what is a disadvantage of using eigrp automatic summarization?
Answers
A disadvantage of using EIGRP automatic summarization is the potential loss of network granularity, leading to inefficient routing decisions and suboptimal traffic flow. It can also cause routing loops and black holes if not properly configured.
EIGRP (Enhanced Interior Gateway Routing Protocol) is a routing protocol used in computer networks. Automatic summarization is a feature of EIGRP that allows the router to summarize network addresses to reduce the size of routing tables. While automatic summarization can be beneficial in some cases, it also has its disadvantages.
One major disadvantage of using EIGRP automatic summarization is the potential loss of network granularity. When summarization is applied, multiple subnets are combined into a single summarized route. This can lead to inefficient routing decisions and suboptimal traffic flow. For example, if a network has multiple subnets with different characteristics or requirements, such as different bandwidth or latency, summarizing them into a single route may not take into account these differences and result in suboptimal routing decisions.
Additionally, automatic summarization can cause routing loops and black holes in the network if not properly configured. Routing loops occur when routers receive conflicting routing information and continuously forward packets in a loop. Black holes occur when a router advertises a summarized route, but the actual subnets within that route are not reachable. These issues can disrupt network connectivity and lead to network instability.
It is important to carefully consider the impact of automatic summarization before implementing it in a network. Network administrators should evaluate the network's requirements, the characteristics of the subnets, and the potential impact on routing decisions and traffic flow. Proper configuration and monitoring are essential to avoid routing issues and ensure optimal network performance.
Learn more:About EIGRP automatic summarization here:
https://brainly.com/question/22311150
#SPJ11
EIGRP can end up using a longer path to reach a destination than necessary. This can lead to increased latency, decreased throughput, and other performance issues.
The disadvantage of using EIGRP automatic summarization is that it can result in sub-optimal routing. When summarization is enabled, EIGRP will automatically summarize the routes it learns. This can lead to longer path lengths than necessary.In more detail, EIGRP uses the concept of the Diffusing Update Algorithm (DUAL) to calculate the shortest path to a destination. DUAL is a loop-free protocol that ensures that the network's topology is updated and converged.
When summarization is used, EIGRP will summarize all the routes it learns to be sent to other routers. It is vital to note that this summarization is carried out on all the routes learned, whether they are subnets or supernet routes.When a router summarizes, it advertises the summarized route rather than all the individual subnets that make up that summary. This is beneficial for a number of reasons.
First, it reduces the amount of information sent to other routers, which can help reduce network overhead. Second, it simplifies the routing table on other routers, as they only see the summarized route. This can help to improve the network's stability.However, this can result in sub-optimal routing since it reduces the level of granularity at which EIGRP sees the network.
As a result, EIGRP can end up using a longer path to reach a destination than necessary. This can lead to increased latency, decreased throughput, and other performance issues.
Learn more about Latency here,
https://brainly.com/question/13010901
#SPJ11
Related Questions
Do a internet search on executive compensation to determine how CEO's are currently being compensated. Detail your findings and discuss your position on executive compensation. Is executive compensation universally excessive or appropriate?
Answers
Executive compensation refers to the financial compensation and benefits provided to top-level executives, particularly CEOs, in organizations. Internet search results reveal that CEO compensation varies widely depending on factors such as the size and industry of the company, its financial performance, and market trends. CEO compensation typically includes a mix of salary, bonuses, stock options, restricted stock, and other perks.
The debate on executive compensation is multifaceted, with different perspectives on whether it is universally excessive or appropriate. It is important to consider factors such as executive performance, company size, market competition, and stakeholder interests when forming a position on executive compensation.
A search on executive compensation reveals that CEO pay varies significantly across industries and companies. In some cases, CEOs of large corporations receive multimillion-dollar compensation packages that include substantial salaries, performance-based bonuses, stock options, and other benefits. These compensation packages are often justified based on the executive's responsibilities, the company's financial performance, and the competitive market for executive talent.
However, opinions on executive compensation are divided. Critics argue that some CEO pay levels are excessive and not aligned with performance or shareholder value. They believe that such high levels of compensation contribute to income inequality and can lead to a misalignment of incentives between executives and shareholders.
On the other hand, proponents of executive compensation argue that attracting and retaining talented executives is crucial for driving company success. They assert that executive pay is determined by market forces and should reflect the value the CEO brings to the organization. They also emphasize that executive compensation is often tied to performance metrics and that excessive pay outliers are relatively rare.
Forming a position on executive compensation requires considering multiple factors. It is important to evaluate the performance of CEOs in relation to the company's financial results, the industry context, and the interests of various stakeholders, including shareholders, employees, and the broader society. Striking the right balance between rewarding executives for their contributions and ensuring fairness and accountability is a complex challenge that requires ongoing scrutiny and evaluation.
To learn more about metrics click here: brainly.com/question/30905058
#SPJ11
Look at the following code:
Line 1 public class ClassA
Line 2 {
Line 3 public ClassA() {}
Line 4 public void method1(int a){}
Line 5 }
Line 6 public class ClassB extends ClassA
Line 7 {
Line 8 public ClassB(){}
Line 9 public void method1(int x){}
Line 10 }
Line 11 public class ClassC extends ClassB
Line 12 {
Line 13 public ClassC(){}
Line 14 public void method1(int y){}
Line 15 }
Which method (line number) will be executed as a result of the following statements?
ClassB item1 = new ClassA();
item1.method1(5);
Answers
Answer:
The answer is "There is an error, that's why the program will crash".
Explanation:
In the given program code, three class "A, B, and C" is defined, and inside the code, all class constructor and a method "method1" is defined, that uses an integer variable in its parameters.
At the last line class B object "item1" is created, that holds the class A instance, and in the next step, method1 is called by accepting integer value. when we create the class B object and convert it into ClassB. it is not possible that's why it will give an error.Use the function written in the last lesson to calculate the gold medalists’ average award money for all of their gold medals. Define another function in your program to calculate the average.
Your program should then output the average award money, including the decimal place. Your program should use a total of two functions. You may assume that the user will provide valid inputs.
Sample Run
Enter Gold Medals Won: 3
How many dollars were you sponsored in total?: 20000
Your prize money is: 245000
Your average award money per gold medal was 81666.6666667
Answers
The program should then output the average award money, including the decimal place is in explanation part.
What is programming?Making computer executable instructions is the process of programming. To accomplish a given goal or find a solution, it entails writing code in a particular programming language that the machine can comprehend and follow.
Here's the Python code that meets the requirements of the task:def calculate_award_money(num_medals, sponsor_money, prize_money):
total_award_money = sponsor_money + prize_money
return total_award_money / num_medals
def calculate_average_award_money():
num_medals = int(input("Enter Gold Medals Won: "))
sponsor_money = float(input("How many dollars were you sponsored in total?: "))
prize_money = float(input("Your prize money is: "))
avg_award_money = calculate_award_money(num_medals, sponsor_money, prize_money)
print(f"Your average award money per gold medal was {avg_award_money:.10f}")
calculate_average_award_money()
Thus, the output shows that the average award money per gold medal for this example is 81666.6666667, which matches the expected output in the task description.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ1
2. What changes, if any, could Lisa make to her income?
Ramsey classroom
Answers
Answer: what changed if any could lisa make to her income
Explanation:
Create an HTML document on the topic Circle v/s Rectangle v/s Triangle.
The web page should contain three frames
Answers
Answer:
Here is answer
Explanation:
<!DOCTYPE html>
<html>
<head>
<title>Circle vs Rectangle vs Triangle</title>
</head>
<body>
<h1>Circle vs Rectangle vs Triangle</h1>
<!-- Create three frames -->
<iframe src="circle.html" frameborder="0"></iframe>
<iframe src="rectangle.html" frameborder="0"></iframe>
<iframe src="triangle.html" frameborder="0"></iframe>
</body>
</html>
<h2>Circle</h2>
<p>A circle is a geometric shape with no sides or corners. It is defined as a set of points that are all the same distance from a central point, known as the center of the circle.</p>
<p>The distance from the center to the edge of the circle is known as the radius. The diameter of a circle is the distance across the circle, passing through the center. The circumference of a circle is the distance around the outside of the circle.</p>
<p>Circles are often used in math and geometry, and they have many practical applications in everyday life, such as in wheels, coins, and circular objects.</p>
User
Application Software
Operating System
Hardware
Assignment #1
•Explain the meaning of this graphics organizer base on what you have learned from this lesson.
• Is an "app" same in meaning with "application"?

Answers
This graphics organizer base talks about Software and how it is divided into two groups such as the operating systems and application software.
What are Software?Software are said to be often shared into two categories such as:
The operating systems The application software.Note that the Operating systems functions by helping the hardware and produce a kind of interface between the hardware and its user while the Application software is said to be a stage of a programs that help the user to do anything meaningful just as seen in the diagram.
Conclusively, The word "app" has the in meaning with "application". It is known to be the short form of application.
Learn more about Application Software from
https://brainly.com/question/1538272
Social media SM. providers host the SM presence using ________ in the cloud.
(1pts)
elastic servers
proxy servers
vanity metrics
viral hooks
Answers
Social media SM is providers host the SM presence using elastic servers in the cloud.
What are SM sites, exactly?Social media refers to as websites and the applications that prioritize collaboration, sharing of content, interaction, and community-based input. People utilize social media to interact and communicate with friends, family, and various communities.
What exactly is the SMM panel and how does it work?Users can use an SMM panel, an online application, to the manage all of their social media profiles. Through the user interface it provides, you may manage your postings, engage with followers, and link your social network accounts.
To know more about Social media visit:-
https://brainly.com/question/14275197
#SPJ4
Drag each tile to the correct location. Identify whether people use personal blogs for each of the following purposes. Drag each phrase to the correct category. share experiences express creativity voice concerns work collaboratively True provide an online forum provide webmail False
Answers
The phrases to the correct category are as follows:
The statement "sharing experiences express creativity voice concerns work collaboratively" is definitely true. The statement "provides an online forum provides webmail" is absolutely false. What do you mean by a Personal blog?A personal blog may be defined as a continuing online diary or commentary that may be written by an individual, rather than a corporation or organization.
According to the context of this question, the intention of making these personal blogs is to aware and inform people about their own life along with entertainment. They share experiences through the expression of creative voices collaboratively.
Therefore, the phrases in the correct category are well described above.
To learn more about blogs, refer to the link:
https://brainly.com/question/17737097
#SPJ1
849 352 768 493 527 sequence
Answers
Look at them like this: Click to show spoiler. Further explanation: Click to show
849, 352, 768, 493, 527 - Unus
which of the following can prolong the life of a computer and conserve resources?
Answers
Practices such as power management, regular maintenance, proper ventilation, surge protection, software optimization, and data management can prolong the life of a computer and conserve resources.
There are several ways to achieve this. One way is by keeping the computer clean and free from dust. Dust can clog up the fans and cause overheating, which can damage the internal components. Another way is to regularly update the computer's software and operating system. Software updates often include bug fixes and security patches, which can help improve the computer's performance and protect it from malware. Additionally, using power-saving settings and turning off the computer when not in use can help conserve energy and prolong battery life.
Lastly, avoiding excessive multitasking and closing unnecessary programs can also help conserve resources and improve the computer's performance.
Learn more about conserve resources: https://brainly.com/question/4722723
#SPJ11
information technology managers are often in a bind when a new exploit (or software vulnerability) is discovered in the wild. they can respond by updating the affected software or hardware with new code provided by the manufacturer, which runs the risk that a flaw in the update will break the system. or they can wait until the new code has been extensively tested, but that runs the risk that they will be compromised by the exploit during the testing period. dealing with these issues is referred to as
Answers
The term that refers to the process of dealing with issues that arise when a new software vulnerability is discovered in the wild is known as Risk Management.
Information technology managers are often in a quandary when a new exploit or software vulnerability is discovered in the wild. They can choose to update the affected software or hardware with the new code provided by the manufacturer, which carries the risk that a flaw in the update will break the system. Alternatively, they can wait until the new code has been extensively tested, but that runs the risk that they will be compromised by the exploit during the testing period.
Risk management refers to the process of identifying, analyzing, and mitigating risks that might adversely affect an organization's ability to achieve its goals. It also entails risk evaluation and prioritization of risks to control or eliminate them. It is necessary to have risk management procedures in place in the event of an unexpected exploit or software vulnerability.
The aim of risk management is to guarantee that the organization is aware of, understands, and handles the hazards it encounters to achieve its objectives.
You can learn more about Risk Management at: brainly.com/question/4680937
#SPJ11
write a loop that counts the number of space characters that appear in the string referenced by my_string
write this in python
Answers
Answer:
1.
my_string = input("Enter a string: ")
count = 0
for c in my_string:
if c == " ":
count += 1
print("Number of spaces in the string:", count)
2.
my_string = input("Enter a string: ")
count = my_string.count(" ")
print("Number of spaces in the string:", count)
Explanation:
in number 1, The code reads a string from the user, then uses a loop to iterate over each character in the string and counts the number of spaces in the string. Finally, the code prints the count of spaces.
This is a simple and straightforward way to count the number of spaces in a string, but using Python's built-in count method (in number 2) would make the code shorter and more efficient.
Answer:
Here's a Python code that uses a loop to count the number of space characters in a given string:
my_string = "Hello world! This is a string with spaces."
count_spaces = 0
for char in my_string:
if char == " ":
count_spaces += 1
print("Number of space characters in the string:", count_spaces)
This code initializes a variable count_spaces to 0 and then loops through each character in the my_string string using a for loop. Inside the loop, it checks whether the current character is a space character by comparing it to the space character " ". If it is, it increments the count_spaces variable by 1.
Finally, the code prints the number of space characters found in the string.
You are a new player in Second Life and are surprised when another avatar asks if you want to buy some marijuana. You are not sure if the person is merely role playing or is serious. What would you do?
Answers
bc it’s good
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
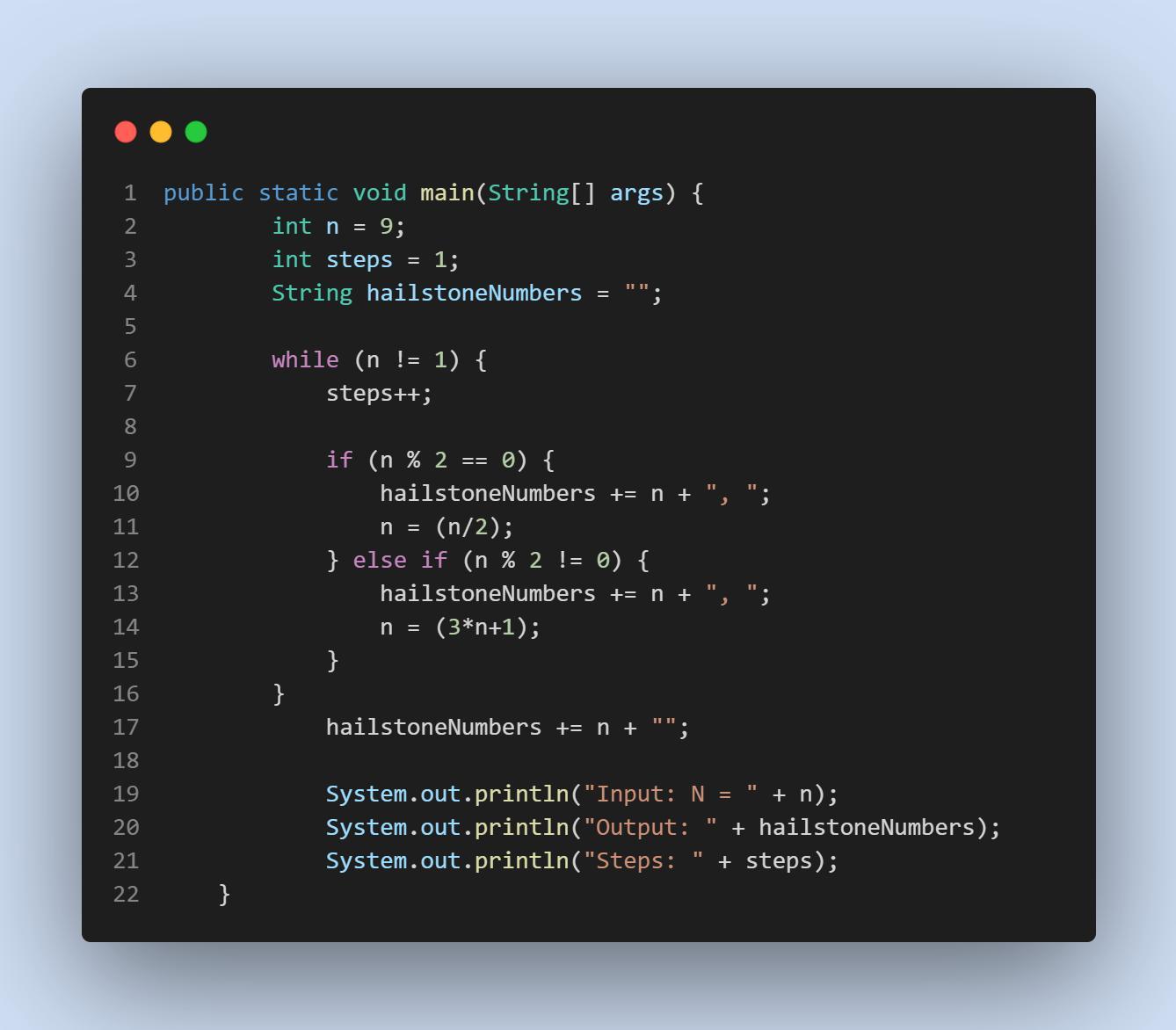
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
Define the term Project brief? why is it important to do planning?
Answers
Answer: the project brief is a document that provides an overview of the project.
Explanation: It says exactly what the designer, architect, and contractor needs to do to exceed your expectations and to keep the project on track with your goals and your budget.
2. Read the following scenarios about how three different programmera approach
programming a computer game. Identify which type of programming design
approach each represents (3 points):
a) Yolanda first breaks down the whole game she needs to program into modules.
She then breaks these modules into smaller modules until the individual parts are
manageable for programming. She writes the smallest modules, and then
recombines them into larger parts.
b) Isabella takes the game process and groups together sets of related data involved
in the process. She then identifies the messages the data should respond to. After
writing the code for each set of data, Isabella then combines, tests, and refines the
subsets until the software runs properly
Answers
a.) Structured programming
b.) Object-oriented programming
c.) Top-down programming
The programming design approach represented in this scenario is modular programming. The programming design approach represented in this scenario is object-oriented programming.
What is programming?The process of creating a set of instructions that tells a computer how to perform a task is known as programming.
Computer programming languages such as JavaScript, Python, and C++ can be used to create programs.
Modular programming is the programming design approach represented in this scenario.
Yolanda divides the entire game into modules, which are then subdivided further into smaller modules until the individual parts are manageable for programming.
Object-oriented programming is the programming design approach represented in this scenario. Isabella organizes sets of related data and determines which messages the data should respond to.
Thus, this method entails representing data and functions as objects and employing inheritance and polymorphism to generate flexible and reusable code.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
Firewall implementation and design for an enterprise can be a daunting task. Choices made early in the design process can have broad security implications for years to come. Which firewall architecture is designed to host servers that offer public services?
Answers
Complete Question:
Firewall implementation and design for an enterprise can be a daunting task. Choices made early in the design process can have far-reaching security implications for years to come. Which of the following firewall architecture is designed to host servers that offer public services?
a) Bastion Host
b) Screened subnet
c) Screened host
d) Screened
Answer:
b) Screened subnet
Explanation:
In Computer science, Firewall implementation and design for an enterprise can be a daunting task. Choices made early in the design process can have far-reaching security implications for years to come.
Screened subnet firewall architecture is designed to host servers that offer public services.
In network security and management, one of the network architecture used by network engineers for the prevention of unauthorized access of data on a computer is a screened subnet. A screened subnet can be defined as a network architecture that uses a single firewall with three screening routers as a firewall.
A screened subnet is also known as a triple-homed firewall, this is because it has three (3) network interfaces;
1. Interface 1: it is known as the external or access router, which is a public interface and connects to the global internet.
2. Interface 2: it is known as the demilitarized zone or perimeter network, which acts as a buffer and hosted public servers (bastions host) are attached herein.
3. Interface 3: it is known as the internal router, which is a subnet that connects to an intranet.
The screened subnet when properly configured helps to prevent access to the internal network or intranet.
Why is it important to understand the default settings?
Why would you customize a document?
Answers
It is important to understand the default settings of a document because they can affect the appearance and functionality of the document.
For example, the default font and margins can affect the readability and layout of the document. Understanding the default settings allows you to make informed decisions about how to customize the document to meet your specific needs.
How can you customize a document?Customizing a document can be done for a variety of reasons. Some common reasons include:
Changing the appearance of the document to match a specific branding or style guideModifying the layout or organization of the document to make it more readable or user-friendlyAdding or removing specific elements from the document, such as images or sectionsAdapting the document for a specific audience or purpose.With this in mind, you can see the importance of understanding default settings and also how to customize a document.
Read more about default settings here:
https://brainly.com/question/29394469
#SPJ1
opinion on sandshrew
Answers
Answer:Sandshrew is cute
Explanation:
The sun has been up for several hours, and it has been shining on these trees.
What can the trees do because they are in sunlight? What does this mean for the number of energy storage molecules in the trees?
The trees can . . .
A. give off carbon to the air. Giving off carbon allows them to make energy storage molecules.
B. give off carbon to the air. Giving off carbon uses up energy storage molecules.
C. take in carbon from the air. The carbon is used to make energy storage molecules.
D. take in carbon from the air. The carbon is used to break down energy storage molecules.
Answers
For some hours now, the light has been beaming on these trees. Because they are in sunlight, The trees can "take in carbon from the air. The carbon is used to make energy storage molecules." (Option C).
What is the above process called?The above process is called Photosynthesis. Photosynthesis is the process through which plants convert sunlight, water, and carbon dioxide into oxygen and sugar energy.
Photosynthesis is the process through which plants and other organisms convert light energy into chemical energy, which is subsequently released to fuel the organism's activities through cellular respiration.
Photosynthesis has the following characteristics: It is a process that happens only in plants that have the green pigment chlorophyll, which is utilized to manufacture food. Sunlight, water, and oxygen are required, and two processes occur, one light-dependent and one light-independent.
Learn more about trees:
https://brainly.com/question/11076581
#SPJ1
Elements such as page parts and calendars are easily inserted by navigating to the _____ grouping. Building Blocks Illustrations Text Page Design
Answers
Answer:
Building Blocks
Explanation:
When referring to the Publisher Application the navigation feature that allows you to do this is the Building Blocks feature. Like mentioned in the question this feature allows you to choose from and insert a predefined set of calendars for insertion into a publication as well as insert a variety of other page parts to better customize the feel of the publication.
which method is used over ieee 802.11 wlans to limit data collisions caused by a hidden node?
Answers
The method used over IEEE 802.11 WLANs to limit data collisions caused by a hidden node is called the Clear Channel Assessment (CCA) mechanism. When a wireless device wants to transmit data, it first performs a CCA to check if the channel is clear.
If it detects a signal from another device, it will not transmit and will wait until the channel is clear. This helps prevent collisions and ensures that the data is transmitted successfully. However, in situations where there is a hidden node (i.e. a device that is out of range or cannot be detected by other devices), the CCA mechanism may not work effectively. In such cases, other methods such as Request to Send (RTS) and Clear to Send (CTS) may be used to prevent collisions and ensure successful data transmission.
In summary, the CCA mechanism is the primary method used to limit data collisions over IEEE 802.11 WLANs, but other methods may be employed in situations where a hidden node is present.
To know more about WLANs visit:-
https://brainly.com/question/31493155
#SPJ11
similarities between two printers
Answers
1. what is the correct GPO settings? /force GPO gpupdate /now policyupdate /force
2. why is it important to set a strict password policy as part of your security template?
3. why is it important to bring standalone systems into the Domain?
4. what was the command line syntax to connect as the root user to 172.30.0.11 using PUTTY?
5. name five different Windows password policies.
6. what is the purpose of the business impact analysis (BIA)?
7. What is the difference between a disaster recovery plan (DRP), and a business continuity plan (BCP)?
8. what are the commands used in windows 2012 to mount the NFS share on the Linux server
9. Is creating redundancy for systems such as Active Directory or Web servers a part of the DRP or the BCP?
10. Why use the mklink command?
Answers
1. Correct GPO settings is gpupdate /force
2. Strict password policy enhances overall security by preventing weak passwords.
3. Bringing standalone systems into the Domain improves centralized management and security.
4. Command to connect as root user to 172.30.0.11 using PuTTY: "putty -ssh rootat172.30.0.11"
5. Windows password policies: complexity, length, history, lockout, and expiration.
6. Business Impact Analysis (BIA) identifies critical processes and their potential impacts.
7. DRP focuses on recovering from disasters, while BCP ensures business continuity.
8. Commands to mount NFS share on Windows Server 2012: "mount -o anon 172.30.0.11:/share Z:"
9. Redundancy for systems like Active Directory or Web servers is part of the BCP.
10. The mklink command creates symbolic or hard links in Windows.
What is the explanation for the above?1. The correct GPO settings are applied using the command "gpupdate /force" to enforce policy updates immediately.
2. Setting a strict password policy is important to prevent weak passwords that can be easily compromised, enhancing overall security.
3. Bringing standalone systems into the Domain improves security and enables centralized management, ensuring consistent policies and controls.
4. To connect as the root user to 172.30.0.11 using PuTTY, use the command "putty -ssh rootat172.30.0.11" in the command line.
5. Windows password policies include complexity (requiring a mix of characters), length, history, lockout, and expiration requirements.
6. The purpose of a Business Impact Analysis (BIA) is to identify critical processes and assess their potential impacts on business operations.
7. A Disaster Recovery Plan (DRP) focuses on recovering from disasters, while a Business Continuity Plan (BCP) ensures ongoing business operations.
8. In Windows Server 2012, the commands "mount -o anon 172.30.0.11:/share Z:" are used to mount an NFS share on a Linux server.
9. Creating redundancy for systems like Active Directory or Web servers is typically part of the Business Continuity Plan (BCP).
10. The "mklink" command in Windows is used to create symbolic or hard links between files or directories.
Learn more about GPO settings:
https://brainly.com/question/14301506
#SPJ1
2. How can Tailwind Traders ensure applications use geo-redundancy to create highly available storage applications?
Answers
Tailwind Traders CAN ensure applications use geo-redundancy to create highly available storage applications by:
Running one's application in read-only mode.Enforcing its use.What is geo redundant storage?Geo-redundant storage (GRS) is known to be a device that tends to copy one's data synchronously three times in the same or inside a single physical location in the primary region via the use of LRS.
Note that in the case above, Tailwind Traders CAN ensure applications use geo-redundancy to create highly available storage applications by:
Running one's application in read-only mode.Enforcing its use.Learn more about Geo-redundant storage from
https://brainly.in/question/6073238
#SPJ1
working on a python assignment, not sure what i did wrong can anyone help?

Answers
Answer:
Explanation:
line 13 should be changed to:
print(“Item 1: “ + item1 + “ - $” + str(float(const1)))
You cannot concatenate a string to float type.
As Muslim scholars fled into India in the 1200s C. E. , they brought with them the learning of what three cultures
Answers
Muslim scholars brought the learning of Persian, Arab, and Central Asian cultures to India in the 1200s C.E., influencing various aspects of Indian society and enriching the intellectual landscape.
As Muslim scholars fled to India in the 1200s C.E., they brought with them the learning and knowledge of three main cultures: Persian, Arab, and Central Asian. These cultures had a rich intellectual heritage, including advancements in various fields such as science, mathematics, philosophy, literature, and art. The scholars who migrated to India played a significant role in shaping and enriching the intellectual and cultural landscape of the region. They contributed to the development of Indo-Islamic civilization, blending their own cultural traditions with the existing Indian traditions. This exchange of knowledge and ideas had a profound impact on various aspects of Indian society, including language, literature, architecture, music, and religious practices. The influence of Persian, Arab, and Central Asian cultures can still be observed in different aspects of Indian culture today.
learn more about Muslim scholars here:
https://brainly.com/question/24284868
#SPJ11
A piece of hardware used to enter data into a computer: Output Device Backing Storage Device Programming language Input Device
Answers
Answer:
Input Device.
Explanation:
A piece of hardware used to enter data into a computer is known as an input device.
Basically, this input device is also known as peripherals and it comprises of all of the devices that are interconnected with the CPU. Some examples of input devices used with a computer includes keyboards, scanner, mouse, etc. They avail the end users the ability to send an information to the computer system for processing into a desired output.
BLANK refer to system maintenance activities such as backups and file management.
Remote desktop service
Network management services
Network encryption
BLANK provide features to prevent unauthorized access to the network.
Security services
File replication services
Printing services
Answers
Network management services
Second answer:
Security services
to cache nodes in a graph, a bfs traversal uses a _____ data structure and a dfs traversal uses a _____ data structure.
Answers
BFS uses a queue, and DFS uses a stack to cache nodes in a graph.
Breadth-First Search (BFS) uses a queue data structure to cache nodes in a graph. It starts by visiting the initial node, then explores its neighboring nodes before moving to the next level. By using a queue, BFS ensures that nodes are processed in the order of their depth from the starting node, resulting in a breadth-first traversal. On the other hand, Depth-First Search (DFS) uses a stack data structure to cache nodes. It explores the graph by going as deep as possible before backtracking. The stack allows DFS to prioritize deeper nodes, resulting in a depth-first traversal.
learn more about cache nodes here :
https://brainly.com/question/31481786
#SPJ11