the first "killer application" for the arpanet was
Answers
The first "killer application" for the ARPANET was the email. ARPANET was the first operational packet-switching network, and its goal was to enable computers to communicate with each other.
It was developed by the Advanced Research Projects Agency (ARPA) of the U.S. Department of Defense in the late 1960s and early 1970s. Email was a groundbreaking application because it allowed people to communicate quickly and easily with each other over long distances. At that time, there was no other way to send messages electronically over long distances besides using snail mail, which was a slow and cumbersome process.Email was initially designed as a way for researchers and scientists to communicate with each other over the ARPANET, but it quickly became popular with the general public.
It revolutionized the way people communicated and paved the way for the development of other internet applications such as instant messaging, social media, and video conferencing.In conclusion, the email was the first "killer application" for the ARPANET. It was groundbreaking because it allowed people to communicate quickly and easily with each other over long distances, revolutionizing the way people communicated and paving the way for the development of other internet applications.
Learn more about ARPANET here,https://brainly.com/question/14823958
#SPJ11
Related Questions
If you Buy my group clothing in R.o.b.l.o.x for a donation i will make you brainliest
My group is One Percenters
Answers
Answer:kk ima do it
Explanation:
Answer:
this and that
Explanation:
this and that
"If a security measure or control has failed for whatever reason, the system is not rendered to an insecure state" is a statement of what security principle?
Answers
The security principle is referred to as "defense in depth," and it means that a system should not be entirely reliant on a single security measure or control to keep it secure.
A failure of any one security mechanism does not imply that the system is insecure. Instead, a system should be safeguarded by a variety of security measures that can detect and avoid assaults. No security mechanism is ideal, and no security mechanism can prevent all attacks. As a result, security measures must be used in layers, each layer improving the security of the system.
Therefore, it is the responsibility of security managers and system administrators to put in place a multi-layered security strategy that is resilient to a wide range of threats and cyber attacks. It can be concluded that "if a security measure or control has failed for whatever reason, the system is not rendered to an insecure state" is a statement of the "defense in depth" security principle. The defense in depth principle acknowledges that a system cannot be fully secured with a single security mechanism or control. Instead, several security measures are used in layers to keep the system secure from potential threats.
A security failure in one layer should not compromise the system's security because other layers can compensate for the failure. As a result, a multi-layered security approach should be implemented to ensure the security of the system.
Learn more about defense in depth here,
https://brainly.com/question/30395225
#SPJ11
er reports that he is having problems with his monitor. He explains that his laptop's liquid crystal display (LCD) is no longer spreading the light over the entire screen. Which component of the LCD is most likely causing this problem?
Answers
Answer:
diffuser
Explanation:
Based on the scenario being described, the most likely cause of the problem is a bad diffuser. This is a component found in nearly every type of LCD backlit displays and are used to produce an even array of lighting across the entire display. If this component fails then it will cause bright spots and dim spots throughout the display, similar to what the client is reporting in this scenario since the light is not being evenly distributed.
What would happen if computers only had input devices?
Computers would process and display data.
O Computers would receive input and process data.
Computers would receive input, process, and print data
Computers would receive input and display data.
Answers
Answer:
B. Computers would receive input and process data
Explanation:
Without and output device, the computer can't display the data so they would only be able to receive and process the data but not display it.
this is pixlr
You have an image of a building, but people are standing on the far left side. You will like to remove those people. Which tool do you need?
Cropping
Clipping
Snipping
Cutting
You want to transform an image with artistic effects. Which menu would you look under?
Filter
Edit
View
File
Sharing an image online generally, requires which of the following?
Low resolution
High resolution
Blurring
Kaleidoscope
You have been asked to design a logo for community organizations. What kind of image would you create?
Raster
Vector
Transparent
Opaque
Answers
2 - Filter
3 - High Resolution
4 - Opaque
Thank you!
what determines the size of words in a word cloud?
Answers
A word appears bigger and bolder in the word cloud the more times it appears in a textual data source (such as a speech, blog post, or database).
What is the word cloud's word density?A word's size in the word cloud varies depending on how frequently it appears in the input text. You can see and change that frequency in the word list.
What is the optimum word count for a word cloud?Word clouds often appear better with 20–100 words or phrases, although there is a broad range of freedom in the format options. Depending on how big your display is, if you choose too many words, they can end up being too small to read.
To know more about word cloud visit:-
brainly.com/question/5273607
#SPJ1
Unit and begin planning and creating an original video game, in the style of The Oregon Trail, which will be used to educate people on the real historical struggles the Native Americans had during the Trail of Tears resettlement in 1830. Start by reviewing the source provided, taking notes of what aspects you want to include in your game.
Each game must have the following parts:
A) A paragraph like the one written for The Oregon Trail, which explains the overall point of the game, while also using language which makes the reader want to play the game.
B) Two scenarios the player will face in the game, explained in a paragraph each, what happens in the scenario, what two or three outcomes are possible, and why you chose to include it in your game.
C) A paragraph explaining what the best & worst case scenarios of your game are, with an explanation of why you chose this.
Answers
The total point of our game, "Trail of Tears: The Journey of the Native Americans," is to educate players on the real historical struggles faced by the Native Americans during the Trail of Tears resettlement in 1830.
As players journey along the trail, they will encounter various challenges and decisions that the Native Americans faced during this time period.
By immersing themselves in the game, players will gain a deeper understanding and appreciation for the hardships and triumphs of this significant event in history.
What is the scenario in the game about?One scenario the player will face in the game is the decision to rest or push on. As the player travels along the trail, they will have the option to stop and rest at a campsite or to continue on to the next destination. If the player chooses to rest, they will have the chance to heal injuries and gather resources, but it will also cost them time.
On the other hand, if the player chooses to push on, they may be able to make up time, but they risk further injury and depletion of resources. The outcome of this scenario will depend on the player's strategy and the resources they have available.
Another scenario the player will face is the decision to trade with or avoid other groups on the trail. As the player encounters other Native American tribes and settlers, they will have the option to trade goods and resources or to avoid interaction. If the player chooses to trade, they may be able to acquire valuable resources, but they also risk losing some of their own.
Therefore, In the best case scenario, the player will successfully navigate the Trail of Tears and arrive at their destination with a deep understanding and appreciation for the struggles faced by the Native Americans during this time period
Learn more about gaming from
https://brainly.com/question/27355039
#SPJ1
I keep having trouble with my IXL's is there anyway anyone can help me?
Answers
Arthur Meiners is the production manager for Wheel-Rite, a small manufacturer of metal parts. Wheel-Rite sells 10,378 gear wheels each year. Wheel-Rite setup cost is $45 and maintenance cost is $0.60 per sprocket per year. Wheel-Rite can produce 493 gear wheels per day. The daily demand for the gear wheels is 51 units. Show your work.
1. What inventory management model should we use to solve this problem?
Model for discount purchases
Model Economic Quantity to Order
Model Economic Quantity to Produce
Model to handle dependent demand
2. What is the optimal amount of production? 3. What is the maximum inventory level of gear wheels that will be in the Wheel-Rite warehouse? 4. What is Wheel-Rite's annual setup cost? 5. What is the annual cost of maintaining Wheel-Rite?
Answers
2. To calculate the optimal amount of production using the EOQ model, we need the following information:
- Demand per year (D) = 10,378 gear wheels
- Setup cost (S)= $45
- Production rate per day (P) = 493 gear wheels
- Working days per year (W) = 365 (assuming no downtime)
The formula to calculate the EOQ is:
EOQ = sqrt((2 * D * S) / (P * (1 - (D / (P * W)))))
Plugging in the values:
EOQ = sqrt((2 * 10,378 * 45) / (493 * (1 - (10,378 / (493 * 365)))))
Calculating this equation will give you the optimal amount of production.
3. The maximum inventory level of gear wheels that will be in the Wheel-Rite warehouse can be calculated by multiplying the optimal amount of production (EOQ) by the number of production cycles in a year. The number of production cycles can be calculated by dividing the annual demand (D) by the optimal amount of production (EOQ) and rounding up to the nearest whole number.
Maximum inventory level = EOQ * ceil(D / EOQ)
4. Wheel-Rite's annual setup cost can be calculated by multiplying the setup cost (S) by the number of production cycles in a year.
Annual setup cost = S * ceil(D / EOQ)
5. Wheel-Rite's annual cost of maintaining inventory can be calculated by multiplying the holding cost per unit (which is the maintenance cost per sprocket per year) by the average inventory level. The average inventory level can be calculated by dividing the maximum inventory level by 2.
Annual cost of maintaining inventory = (Holding cost per unit) * (Average inventory level)
In this case, the holding cost per unit is $0.60 per sprocket per year, and the average inventory level can be calculated as (Maximum inventory level / 2).
Please note that you need the calculated EOQ value from question 2 to answer questions 3, 4, and 5.8
Q3. The 1st day of 2022 was Saturday, write a program to input any day number within the month of January and print which day was it. Also check whether the day number entered is a valid date or not.
For example, Input:
Enter day number: 20 Output: Thursday
Input:
Enter day number: 30
Output: Sunday Input:
Enter day number: 34 Output: Invalid day number
Answers
Answer: Here's the code if you solve it using python
Explanation:
day="Saturday"
date=int(input("Enter the day number: "))
if (date<=0) or (date>31):
print("Invalid day number")
else:
if date%7==1:
day="Saturday"
elif date%7==2:
day="Sunday"
elif date%7==3:
day="Monday"
elif date%7==4:
day="Tuesday"
elif date%7==5:
day="Wednesday"
elif date%7==6:
day="Thursday"
elif date%7==0:
day="Friday"
print(day)
Let's see
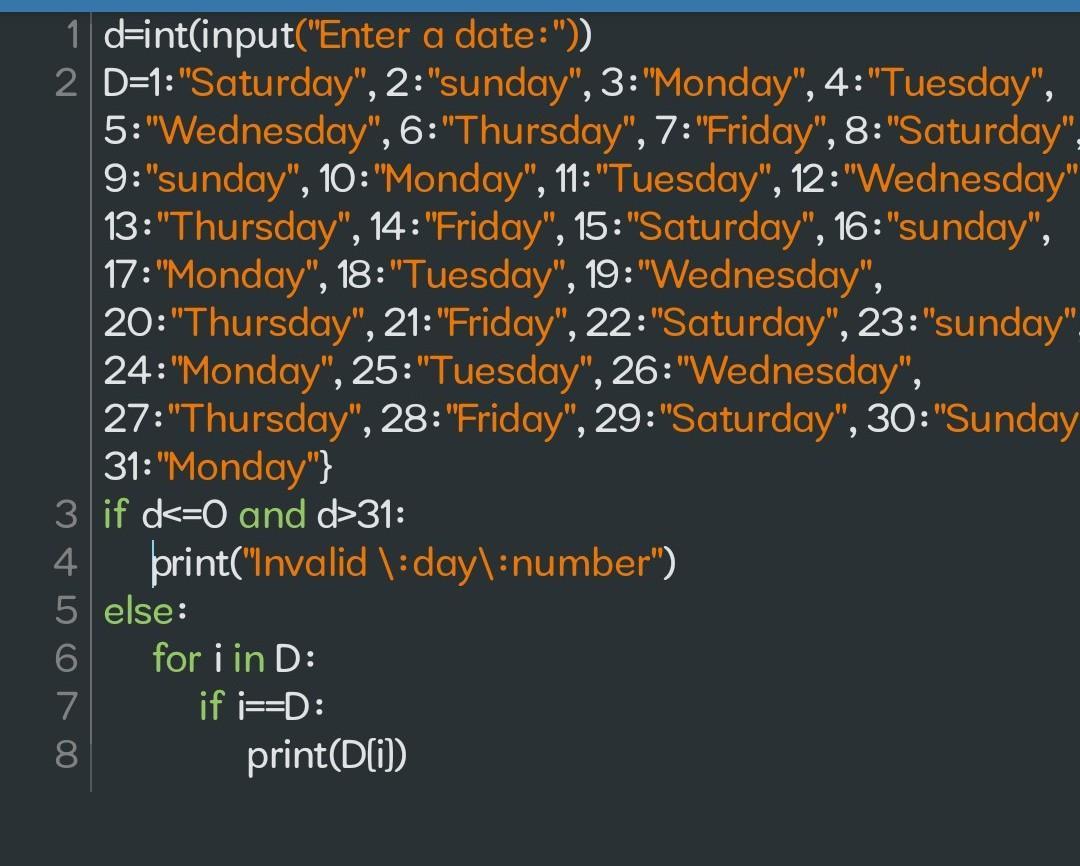
\(\tt d=int(input("Enter \:a \:date:"))\)
\(\tt D=\left\{1:"Saturday",2:"sunday",3:"Monday",4:"Tuesday",5:"Wednesday",6:"Thursday",7:"Friday",8:"Saturday",9:"sunday",10:"Monday",11:"Tuesday",12:"Wednesday",13:"Thursday",14:"Friday",15:"Saturday",16:"sunday",17:"Monday",18:"Tuesday",19:"Wednesday",20:"Thursday",21:"Friday",22:"Saturday",23:"sunday",24:"Monday",25:"Tuesday",26:"Wednesday",27:"Thursday",28:"Friday",29:"Saturday",30:"Sunday",31:"Monday"\right\}\)
\(\tt if\:d<=0\:and\:d>31:\)
\(\quad\tt print("Invalid \:day\:number")\)
\(\tt else:\)
\(\quad\tt for\:i\:in\:D:\)
\(\quad\quad\tt if\:i==d:\)
\(\quad\quad\quad\tt print(D\left[i\right])\)
Kerri uses a photo editing program a lot. To increase her productivity, she should_____.
delete it from the Start menu
put it in her My Documents folder
move the program to the desktop
create a shortcut for it on Quick Launch
Answers
Answer:
Move the program to the desktop
Explanation:
It will be easier to access and quicker to open.
17. Electrospinning is a broadly used technology for electrostatic fiber formation which utilizes electrical forces to produce polymer fibers with diameters ranging from 2 nm to several micrometers using polymer solutions of both natural and synthetic polymers. Write down 5 different factors that affect the fibers in this fabrication technique. (5p) 18. Write down the definition of a hydrogel and list 4 different biological function of it. (Sp) 19. A 2.0-m-long steel rod has a cross-sectional area of 0.30cm³. The rod is a part of a vertical support that holds a heavy 550-kg platform that hangs attached to the rod's lower end. Ignoring the weight of the rod, what is the tensile stress in the rod and the elongation of the rod under the stress? (Young's modulus for steel is 2.0×10"Pa). (15p)
Answers
The elongation of the rod under stress is 0.09 m or 9 cm. Five factors that affect the fibers in electrospinning fabrication technique.
1. Solution properties: The solution concentration, viscosity, surface tension, and conductivity are examples of solution properties that influence fiber morphology.
2. Parameters of electrospinning: Voltage, flow rate, distance from the needle to the collector, and needle gauge are examples of parameters that influence the fiber diameter and morphology.
3. Physicochemical properties of the polymer: The intrinsic properties of the polymer chain, such as molecular weight, crystallinity, and orientation, influence the morphology and properties of the fibers.
4. Ambient conditions: Humidity, temperature, and air flow rate can all influence fiber morphology.
5. Post-treatment: Electrospun fibers can be subjected to post-treatments such as annealing, solvent treatment, and crosslinking, which can influence their mechanical, physical, and chemical properties.Answer to question 18:A hydrogel is a soft, jelly-like material that is primarily composed of water and a polymer network. Hydrogels have a range of biological functions due to their properties such as mechanical and biocompatible. Some of the biological functions of hydrogel are mentioned below:
1. Drug delivery: Hydrogels are widely utilized in drug delivery systems, particularly for the sustained release of drugs over time.
2. Tissue engineering: Hydrogels are frequently used as biomaterials in tissue engineering due to their similarities to the extracellular matrix (ECM).
3. Wound healing: Hydrogels are employed in wound healing due to their potential to promote tissue regeneration and repair.
4. Biosensing: Hydrogels are utilized in the production of biosensors that are capable of detecting biological and chemical compounds. Answer to question 19:Given,Magnitude of the force acting on the rod, F = 550 kg × 9.8 m/s² = 5390 NArea of the cross-section of the rod, A = 0.30 cm³ = 0.3 × 10^-6 m³Length of the rod, L = 2.0 mYoung's modulus of steel, Y = 2.0 × 10¹¹ N/m²The tensile stress in the rod is given by the relation;Stress = Force / Areaσ = F / Aσ = 5390 N / 0.3 × 10^-6 m²σ = 1.80 × 10^10 N/m²The elongation of the rod under stress is given by the relation;Strain = Stress / Young's modulusε = σ / Yε = 1.80 × 10¹⁰ N/m² / 2.0 × 10¹¹ N/m²ε = 0.09. The elongation of the rod under stress is 0.09 m or 9 cm.
Learn more about morphology :
https://brainly.com/question/1378929
#SPJ11
This processing activity involves pre-cooking.
Answers
Answer:
what processing activity ? xd
Explanation:
Answer:
no
Explanation:
List any two features of this computer
h. Who invented Electronic Discrete Variable Automatic Computer?
Answers
Answer:
John Mauchy 1. designed to be a stored-program computer 2. it was binary rather than decimal
who regarded techniques for rendering depth as a kind of deception?
Answers
Plato regarded techniques for rendering depth as a kind of deception.
Despite the growing importance of this issue in social media, the general public, and organizational management, the modeling of deceptions in game theory and decision theory has not received much attention. The information-theoretic models of deception that are currently in use are improved in this paper, along with a framework for incorporating them into game and decision theoretic models of deception. These models and the framework are then used in an agent-based evolutionary simulation to model two common deception types used in "fake news" attacks. people in favor of agents using the "always defect" tactic The findings also demonstrate that the cost of deception has a strong bearing on a population's capacity for deceit, both in terms of its ability to establish itself and its ability to persist.
learn more about depth kind of deception here:
https://brainly.com/question/19931595
#SPJ4
Which is the most viewed vdo in YT ever?
Answers
“Despacito” by Luis Fonsi, featuring Daddy Yankee (7.32bn views) ...
“Shape of You” by Ed Sheeran (5.29bn views) ...
“Johny Johny Yes Papa” by LooLoo Kids (5.24bn views) ...
A
is a document that thanks an interviewer and restates an applicant's interest in the job.
a. thank-you letter
D. letter of acceptance
c. rejection letter
Answers
Answer: D. thank you letter
Explanation:
Several small stores rent space within a larger shopping centre. The owners of the shopping centre have provided a physical network throughout the entire centre.
(a) Explain how virtual networking can be used to give each store a private logical network. Diagrams may be used in your answer.
Answers
Answer:
okay so my first question is what is this question for because I cant really answer without more info
When is the possibility of solar weather affecting terrestrial weather the highest?(1 point)
during solar minimum
during solar minimum
during the solar cycle
during the solar cycle
during solar maximum
during solar maximum
during Total Solar Irradiance
during Total Solar Irradiance
Answers
The possibility of solar weather affecting terrestrial weather the highest is option c: during solar maximum.
Does solar weather have an effect on terrestrial weather?There are different forms of weather on Earth, this is one that ranges from the surface of the planet out unto the outer space.
Note that Space weather as well as terrestrial weather are known to be influenced by the little alterations that the Sun undergoes during its solar cycle.
Hence, The possibility of solar weather affecting terrestrial weather the highest is option c: during solar maximum.
Learn more about solar weather from
https://brainly.com/question/15279276
#SPJ1
with the use of mobile ip, which device is responsible for assigning each mobile node (mn) a local address?
Answers
With the use of Mobile IP (Internet Protocol), the responsibility of assigning a local address to each Mobile Node (MN) falls on the Foreign Agent (FA).
The Foreign Agent is a network entity that resides on a foreign network, i.e., a network other than the home network of the Mobile Node. The Foreign Agent is responsible for authenticating and registering the Mobile Node on its network and also provides the Mobile Node with a care-of-address, which is a temporary IP address assigned to the Mobile Node by the Foreign Agent.When the Mobile Node moves to a different network, it acquires a new care-of-address from the Foreign Agent on the new network. This allows the Mobile Node to maintain its connectivity to the Internet and communicate with other nodes on the network, even as it moves from one network to another. Mobile IP provides a mechanism for Mobile Nodes to move freely between different networks, while still maintaining their IP connectivity and ensuring that they can be reached by other nodes on the Internet.
To learn more about Mobile IP click the link below:
brainly.com/question/30164704
#SPJ1
How to solve the problem with the expiration of the root password to VMware vCenter (VCSA 6.7 console) - tip
Answers
To solve the problem with the expiration of the root password on VMware vCenter (VCSA 6.7 console), Restart the VCSA appliance,Modify boot parameters,Resume the boot process,Remount the file system as read-only and Reboot the appliance.
1.) Restart the VCSA appliance: First, you need to reboot the VCSA 6.7 appliance. To do this, access the vCenter Server Appliance Management Interface (VAMI) by browsing to https://:5480, and then log in with your administrator credentials. Go to the "Summary" tab and click on "Reboot" under "Actions."
2.) Interrupt the GRUB boot loader: During the appliance boot process, you will see the GRUB boot loader screen. Press the "e" key to interrupt the boot loader and enter edit mode.
3.) Modify boot parameters: In the edit mode, look for the line that starts with "linux" or "linuxefi" (depending on your VCSA version). At the end of this line, add the following parameter: rw init=/bin/bash. This will allow you to boot the appliance with root access.
4.)Resume the boot process: Press the "F10" key or "Ctrl+x" to resume the boot process. The VCSA will now boot with root access and a command prompt.
5.) Reset the root password: At the command prompt, enter the following command to reset the root password: passwd. You will be prompted to enter a new password for the root user. Make sure to create a strong, unique password.
6.) Remount the file system as read-only: After setting the new root password, you need to remount the file system as read-only to prevent any data corruption. To do this, enter the following command: mount -o remount,ro /
7.) Reboot the appliance: Finally, reboot the VCSA appliance by entering the following command: reboot -f
After the reboot, you should be able to log in to the VCSA 6.7 console with your new root password. Make sure to keep track of your password securely to avoid future issues.
for more such question on parameter
https://brainly.com/question/29673432
#SPJ11
PLS HELP MEHHHHHHHHHHHHHHHHHHH
Tyra used the software development life cycle to create a new game. She released it to her friends in order to get feedback.
Which stage of the software development life cycle is Tyra currently in?
a
Coding
b
Design
c
Planning
d
Testing
Answers
Answer:
D.) Testing
Explanation:
Tyra developed a new game and let her friends try it. This means she already made it planned, designed, and coded the game. now her friends are testing it.
I hope this helps you :)
-KeairaDickson
How do libraries let you write programs at a higher level? Why is testing important when building and sharing libraries?
Answers
Answer:
libraries do this so that you dx chae
Explanation:
As a student, what are the things you need to know to start building a program?
Answers
Answer:
Get the basics right. When you start learning, the first thing you need to be sure of are the“basics”. ...
Build patience. The number one prerequisite for being successful as a programmer is building patience. ...
Set a goal & move towards it. ...
Do more projects. ...
Get into social coding. ...
Balance your learning.
Why is it Important to understand electricity?? Please answer fast the assignments already missing!!
Answers
Answer:
Electricity not only plays a big part in our daily lives at home, but it is extremely important for all the things that go on in the world around us in our modern life, such as industry that we depend on, communication as in form of radio, television, e-mail, the Internet, etc.
Explanation:
if lain and Wi-Fi were to go out at the same would the circuit break
Answers
Answer:
yes and no because the LAN circuit would stop the connection and the Wi-Fi circuit would fry
which features must you remove from a full gui installation of windows server 2012
Answers
When it comes to features that need to be removed from a full GUI installation of Windows Server 2012, you need to consider what specific roles and features are necessary for your intended use.
However, to provide a general answer, here are some features that can be safely removed from a full GUI installation of Windows Server 2012 without impacting its core functionality:Windows PowerShell Integrated Scripting Environment (ISE)Graphical Management Tools and InfrastructureInternet ExplorerServer Graphical ShellWindows Defender FeaturesThese features can be safely removed by using the Remove Roles and Features wizard or by using the PowerShell command Remove-WindowsFeature.
It's important to note that removing these features can help reduce the size of the installation and decrease its attack surface, which can be useful in some scenarios. However, it's recommended to carefully evaluate the roles and features that are necessary for your intended use and only remove the ones that are not needed to avoid potential compatibility issues.
To know more about Windows visit:
brainly.com/question/29509027
#SPJ11
write an sql query to fetch the sum of salary working in the department id =90
Answers
SELECT SUM(salary) AS TotalSalary FROM employees WHERE department_id = 90;
Surely, I can help you write an SQL query to fetch the sum of salaries of employees working in the department id=90.
SQL query to fetch the sum of salary working in the department id=90
The SQL query to fetch the sum of salary working in the department id=90 is as follows:
SELECT SUM(salary) AS TotalSalary FROM employees WHERE department_id = 90;
The above SQL query retrieves the sum of the salaries of all the employees who work in the department id = 90.
Here, the 'SUM()' function adds the values of the 'salary' column for each employee. The 'AS' keyword is used to provide an alias 'TotalSalary' to the 'SUM()' function.
Lastly, the 'WHERE' clause filters the rows based on the 'department_id' column value equal to 90 to retrieve the sum of salaries of employees in that department.
Learn more about queries at: https://brainly.com/question/31588959
#SPJ11
edhesive 6.8 lesson practice answers please
Answers
Answer: any more info yo can give me. i want to help i dont undestand
Explanation:
Answer:
import simplegui
import random
# global constants
WIDTH = 600
HEIGHT = 400
PARTICLE_RADIUS = 5
COLOR_LIST = ["Red", "Green", "Blue", "White"]
DIRECTION_LIST = [[1,0], [0, 1], [-1, 0], [0, -1]]
# definition of Particle class
class Particle:
# initializer for particles
def __init__(self, position, color):
self.position = position
self.color = color
# method that updates position of a particle
def move(self, offset):
self.position[0] += offset[0]
self.position[1] += offset[1]
# draw method for particles
def draw(self, canvas):
canvas.draw_circle(self.position, PARTICLE_RADIUS, 1, self.color, self.color)
# string method for particles
def __str__(self):
return "Particle with position = " + str(self.position) + " and color = " + self.color
# draw handler
def draw(canvas):
for p in particle_list:
p.move(random.choice(DIRECTION_LIST))
for p in particle_list:
p.draw(canvas)
# create frame and register draw handler
frame = simplegui.create_frame("Particle simulator", WIDTH, HEIGHT)
frame.set_draw_handler(draw)
# create a list of particles
particle_list = []
for i in range(100):
p = Particle([WIDTH / 2, HEIGHT / 2], random.choice(COLOR_LIST))
particle_list.append(p)
# start frame
frame.start()
Explanation:
What information will she need to know in order to obtain assistance from the chief medical officer to reduce the number of delinquent records?
Answers
The information that she need to know in order to obtain assistance from the chief medical officer to reduce the number of delinquent records is the Discharge Record Assembly .
What is an incomplete health record or a delinquent health record?
An incomplete health record is one that is often open after a set period of time such as more than 30 days and if not complete, the health record is said to be delinquent.
Note that Nurses are mandated to carefully maintain patient records. Therefore, The information that she need to know in order to obtain assistance from the chief medical officer to reduce the number of delinquent records is the Discharge Record Assembly .
Learn more about chief medical officer from
https://brainly.com/question/18696862
#SPJ1