If you plug a hard drive controller card into an expansion slot, it functions just as if it were built into the motherboard, albeit with one big difference: _______________.
Answers
If you plug a hard drive controller card into an expansion slot, it functions just as if it were built into the motherboard, albeit with one big difference: "it is not directly integrated into the motherboard's chipset."
When you add a hard drive controller card to an expansion slot on the motherboard, it allows you to connect and control additional hard drives. The controller card provides the necessary hardware and interfaces to communicate with the hard drives, just like a built-in controller on the motherboard would.
However, the key difference is that the controller card is not directly integrated into the motherboard's chipset. The motherboard's chipset typically includes various components and controllers, including the built-in hard drive controller. On the other hand, the expansion slot allows you to add additional functionality to the motherboard by installing a separate controller card.
This distinction is important because the integration of the controller into the motherboard's chipset can have implications for factors such as performance, compatibility, and system resources. The use of a separate controller card may introduce differences in terms of data transfer rates, supported features, and overall system performance compared to the built-in controller.
Nevertheless, by adding a hard drive controller card to an expansion slot, you can expand the storage capacity and capabilities of your system, allowing for additional hard drives to be connected and controlled.
To learn more about motherboard Click Here: brainly.com/question/29981661
#SPJ11
Related Questions
The act of color balancing in film is known as
A:Blue
B:white
C:Black
D:Gray
Answers
Select from the list below those features that are characteristic of the FTP client.
IT IS TIMED SO PLEASE HURRY 20 Points + Brainliest
- reformatting the remote server
- file processing
- addressing the remote server
- decompressing
- file transfer
- authentication
Answers
Answer:
reformatting the remote server
Explanation:
Mr. Morrison wants told Austin there is always going to be some storms that you have to go through what were Austin’s biggest storms 
Answers
Austin, Texas is no stranger to severe weather, such as hurricanes, tornadoes, and snowstorms. Some of Austin's most powerful storms include
storm Carla (1961)Tornado outbreak (1981)How is this so?* storm Carla (1961): On September 11, 1961, a Category 4 storm made landfall in Port O'Connor, Texas. The storm dumped torrential rains and caused floods in Austin, causing significant damage and power disruptions.
* Tornado outbreak (1981): On Memorial Day weekend in 1981, a tornado outbreak occurred, resulting in six tornadoes in the Austin region. The most powerful tornado was an F4 tornado that devastated Georgetown, killing 11 people and injured over 100 others.
* Ice storm (2021): In January 2021, a significant ice storm hit the Austin region, causing extensive power disruptions and destruction. The storm also caused several road accidents and deaths.
*snowfall (2023): In February 2023, a severe snowfall hit the Austin region, dumping several inches of snow on the city. The storm disrupted transport and caused power outages throughout the region.
These are just a few of Austin's most powerful storms. Mr. Morrison is correct in predicting that Austin will face storms in the future. Residents must be prepared for severe storms and have a strategy in place in case they materialize.
Learn more about storms:
https://brainly.com/question/11163773?
#SPJ1
What is the purpose of the CC option in an email?
A.
Create a carbon copy of the message.
B.
Save the message as a template for future use.
C.
Send a copy of the message to one or more people.
D.
Forward a message to multiple recipients.
( Edmentum MSE )
Answers
Answer:
c
Explanation:
send a copy of the messege
Go to your Canvas course and locate the Assignment: Writing Prompt 1: Is the Internet making us Meaner?and complete the activity.
When you are finished, come back here and copy/paste the following as your answer below:
I have completed the Writing Prompt 1: Is the Internet making us Meaner? activity and submitted my assignment in CANVAS. By pasting this text below. I understand that the grade marked here is NOT the grade for the actual assignment and only a place holder for the grade I earn in Canvas.

Answers
Answer and Explanation:
The Internet is not changing anything other than making you extreme. The nice become nicer, the mean become meaner, the nice become mean, and the mean become nice. The internet just makes things easier to do. It really isn't a factor in if you are mean or not.
Answer:
Explanation:
POV: you didn’t find your answer
what is the relationship between http and www?
Answers
Answer:
The very first part of the web address (before the “www”) indicates whether the site uses HTTP or HTTPS protocols. So, to recap, the difference between HTTP vs HTTPS is simply the presence of an SSL certificate. HTTP doesn't have SSL and HTTPS has SSL, which encrypts your information so your connections are secured.
Answer:
Simply put, Http is the protocol that enables communication online, transferring data from one machine to another. Www is the set of linked hypertext documents that can be viewed on web browsers
Explanation:
for a real-world social network, is bfs or dfs more desirable? provide details.
Answers
.In real-world social networks, BFS is often favoured over DFS because it simulates information flow, makes it possible to perform operations like shortest path finding and network connectivity analysis, and ensures systematic investigation of connections for a thorough understanding of the network.
The Breadth-First Search (BFS) algorithm is typically preferred over Depth-First Search (DFS) in a real-world social network. BFS mimics the way information flows in a network by accessing nodes at each level before advancing to the next level as it explores the social network. Because of this, BFS is appropriate for tasks like determining the shortest path, examining network connections, or locating communities. DFS, on the other hand, is less effective for massive social networks since it can get stuck in deep branches. BFS makes sure that connections are explored systematically and offers a more thorough understanding of the network's interactions
learn more about networks, here:
https://brainly.com/question/29350844
#SPJ11
What is NOT a basic font category? A. Serif B. Sans-Serif C. Subtle-Serif D. Script
Answers
Answer:
I would say C.
the taskbar contains what
Answers
Answer:The taskbar is anchored to the bottom of the screen by default, but can be moved to any screen side, and contains the Start button, buttons for pinned and running applications, and a system tray area that contains notification icons and a clock.
Explanation:
What does anyone who chooses to use speech recognition software need to do?
A) Create a Guest Account.
B) Create an on-screen keyboard.
C) Set up visual alternatives for sounds.
D) Train the computer to understand his or her voice
Answers
Answer:
Train the computer to understand his or her voice.
Explanation:
Thats what u need to do
What ftp command uploads the filename from the current directory on the local computer to the current directory on the remote computer, and allows the use of wildcard metacharacters to specify the filename.
Answers
Answer:
The command is "put filename"
A text file has 456789 letters. If the text file is text wrapped to 80 characters per line (a line folds to the next after 80 columns of characters from the left), the number of lines with letters in the text file would be: . How many letters are in the last line
Answers
Answer:
5710 lines
Explanation:
Which of these would make text on a slide difficult to read?
Ohigh contrast between text and background
Olow contrast between text and background
O a sans serif font
O a large font when the presentation is in a large room
Answers
Be careful when using the SQL UPDATE statement. If you omit the ____ clause, ALL records will be updated!
WHERE
SELECT
GROUP BY
JOIN
Answers
If you omit the WHERE clause in an SQL UPDATE statement, ALL records will be updated.
What is the purpose of the WHERE clause in an SQL UPDATE statement?Be careful when using the SQL UPDATE statement. If you omit the WHERE clause, ALL records will be updated!
The WHERE clause is used to specify the conditions that must be met for the update to be applied to specific rows in the table.
If you don't include a WHERE clause, the update statement will modify all the rows in the table, which can have unintended consequences and potentially lead to data corruption.
It's crucial to double-check your conditions and ensure that the WHERE clause is correctly specified to target the desired rows for updating.
Learn more about WHERE clause
brainly.com/question/30097925
#SPJ11
Write a pseudocode to calculate the sum upto the nth term for the following sequence 1,1,2,3,7,22,155,...., 2. Write a pseudocode to find the factorial of even numbers between two numbers.
Answers
1) Pseudocode to calculate the sum up to the nth term for the given sequence is given as follows
function calculateSum(n):
if n <= 0:
return 0
else if n == 1:
return 1
else if n == 2:
return 2
sequence = [1, 1] # Initialize the sequence with the first two terms
sum = 2 # Initialize the sum with the value of the second term
for i from 3 to n:
term = sequence[i - 2] + (i - 1) * sequence[i - 1] # Calculate the current term
sequence.append(term) # Add the current term to the sequence
sum += term # Add the current term to the sum
return sum
2) Pseudocode to find the factorial of even numbers between two numbers (start and end) -
function calculateFactorial(start, end):
if start % 2 != 0: # If the start number is odd, increment it to make it even
start += 1
result = 1 # Initialize the result as 1
for i from start to end step 2:
result *= i # Multiply the current number with the result
return result
How do the above work?1. The first pseudocode calculates the sum of the sequence by iteratively generating each term based on the previous terms. It starts with the initial terms (1, 1), calculates subsequent terms using the given formula, and accumulates their sum.
2. The second pseudocode finds the factorial of even numbers between a given range. It initializes the result as 1 and iteratively multiplies each even number in the range to calculate the final factorial.
Learn more about Pseudocode at:
https://brainly.com/question/24953880
#SPJ4
How large does a telsa coil need to be to transmit wireless electricity
Answers
The size of the largest operational Tesla Coil is measured to be 38ft or 12 meters. It transmits about 138kw of electricity.
What is a Tesla Coil?Nikola Tesla invented the Tesla coil, an electrical resonant transformer circuit, in 1891. It is used to generate high-voltage, low-current, high-frequency alternating current.
During his efforts to construct a "wireless" lighting system with gas discharge light bulbs that would shine in an oscillating electric field generated by a high voltage, high-frequency power source, Tesla devised the Tesla coil.
Tesla coils provide various health risks owing to high voltage radio frequency emission, including skin burns and nervous system and heart damage.
Learn more about Tesla Coil:
https://brainly.com/question/7295601
#SPJ1
What can happen if you do not follow the directions when cooking or baking? (Give 4 examples in a sentence each)
Answers
Answer: 1: You will make it incorrectaly 2: It will taste terrible 3: You may break appliences 4: you may burn down your house.
Explanation:
Choose all of the items that are important factors to consider for effective web design.
purpose
top-level domain name
content
visually appealing
audience
html
easy to use
Answers
Here's a list of the important factors to consider for effective web design:
PurposeTop-level domain nameContentVisually appealingAudienceHTMLEasy to useWhat is Web Design?Clever web design takes into account a range of factors, such as the objective of the website, the domain name, the quality of the content and the aesthetic elements, the intended audience, the HTML framework, and the ease of use. '
Having a clear comprehension of the goal of the website is crucial in determining the appropriate design strategy; in addition, a fitting domain name can positively impact branding efforts.
Compelling content captivates visitors. The visual aspect is a crucial factor in catching attention and improving the user's experience. Having an understanding of the intended viewers allows for customized creation and material presentation. The fundamental basis for organizing web pages is provided by HTML.
Read more about web design here:
https://brainly.com/question/25941596
#SPJ1
The library is purchasing Argus TL2530P All-In-One Thin clients. What does it mean that the thin clients are 802.3at compliant?
Answers
In this set up, the servers are workstations which perform computations or provide services such as print service, data storage, data computing service, etc. The servers are specialized workstations which have the hardware and software resources particular to the type of service they provide.
1. Server providing data storage will possess database applications.
2. Print server will have applications to provide print capability.
The clients, in this set up, are workstations or other technological devices which rely on the servers and their applications to perform the computations and provide the services and needed by the client.
The client has the user interface needed to access the applications on the server. The client itself does not performs any computations while the server is responsible and equipped to perform all the application-level functions.
Each server handles a smaller number of thin clients since all the processing is done at the server end. Each server handles more thick clients since less processing is done at the server end.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1
tabitha is assigning initial values to each variable in her program. which term describes the process of assigning an initial value to a variable? question 12 options: initializing storing valuing declaring
Answers
The term that describes the process of assigning an initial value to a variable is "initializing." (Option a)
Why is initializing important in programming?Initializing variables is important in programming because it sets an initial value for a variable before it is used in computations or operations.
This helps avoid unexpected behavior or errors caused by using uninitialized variables.
Initialization ensures predictable and consistent behavior, promoting code reliability and preventing potential bugs or issues.
Learn more about initializing at:
https://brainly.com/question/27230187
#SPJ4
______ is data that has been shaped into a form that is meaningful to human beings.
Answers
When we talk about information, we mean data that has been transformed into a format that is understandable to people.
What is an information system, exactly?We define information as data that has been transformed into a format that is understandable and practical for people. As opposed to information, which is a collection of organised and sorted facts that may be used and understood, data is a stream of unorganised facts that represents events that take place in organisations or the physical environment. Information is what is created when unprocessed data is transformed into something meaningful. In order to gather usable data, particularly within an organisation, an information system combines hardware, software, and communication networks. Many organisations rely on information technology to carry out and manage their operations, communicate with customers, and outperform their rivals.To learn more about information system, refer to:
https://brainly.com/question/24944623
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
Which command can be used to remove a job from the list of pending jobs?
Answers
The specific command to remove a job from the list of pending jobs depends on the system or application that is being used to manage the jobs.
However, in general, there are a few approaches that can be taken to remove a job from the list of pending jobs. Cancel the job: If the job has not started running yet, it can usually be cancelled using a command such as "canceljob" or "qdel" (for job schedulers like PBS or Slurm) followed by the job ID. Kill the job: If the job has already started running, it may be possible to kill it using a command like "kill" or "pkill" (for Linux-based systems) followed by the process ID of the job. Remove the job from the queue: If the job is still in the queue waiting to be run, it may be possible to remove it using a command like "qdel" or "scancel" (for job schedulers like PBS or Slurm) followed by the job ID.
Learn more about command to remove here:
https://brainly.com/question/30173976
#SPJ11
A Hospital wants to store different types of data I need to find the best storage device for each type and why what is the best storage device to store the patient's data
Answers
Answer:
On-Premise Data storage
Explanation:
On-Premise Data storage prefers on-premise data to store and manage patient data. The main reason is straightforward and control over the in-house data. On-premise data centers do not need wireless connections, and no risk of downtimes. Healthcare can access the data from secure, making on-premise data storage choices.
On-premise data storage stored and managed escalates and demand more physical space. When hospitals use on-premise data storage, they have to arrange the physical space within the premises of the host of the server. On-premise data is connected to the local network and could consider the secure data option in upkeeping the security of premise healthcare with anti-virus software, firewalls, and multifactor authentication.
Hospital moves toward holistic data storage option. The on-premise to cloud data storage for healthcare affirms that challenges are nullified.
consider an implantable insulin pump and an implantable cardioverter defibrillator. how would a successful jamming attack affect them?
Answers
A successful jamming attack on an implantable insulin pump or an implantable cardioverter defibrillator could potentially cause serious harm or even death to the patient.
The insulin pump may fail to deliver the necessary dose of insulin, leading to hyperglycemia or diabetic ketoacidosis. On the other hand, a cardioverter defibrillator may fail to detect or treat dangerous heart rhythms, leading to cardiac arrest or other life-threatening conditions. In both cases, a successful jamming attack could interfere with the normal functioning of the devices and compromise the patient's health. It is therefore critical to ensure the security and reliability of these medical devices to prevent such attacks from occurring.
To learn more about Jamming attack, click here:
https://brainly.com/question/28153785
#SPJ11
T/F : in any comparison the two values compared can be either variables or constants
Answers
The statement is true. Comparisons can involve variables or constants, providing flexibility in evaluating conditions.
How to compare variables and constants?In any comparison, the values being compared can be either variables or constants. Variables represent placeholders for values that can change during program execution, while constants are fixed values that remain unchanged.
When performing a comparison, the variables or constants are evaluated to determine if the comparison statement is true or false. The comparison can involve various operators such as equality (==), inequality (!=), greater than (>), less than (<), etc.
Using variables in comparisons allows for flexibility in programming logic, as the values can be updated based on user input or calculations within the program. Constants, on the other hand, are useful when comparing against known, fixed values that do not change.
Both variables and constants play essential roles in comparisons and decision-making within programs. They enable conditional statements, loops, and other control structures to be executed based on the outcome of the comparison, providing flexibility and adaptability in program behavior.
Learn more about variables
brainly.com/question/15740935
#SPJ11
Question 2
What are the main components of file management? Check all that apply.
Answers
Answer:
Component of file management:
PDF elements: It is one of the best file management system software. With the help of OCR you can convert PDF file into WORD, EXCEL, OR POWER POINT. It supported multiple operating systems like Mac , Windows , and iOS. Agiloft : It is great in terms of managing large enterprise document . Graphical Workflow feature lets you create a step by step model on how a certain document should be processed on each step. More information and less hassle lead to efficient task execution. With Audit Trail feature, you can easily find what changes were made at a certain time and who was responsible. Round Robin Assignment feature helps distribute work fairly. Alfresco one: Alfresco One is available in both cloud and self-hosted option. This file management system's compatibility with different devices and operating systems make it easy for users to view, manage and change the documents from anywhere. Cabinet: This file management system is also available in self-hosted and cloud options. It is compatible with several accounting software and email clients. Electronic Signatures can also be inserted into documents. Document storage, search, and retrieval are easy and efficient. Content verse: This file management system is designed in a very versatile way so that it can fit the requirements of any organization small or large. File storage and finding or retrieving is really fast. With the help of workflow management, you can set milestones and goals for your team. Digital Drawer: This file management system is only available in on-premises options. Importing a document is an easy process as you can scan or upload documents. Every document is secure and nobody can access your data without authorization. Documents organization is efficient as you can place files in a window like a tree folder structure.what important part of support for object-oriented programming is missing in simula 67?
Answers
Simula 67 is a programming language developed in the 1960s, which is considered the first object-oriented programming (OOP) language. It introduced the concepts of classes, objects, and inheritance, which are fundamental to modern OOP languages. However, there is an important part of support for object-oriented programming that is missing in Simula 67.
The missing element in Simula 67 is "polymorphism". Polymorphism is a key principle of OOP that allows objects of different classes to be treated as objects of a common superclass. It enables the programmer to write more flexible and reusable code, as the same function or method can be used with different types of objects, simplifying code maintenance and enhancing code reusability. In Simula 67, programmers could not fully utilize polymorphism, as it lacks support for dynamic dispatch, which allows a method to be resolved at runtime based on the actual type of the object rather than its declared type.
While Simula 67 played a crucial role in the development of object-oriented programming, it lacked support for polymorphism, a vital OOP concept. This limitation prevented the full potential of OOP from being realized within the language, and it was not until the advent of languages like Smalltalk and later, C++, that polymorphism became an integral part of OOP, contributing to its widespread adoption and success in software development.
To learn more about object-oriented programming, visit:
https://brainly.com/question/26709198
#SPJ11
Please! I need help matching this.
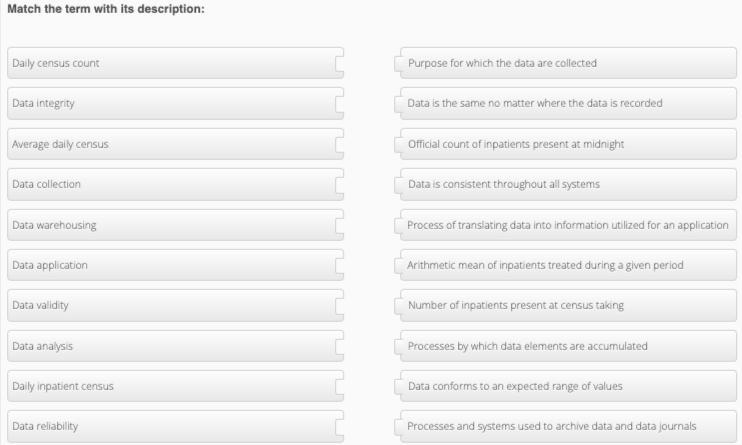
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
The ____ of a process contains temporary data such as function parameters, return addresses, and local variables
Answers
The stack of a process contains temporary data such as function parameters, return addresses, and local variables. It is a type of memory management that is used by computers. In a computer system, there are different types of memories used to store data.
These include primary memory (RAM), secondary memory (hard disks), and cache memory. The stack is a part of primary memory, and it is used to store temporary data that is required by the computer during the execution of a process. When a process is started, a stack is created for it. The stack contains information about the process, such as its name, its size, and its location in memory. It also contains temporary data such as function parameters, return addresses, and local variables. As the process executes, the stack grows and shrinks to accommodate the data that is required by the process. When the process terminates, the stack is deleted. In summary, the stack is an essential part of memory management, and it is used to store temporary data required by the computer during the execution of a process.
To know more about management visit:
https://brainly.com/question/32216947
#SPJ11