/16128207
FILL IN THE BLANK _________ are the principal transporters of cholesteryl esters to tissues.
Answers
High-density lipoproteins (HDLs) are the principal transporters of cholesteryl esters to tissues.
HDLs are often referred to as "good cholesterol" because they play a critical role in removing excess cholesterol from the body and transporting it to the liver for processing and elimination. In addition to transporting cholesteryl esters, HDLs also have anti-inflammatory and antioxidant properties that help to protect against cardiovascular disease. Maintaining high levels of HDL cholesterol is an important component of a healthy lifestyle and can be achieved through regular exercise, a diet rich in healthy fats and fiber, and avoiding smoking and excessive alcohol consumption.
learn more about High-density lipoproteins here:
https://brainly.com/question/28620545
#SPJ11
Select the correct answers.
Which are the benefits of leveraging web technologies?
processing of large amounts of data
more manpower
better marketing and customer service
increased production costs
difficulty in handling customer complaints

Answers
Answer:
Explanation:
Select the correct answers.
Which are the benefits of leveraging web technologies?
1) Processing of large amounts of data
2) Better marketing and customer service
what will you see on the next line after the following lines of code?
>>> aList = [9, 2, 3.5, 2]
>>> aList.remove(2)
>>> aList
[9, 3.5]
[9, 3.5, 2]
[9, 2, 3.5, 2]
Answers
Answer: I think its A [9, 3.5]
Explanation:
Answer:
[ 9, 3.5, 2]
Explanation:
To find spelling errors in your document you can use....
A.Grammarly
B. Spell Changer
C.Spell Check
D.Spell Corrector
Answers
Answer:
Spell check
Explanation:
On the Review tab, click Spelling & Grammar. If Word finds a potential error, the Spelling & Grammar dialog box will open, spelling errors will be shown as red text, and grammatical errors will be shown as green text.
consider a system that consists of 4 parameters, p1, p2, p3, and p4. each parameter has two values 0 and 1. apply algorithm ipo to create a pairwise test set for this system.
Answers
Here's an example of a pairwise test set generated using the IPO algorithm for this system:
Test Case 1: p1=0, p2=0, p3=0, p4=0
Test Case 2: p1=0, p2=1, p3=0, p4=1
Test Case 3: p1=1, p2=0, p3=1, p4=0
Test Case 4: p1=1, p2=1, p3=1, p4=1
The IPO (Input-Process-Output) algorithm is commonly used to create a pairwise test set that covers all possible combinations of input parameters. In this case, we have four parameters, p1, p2, p3, and p4, each with two values (0 and 1).
To apply the IPO algorithm, we need to generate test cases that cover all possible combinations of the parameter values. Since we have two values for each parameter, we can generate a pairwise test set that covers all possible combinations of two values for each pair of parameters.
In this test set, each parameter is paired with all other parameters, ensuring that all possible pairwise combinations are covered. The test cases can be executed to validate the system's behavior and identify any potential issues or interactions between the parameters.
By using the IPO algorithm, we can generate an efficient and effective test set that covers a wide range of parameter combinations while minimizing the number of test cases required.
For more such questions on IPO algorithm, click on:
https://brainly.com/question/32147965
#SPJ8
When a variable is assigned a number that is too large for its data type, it:A) underflowsB) overflowsC) reverses polarityD) exceeds expectationsE) None of the above
Answers
When a variable is assigned a number that is too large for its data type, it: B) overflows.
What is database?A database in computing is a structured collection of data that is electronically accessible and stored. Large databases are housed on computer clusters or cloud storage, whilst small databases can be stored on a file system. Data modeling, effective data representation and storage, query languages, security and privacy of sensitive data, and distributed computing challenges, such as providing concurrent access and fault tolerance, are all part of the design of databases. In order to collect and process data, a database management system (DBMS) communicates with applications, end users, and the database itself. The primary tools offered to manage the database are also included in the DBMS software.
To know more about database visit:
https://brainly.com/question/29775297
#SPJ1
When considering technology infrastructure for mobile commerce applications, which of the following are limitations that may complicate their use?
Select one:
a. Choice 4: All of the above
b. Choice 3: Potential for less processing power and bandwidth
c. Choice 1: Small screen size
d. Choice 2: Limited input capabilities (e.g., fewer buttons may be presented)
Answers
The correct answer is: a. Choice 4: All of the above
when considering technology infrastructure for mobile commerce applications, it is important to take into account the limitations that may complicate their use.
All of the aforementioned options—a small screen, limited input options, and the possibility of using less processing power and bandwidth—can be obstacles that make using mobile commerce applications more difficult.
Small size of screen: In general, mobile devices have smaller screens than desktop or laptop computers. This restricted screen land can make it trying to show complex connection points or a lot of data, possibly influencing the client experience and convenience of portable business applications.
Capacity for input is limited: Cell phones frequently have less actual fastens or input choices contrasted with conventional PCs. On mobile commerce applications, this may make certain tasks more difficult or time-consuming, limiting the variety of input methods available to users.
Potentially less bandwidth and processing power: When compared to desktop computers, mobile devices may have limited bandwidth and less processing power. When dealing with tasks that require a lot of resources or when the network connection is slow or unstable, this can have an effect on the performance and responsiveness of mobile commerce applications.
In order to ensure a seamless user experience and optimal performance on mobile devices, it is essential to take these limitations into consideration when developing mobile commerce applications.
To know more about Technology, visit
brainly.com/question/27960093
#SPJ11