the feature that simplifies text wrapping around an object is
Answers
The feature that simplifies text wrapping around an object is called text wrap.
The feature that simplifies text wrapping around an object is called text wrap. Text wrap is a feature commonly found in word processing software, graphic design tools, and web development applications. It allows text to flow around an object, such as an image or a shape, instead of appearing in a rectangular block.
Text wrap is particularly useful when creating visually appealing layouts or designs that involve multiple elements. It helps enhance the visual presentation of text and images by allowing them to interact with each other in a more dynamic and engaging way.
For example, in a word processing document, you can use text wrap to position an image within the text and have the text flow around it. This can create a more visually interesting and professional-looking document.
Learn more:About text wrapping here:
https://brainly.com/question/32265831
#SPJ11
Text Wrap is a helpful tool that simplifies the task of fitting text around images and other objects in your document.
The feature that simplifies text wrapping around an object is called Text Wrap. It is a useful tool that allows you to fit your text around images and other objects in your document. Text Wrap simplifies the task of moving images and other graphic elements around a document and then positioning text around them.There are different Text Wrap settings to choose from, such as No Text Wrap, Square, Tight, Through, Top and Bottom, and Custom.
The different settings allow you to choose the most appropriate setting for your document, depending on your text and image layout needs.In order to apply the Text Wrap feature, follow these steps:Select the image or object you want to apply the Text Wrap to.Click on the "Wrap Text" button from the "Format" tab.Select the preferred Text Wrap option from the list.The text will now wrap around the object according to the Text Wrap setting chosen.
You can adjust the image's position and the wrap by using the various Text Wrap options until you achieve the desired effect. This will help your documents to look more professional.Overall, Text Wrap is a helpful tool that simplifies the task of fitting text around images and other objects in your document.
Learn more about graphic elements here,
https://brainly.com/question/25721926
#SPJ11
Related Questions
Need help ASAPppppppppp

Answers
Answer:
Below picture should give you an indication. On different PC cases, the position of the connectors can be different, so you have to look at the shape.

______ are invisible images or HTML code hidden within a web page or e-mail message and are used to transmit information without your knowledge.
Answers
The term you are looking for is "web beacons". Web beacons are often used by advertisers and marketers to track user activity on a web page or within an e-mail message.
They are essentially tiny, invisible images or snippets of HTML code that are embedded within a web page or e-mail and can transmit information about the user's behavior back to the sender. This can include things like the user's IP address, browser type, and device type, as well as more specific information like which links they click on or which pages they visit. While web beacons are typically used for legitimate purposes like tracking website traffic and measuring advertising effectiveness, they can also be used for more nefarious purposes like phishing or malware distribution. A web page is a document that is displayed on a web browser when accessed by a user through the internet.
Learn more about web page here:
https://brainly.com/question/30549924
#SPJ11
Which of the variables have the value 50 after executing the code segment?
see the image below for reference
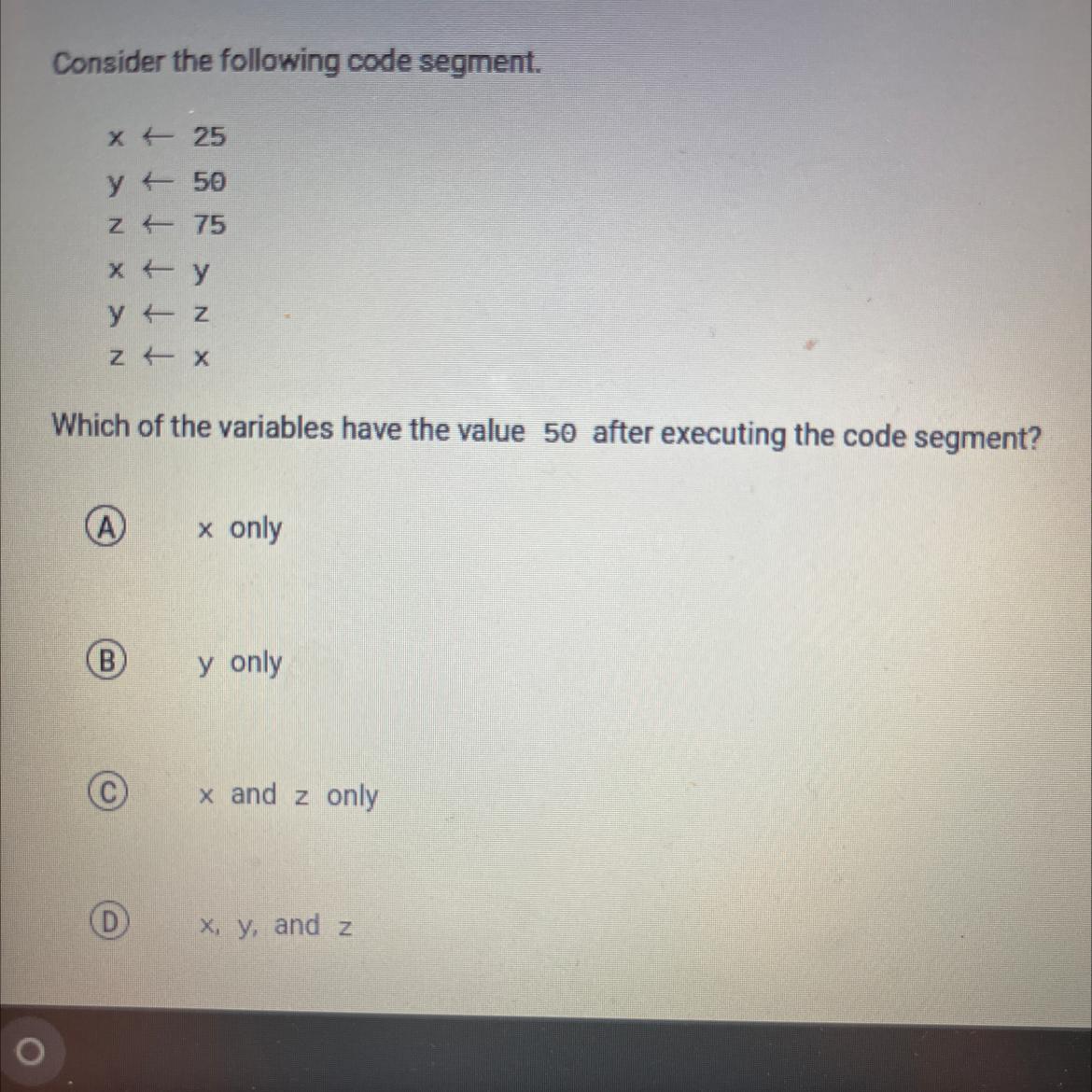
Answers
The segment of code that will have the value of 50 after executing the code segment is this:
C. X and Z only
What is the segment?A segment is a section of code that instructs the computer to take certain actions. In the above code, we can see that the y value is set to return the value of 50.
Also, in the fourth instruction, the x value is instructed to return the value of y. So, the segment of code that is meant to execute and return the number, 50 is option c which contains x and z.
Learn more about coding here:
https://brainly.com/question/22654163
#SPJ1
Answer the following questions: a. What is the Internet? Who controls and supervises it?
Answers
Answer:
Answer the following questions: a. What is the Internet? Who controls and supervises it?
Explanation:
Can someone plss help me with this!!

Answers
Answer:
Text
Explanation:
There is no text in between the <h1> and </h1> tags.
I hope thats correct.
Dylan just finished business school and is looking for his first job. He is interviewed by a manufacturing company. If he gets this job, Dylan can expect that he will be offered a high salary and a high position. A. True B. False
Answers
Answer:
B. False
Explanation:
He finished business school but is going into the manufacturing industry. It doesnt state that he went into a place where his business degree would be applicable in any way, therefore it is false.
Web browsers save website information in their _________, which helps the site load faster on future visits. memory repository storage cache
Answers
Answer:
cache
Explanation:
Every browser saves your cache
Web browsers are designed and developed to save website information in their cache, which helps the website load faster on future visits.
Given that,
Web browsers save website information.
Since, A web browser can be defined as a type of software application (program) that is designed and developed to enable an end-user to view, access, and perform certain tasks on a website, especially when connected to the Internet.
A website can be defined as a collective name that connotes a series of web pages that are interconnected and linked together with the same domain name, so as to provide certain information to end users.
In Computer technology, web browsers are typically designed and developed to save website information in their cache, which helps the website load faster on future visits.
Read more on web browsers here:
brainly.com/question/28088182
#SPJ6
2 types of input, and why it is called an output device
1.
2.
5 types of output devices, and why it is called an output device
1.
2.
3.
4.
5.
Answers
Answer:
Mouse, Keyboards etc., are input device examples. Monitors, Printers etc., are examples of output devices.
Explanation:
What can be used to help identify mission-critical systems?
A. Critical outage times
B. Critical business functions
C. PCI DSS review
D. Disaster recovery plan
Answers
The term that can be used to help identify mission-critical systems is B. Critical business functions.
What is a critical business?A critical business service is one that, if interrupted, might have a major negative effect on the organization's safety and soundness, its clients, or other organizations that depend on it.
Any IT component such as software, hardware, database, process, ) that performs a function crucial to business operations is referred to as a "mission-critical system" or "mission-critical computing."
Learn more about business functions at;
https://brainly.com/question/14688077
#SPJ4
Often presented visually on an executive dashboard, what type of report focuses attention on business processes whose performance falls outside of the tolerance ranges defined a kpi metric?.
Answers
The answer to the assertion whose performance falls outside of the tolerance ranges defined a kpi metric made is an exception.
Does metric correspond to KPI?
Metrics are often operational or tactical, whereas KPIs are strategic. Metrics are less complex indications that are unique to a department, whereas KPIs can be reviewed by many departments that are working toward the same goal. KPIs assist you in making strategic decisions, whilst metrics give you a perspective on your business activity.
What is a KPI measurement?
The metrics you use to assess tasks, goals, or objectives that are essential to your business are known as key performance indicators, or KPIs. The use of the word "key" in the sentence denotes that the words have a unique or important meaning. KPIs serve as measurable benchmarks in relation to established targets.
To know more about KPI metric visit:
brainly.com/question/28455765
#SPJ4
Why is the no video recording in iPhone camera
Answers
Answer:
it really does depend on what iphone you have but go to Settings > Privacy > Camera and disable the last app that was allowed access to the phone's Camera. check the camera app again and you should see the video recording access.
hope this helped!
Answer:
Wait is this a genuine question im not sure how to answer
Explanation:
a core authentication server is exposed to the internet and is connected to sensitive services. what are some measures you can take to secure the server and prevent it from getting compromised by a hacker? select all that apply.
Answers
The measures you can take to secure the server and prevent it from getting compromised by a hacker are the use of option b, c and d:
Secure firewall Access Control Lists (ACLs) Bastion hostsWhat is core authentication?The process of confirming a user's identification is called authentication. The process of deciding whether a user has access to a resource is known as authorization.
Secure or Discreet Firewall: A safe firewall configuration should forbid connections to systems and networks that are not trusted.
Bastion Hosts: What is allowed to run on Bastion hosts is restricted and carefully hardened. Bastion hosts are typically assumed to be exposed to the internet, thus extra care is taken to harden and lock them down to reduce the likelihood of compromise.
Then the Lists of access controls (ACLs). To secure sensitive services without compromising the convenience of the entire business, secure configurations, such ACLs, could be enabled on selected bastion hosts.
Learn more about core authentication from
https://brainly.com/question/17093485
#SPJ1
See options below
Decker service
Secure firewall
Access Control Lists (ACLs)
Bastion hosts
which of the following would not transmit signals from one point to another? a. telephone line. b. modem. c. fibre optics. d. coaxial cable
Answers
Answer:
b
modem
Explanation:
modem is used to receive signals not transmit
Deirdre has a hearing disability. One of her friends advised her to use real-time text or RTT on her phone. In which of these
ways can it help Deirdre? Select all that apply.
Answers
The way that real-time text or RTT on her phone can help her is that;
C: On phone calls, it will convert speech into text
Speech to TextWe are told that Deirdre has a hearing disability. This means that she has difficulty in hearing words clearly but can read.
Thus, from her friends advice about real time text or RTT, it will aid her because whenever someone calls her on the phone, it can convert the content of the call speech into text.
The missing options are;
A. It will make her phone vibrate to notify her when she gets a phone call
B. It will make her phone vibrate to notify her when she gets a text message.
C. On phone calls, it will convert speech into text. D. While text messaging, it will convert text into speech
Read more on speech to text at; https://brainly.com/question/2375490
NEED THIS ASAP!!) What makes open source software different from closed source software? A It is made specifically for the Linux operating system. B It allows users to view the underlying code. C It is always developed by teams of professional programmers. D It is programmed directly in 1s and 0s instead of using a programming language.
Answers
Answer: B
Explanation: Open Source software is "open" by nature, meaning collaborative. Developers share code, knowledge, and related insight in order to for others to use it and innovate together over time. It is differentiated from commercial software, which is not "open" or generally free to use.
What is the name of the item that supplies the exact or near exact voltage at the required wattage to all of the circuitry inside your computer?
Answers
Answer:
It's the power supply
Explanation:
The power supply is what essentially enables the computer to operate. It is able to do that by converting the incoming alternating current (AC) to direct current (DC) at the correct wattage rating that is required by the computer to function. The power supply is a metal box that is generally placed in the corner of the case.
I need help with this question. asap please

Answers
Answer:
what are you talking about
Explanation:
can you help me with my question

"A.Country" represents Column "Country" from Table A Column "A" from Table Country Table Column None of the above
Answers
"A.Country" represents the column "Country" from Table A.
In the given statement, "A.Country" represents a column from Table A. This notation indicates that the column named "Country" is specifically associated with Table A. It is a common practice to use such notation to specify the origin of a column when working with multiple tables in a database schema.
Using the dot notation, "A.Country" clearly identifies that the column "Country" belongs to Table A and helps to avoid ambiguity or confusion, especially when there are columns with the same name in different tables. This notation is particularly useful in situations where tables are joined or when writing complex queries involving multiple tables.
By explicitly stating the table name along with the column name, "A.Country" provides a clear reference to the desired data element, ensuring accurate data retrieval and manipulation in database operations.
learn more about table here
https://brainly.com/question/30883187
#SPJ11
How can we solve mental stress?
Hello can anyone answer
Answers
Answer:
Please don't delete it. Because other people did!
Explanation:
Use guided meditation, Practice deep breathing, Maintain physical exercise and good nutrition!
By making yourself comfortable around your environment.I know it can be hard but try making yourself feel distracted from stress.Have a break from what you are doing and take your time to heal.
Explanation:
What is the output frequency of a three-stage binary counter with an input clock frequency of 40 kHz
Answers
The rate at which a signal or waveform is generated as an output by a device or system is referred to as output frequency. It shows how many cycles or events take place in a certain amount of time.
An input signal or clock is processed or controlled in a variety of electronic systems, such as oscillators, counters, timers, or communication devices, to produce an output signal at a particular frequency.
Depending on the device's design and operation, the output frequency may be more, lower, or equal to the input frequency.
Learn more about frequency here:
brainly.com/question/29739263
#SPJ4
Differentiate ways to stay safe online by matching each question about security to its answer.
Answers
Being safe online includes avoiding risks and harms that could jeopardize personal information, result in dangerous communications, or even have a negative impact on one's mental health and wellness.
What to stay safe online about security?Most people store a lot of sensitive information on their laptops. If you don't properly safeguard your computer when you're online, confidential information might get stolen or unintentionally deleted. Your computer could be attacked in a number of ways online.
Therefore, which could put their personal information in danger, result in hazardous communications, or even have an impact on their mental health and wellness.
Learn more about online here:
https://brainly.com/question/11265075
#SPJ1
If your computer is running slowly, which of the following is most likely to solve the problem?
Scanning, cleaning, and optimizing your hard drive
Checking to make sure all of the computer’s cords are plugged in
Reentering the serial numbers of the software programs the computer is running
Searching the hard drive for missing DLL files
Answers
Answer:
Purchase Anti-virus
Explanation:
Delete old files.
clear your temp
update to a ssd
Answer:
A. Scanning, cleaning and optimizing your hard drive
Explanation:
IM A DIFFERENT BREEED!
also... when your computer is slow, you usually scan and clean your computer files and delete unnecessary files you don't need so that your computer can run more smoothly and faster.
A piece of data in a program whose value can change is called
Answers
Answer:
cancell be cause is sick
Explanation:
period ah period uh
Choose the word that matches each definition.
: intangible
: intellectual property
Answers
Explanation:
intangible: Something that cannot be touched or physically grasped, such as a feeling or an idea.
intellectual property: Creations of the mind, such as inventions, literary and artistic works, and symbols, names, and images used in commerce, which are protected by law.
Answer:
intangible: Something that cannot be touched or physically grasped, such as a feeling or an idea.
intellectual property: Creations of the mind, such as inventions, literary and artistic works, and symbols, names, and images used in commerce, which are protected by law.
These tabs are part of the Member's disciplinary action record. (True or False)
Answers
True. These tabs, which refer to any disciplinary actions taken against a member, are an integral part of their disciplinary action record.
This record is maintained to track the member's behavior and ensure that they follow the rules and regulations of the organization or institution they belong to. Any disciplinary action taken against a member, whether it be a warning, suspension, or termination, is recorded in their disciplinary action record and can be used as a reference in future situations. It is important for members to understand the significance of these tabs and maintain a positive track record to avoid any negative consequences in the future.
True. These tabs are part of the Member's disciplinary action record. This statement indicates that the mentioned tabs contain information related to disciplinary actions taken against a member within an organization or group. These records are typically maintained to track any issues and ensure proper conduct among members.
Learn more about disciplinary action at: brainly.com/question/30296795
#SPJ11
You have worked as the network administrator for a company for seven months. One day, all picture files on the server become corrupted. You discover that a user downloaded a virus from the internet onto his workstation that propagated to the server. You successfully restore all files from backup, but your boss is adamant that this situation does not reoccur. What should you do
Answers
Who put forward the idea of nanotechnology to the world?
Answers
Answer:
Richard Feynman
Explanation:
Richard Feynman who was the physicists. Idea of Nanotechnology was put forward for the first time by him in 1959.
During his lecture at an American Physical Society meeting at Caltech on December 29, 1959, he said "There's Plenty of Room at the Bottom," this statement by him often held to have provided inspiration for the field of nanotechnology.
Common security and privacy risks that occur on a network are
USB Drives
Insider Threats
Wireless Networking
Email Cams
Answers
Common security and privacy risks that occur on a network are option B: Insider Threats.
What are insider threats?Insider threat is defined by the Cyber and Infrastructure Security Agency (CISA) as the risk that an insider will intentionally or unintentionally use his or her permitted access to harm the mission, resources, and others.
The common security threats are:
Viruses and wormsDrive-by download attacks. Phishing attacks. Ransomware, etc.Note that an insider threat can make your network to be in a huge risk of being attacked.
Learn more about security threats from
https://brainly.com/question/15235043
#SPJ1
Answer: C
Explanation:
Things to be considered while purchasing a new computer
Plzzz help emergency
Answers
Answer:
Explanation:
If you are getting a new computer there are many things to consider, for a gaming computer you should look for a good prosseser priferably a core i9. you should also look for a good graphics card. Lastly you should have good ram and space, a good ram amount is 16 gigs, for space you should at LEAST have 50 gigs for games.
Okay so I am using the OBS video recording software to record gaming videos but for some reason, it won't record sound. Do you know how to fix this?
I know this isn't exactly computer science or anything but still related to computers.
Answers
Answer:
It could be broken, your browser does not support it, or something in your settings may be blocking it.
According to my knowledge, "The simplest solution is to reboot. Close it down and open it again. If the problem persists, try restarting your computer. Try restarting and see if your camera works."
Hope this helps!