The ____________ layer of the osi model is responsible for data format translation
Answers
Answer:
Presentation
Explanation:
The sixth layer of the OSI model, responsible for translation, encryption, authentication, and data compression.
Related Questions
Which of these might cause a STOP error in Windows? Select 2 options. bad application coding bad or incompatible driver overheating an application stops responding to commands a missing image on a web page
Answers
Answer:
i think its bad driver and coding
Explanation:
The STOP error in Windows can be found with bad application coding or bad or incompatible driver. Thus, options A and B are correct.
What is a STOP error?STOP error in windows can be given as the blue and death screen. The screen has been found in the operating system with the fatal error and gave rise to the development of a bug enabling the operation.
The error causes the system to shut down or restart the computer system. The error can be fixed by restarting the computer or updating the windows, and other ways.
The error in Windows such as STOP can be found for the reasons such as bad coding for the application, or the incompatible driver installed in the system that gave rise to inappropriate working. Thus, options A and B are the correct reasons for the STOP error in windows.
Learn more about STOP error, here:
https://brainly.com/question/15031386
#SPJ5
if you go over 255 in RGB by 1 does it reset to 0 or 1
Answers
Answer:
With Apple i remember it was 1.
10. Two technicians are discussing recycling specifications for refrigerant. Technician A says that refrigerant oil with 5,000 parts per million (ppm) does not fall
within specifications. Technician B says that air can only have a maximum of 330 ppm. Who is correct?
O A. Neither Technicians A and B
OB. Technician B
O C. Both Technicians A and B
O D. Technician A
Answers
Two technicians are discussing recycling specifications for refrigerant Technician A is correct.
What is the recycling ?Recycling is the process of transforming waste materials into new products to prevent the waste of potentially useful materials and reduce the consumption of fresh raw materials. It is an important part of the global economy and helps to preserve the environment by reducing energy usage, air and water pollution, and reducing the amount of waste sent to landfills. Recycling can be done through mechanical means such as shredding or separation, or through chemical processes such as melting and reforming.
To learn more about recycling
https://brainly.com/question/27248056
#SPJ1
Create a C++ program to compute the average of three tests or quizzes and display the score and average on distinct lines, and do it using arithmetic operators.
Answers
#include <iostream>
#include <vector>
#include <numeric>
int main() {
std::vector<int> store(3);
for(int i=0;i<3;i++){
std::cout << i+1 << ". test result: ";
std::cin>>store[i];
}
for(int i=0;i<3;i++) {
std::cout << i+1 << ". test score: " << store[i] << std::endl;
}
std::cout << "Average: " << double(std::accumulate(store.begin(),store.end(),0.0)/store.size()) << std::endl;
return 0;
}
________ operating systems are used to control and coordinate computers that are linked together. group of answer choices embedded stand-alone network real-time
Answers
Network operating systems are used to control and coordinate computers that are linked together.
Network operating systems are specifically designed to control and coordinate computers that are interconnected within a network.
These operating systems provide features and functionalities that facilitate sharing resources, such as files, printers, and applications, among multiple computers in the network.
Network operating systems also handle network communication protocols, security, user authentication, and centralized management of network resources.
Learn more about Operating system here:
https://brainly.com/question/33634948
#SPJ4
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
I get such an error when I turn on the computer, how can I fix it?

Answers
Answer:
Use the HLL ( Java C++ ) code to fetch the commands of that program, then translate them using any translatory program such as Microsoft notepad.
Or:
Download any utility software such as Avast, thunderbird, Dr. Solomon, or Norton software
Then install it to memory.
Why can a bank afford to pay an interest rate on a savings account?
A.
Because the bank is insured by the FDIC
B.
Because the Fed prints more currency when needed
C.
Because the bank puts the money into equity investments
D.
Because the bank lends that money out at a higher interest rate
Answers
Answer:
D
Explanation:
Because the bank lends that money out at a higher interest rate
KEEP IN TOUCH IF YOU NEED ANYTHING.
which of the following are true regarding making random numbers in python? the random() function, like other languages, can be used to generate random numbers. to display a random number between 1 and 13: import random print(random.randrange(1,13)) to generate a random number or numbers, start with: import random python has the option to utilize the random module. to display a random number between 1 and 13: import random print(random.randrange(1,14))
Answers
Options B, C, and D are true regarding making random numbers in Python.
Option B is true because in Python 'import random print(random.randrange(1 ,13))' generates a random number between 1 and 13 inclusively. The 'randrange()' function in Python returns a randomly generated number from the range specified. Option C is true because to create one or more random numbers in Python, it is required to start with 'import random'. Option D is true because Python has the option to utilize a 'random module' in order to generate random numbers. True options are as follows:
To create a random number between 1 and 13: import random print(random.randrange(1,13)) To produce a random number or numbers, start with: 'import random' Python has the option to use the 'random module'You can learn more about random numbers in python at
https://brainly.com/question/20693552
#SPJ4
In Python, what is the major difference between dictionaries and strings?
A) Dictionaries hold any data type, while strings hold only keys.
B) Dictionaries hold only keys, while strings hold integers that code letters.
C) Strings cannot be changed after creation, while dictionaries can be changed.
D) Strings hold only characters, while dictionaries hold any data type
Answers
Answer:
C) Strings cannot be changed after creation, while dictionaries can be changed.
A(n) _____ is any piece of data that is passed into a function when the function is called.
a. global
b. argument
c. scope
d. parameter
Answers
The correct option b. argument; Any piece of information supplied into a function when it is called is known as an argument.
Describe the term argument and its features?You can provide a function more information by using an argument.
The data can then be used by the function as a variable as it executes. To put it another way, when you construct a function, you have the option of passing data as an argument, also known as a parameter.Variables only used in that particular function are called arguments.When we call the function, you must specify that value of an argument.Function arguments provide your applications access to more data.Using justifications
1. Change the function prototype as well as implementation such that a string argument is accepted:howMuchFun=string(string amount);2. Modify the return statement to read "fun" plus the return amount;3. Insert the string howMuchFun between the parentheses wherever you call the function ("tons of")Thus, any piece of information supplied into a function when it is called is known as an argument.
To know more about the argument, here
https://brainly.com/question/29223118
#SPJ4
Why is it hard for an ethical hacker to avoid breaking any laws?
Answers
As an ethical hacker, it can be challenging to avoid breaking any laws because the activities involved in hacking, such as scanning networks, testing software, and exploiting vulnerabilities, may be prohibited by the law.
Moreover, hacking may violate terms of service or contracts that are legally binding. Additionally, some hacking techniques may unintentionally disrupt systems or cause damage, leading to potential liability issues. Therefore, ethical hackers need to be well-versed in the laws and regulations governing their activities and should take appropriate measures to ensure compliance such as obtaining permission from system owners and using only approved tools and methods.
In short, ethical hacking requires a deep understanding of the legal framework and responsible behavior to avoid any legal issues.
Learn more about ethical hacker: https://brainly.com/question/24119349
#SPJ11
in what order is the following code processing the image pixels?
Answers
The order of processing can vary depending on the programming language, libraries, and algorithms used in the code.
The order in which the code processes image pixels depends on how the code is written and the underlying image processing algorithms employed. Different programming languages and libraries may have different conventions or default behaviors for handling images, such as row-major or column-major order.
In general, image pixels can be processed in a sequential manner, where each pixel is processed one after another in a specific order. This can be row-wise, column-wise, or using a different scanning pattern such as a diagonal scan.
Alternatively, image processing algorithms may employ parallel processing techniques, where pixels are processed concurrently using multiple threads or processes. In such cases, the order of processing may not follow a sequential pattern.
Learn more about algorithms here:
https://brainly.com/question/21172316
#SPJ11
Question 6 [10 marks] a) How does a company's use of information systems affect its corporate strategies? (7 marks) b) Provide an example. (3 marks)
Answers
Answer:
following are the responses to the given question.
Explanation:
The capability to successfully utilize IT is mutually dependent on its ability to execute strategic strategy and set business goals. The ability to compete more and more relies on the capacity of an organization of using technology. In the future, what a company wants to do will rely on what its technologies can do. It may be an example of a company investing in information technology that allows a company to manufacture new products or improve the efficiency of the distribution system to the corporation's economic efficiency.
How do I do this?
Someone Please help

Answers
Answer:
I am done solving there was a synthetic error very sorry I tried to help for 30mins
In cell H4 create a formula without a function that adds 14 days to the date the client was last contacted cell G4
Answers
Which should be addressed by stakeholders when reviewing the problem statement? Select all that apply.
All possible outcomes have been thoroughly researched and rejected.
The problem as they see it has been addressed.
The solution proposed will meet their needs.
The needs of their colleagues are being met.
All issues and constraints have been identified.
Answers
The statement that should be addressed by stakeholders when reviewing the problem statement are the problem as they see it has been addressed, the solution proposed will meet their needs and all issues and constraints have been identified.
What are the elements of an effective problem statement?An effective problem statement includes the description of the problem and the method that will be used to solve the problem.
The problem as they see it has been addressed, the solution proposed will meet their needs and all issues and constraints have been identified are the statement that should be addressed by stakeholders when reviewing the problem statement.
Therefore, B, C and E are the correct options.
Learn more about problem statement here:
https://brainly.com/question/11657822
#SPJ1
Samiyah is playing a game that mainly uses black and gray colors. What mood is most likely being portrayed?
A.
joy and happiness
B.
energy and strength
C.
anger and violence
D.
fear and horror
Answers
Answer: D
Explanation:if u want to go into details we can but its the answer trust me
Please post detailed answers to the following questions. Please use complete sentences.
The COVID-19 pandemic in 2020 provided an opportunity for companies to explore allowing their employees to work remotely. Briefly describe what remote working is, what you think the pros and cons of remote working are, and if you think that you could be successful in a remote working environment.
Answers
Remote working, also known as telecommuting, refers to working from a location outside of the traditional office setting, often from home or other remote locations.
What are the benefits?Remote working offers several benefits, including flexibility in work schedules, increased productivity, reduced commuting time and costs, and access to a broader pool of talent. H
However, it also comes with potential challenges, such as difficulty in separating work and personal life, reduced face-to-face interactions, and lack of direct supervision.
Read more about telecommuting here:
https://brainly.com/question/29645344
#SPJ1
A subquery whose return value depends on the row being returned in a main query is called a(n) _____ query.
Answers
Answer:
correlated
Explanation:
A correlated subquery is a method of reading each row of a table and comparing the values in each row to related data. It's utilized when a subquery has to deliver a different result or collection of results for each candidate row that the main query considers. I hope this helps! ^-^
Please! I need help matching this.
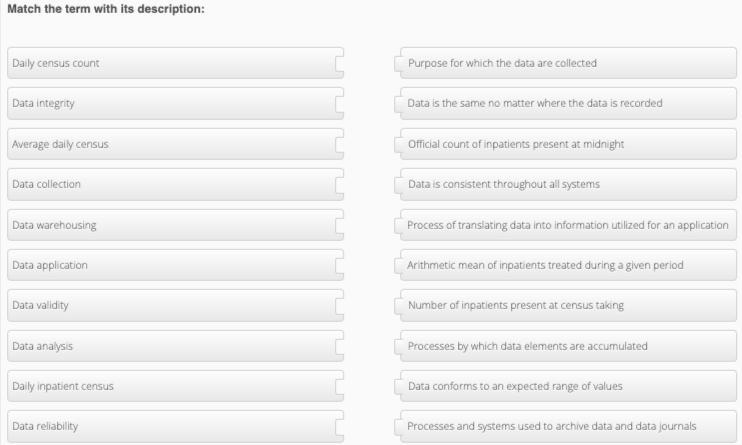
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
What is the difference between an open network and a secure network?
Answers
An open network is a network that allows any device to connect to it without any restrictions or authentication, while a secure network is a network that has some level of security measures in place to prevent unauthorized access.
An open network is convenient because it allows anyone to easily connect to it, but it can also be vulnerable to security risks because it lacks any protection against unauthorized access. In contrast, a secure network uses various security measures such as encryption, authentication, and access controls to prevent unauthorized access and protect the data transmitted over the network. As a result, secure networks are generally more secure than open networks, but they may require additional setup and configuration.
What are attributes and what role do they play with in a HTML document?
Answers
Answer:
HTML attributes are special words used inside the opening tag to control the element's behavior. HTML attributes are a modifier of an HTML element type. An attribute either modifies the default functionality of an element type or provides functionality to certain element types unable to function correctly without them.
Explanation:
you need to stop an application from running in the task manager. which tab should you use to accomplish the task?
Answers
You need to stop an application from running in the task manager. Detail tab should you use to accomplish the task.
What is the 'Details' tab?
Game Analytics' 'Details' tab contains many statistics about the moves made in the game, as well as details about who won how and when the game was played. is also displayed. You can see the priority of each process on the Details tab.
Windows schedules process threads based on this ranking. However, you can do more on the Details tab and change the process priority.
What is the Details Tab in Salesforce?The Record Info Tabs component displays detailed record information, a list of related records, and a record feed.
Learn more about task manager:
brainly.com/question/6500846
#SPJ4
Write the pronoun that best completes the sentence. Dad gave Harry and ___ two $5 bills.
Answers
The correct pronoun in this context is: "Dad gave Harry and I two $5 bills.
What is a Pronoun?This refers to the term that is used to describe and define the part of speech that is used to show the word that is used in the place of a noun in a sentence.
Hence, it can be seen that the given sentence needs to replace the noun of the name of the speaker and then the personal pronoun "I" is the most appropriate pronoun to use to complete the sentence in this case.
Read more about pronouns here:
https://brainly.com/question/26102308
#SPJ1
If you forget your privacy password what will you do if the ask this question what is the name of one of your teacher?
Answers
Explanation:
you write the name of your primary school teacher
A security question is a form of the shared secret used as an authenticator. The answer to questions asked by the system is personalized and can be answered by you only.
What are security questions?A security question is a form of the shared secret used as an authenticator. It is commonly used by banks, cable companies, and wireless providers as an extra security layer.
When you forget your privacy password, the system tries to help you to get your password back or reset it. But for this, it needs to make sure that it's you. Therefore, whenever you set a privacy password for the first time the system also asks you a few questions these questions are known as security questions and are present in the system for such situations. Therefore, the answer to questions asked by the system is personalized and can be answered by you only.
Learn more about the Security Questions:
https://brainly.com/question/15008697
#SPJ2
A(n) ____ is perceived as a two-dimensional structure composed ofrows and columns.
a.table
c.attribute
b.rowset
d.intersection
Answers
A(n) table is perceived as a two-dimensional structure composed ofrows and columns.
The correct option is A.
A table is a structured arrangement of data in rows and columns. It is commonly used to organize and present information in a clear and organized manner.
Each row represents a separate record or observation, while each column represents a specific attribute or variable. The combination of rows and columns creates a two-dimensional structure that allows for easy comparison and analysis of the data.
Tables are widely used in various fields, including data analysis, statistics, databases, and spreadsheets, to present data in a structured format.
Learn more about Table here:
https://brainly.com/question/33917017
#SPJ4
what is memory?
How many type of memory in computer system?
Answers
Memory is the process of taking in information from the world around us, processing it, storing it and later recalling that information, sometimes many years later. Human memory is often likened to that of a computer memory.
How many type of memory in computer system?two typesMemory is also used by a computer's operating system, hardware and software. There are technically two types of computer memory: primary and secondary. The term memory is used as a synonym for primary memory or as an abbreviation for a specific type of primary memory called random access memory (RAM).Hope it helps you my friendHave a great day aheadGood morning friendExplain network representation and how they are used in network topologies
Answers
Answer:
Network topology is the way a network is arranged , including the physical or logical description of how links and nodes are set up to relate to each other.
What are the five types of alignment in Word? side, middle, top, bottom, and graphing left, center, right, decimal, and bar tab, alt, shift, control, and function page layout, review, view, references, and insert
Answers
Answer:
side, middle, top, bottom, and graphing.
Explanation:
Answer: A. side middle top bottom and graphing
Explanation: Saw it on Edgen.