FILL IN THE BLANK. in access, when you add a new record by using a form, you must___to save the new record to the database.
Answers
In access, when you add a new record by using a form, you must press Shift+Enter to save the new record to the database.
Access saves the new record that you added when you view another record or close the table or form. Press Shift+Enter to explicitly save changes to the current record.
What is a Database?
A database is a systematic or organized collection of related information that is stored in a way that allows for easy access, retrieval, management, and updating.
It is the repository for all data, similar to a library that houses a diverse collection of books from various genres.
To know more about Access, visit: https://brainly.com/question/14350549
#SPJ1
Related Questions
Analyze the following source code and then find the best description. void Task1(void *pvParameters)\{ for (;;) \{ if (xSemaphoreTake(mutex, 10/portTICK_PERIOD_MS) = pdTRUE) Serial.println("TaskMutex"); xSemaphoreGive(mutex); \} vTaskDelay(10/portTICK_PERIOD_MS); (a) If the semaphore is not available, the system will wait 10 ticks to see if it becomes free. (b) If the semaphore is available within 10 ms, the system will send "TaskMutex" via serial communcation. (c) If the semaphore is not available after 10 ms, the system will send "TaskMutex" via serial communcation. (d) This task will be executed every 10 ms.
Answers
The best description is (b) If the semaphore is available within 10 ms, the system will send "TaskMutex" via serial communication.
The code snippet is a task function written in C for a real-time operating system. Let's analyze the code line by line:
1. The function Task1 is defined with a void pointer argument (pvParameters), indicating that it is a task function for an RTOS.
2. The for (;;) loop represents an infinite loop, which means the task will keep executing repeatedly.
3. Inside the loop, the code checks if the semaphore (mutex) can be taken by calling xSemaphoreTake(mutex, 10/portTICK_PERIOD_MS). The second argument, 10/portTICK_PERIOD_MS, indicates a timeout value of 10 ms.
4. If the semaphore is successfully taken (xSemaphoreTake returns pdTRUE), the code executes Serial.println("TaskMutex"), which sends the string "TaskMutex" via serial communication.
5. After executing the code within the if statement, xSemaphoreGive(mutex) is called to release the semaphore.
6. The vTaskDelay(10/portTICK_PERIOD_MS) function suspends the task for 10 ms before executing the next iteration of the loop.
Based on the code analysis, the best description is (b) If the semaphore is available within 10 ms, the system will send "TaskMutex" via serial communication. The code waits for a maximum of 10 ms to acquire the semaphore, and if it succeeds, it sends "TaskMutex" via serial communication. If the semaphore is not available within 10 ms, the code moves on to the next iteration of the loop without sending anything.
To know more about serial communication, visit
https://brainly.com/question/33186106
#SPJ11
JavaScript is an object-based programming language that involves working with the properties and methods associated with objects. True False
Answers
JavaScript is an object-based programming language that involves working with the properties and methods associated with objects is a true statement.
Is JavaScript Object-based?Yes, JavaScript are known to be a kind of object-based language that depends on prototypes, due to the fact that it has different basis.
Hence, JavaScript is an object-based programming language that involves working with the properties and methods associated with objects is a true statement.
Learn more about JavaScript from
https://brainly.com/question/16698901
#SPJ1
Python program which squares all the number in list number = [2,3,4,5,6,7,8,9] and store it in another list name square. Please write a program :|
Answers
Answer:
l = [2,3,4,5,6,7,8,9]
def solve(l):
for i in l:
print(i**2)
solve(l)
Explanation:
loops through each element of the list and squares it.
Use bubblesort to arrange the numbers 76, 51, 66, 38, 41 and 18 into ascending order. Write the list after each exchange of numbers. How many comparisons are there altogether?.
Answers
Below is the complete step wise solution of the arrangement given for the asked bubblesort.
Step-by-step explanation:
Bubble sort Original list is [76, 51, 66, 38, 41, 18] Iteration: 1
> Swap 76 and 51, since they are not in correct order. Now, the list becomes [51, 76, 66, 38, 41, 18]
> Swap 76 and 66, since they are not in correct order. Now, the list becomes [51, 66, 76, 38, 41, 18]
> Swap 76 and 38, since they are not in correct order. Now, the list becomes [51, 66, 38, 76, 41, 18]
> Swap 76 and 41, since they are not in correct order. Now, the list becomes [51, 66, 38, 41, 76, 18]
> Swap 76 and 18, since they are not in correct order. Now, the list becomes [51, 66, 38, 41, 18, 76]
> 5 swaps happened in this iteration
> List after iteration 1 is [51, 66, 38, 41, 18, 76] Iteration: 2
> Swap 66 and 38, since they are not in correct order. Now, the list becomes [51, 38, 66, 41, 18, 76]
> Swap 66 and 41, since they are not in correct order. Now, the list becomes [51, 38, 41, 66, 18, 76]
> Swap 66 and 18, since they are not in correct order. Now, the list becomes [51, 38, 41, 18, 66, 76]
> 3 swaps happened in this iteration
> List after iteration 2 is [51, 38, 41, 18, 66, 76] Iteration: 3
> Swap 51 and 38, since they are not in correct order. Now, the list becomes [38, 51, 41, 18, 66, 76]
> Swap 51 and 41, since they are not in correct order. Now, the list becomes [38, 41, 51, 18, 66, 76]
> Swap 51 and 18, since they are not in correct order. Now, the list becomes [38, 41, 18, 51, 66, 76]
> 3 swaps happened in this iteration
> List after iteration 3 is [38, 41, 18, 51, 66, 76] Iteration: 4
> Swap 41 and 18, since they are not in correct order. Now, the list becomes [38, 18, 41, 51, 66, 76]
> 1 swaps happened in this iteration
> List after iteration 4 is [38, 18, 41, 51, 66, 76] Iteration: 5
> Swap 38 and 18, since they are not in correct order. Now, the list becomes [18, 38, 41, 51, 66, 76]
> 1 swaps happened in this iteration
> List after iteration 5 is [18, 38, 41, 51, 66, 76] Iteration: 6
> 0 swaps happened in this iteration
> List after iteration 6 is [18, 38, 41, 51, 66, 76] Sorted list is [18, 38, 41, 51, 66, 76] total number of comparisons made = 5+4+3+2+1 = 15
To learn more about Bubblesort, visit: https://brainly.com/question/29325734
#SPJ4
In Marvel Comics, what imaginary rare metal is an important natural resource of Wakanda, the home country of Black Panther?
Answers
Answer:
vinranium
Explanation:
i watched the movie
IM SO SMART!!!!!!!!!!!!! UWU
Exception Java gateway process exited before sending its port number error slowing you down?
Answers
Exception Java gateway process exited before sending its port number is an error that can slow you down when running a Java application. To solve this problem, check the Java code for any potential errors, ensure the Java application is up-to-date and restart the application.
Just one Java gateway may be configured per Zabbix server or Zabbix proxy since access to each Java gateway is explicitly configured in the Zabbix server or proxy configuration file. Only the JMX agent items will be sent to the Java gateway for retrieval if a host has both items of type JMX agent and items of other types. It is constructed on top of the Spring framework and offers a practical method for quickly configuring a Spring-based application. An element that stands between your backend services and your API clients is called an API gateway.
Learn more about proxy configuration: https://brainly.com/question/31077422
#SPJ11
Create two sample HTML pages that include a DOCTYPE statement and a title. Include at least one example of each of the following:
a standard paragraph of text
a left-justified headline (like a title)
a centered headline (like a title)
a sub headline (like a subtitle)
a section of colored text (not all text, just a segment or headline)
an image (from a URL)
an image (from a local source)
an image with a size adjustment (maintaining the aspect ratio)
hyperlinks
a hyperlinked image
a split line (empty element)
one page that has a background color
Extra Credit:
Include a sample of Italic text.
Include an email address link that does not spell out the address on the web page (HINT: mailto).
Create a hyperlink to a local page on your computer.
Answers
Answer:
<!DOCTYPE html>
<html>
<head>
<title>Hello</title>
</head>
<body style="background-color:pink;">
<h1 style="text-align:center">The Centered Headline</h1>
<h1 style="text-align:left">Left</h1>
<h2>Sub headline</h2>
<p>This is the paragraph.</p>
<h1 style="color:purple;">colored word</h1>
<img src="flower.jpeg" alt="Flower" width="460" height="345">
htmlimg2.jpeg
</body>
</html>
Explanation:
The algorithm below is used to find the largest element in a list of numbers.
By modifying one of the lines in the program it is possible to make the algorithm find the SMALLEST element. Which line would need to be modified and how?

Answers
The line that can be modified in the algorithm to return the smallest of the list is line 04
From the question, we understand that:
The algorithm returns the largest of all elements in a listThe above action is executed on line 04
To change the function of the algorithm to return the smallest, line 04 must be modified as follows:
IF (num < target)
Hence, the line that can be modified in the algorithm to return the smallest of the list is line 04
Read more about algorithms at:
https://brainly.com/question/24793921
3. What will be the output of the following Python code snippet? not(3>4) not(1 & 1) a) True True b) True False c) False True d) False False
Answers
Therefore, the output of the code snippet would be:
a) True True
The correct option is a) True True.
The output of the given Python code snippet can be determined as follows:
1. not(3 > 4):
The condition "3 > 4" evaluates to False. The not operator negates the result, so not(3 > 4) evaluates to True.
2. not(1 & 1):
The bitwise AND operation "1 & 1" evaluates to 1. The not operator negates the result, so not(1 & 1) evaluates to False.
Therefore, the output of the code snippet would be:
a) True True
The correct option is a) True True.
Learn more about Python:https://brainly.com/question/26497128
#SPJ11
What are a few ways to format the text in a mail message in Outlook? Check all that apply.
Attach a file to the message to be opened separately.
Open the Font dialog box to access more detailed options.
Increase or decrease the indent.
Copy and paste text from a Word document
Use the Mini Toolbar to change the font appearance.
Click the Format Painter to paste a saved font format.
Answers
Answer:
The answers are b,c,d,e,f
Explanation:
A small business utilizes a SOHO router and wishes to secure its existing wireless infrastructure. The business has fewer than ten devices, which are a mixture of old and new machines. Due to the varying ages of the machines, the latest wireless encryption methods may not be supported on all devices. Which of the following would be the MOST cost-effective method to add a layer of security while allowing all machines to connect?
A. MAC filtering
B. 802.1X
C. WPA2
D. EAP-FAST
Answers
Answer:
C
Explanation:
WPA2 builds on its predecessor, WPA, and is specifically designed to meet the most demanding enterprise security needs. ... Furthermore, because WPA2 is backwards- compatible with WPA, organizations that have already implemented the WPA standard can migrate to WPA2 at their own pace.
What is Multimedia Authoring Tools
Answers
Computer hardware without computer software is useless while computer software without computer hardware is meaningless. Discuss!
Answers
Answer:
I agree
Explanation:
Without ant software you'd have no use for a computer making it useless and a paper weight basically but a software without compute hardware is meaningless because it has no one to use it it becomes dead
a client has requested adjustments to the arrangement and placement of elements on an image. what does the client want changed?
Answers
Considering the situation described above, the client wants the image's recipe to be changed.
What is the Image Recipe?Image Recipes are characteristics of an image or picture. It includes features like shape, size, form, pattern, line, shadow, tone, color, contrast, positive space and negative space, etc.
Given that the client needs adjustments to the arrangement and placement of elements on an image, this is a request for a change in the image recipe.
Hence, in this case, it is concluded that the correct answer is "the client wants the recipe of the image changed."
Learn more about the Image Recipe here: https://brainly.com/question/1605430
How is life complicated without electronics
Answers
Answer:
life is complicated without electronics
Explanation:
because we wont know the weather or if anything know anything about and we would mostly not know anything
I am looking for code HS 3.4.5 in Technology
Answers
Answer (Code):
penup()
backward(100)
def bottom_line():
left(120)
color("red")
forward(100)
def triangle():
left(120)
color("blue")
forward(50)
left(120)
color("green")
forward(50)
pendown()
pensize(5)
color("red")
forward(50)
for i in range(4):
triangle()
bottom_line()
What is the typical educational requirement for a non-entry level software programmer? high school diploma technical certificate bachelor’s degree master’s degree
Answers
Answer: technical certificate
Explanation: i just took the test and i got it right
A bachelor's degree in computer science, information technology, or computer engineering is usually required for a career as a computer programmer. Option C is correct.
What education do you need to be a non-entry level software programmer?Computer programmers create computer programs by creating code in a variety of programming languages. They run new programs through their paces and look for flaws. A bachelor's degree is often required for computer programmers, however some firms may recruit programmers with an associate degree.
Individuals who want to work as computer programmers must have a degree in computer science, information technology, mathematics, or a related field.
A bachelor's degree in computer and information technology or a related discipline, such as mathematics, is often required for computer programmers. Some firms, however, hire people with different degrees or experience in specialized programming languages.
Therefore, option C is correct.
Learn more about the bachelor’s degree, refer to:
https://brainly.com/question/5709442
#SPJ2
what does good time management mean
Answers
Answer:
When you are consistent with your work and not wasting time
Explanation:
Have a good day and a merry Christmas
10. There is repeated code in these onevent blocks. Choose the correct code for the updateScreen() function which would be called in each of the onEvent blocks.
1
var counter
0;
2
3
onEvent("upButton", "click",
function
4
counter
counter + 1;
5
setText ("counter_label", counter);
set Property ("counter_label", "text-color",
6
"red");
7
if
counter
8
set Property ("counter label",
"font-size", 24);
9
10
11
onEvent ("downButton",
"click",
function
12
counter
counter
Answers
Answer:
front zise24
Explanation:
on event down botton
The correct code for the updateScreen() function which would be called in each of the onEvent blocks is setText ("counter_label" counter) = = 0.
What is a function?A function refers to a set of statements that makes up an executable code and it can be used in a software program to perform a specific task on a computer.
In this scenario, the correct code for the updateScreen() function is written as follows:
function updateScreen() { ⇒
setText ("counter_label" counter) {
if (counter == 0);
setProperty ("counter_label", "font-size", "24") ;
} +
}
In conclusion, the executable code for the updateScreen() function which would be called in each of the onEvent blocks is "setText ("counter_label" counter) = = 0."
Read more on function here: brainly.com/question/20264183
#SPJ2

Katie is a professional photographer. For a wedding season shoot, she chose an outdoor location to shoot her models wearing different kinds of
wedding gowns. She used natural lighting, and she kept the focus on the models with a blurry background. Which kind of focusing technique did
Katie use?
A- rack focus
B- silhouette focus
C- follow focus
D- selective focus
Answers
Answer:
D- selective focus
Explanation:
In photography the phrase 'selective focus' introduces a procedure where the photographer selectively concentrates on the subject of an illustration, basically neglecting all other characters of the scene. The contrast of the intense subject toward the delicate image background formulates powerful, meditative images.
Answer:
Selective focus
Explanation:
can direct the viewers' attention to a subjectt by focusing on the subject and burring the background
Recommend a minimum of 3 relevant tips for people using computers at home, work or school or on their SmartPhone. (or manufacturing related tools)
Answers
The three relevant tips for individuals using computers at home, work, school, or on their smartphones are ensure regular data backup, practice strong cybersecurity habits, and maintain good ergonomics.
1)Ensure Regular Data Backup: It is crucial to regularly back up important data to prevent loss in case of hardware failure, accidental deletion, or malware attacks.
Utilize external hard drives, cloud storage solutions, or backup software to create redundant copies of essential files.
Automated backup systems can simplify this process and provide peace of mind.
2)Practice Strong Cybersecurity Habits: Protecting personal information and devices from cyber threats is essential.
Use strong, unique passwords for each online account, enable two-factor authentication when available, and regularly update software and operating systems to patch security vulnerabilities.
Be cautious while clicking on email attachments, downloading files, or visiting suspicious websites.
Utilize reputable antivirus and anti-malware software to protect against potential threats.
3)Maintain Good Ergonomics: Spending extended periods in front of a computer or smartphone can strain the body.
Practice good ergonomics by ensuring proper posture, positioning the monitor at eye level, using an ergonomic keyboard and mouse, and taking regular breaks to stretch and rest your eyes.
Adjust chair height, desk setup, and screen brightness to reduce the risk of musculoskeletal problems and eye strain.
For more questions on computers
https://brainly.com/question/24540334
#SPJ8
problem 1: explain what this method is doing. to use it, create a new java project and write a main method, too. call mystery method from main at least two times with different parameters. public static boolean mystery(int first, int second) { boolean result
Answers
This is the code of your question. Copy and paste the code in java IDE or compiler and run it and name the file as "abc1.java"
Moreover, method Mystery() takes two argument first and second and check whether number 'first' contains digit 'second' or not means when we call method with:
public class abc{
public static boolean Mystery(int first,int second){
boolean result=false;
while(first>0){
if(first%10==second)
result=true;
first=first/10;
}
return result;
}
public static void main(String[] args) {
System.out.println(Mystery(252,2));
System.out.println(Mystery(322,5));
}
}
It will give output as:
True
False
Because when we call method with argument 252 and 2 then it will find remainder as 2 by dividing by 10 and check whether remainder 2 is equal to second argument or not if it equal then it will assign true in variable result. This process continue until first argument is greater than zero. It will true because number 252 contains digit 2.
Similarly it will do same thing with second call with argument 322 and 5 it will return false because number 322 does contains 5.
2) method zeroDigits takes one argument and count number of zero in a argument. when we run following code:
public class abc{
public static int zeroDigits(int number){
int count=0;
do{
if(number%10==0)
count++;
number=number/10;
}while(number>0);
return count;
}
public static void main(String[] args) {
System.out.println(zeroDigits(500));
System.out.println(zeroDigits(20));
}
}
It will give output as:
2
1
Because when we pass 500 as parameter then method counts the number of zeros bu finding remainder and check whether it is equal to 0 or not if it is equal then it increment variable count by 1. It will return 2 because 500 contains 2 zeros. Similarly, when we pass 20 as parameter then method returns 1 because 20 contains 1 zero.
This is the code of your question. Copy and paste the code in java IDE or compiler and run it and name the file as "abc.java" . I also provide the screenshot of output.
public class abc{
public static void main(String[] args) {
for(int i=1;i<=7;i++){
System.out.println(i+"+"+(i+1));
}
}
}
You can learn more about this at:
https://brainly.com/question/15710251#SPJ4
Joe, a user, wants his desktop RAID configured to allow the fastest speed and the most storage capacity. His desktop has three hard drives. Which of the following RAID types should a technician configure to achieve this?
A. 0
B. 1
C. 5
D. 10
Answers
For Joe, the technician has to set up RAID 0. By dividing data into many copies, RAID 0, also known as the striped volume or stripe set, is set up to provide the highest performance and greatest storage space.
How does a RAID function?
Data is duplicated across two drives in the array using RAID 1 (mirrored disks), which offers complete redundancy. The identical data is always stored on both drives at the same time. As long as one disk remains, no data is lost.
Why could someone utilize RAID?
Redundant Array of Independent Disks, or RAID, is a technology that combines many hard disks to increase performance. RAID configuration might affect how quickly your computer operates.
To know more about RAID visit:
https://brainly.com/question/14669307
#SPJ4
When data is anonymized, the PII is eliminated or encrypted. PII includes names, Social Security numbers, addresses, and more and stands for ______ identifiable information.a. powerb. personallyc. publiclyd. private
Answers
When data is anonymized, the PII is eliminated or encrypted. PII includes names, Social Security numbers, addresses, and more and stands for personally identifiable information. The answer is (b).
PII refers to any information that can be used to identify an individual. This includes both direct identifiers such as name, address, and Social Security number, as well as indirect identifiers such as IP address and location data. Anonymization is the process of removing or encrypting PII from data sets to protect individuals' privacy and prevent unauthorized access to sensitive information.
You can learn more about personall identifiable information at
https://brainly.com/question/30023988
#SPJ11
who knows how to cope and paste on (ape.x)
Answers
To copy and paste on Apex, you can use the keyboard shortcuts "Ctrl+C" and "Ctrl+V" or right-click the selected text and choose "Copy" and "Paste."
Without more information about the context and platform you are referring to, it is difficult to provide a helpful response. However, if you are asking how to copy and paste on a computer or mobile device, the process typically involves selecting the text or item you want to copy, pressing "Ctrl + C" on a PC or "Command + C" on a Mac, and then pasting it by pressing "Ctrl + V" or "Command + V". The specific steps may vary depending on the software or device you are using, so it is recommended to consult the instructions or help resources for that specific platform.
Copying and pasting are essential computer skills that allow you to duplicate text or other content from one place and insert it into another. In Apex, you can use these methods to copy and paste information, making it easier to complete tasks efficiently.
To know more about keyboard visit:
https://brainly.com/question/24921064
#SPJ11
please help
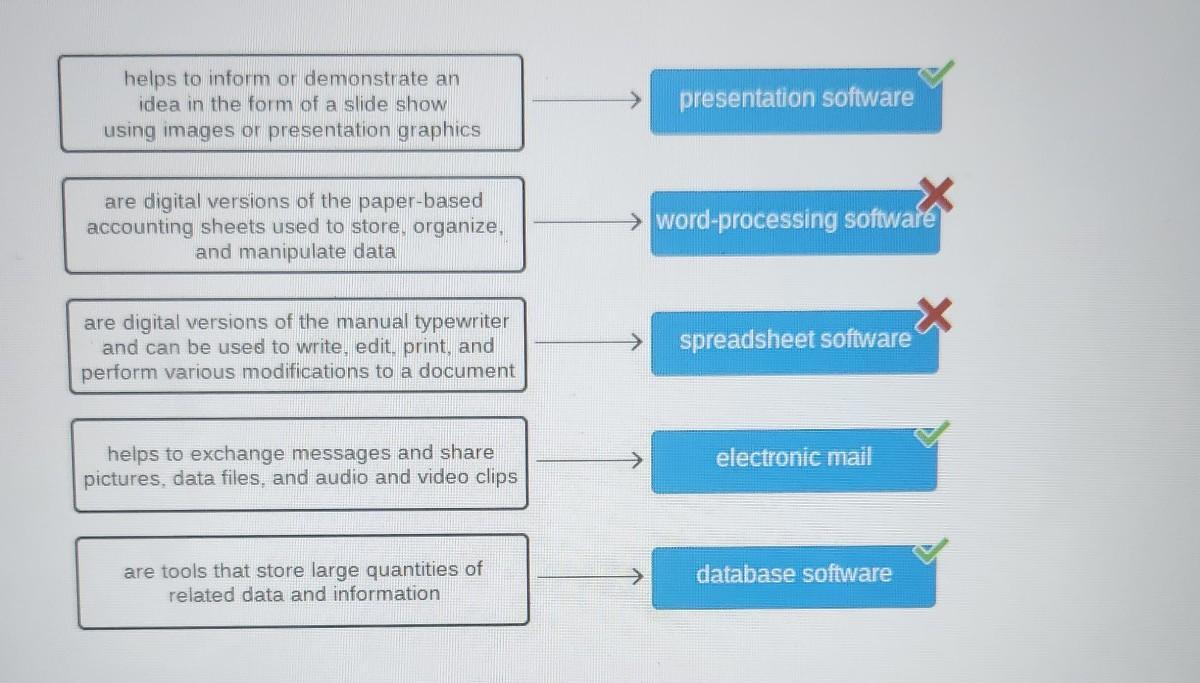
match the features with the software
Word Processor, Spreadsheet, Database
- addiction of images, drawings, tables and graphics to text
- centralized data management
- data security
- digital version accounting sheets
- supports multiple users for adding data simultaneously
- visual representation of data
- digital version of a typewriter
Answers
Answer:
word processor- addition of images, drawing tables, and graphics to texts and digital version of a typewriter. spreadsheet- digital version of accounting sheets and visual representation of data. database- centralized data management, data security, and supports multiple users for adding data simultaneously
Just switch the two I got wrong and you'll get the correct answers. :)
which feature offered by some database management systems masks confidential data within database fields so that it cannot be accessed by unauthorized users? a. lookup tables b. redaction c. blind fields d. tps
Answers
The feature offered by some database management systems that masks confidential data within database fields so that it cannot be accessed by unauthorized users is b. redaction.
The feature offered by some database management systems that masks confidential data within database fields so that it cannot be accessed by unauthorized users is known as redaction.
Redaction is a process that replaces sensitive or confidential data with asterisks or other symbols in order to keep it hidden from unauthorized access. This feature is often used in databases that store personal or financial information, such as credit card numbers, social security numbers, and medical records. While there are other techniques that can be used to secure data, such as encryption and access controls, redaction is a useful tool for protecting data from both internal and external threats. In summary, redaction is a long answer to the question of which feature offered by some database management systems masks confidential data within database fields.Know more about the database management systems
https://brainly.com/question/24027204
#SPJ11
Who was responsible for the development of the rocket motor?
-Technical Societies
-Robert H. Goddard
-Germans
-Wernher von Braun
I WILL MARK YOU BRAINLIEST ‼️‼️
Answers
Answer: Robert H. Goddard
Explanation: he developed and flew the first liquid-propellant rocket
Answer:
-Technical Societies
Explanation:
Rocket enthusiasts and rocket clubs were active in Germany, the US, Russia, and other countries. Experimental rockets were designed, tested, and sometimes flown. Some of the experiments used liquid fuel, though solid-fuel rockets were also developed. In 1932, the rocket motor was developed as a reusable method for the flight of a rocket.
PLZZZZ HELPPP and please don’t send a link , Explain how the processing stage contributes to a computer creating an output.
Answers
Sarah is having a hard time finding a template for her advertising buisness that she mah be able to use at a later date and also make it availible to her colleagues, What is her best option?
Answers
Answer: create a custom template
Explanation:
Since Sarah is having a hard time finding a template for her advertising business that she may be able to use at a later date and also make it available to her colleagues, her best option will be to create a custom template.
Creating a custom template will ensure that she makes the template based on her requirements and can tailor it specifically to her needs which then makes it unique.