HTML stands for
-Hyperlink Tools Main Language
-Hypertools Main Linguistics
-Hypertools Markup Linguistics
-Hypertext Markup Language
Answers
The abbreviation of HTML stands for Hypertext Markup Language.
HTML (Hypertext Markup Language) is a coding language used to build web pages and make them appear on the internet. HTML is the language used to create web pages, and it stands for Hypertext Markup Language. HTML's key feature is that it enables users to insert images, videos, hyperlinks, and other digital elements into a web page. HTML files can be constructed and edited with a simple text editor or a specialized HTML editor. It's simple to master the basics of HTML, and it's a good place to start if you want to learn about web development. In summary, the answer to the question is, "Hypertext Markup Language."
Learn more about language:https://brainly.com/question/10585737
#SPJ11
Related Questions
Click on the arrow in A. What will enable you to do?
Answers
Answer:
We need a picture
Explanation:
Drag the tiles to the boxes to form correct pairs.
Match the items to their uses.
simple design template
illustrations
contrast colors and background
note page
to used to improve the appearance of the presentation
used to refer to content while delivering a presentation
used to make
the content easily readable
used to complement content

Answers
The correct matching of the items to their users is given below:
Simple design template - used to improve the appearance of the presentationIllustrations - used to complement the contentContrast colors and background - used to make the content easily readableNote page - used to refer to content while delivering a presentationWhat is an Illustration?In print and digitally published media such as posters, flyers, magazines, books, educational materials, animations, video games, and films, illustrations are decorations, interpretations, or visual explanations of a text, concept, or process.
Read more about illustrations here:
https://brainly.com/question/26475534
#SPJ1
which of the following types of attacks are possible on the building automation systems - the building’s heating, ventilation and air conditioning (hvac) systems? [choose all that apply]
Answers
There are several types of attacks that are possible on building automation systems, including the building's HVAC systems. Some possible types of attacks include:Malware or virus attacks, Denial of Service (DOS) attacks,Physical attacks ,Remote access attacks.
Here are some of the possible attacks on building automation systems explain as :
Malware or virus attacks - these can infiltrate the system and cause damage or disrupt its normal operation. Denial of Service (DoS) attacks - these can overload the system with traffic or requests, causing it to crash or become unresponsive.Physical attacks - someone could physically damage or tamper with the HVAC system components, causing them to malfunction or stop working altogether. Insider attacks - someone with authorized access to the system could intentionally or unintentionally cause harm or disrupt its normal operation.Remote access attacks - someone could gain unauthorized access to the system through a remote connection, such as via the internet or a wireless network.Overall, it's important for building owners and operators to be aware of these potential threats and take steps to mitigate them through security measures such as firewalls, encryption, access controls, and regular system updates and maintenance.
To learn more about building automation systems visit: https://brainly.com/question/25984569
#SPJ11
when you turn on your computer for the day, you notice lights and fans but no beeps and no video. the num lock light does not come on. what might be the problem with your computer? (select all that apply.)
Answers
Computer - Processor has failed or is not seated properly; motherboard has failed; RAM is not working properly.
What is computer?
A computer is indeed a digital electrical device that may be configured to automatically perform series of logical or mathematical operations (computation). Programs are generic sets or operations that can be carried out by modern computers. These apps give computers the ability to carry out a variety of tasks. A computer system is a "full" computer that comes with the peripheral devices, operating system, and hardware required for "full" functioning. This phrase may also apply to a collection of connected computers that work as a unit, like a computer network a computer cluster.
Computers are used as control systems in a wide range of industrial goods.
To learn more about computer
https://brainly.com/question/24540334
#SPJ4
refer to the exhibit. pc1 is unable to communicate with server 1. the network administrator issues the show interfaces trunk command to begin troubleshooting. what conclusion can be made based on the output of this command?
Answers
Note that the concluion that acan be made based on the output of the command is that "Interface G0/2 is not configured as a trunk."
What is the rationale for the above response?The G0/2 interface of DLS1 is not listed in the display interfaces trunk output.
This shows that the interface was most likely not setup as a trunk link. The G0/2 interface of DLS1 is not listed in the display interfaces trunk output.
This shows that the interface was most likely not setup as a trunk link.
Learn more about command at:
https://brainly.com/question/30319932
#SPJ1
Full qeustion:
Fefer to the exhibit (Attached). pc1 is unable to communicate with server 1. the network administrator issues the show interfaces trunk command to begin troubleshooting. what conclusion can be made based on the output of this command?

three different types of routing protocols in multiphop ad hoc network is
Answers
There are three main types of routing protocols in a multiphop ad hoc network:
1. Proactive Routing Protocols: In this type of protocol, nodes constantly exchange information with each other to maintain up-to-date routing tables. This ensures that the network has an accurate and efficient path for data transmission at all times. Examples of proactive routing protocols include OLSR and Optimized Link State Routing (OLSR).
2. Reactive Routing Protocols: Reactive protocols are also known as on-demand routing protocols. These protocols only establish routes when a node needs to send data to a destination node. This means that the network does not maintain a constant flow of data, but rather only sends data when necessary. Examples of reactive routing protocols include Ad hoc On-Demand Distance Vector (AODV) and Dynamic Source Routing (DSR).
3. Hybrid Routing Protocols: Hybrid protocols combine the best features of proactive and reactive protocols. In a hybrid protocol, nodes maintain a proactive routing table for nodes that are frequently accessed, while maintaining a reactive protocol for less frequently accessed nodes. Examples of hybrid routing protocols include Zone Routing Protocol (ZRP) and Temporally Ordered Routing Algorithm (TORA).
To know more about Algorithm please refer:
https://brainly.com/question/22984934
#SPJ11
OPERATION SHEET 6.2.2 Given the Neccesary tools materials and equipment identify the common faults and errors of computer when you detached the following Keyboard-PS/2 Mouse-PS/2 Hard disk- IDE cable Floppy disk drive-IDE cable Room disk-IDE CABLE

Answers
Answer: NO MORE TYPING! NO MORE CLICKING! NO MORE MEMORY! NO MORE OPERATING!
in a recursive power function that calculates some base to a positive exp power, at what value of exp do you stop? the function will continually multiply the base times the value returned by the power function with the base argument one smaller.
Answers
In a recursive power function, the value of exp at which the recursion stops depends on the specific implementation of the function and the requirements of the program using the function.
Generally, the recursion stops when the exp value reaches 0 or 1, as any number raised to the 0th power equals 1, and any number raised to the 1st power equals itself. However, depending on the program's requirements, the recursion may stop at a different value of exp.
For example, if the program only needs to calculate the power of 2 up to a certain limit, the recursion could stop at that limit and not continue to calculate higher powers. It is important to consider the requirements of the program and choose an appropriate stopping point to avoid unnecessary calculations and improve efficiency.
You can learn more about recursive power at: brainly.com/question/13152599
#SPJ11
Which situations make use of interactive multimedia and which do not? Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister. Roy is going through a tutorial on his laptop that explains a do-it-yourself project. Jaden is listening to a presentation on early music in his class. Fred is answering an online quiz that requires him to select correct answers. Linear Multimedia Kristen is watching an educational film on her tablet. Non-linear Multimedia
Answers
The situation that make use of interactive multimedia is Roy is going through a tutorial on his laptop that explains a do-it-yourself project, and that do not is Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister.
What is an interactive multimedia?Interactive multimedia is a type of interaction in which the user can operate, control, and change the text, image, and picture, and function in a phone or computer.
Thus, the correct options are A and B.
Learn more about interactive multimedia
https://brainly.com/question/26090715
#SPJ1
c724 wgu True or false. A storage device consists of all the components that work together to process data into useful information
Answers
Answer:
False
Explanation:
A output device consists of all the components that work together to process data into useful information
What are at least four impacts of augmented reality, virtual reality, and mixed reality on teaching-learning processes rather than gaming and entertainment?
Answers
Augmented reality (AR), virtual reality (VR), and mixed reality (MR) have significant impacts on teaching-learning processes.
1. Enhanced Engagement: These technologies increase student engagement by providing immersive and interactive learning experiences, making it easier for students to understand complex concepts.
2. Collaboration and Communication: AR, VR, and MR facilitate collaboration and communication among students, allowing them to work together on projects and share ideas in real-time, regardless of geographical barriers.
3. Personalized Learning: These technologies enable personalized learning by allowing educators to create tailored content and experiences for individual students based on their unique needs and learning styles.
4. Skill Development: AR, VR, and MR help develop various skills, such as critical thinking, problem-solving, and creativity, by providing hands-on experiences and simulations that mimic real-world situations.
To know more about Augmented reality visit:
brainly.com/question/29036753
#SPJ11
exchanging a secret key over the phone before using it to send a secret message over the internet would be a form of:
Answers
Answer:
end-to-end encryption
Explanation:
im only guessing because you dont provide me with a list of options. so, this sounds similar to end-to-end encryption, where participants in a digital conversation use a secret key to ensure that only they can decrypt and read the messages.
ursa major solar has selected report folders that are shared with a small group of users who are on lightning experience. the administrator needs to prevent these users from customizing the information in the reports. what should the administrator do to achieve this goal?
Answers
The administrator must prevent such users from customizing this same information in Ursa major solar reports for lightning experience. To accomplish this, the administrator must "Lock report filters."
What is defined as the Lock filters?Locking a filter, which prevents Viewers from making direct changes to it.
The specified filter settings will be visible to the Viewer, but editing will be disabled. Locking a filter enables you to restrict the data selected so anyone with View Only access to the this report cannot alter the locked filters. This allows you to grant very limited permissions and have greater control over your users' access.Furthermore, you can 'Lock' the filters just on reports. By design, the planning are not synced with report template, allowing you to have numerous schedules per report template, but you can force them to combine by "locking" a report filter.Thus, by locking the report using filter, Ursa major prevent such users from customizing this information for lightning experience.
To know more about the filters, here
https://brainly.com/question/7411233
#SPJ4
__________ variables are factors that come from outside a theoretical system and cannot be explained by that system.
Answers
Exogenous variables are factors that come from outside a theoretical system and cannot be explained by that system.
Given data:
The variables referred to in the statement are called "exogenous" variables. Exogenous variables are factors or influences that originate from outside the system being studied or analyzed. These variables cannot be explained or determined by the internal workings of the system itself.
Exogenous variables are important in various fields such as economics, social sciences, and systems analysis. They are typically used to account for external factors that can affect the behavior or outcomes of a system. These variables are considered independent of the system and are often treated as given or assumed rather than being directly influenced or controlled by the system.
To learn more about endogenous and exogenous variables click:
https://brainly.com/question/32230531
#SPJ4
A security program alerts you of a failed logon attempt to a secure system. On investigation, you learn the system's normal user accidentally had caps lock turned on. What kind of alert was it?A.True positiveB.True negativeC.False positiveD.False negative
Answers
The alert in this scenario would be a false positive. A false positive occurs when the security program mistakenly identifies a non-threatening event as a security breach.
In this case, the failed logon attempt was due to the user accidentally having caps lock turned on, which does not pose a security risk. The security program incorrectly flagged it as a potential unauthorized access attempt, leading to the false positive alert.
False positives can occur in various security systems, such as intrusion detection systems or antivirus software. While these systems aim to be proactive in identifying potential threats, false positives can be disruptive and may require additional investigation and resources to determine the actual threat level. Regular monitoring and fine-tuning of security systems can help reduce the occurrence of false positives and improve their overall effectiveness.
Learn more about security breach here:
https://brainly.com/question/29822649
#SPJ11
Assume that chessboard has been declared to be a two-dimensional array of strings. Write a statement that instantiates an 8x8 array of strings and assign it to chessboard.
Answers
The statement that instantiates an 8x8 array of strings is chessboard = new String[8][8]
Explain what an array is:This arrays is a grouping of identically typed items that are stored in adjacent memory regions and may each be separately referred to via a reference to a special identifier. There is no need to declare five distinct variables when declaring an array of five int values (each with its own identifier).
What does the Excel term array mean?A formula with numerous computations capabilities on one or maybe more elements in an array is known as that of an array formula. An assortment can be thought of as a row, column, or mix of rows or columns of values.
To know more about Array visit:
https://brainly.com/question/19570024
#SPJ4
What digital security measure can you use to catch and delete bad software?
help
Anti-virus
Encryption
Firewall
Password
Answers
Hey there :)
As per question, the best way is Encryption.
You may feel this as wrong answer but as per the latest scrutiny, I'll explain:-
Option: Antivirus (NO)
This is safe and does the job to some extent. But none has ever found with clear proof of the best antivirus. Everyone of those antivruses has some pros and cons.
Some of them does the job of protection but with them, they also give us some threats !
Option: Firewall (No)
Firewall also helps to catch and delete malicious softwares to 79%, but it doesnt give you the maximum security from data breaches.
Option: Password (Obviously NO)
Passwords may help in personal accounts and bank, but they are useless in online world. Nothing can be protected fully by passwords. Also, password is the easiest way for cyber criminals to attack.
So, answer is "Encryption"
who was Dr. Hean Hollerith
Answers
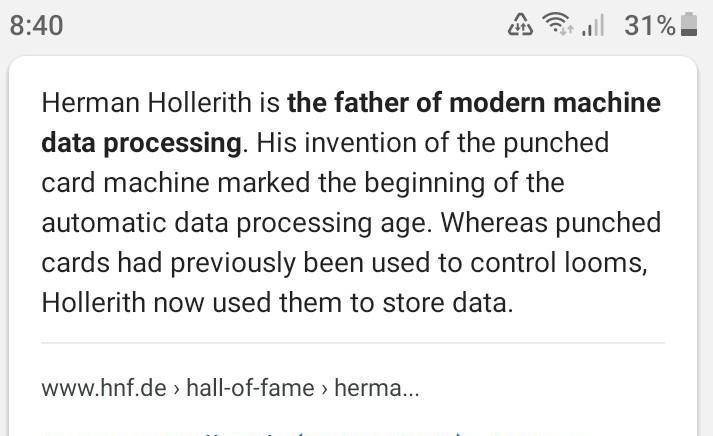
Answer: Herman Hollerith, (born February 29, 1860, Buffalo, New York, U.S.—died November 17, 1929, Washington, D.C.), American inventor of a tabulating machine that was an important precursor of the electronic computer.
Explanation:
Answer:
☝️here is a answer ......
1
4
What data unit is encapsulated inside a packet?
O datagram
O segment
frame
O session
Answers
Answer:
Segment.
Explanation:
In Computer Networking, encapsulation can be defined as the process of adding a header to a data unit received by a lower layer protocol from a higher layer protocol during data transmission. This ultimately implies that, the header (segment) of a higher layer protocol such as an application layer, is the data of a lower layer such as a transportation layer in the Transmission Control Protocol and Internet Protocol (TCP/IP).
The TCP/IP model comprises of four (4) layers;
1. Application layer: this is the fourth layer of the TCP/IP model. Here, the data unit is encapsulated into segments and sent to the transport layer.
2. Transport layer (layer 3): it receives the segment and encapsulates it into packets and sends to the internet layer.
3. Internet layer (layer 2): packets are encapsulated into frames.
4. Network layer (layer 1): frames are then converted into bits and sent across the network (LAN).
Hence, the data unit encapsulated inside a packet is known as segment, which is typically referred to as packet segmentation.
Additionally, these data, segments, packets, frames and bits transmitted across various layers are known as protocol data units (PDUs).
To find the item with the lowest cost in column C, what Excel formula should be used in C11? SUM (C3:C10) =MAX (C4:C10) MIN (C3:C10) =MIN (C4:C10)
Answers
Answer:
The correct excel formula to use can't be sum cause that's addition of everything in the column. It can't be Max cause that's for the highest. Depending on where the values start, it could be either MIN(C3:C10) or MIN(C4:C10)
The correct Excel formula to find the item with the lowest cost in column C would be =MIN(C3:C10).
The MIN function in Excel is used to find the minimum value in a range of cells. In this case, we want to find the lowest cost in column C, so we use the MIN function with the range C3:C10. This will compare the values in cells C3 to C10 and return the smallest value.
When you enter the formula =MIN(C3:C10) in cell C11, Excel will evaluate the range C3:C10 and return the smallest value in that range. It will display the item with the lowest cost from column C.
By using the MIN function in Excel, you can easily identify the item with the lowest cost in a given range of cells. This is useful for analyzing data and making decisions based on the minimum value in a set of values. Excel provides a range of functions to perform calculations and analyze data, making it a powerful tool for managing and manipulating numerical information.
To know more about Excel Formula, visit
https://brainly.com/question/20497277
#SPJ11
Imagine you have borrowed your friend's computer to work on a class project. Checking
the computer out, you notice they've left their web browser open and are signed in to
their email account. Would it be considered a computer crime to read their email, even
though you didn't "hack" their password? What if they had left a text file on their
desktop that included personal information, like their social security number, banking
and credit card information, passwords for sites, etc., but didn't have it password
protected-would accessing that file be a computer crime, even though there was no
password protection on it? Explain your answers
Answers
Answer:
Yes.It would be considered as a computer Crime.
Explanation:
This is because you are an unauthorised user
It would be considered a computer crime when one accesses unauthorized information.
What are computer crimes?Computer crimes are also known as cyber crimes. It ranges from accessing information illegally, committing fraud, phishing, identity theft, and so on.
When a user of a computer accesses information that is unauthorized on the computer, such a user has committed a computer crime. It does not matter whether the accessed information is password-protected or otherwise. If it is not stated categorically that such information can be freely accessed, then accessing it is illegal.
More on cyber crimes can be found here: https://brainly.com/question/24182813
#SPJ2
what does an organization do to identify areas of vulnerability within their network and security systems?
Answers
Organizations can use a variety of methods to identify areas of vulnerability within their network and security systems.
These methods include:
conducting a risk assessmentscanning external systemsconducting vulnerability scansdeploying a defense-in-depth solution.Additionally, organizations may call on ethical hackers to uncover potential security risks and identify vulnerabilities in target systems, networks, or systems.
Organizations can use a variety of methods to identify areas of vulnerability within their network and security systems. These methods include conducting a risk assessment, scanning external systems, conducting vulnerability scans, deploying a defense-in-depth solution, and calling on ethical hackers to uncover potential security risks and identify vulnerabilities in target systems, networks, or systems.
Learn more about vulnerabilities of a network and its security systems:
https://brainly.com/question/30325550
#SPJ4
Do you think that the United States would have been able to win world war l and world war ll without the help of code talkers?
Answers
Code talkers helped US to win both the world wars. As the code talkers were the persons who are experts in delivering secret messages in both regional languages and English.
A name, code talker, was given to American Indians who used their regional language to convey secret messages in the warzones.
Type 1 code was the first code created. Code talkers had a tough task of keep moving because there was always a threat to the transmitted messages.
To learn more about code talkers,
https://brainly.com/question/27876958
Mac or PC (Need more opinions!)
Just pick which one do you like and why. I need it for my research paper, please.
Answers
Answer:
PC or mac
Explanation:
depends. If you want more focused on a work aspect then go with mac. If you want more of gaming and compatibility go with a pc. But overall go with a pc. Because some programs require windows.
Compare and contrast the NIST digital signature scheme with the
Elgamal and schnorr digital signature schemes?
Answers
The NIST digital signature scheme, ElGamal, and Schnorr digital signature schemes are all cryptographic algorithms used for digital signatures.
The NIST digital signature scheme is based on the Digital Signature Standard (DSS) developed by the National Institute of Standards and Technology (NIST). It uses the Digital Signature Algorithm (DSA) and is widely adopted in various applications. It provides strong security and efficient signature verification.On the other hand, ElGamal and Schnorr are both based on the discrete logarithm problem. The ElGamal signature scheme is a probabilistic algorithm that generates a pair of values as the signature. It offers high security and is particularly suitable for applications where signer anonymity is desired. However, it requires a larger key size compared to other schemes.The Schnorr signature scheme, named after its inventor Claus Schnorr, is a deterministic algorithm that produces a shorter signature compared to ElGamal. It offers strong security and is known for its simplicity and efficiency. Schnorr signatures also support additional features like multi-signatures and interactive protocols.While all three schemes are used for digital signatures, they differ in terms of their underlying mathematics, security levels, and efficiency. The NIST digital signature scheme is widely recognized and adopted due to its standardized nature and strong security. ElGamal offers signer anonymity but requires larger key sizes. Schnorr, on the other hand, provides shorter signatures and additional features like multi-signatures.In summary, the NIST digital signature scheme, ElGamal, and Schnorr digital signature schemes each have their own strengths and characteristics, catering to different security and efficiency requirements in various applications.Learn more about digital signature scheme
brainly.com/question/31971616
#SPJ11
Which of the following are print options select all that apply
A)Collated
B)page orientation
C)margins
D)font
Answers
Answer:
A
Explanation:
the rest are not print options but layout options, tho just check a print preview of a blank word doc to confirm if b is valid
45 POINTS!!!!!!!!!!!PLZ HELP ME!!!!!!!!!!Select the correct answer. Which statement describes a characteristic of dynamic websites? A. They can be developed quickly. B. They are not functional. C. They are less flexible than static websites. D. They have content that is constantly updated. E. They are less expensive to host than static websites.
Answers
Answer:
D
Explanation:
Because anyone can update dynamic websites at any time, these are more functional and flexible. Therefore, content on dynamic websites keeps changing. Diverse content encourages users to return to these websites. The disadvantages of dynamic websites are that they are more expensive and take longer to develop than static websites. Hosting dynamic websites also costs more.
Answer:
D
Explanation:
- One simple system effect or potential effect - One complicated system effect or potential effect, including discussion of one or more of Senge's Eleven Laws of the Fifth Discipline - One complex system effect or potential effect
Answers
Simple System Effect or Potential Effect:One simple system effect or potential effect could be the implementation of a new software system in an organization, but once familiarized, it can streamline processes, improve data accuracy, and enhance overall productivity.
This can lead to increased efficiency and automation of certain tasks, reducing the need for manual work and potentially saving time and resources. Employees may experience a learning curve as they adapt to the new system.
Complicated System Effect or Potential Effect:
A complicated system effect or potential effect could be the introduction of a new hierarchical structure within an organization. This change may involve redefining roles, responsibilities, and reporting relationships. It can lead to a more streamlined decision-making process, clearer lines of authority, and improved coordination between different departments. However, implementing such a change may also face resistance, as it disrupts established power dynamics and may require individuals to adapt to new roles and responsibilities.
In the context of Senge's Eleven Laws of the Fifth Discipline, one relevant law that could apply to this complicated system effect is the "Law of Requisite Variety." This law states that to effectively deal with complexity, a system must have internal diversity or variety that matches the external complexity it faces. When implementing a new hierarchical structure, it is important to consider the diversity of skills, knowledge, and perspectives required to effectively manage and operate within the new system. Ensuring that individuals with the appropriate variety of skills and expertise are placed in relevant positions can enhance the system's ability to address complex challenges.
Complex System Effect or Potential Effect:
A complex system effect or potential effect could be the implementation of a new organizational culture focused on innovation and collaboration. This can result in increased employee engagement, creativity, and adaptability to changing market conditions. By fostering an environment that encourages experimentation, learning, and sharing of ideas, organizations can improve their ability to navigate complex and uncertain situations. This can lead to the development of innovative solutions, improved problem-solving capabilities, and a competitive advantage.
In the context of Senge's Eleven Laws of the Fifth Discipline, one relevant law that could apply to this complex system effect is the "Law of Unintended Consequences." This law suggests that actions taken within a system often have unexpected consequences that may go beyond the initial intent. When implementing a new organizational culture, it is crucial to consider the potential unintended consequences that may arise. For example, fostering a culture of collaboration and innovation may lead to increased risk-taking, which could result in failures or conflicts. Organizations must be prepared to address these unintended consequences and adapt their strategies accordingly to maintain a healthy and productive system.
To know more about productivity click the link below:
brainly.com/question/31916354
#SPJ11
what is computer engineering
Answers
Answer:
Computer Engineering is the discipline embodying science and technology in the design, building, implementing, and maintenance of modern computer systems and computer-controlled equipment software, and hardware components.
Explanation:
Computing engineering is an engineering branch that incorporates several computer sciences and engineering industries that are necessary for the development of computer equipment and software. In general, computer engineers are educated not only in software engineering or electronic engineering but also in software design and software integration. Computer engineers participate in numerous computer software and hardware aspects from the conception of different microcontrollers, micro-producers, personal computers, and supercomputers to the design of circuits.
Computer engineers are usually involved in the writing of software and firmware for embedded microcontrollers, the design of VLSI chips, analog sensors, the construction of mixed-signal systems, and the design of operating systems. The robotic research process is also suitable for the use of digital systems to control and monitor electrical systems, such as drives, communications, and sensors. Computer engineers are also suitable.
In many universities, informatics students are allowed to choose areas of in-depth study in their junior and senior levels, as the full size of knowledge used in computer design and use is beyond the scope of a bachelor's degree. Other institutions may require students to complete one or two years of general engineering before declaring the focus on computer technology
what makes a good design
Answers
Answer:
Life
Explanation:Life makes a good design or just some cottonwood fabric that 10*==^667