in an office setting, instead of using a wireless broadband router, a more sophisticated device known as a(n) is used.
Answers
Instead of a wireless router, an access point (AP), a more advanced device, is used in an office setting.
What is the name of the kind of networking connection standard utilized in wireless?Currently, the IEEE 802.11b/g standard is well-liked in the business and offers the right amount of range, network speed, and device mobility support to efficiently meet the majority of the university community's needs.
In order to connect devices within a city and form a metropolitan area network, what kind of wireless network is used?The Wireless Metropolitan Area Network (WMAN) technology based on the IEEE 802.16 set of standards is known as WiMAX.
To know know more about wireless broadband visit :-
https://brainly.com/question/14827380
#SPJ4
Related Questions
A small software development project at Krishna Dhir's firm has five major activities. The times are estimated and provided in the table below. ACTIVITY IMMEDIATE PREDECESSOR a m b A - 2 5 8 B - 3 6 9 C A 4 7 10
a) Find the expected completion time for this project. The expected completion time for this project is (enter your response as a whole number). b) What variance value would be used to find probabilities of finishing by a certain time? The project variance value of completion time is (enter your response as a whole number).
Answers
(a) The expected completion time for this project is 13 (as a whole number).
(b) The project variance value of completion time is 2 (as a whole number).
(a) The expected completion time for the project can be found by calculating the Critical Path Method (CPM). CPM involves finding the longest path through the network of activities, considering the estimated times.
Using the given table, we can calculate the expected completion time as follows:
Activity A: Estimated time = (a + 4m + b) / 6 = (2 + 4(5) + 8) / 6 = 34 / 6 = 5.67
Activity B: Estimated time = (a + 4m + b) / 6 = (3 + 4(6) + 9) / 6 = 39 / 6 = 6.5
Activity C: Estimated time = (a + 4m + b) / 6 = (4 + 4(7) + 10) / 6 = 46 / 6 = 7.67
The expected completion time is the sum of the estimated times of all activities on the critical path:
Expected completion time = 5.67 + 7.67 = 13.34 (approximated to 13 as a whole number)
Therefore, the expected completion time for this project is 13.
(b) The variance value used to find probabilities of finishing by a certain time is calculated by summing the variances of activities on the critical path.
Using the estimated times, we can calculate the variances as follows:
Variance of activity A: [(b - a) / 6] ^ 2 = [(8 - 2) / 6] ^ 2 = (6 / 6) ^ 2 = 1
Variance of activity C: [(b - a) / 6] ^ 2 = [(10 - 4) / 6] ^ 2 = (6 / 6) ^ 2 = 1
The variance value for the project completion time is the sum of the variances of activities on the critical path:
Variance = 1 + 1 = 2
Therefore, the project variance value of completion time is 2.
Learn more about Critical Path Method:
https://brainly.com/question/31730624
#SPJ11
Which among the following is a collaboration tool that allows users to stay updated on topics of interest?
A browser cookie
A browser cookie
Really Simple Syndication
Desktop sharing
Answers
The collaboration tool that allows users to stay updated on topics of interest is Really Simple Syndication.
What is Really Simple Syndication?It should be note that Users and programs can obtain website changes in a standardized, computer-readable format through RSS, a type of web feed.
Real Simple Syndication, or RSS, is a web feed format for constantly updated content like blog posts, news headlines, the newest homes and cars, etc. in a uniform format.
Learn more about tool at;
https://brainly.com/question/25898149
#SPJ1
The type of line shown below represents an / a:
Answers
Answer:
esrfsrtg
Explanation:
in 100 word, tell me who is a significant public figure who has the job profile as a "set designer" and explain why
Answers
A significant public figure who holds the job profile of a set designer is Sarah Jones.
Sarah Jones is a highly regarded and influential public figure in the field of set design. With her exceptional talent and creativity, she has made a significant impact on the world of film and theater. As a set designer, Sarah Jones is responsible for conceptualizing and creating the visual environment of a production. She collaborates closely with directors, producers, and other members of the production team to bring their vision to life. Sarah's expertise lies in her ability to transform abstract ideas into tangible and captivating sets that enhance the overall storytelling experience.
Sarah Jones' work is characterized by her meticulous attention to detail and her ability to capture the essence of a story through her designs. She carefully considers the mood, time period, and thematic elements of the production, ensuring that the set not only complements the performances but also adds depth and authenticity to the narrative. Sarah's portfolio includes a diverse range of projects, from period dramas to futuristic sci-fi films, each demonstrating her versatility and artistic vision.
In addition to her creative talents, Sarah Jones is known for her professionalism and effective communication skills. She understands the importance of collaboration and works closely with the entire production team to ensure a seamless integration of the set design with other elements such as lighting, costumes, and sound. Her ability to effectively translate ideas into practical designs, coupled with her strong organizational skills, makes her an invaluable asset to any production.
Learn more about job profile
brainly.com/question/884776
#SPJ11
will i3 pull 3220
and 6 GB of RAM windows 10 without lags?
Answers
It is to be noted that a Core i3 CPU (or processor) with 6GB of RAM running Windows 10 will most certainly be able to run without noticeable delays. However, the performance of the system will be determined by the exact tasks and apps that you will execute on it.
What is a Core i3 Processor?An i3 CPU is a low-end processor that will struggle to handle intense workloads or high-end games, but it should do simple activities like web surfing, word processing, and video playback without trouble. 6GB of RAM is also considered a little amount of memory; it may not be enough to run numerous apps at the same time, or to run heavy applications such as video editing software, but it should be plenty for simple activities.
It's crucial to remember that a computer's performance is influenced by numerous variables other than the CPU and RAM. Other elements, like as the storage drive, graphics card, and cooling system, can all contribute to the total system performance.
Learn mroe about processors:
https://brainly.com/question/28255343
#SPJ1
nano is an easy-to-use text editor for Linux. There are arguably better editors (Vim, being the obvious choice); however, nano is a great one to start with.What switch would you use to make a backup when opening a file with nano?
Answers
To make a backup of the original file when opening it with nano, you can use the "-B" or "--backup" option.
The command would be: nano -B filename This will create a backup of the original file with a "" appended to the end of the filename. For example, if you open a file named "example.txt", nano will create a backup file named "example.txt".Note that you can also customize the backup behavior using additional switches, such as "--backupdir" to specify a backup directory, or "--suffix" to use a different suffix for the backup file. For more information on the backup options in nano, you can refer to the nano manual page by typing "man nano" in the terminal.
To learn more about backup click the link below:
brainly.com/question/17355457
#SPJ11
I need help building a computer what are some good parts?
Answers
Answer:
glass for the screen, wires to connect everything, something for the buttons, you also might need a screen protector so it can help your eyes because the screen will be bright, use something that will help the computer not fall off the desk, you also need to make some space at the bottom of the computer for the sound to go through, you need to make some more space at the either side you want the charger for it to always have power so you can always use it, and memory space, if you want to you can add a little space at the side for your earbuds.
Explanation:
you need to have your parents help you so you don't get hurt.
What is the difference between a function with parameters, and a function
without parameters? *
Answers
Answer:
A function with out parameters cannot take any arguments or perform operations on variables passed in. A function with parameters can.
Mathematical foundations of computer science
The result set of the following SQL query would contain how many rows? Do not count either the column headings or the table heading as rows.
SELECT * FROM PartNeeds WHERE Supplier = 31 OR Project = 1
PartNeeds
Supplier PartNumber Project
23 1092 1
23 1101 3
23 9048 4
31 4975 3
31 3477 2
32 6984 4
32 9191 2.
33 1001 1
Answers
The result set of the SQL query would contain 4 rows.
How many rows would the result set contain for the given SQL query?
The given SQL query retrieves rows from the "PartNeeds" table based on the specified conditions.
The conditions state that the "Supplier" column should have a value of 31 OR the "Project" column should have a value of 1.
Looking at the provided table, we can see that there are two rows where the "Supplier" column has a value of 31 and two rows where the "Project" column has a value of 1.
we don't count the column headings or the table heading as rows, so we only consider the actual data rows in the result set.
Learn more about SQL query
brainly.com/question/31663284
#SPJ11
. in a linked-based implementation of the adt list with only a head reference, what is the performance of adding an entry at the end of the list?
Answers
In a linked-based implementation of the ADT list with only a head reference, the performance of adding an entry at the end of the list is typically O(n) in the worst case scenario.
This is because in order to add an entry at the end of the list, you would need to traverse the entire list from the head reference until you reach the end, which takes a linear amount of time proportional to the number of entries in the list. However, if you have a tail reference in addition to the head reference, the performance of adding an entry at the end of the list can be improved to O(1) since you can simply update the tail reference to point to the new entry.
Hi! In a linked-based implementation of the ADT list with only a head reference, the performance of adding an entry at the end of the list is typically O(n). This is because you need to traverse the entire list to find the last node before adding a new entry.
To learn more about implementation click on the link below:
brainly.com/question/31439616
#SPJ11
The open source movement makes _____ available to everyone in an effort to continue to build and improve the functionality of open source software.
Answers
Answer:
programs
Explanation:
Looking for my Amoung Us buddy
I was playing the game Amoung Us a bit ago and met a great person. His tag was "Im stuck i" and would be yellow most of the time. If thats you reading this, hey its Pancake! If this is not you, please ignore this.
Answers
Answer:
sorry I'm not this person
Explanation:
but I do follow this Instagram account that helps you find friends you've made on among us. I don't think your friend would be on here if I'm being honest, but you could have a way better chance with that
Answer:
I think I have played with him. He was reaally great person. I will try to find him.
Explanation:
Pancake WE will find "Im stuck i"
#FIND"Imstucki"
Write a QBASIC program to generate following series.2,4,6,8............10th term.
Answers
Here's a QBASIC program to generate the series 2, 4, 6, 8, ..., up to the 10th term:
FOR i = 1 TO 10
PRINT i * 2;
NEXT i
What is the explanation of the above program?In this program, the FOR loop iterates from 1 to 10, and for each iteration, it multiplies the loop variable i by 2 and prints the result using the PRINT statement.
The semicolon ; after the PRINT statement prevents the cursor from moving to the next line after printing each number, so the output appears on the same line.
Learn more about Q-Basic:
https://brainly.com/question/24124254
#SPJ1
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
If i paid $37.20 for 12 gallons of ice cream how many would 1 quart of ice cream cost
Answers
Answer:
$0.78
Explanation:
12 gallons• 4 quarts= 48 quarts for 12 gallons
Now, you can divide 48 from $37.20 to find the price of 1 quart.
$37.20 / 48 quarts = 0.775, written as $0.76 per quart of ice cream.
Answer: $0.76 per quart of ice cream
What are the future developments of Handoff or Handover
(process) in cellular communications. Show examples and explain
briefly. Please no plagiarism.
Answers
The future developments of handoff or handover in cellular communications are focused on improving the efficiency, reliability, and seamless transition of mobile devices between different networks or cells. Here are some examples of future developments in handoff:
1. 5G Technology: The deployment of 5G networks brings several advancements in handoff capabilities. With higher data rates, low latency, and network slicing, 5G networks enable faster and more efficient handoffs between cells.
2. Multi-RAT Handover: As mobile networks continue to evolve, the future will witness the integration of multiple radio access technologies (RATs) such as 5G, LTE, Wi-Fi, and even satellite networks. Multi-RAT handover aims to seamlessly switch between different RATs based on network availability, capacity, and user requirements.
3. HetNets and Small Cells: The deployment of heterogeneous networks (HetNets) and small cells plays a crucial role in enhancing network coverage and capacity. These networks consist of a combination of macro cells, micro cells, and pico cells.
4. Mobility Management Protocols: Advanced mobility management protocols, such as Proxy Mobile IPv6 (PMIPv6) and Hierarchical Mobile IPv6 (HMIPv6), are being developed to improve handoff performance. These protocols provide enhanced mobility support, seamless handover, and reduced signaling overhead.
Overall, the future developments of handoff in cellular communications focus on enhancing the efficiency, reliability, and user experience during network transitions. These developments leverage advancements in network technologies, protocols, and intelligent decision-making algorithms to enable seamless handover and uninterrupted connectivity for mobile devices.
Learn more about cellular communications click here:
brainly.com/question/7265916
#SPJ11
These statements describe LANs. SELECT ALL THAT APPLY
1) are not able to connect to the Internet
2) connect networks over a large geographic area
3) don't have to be connected to other networks
4) located in one building or adjacent buildings
5)wires connecting the network owned by the organization
Answers
Local area networks connect computers and give users shared access to printers, data, and other resources. Peer-to-peer or client-server architectures are the two main types of local area network architecture. Thus, option B, D, E is correct.
What is the significance of local area network?Computers may swiftly and readily exchange data and messages using local area networks. This expedites the process and saves time.
Therefore, Any user on the network can send and receive messages and data using LAN. Users can access the server-stored data via the network from any computer.
Learn more about local area network here:
https://brainly.com/question/1167985
#SPJ1
9. With each element of the list defining both a key exchange algorithm and a CipherSpec, the list that contains the combination of cryptographic algorithms supported by the client in decreasing order of preference is the __________ .
Answers
The list that contains the combination of cryptographic algorithms supported by the client in decreasing order of preference is the CipherSuite.
What is CipherSuite?CipherSuite can be defined as a group of instructions used to produce network connections in a secure manner.
CipherSuite is associated with Transport Layer Security, which involves the usage of algorithms to protect data.
Transport Layer Security can be defined as a computational cryptographic protocol aimed at protecting information.
Learn more about Transport Layer Security here:
https://brainly.com/question/14425531
Help!! bob searching for a website using the two words theory and practice he finds only one website that has both words most of the other results have only one of the two words some results don't have either of the two words which logic gate principal will help
Answers
Answer:
please just can u explain that
Explanation:
name two components required for wireless networking
(answer fastly)
Answers
Explanation:
User Devices. Users of wireless LANs operate a multitude of devices, such as PCs, laptops, and PDAs. ...
Radio NICs. A major part of a wireless LAN includes a radio NIC that operates within the computer device and provides wireless connectivity.
or routers, repeaters, and access points
PLEASEEE HELP HURRY

Answers
To start searching for a scholarly article on G. o. ogle Scholar, you should:
"Type the title of the article or keywords associated with it." (Option A)
What is the rationale for the above response?Here are the steps you can follow:
Go to Go. o. gle Scholar website In the search box, type the title of the article or relevant keywords associated with it.Click the "Search" button.Browse through the search results to find the article you are looking for.Click on the title of the article to view the abstract and other details.If the article is available for free, you can download or access it directly from the search results page. If not, you may need to purchase or access it through a library or other academic institution.Note that you can also use advanced search options and filters available on Go. ogle Scholar to narrow down your search results based on various criteria, such as publication date, author, and journal.
Learn more about G. o. ogle at:
https://brainly.com/question/28727776
#SPJ1
Roland knew that the code to his sister toy safe was only two digits ong he was able to crack the safe open by attempting every two digit code until he found the correct one what method code breaking did Roland use
Answers
Answer:
Brute-force attack
Explanation:
a brute force attack is when you use a bunch of random passwords in the hopes of eventually getting it right
Answer:
Permutation cipher
This is a complete enumeration of all possible keys of small length (we have a length of 2).
The first digit is 1, 2, 3, ..., 8, 9.
Second digit 0, 1, 2,…, 8, 9
Number of options: 9*10 = 90
10, 11, 12, … 97, 98, 99
Discuss the core technologies and provide examples of where they exist in society. Discuss how the core technologies are part of a larger system
Answers
Answer:
Part A
The core technologies are the technologies which make other technologies work or perform their desired tasks
Examples of core technologies and where they exist are;
Thermal technology, which is the technology involving the work production, storage, and transfer using heat energy, exists in our refrigerators, heat engine, and boilers
Electronic technology is the technology that involves the control of the flow of electrons in a circuit through rectification and amplification provided by active devices. Electronic technology can be located in a radio receiver, printed circuit boards (PCB), and mobile phone
Fluid technology is the use of fluid to transmit a force, provide mechanical advantage, and generate power. Fluid technologies can be found in brakes, automatic transmission systems, landing gears, servomechanisms, and pneumatic tools such as syringes
Part B
The core technologies are the subsystems within the larger systems that make the larger systems to work
The thermal technology in a refrigerator makes use of the transfer of heat from a cold region, inside the fridge, to region of higher temperature, by the use of heat exchange and the properties of the coolant when subjected to different amount of compression and expansion
The electronic technologies make it possible to make portable electronic devises such as the mobile phones by the use miniaturized circuit boards that perform several functions and are integrated into a small piece of semiconductor material
Fluid technologies in landing gears provide reliable activation of the undercarriage at all times in almost all conditions such that the landing gears can be activated mechanically without the need for other source of energy
Explanation:
Core technologies includes biotechnology, electrical, electronics, fluid, material, mechanical, and others.
What are core technologies?Core Technologies are known to be the framework of technology systems. The major Core Technologies includes:
Mechanical StructuralMaterials, etc.They are also called "building blocks" of all technology system as without time, technology would not be existing today.
Learn more about Core technologies from
https://brainly.com/question/14595106
a windows server was corrupted due to a malware attack. a system state backup is available from before the attack occurred, when the server was fully operational. what steps will be needed after recovery from the backup to return the machine to its operational state
Answers
Since the windows server was corrupted due to a malware attack, the steps that will be needed after recovery from the backup to return the machine to its operational state is option C: Recovery will return the system to its operational state.
What serves as the goal of computer recovery?After a crash, corruption, physical or technical error, or other issues that rendered the PC inoperable, it enables PC users to resume basic operations on their machines. Another name for PC recovery is computer recovery.
Therefore, In the event of hardware or operating system failure, the recovery process is intended to return a server to its previous operational state. Using a Bootable Backup Media or a Bootable RecoverAssist Media to boot up your computer will start the recovery process.
Learn more about system Recovery from
https://brainly.com/question/14331162
#SPJ1
See Full question below
A Windows server was corrupted due to a malware attack. A System State backup is available from before the attack occurred, when the server was fully operational. What steps will be needed after recovery from the backup to return the machine to its operational state? Install applidtions required for the server's function. Reconfigure the backup system. Recovery will return the system to its operational state. Reconfigure Windows to the desired state.
Previous question
Name at least 3 different portable computer devices that can be purchased
either from a local retailer or online.
Answers
Answer:
Smart Phone
Cameras
Console Controller
Brainliest and please say if its right!!
Laptops/Computers
Consoles
(Also tablets).
Which three events occur when a DNS request is processed?
A. A local DNS server sends the IP address back to the requesting
device for access.
B. A local DNS server checks to see if it knows the IP address for the
site requested.
C. A subdomain DNS server defines how data will be transferred
over the internet.
D. Top-level domain DNS servers look up the site and return the IP
address.
Answers
The three events occur when a DNS request is processed is that
A local DNS server sends the IP address back to the requesting device for access. A local DNS server checks to see if it knows the IP address for the site requested.Top-level domain DNS servers look up the site and return the IP address.What are the types of DNS queries?There are known to be 3 types of DNS queries which are:
Recursive iterativenon-recursive.Therefore, The three events occur when a DNS request is processed is that
A local DNS server sends the IP address back to the requesting device for access. A local DNS server checks to see if it knows the IP address for the site requested.Top-level domain DNS servers look up the site and return the IP address.Learn more about DNS from
https://brainly.com/question/12465146
#SPJ1
2) When a router forwards incoming packets closer to their destination hosts, this is ________.
A) routing
B) switching
C) bridging
D) relaying
Answers
When a router forwards incoming packets closer to their destination hosts, this is called routing. Routing is the process of selecting the best path for network traffic to reach its destination.
The router examines the destination IP address of the packet and consults its routing table to determine the best next hop to forward the packet. The router will continue to forward the packet through the network until it reaches its final destination. Switching, bridging, and relaying are also important functions in networking, but they refer to different processes. Switching involves forwarding data packets between devices on a local area network (LAN), while bridging connects two different LANs. Relaying involves forwarding messages between servers or clients in a distributed computing environment.
learn more about routing here:
https://brainly.com/question/30409461
#SPJ11
(This has nothing to do with homework by the way) I'm graduating to the 9th grade this year... do the FSA/EOC scores determine my graduation or do my grades?
Answers
Answer:
I dont think so.
Explanation:
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
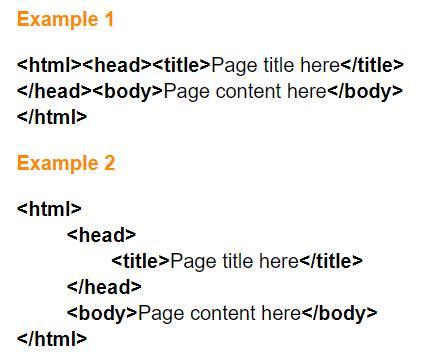
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
which Yandere Simulator update removed the box of matches?
Answers
Answer:
Fixed the glitchy physics of Yandere-chan’s latest hairstyle. Removed exploit that allowed players to keep a character stationary indefinitely by talking to a student about their Task and never dismissing the Task Window. Adjusted the pathfinding grid so that it should be less likely for a student’s path to the male locker room to be blocked.
Explanation:
Answer:
i couldnt find the exact year but heres a list of bug fixes n stuff if this helps
Explanation:
https://yandere-simulator.fandom.com/wiki/Update_History