Define network architecture?
short answer please
Answers
Network architecture refers to the approach network devices and services area unit structured to serve the property desires of shopper devices.
Network devices usually embrace switches and routers.Types of services embrace DHCP and DNS.Client devices comprise end-user devices, servers, and smart things.Networks additionally got to be dynamic, agile, and in lockstep with business desires. ancient, manually intensive strategies of managing pc networks area unit proving to be unsustainable. New approaches area unit necessary, ones that need transformational changes in however networks area unit architected.
This is what spec is all regarding. It’s however information flows expeditiously from one pc to a different. And for businesses with an internet element, it’s a vital idea that encompasses a vital impact on their operation
Learn more about Network Architecture at
https://brainly.com/question/13327017
Related Questions
Ms. Neese is writing a story and wants the title of each chapter to look the same
(font size, style, color, etc.). What feature will help her do this?
Save As
Table of Contents
Text Alignment
Styles
Answers
To make Word documents better, format the text. Find out how to alter the text's alignment, font size, font, and font color.
Which choice allows us to customize text formatting features such font size, color, and alignment?Right-click any style in the Styles gallery on the Home tab and select Modify. Change any formatting elements, such as font style, size, or color, alignment, line spacing, or indentation, that you desire in the formatting area. You can decide if the style change only affects the current document or all future ones.
How do I alter the HTML font size and color?Use the CSS font-size property to alter the font size in HTML. Put it within a style attribute and change the value to what you desire. Then Add this style attribute to a paragraph, heading, button, or span tag in an HTML element.
To know more about Text Alignment visit:-
https://brainly.com/question/29508830
#SPJ1
My best memory was the first time I ever saw a movie like Despicable Me with my father, which was at a movie theater.
Answers
Answer: That sounds really nice. I used to go see movies with my dad all the time too. One of my favorites was Monsters vs. Aliens
Explanation:
Which of the following is the best example of a purpose of e-mail?
rapidly create and track project schedules of employees in different locations
easily provide printed documents to multiple people in one location
quickly share information with multiple recipients in several locations
O privately communicate with select participants at a single, common location
Answers
Answer:
The best example of a purpose of email among the options provided is: quickly share information with multiple recipients in several locations.
While each option serves a specific purpose, the ability to quickly share information with multiple recipients in different locations is one of the primary and most commonly used functions of email. Email allows for efficient communication, ensuring that information can be disseminated to multiple individuals simultaneously, regardless of their physical location. It eliminates the need for physical copies or face-to-face interactions, making it an effective tool for communication across distances.
Explanation:
What kind of material is used for DRAM (dynamic random-access memory)?
Answers
The kind of material that is used for DRAM (dynamic random-access memory) is metal-oxide-semiconductor.
What is DRAM?DRAM was invented in 1968. It is a type of RAM used in modern computers and laptops. It is a type of random access memory. Its name is dynamic random access memory.
Metal-oxide-semiconductor is used in making the transistors and capacitors of the DRAM, which are used to store the data. They hold a bit of the data in these capacitors and transistors.
Thus, the material that is used is metal-oxide-semiconductor to make DRAM (dynamic random-access memory).
To learn more about DRAM, refer to the link:
https://brainly.com/question/20216206
#SPJ1
the left column below gives a proof that the product of two odd integers is odd. match the steps of the proof on the left with the justifications for those steps on the right. 1. let a and b be any two odd integers. (we wish to show that ab is also an odd integer.) 1. let a and b be any two odd integers. (we wish to show that ab is also an odd integer.) drop zone empty. 2. there are two integers m and n such that a
Answers
An odd integer can be expressed in the form 2m + 1 for some integer m according to the definition of an odd integer. We must demonstrate that ab may be expressed in the form 2k + 1 for some integer k
How can the oddness of the product of two odd numbers be established?An odd number is the result of two odd numbers. Let the integers m and k vary. As a result, the numbers 2m+1 and 2k+1 are odd. An odd number, 2 (2mk + m + k) + 1, is obtained.
For two integers m and n, a = 2m + 1 and b = 2n + 1, respectively. (According to what an odd integer is)
4mn + 2m + 2n + 1 is equal to ab = (2m + 1)(2n + 1). (Product expansion)
ab equals (2mn + m + n) + 1. (Factoring out a 2)
Ab is an odd integer since 2mn + m + n is an integer. (According to what an odd integer is)
To know more about integer visit:-
https://brainly.com/question/15276410
#SPJ1
To help insure that an HTML document renders well in many web browsers it is important to included which at top of file
Answers
Answer:
<!DOCTYPE html>
Explanation:
This tells the browseer that the code is HTML5 format
How often do you trade cowoncy? If so, for what and how much?
Answers
There are different ways to trade cowoncy. There are some legitimate site to buy and sell it. In trade cowoncy, about 100000 Cowoncy is bought for $17.89USD.
Cowoncy is commonly described as the OwO bot's form of currency. It is known as a currency used worldwide in hunting.
Its role is mainly for for hunting and in the activation of one's huntbot and it is often used in other form of purchases such as cosmetics, etc.
Learn more about trade from
https://brainly.com/question/17727564
What does influence mean in this passage i-Ready
Answers
In the context of i-Ready, "influence" refers to the impact or effect that a particular factor or element has on something else. It suggests that the factor or element has the ability to shape or change the outcome or behavior of a given situation or entity.
In the i-Ready program, the term "influence" could be used to describe how various components or aspects of the program affect students' learning outcomes.
For example, the curriculum, instructional methods, and assessments implemented in i-Ready may have an influence on students' academic performance and growth.
The program's adaptive nature, tailored to individual student needs, may influence their progress by providing appropriate challenges and support.
Furthermore, i-Ready may aim to have an influence on teachers' instructional practices by providing data and insights into students' strengths and areas for improvement.
This can help educators make informed decisions and adjust their teaching strategies to better meet their students' needs.
In summary, in the context of i-Ready, "influence" refers to the effect or impact that different elements of the program have on students' learning outcomes and teachers' instructional practices. It signifies the power of these components to shape and mold the educational experiences and achievements of students.
For more such questions element,Click on
https://brainly.com/question/28565733
#SPJ8
Please rewrite and correct the following sentences:
1. Their dog ran away last night, and now their looking for him.
2. The company lost there biggest client last year.
3. Who is you going to the party with tonight?
4. The museums is open on Saturdays from 10am to 5pm.
5. Neither the boys or their father have any idea where the car keys is.
Answers
1.Their dog ran away last night, and now they are looking for him.
2. Their company lost their biggest client last year.
3. With whom you are going to the party with tonight?
4. The museums are open on saturdays from 10 am to pm.
5. Fathers or Boys no one knows where the car keys are?
Thus, English has three tenses: past, present, and future. When writing about the past, we employ the past tense.
When writing about facts, opinions, or regular occurrences, we employ the present tense. To write about upcoming events, we utilize the future tense. Each of those tenses has additional characteristics, but we won't cover them in this session.
It's crucial to maintain the same tense throughout a writing endeavor after you've decided on one. To communicate yourself clearly, you may need to switch up the tense from time to time.
Thus, English has three tenses: past, present, and future. When writing about the past, we employ the past tense.
Learn more about Tenses, refer to the link:
https://brainly.com/question/29757932
#SPJ1
An internet download speed is 4.2 MB/S (constant). How long will it take to download a 30 GB file?
And with 900 KB/S?
Answers
Answer:
(a) \(Time= 119.05 \ min\)
(b) \(Time= 9.26\ hr\)
Explanation:
Given
\(File = 30GB\)
Required
Download time
Solving (a): When Speed =4.2Mb/s
Speed is calculated as:
\(Speed = \frac{File\ Size}{Time}\)
Make Time the subject:
\(Time= \frac{File\ Size}{Speed }\)
Substitute values for File Size and Speed
\(Time= \frac{30Gb}{4.2Mb/s}\)
Convert Gb to Mb
\(Time= \frac{30*1000Mb}{4.2Mb/s}\)
\(Time= \frac{30000s}{4.2}\)
Convert to minutes
\(Time= \frac{30000}{4.2*60}\ min\)
\(Time= \frac{30000}{252}\ min\)
\(Time= 119.05 \ min\)
When converted, it is approximately 2 hours
Solving (a): When Speed =900Kb/s
\(Time= \frac{File\ Size}{Speed }\)
Substitute values for File Size and Speed
\(Time= \frac{30Gb}{900Kb/s}\)
Convert Gb to Kb
\(Time= \frac{30*1000000Kb}{900Kb/s}\)
\(Time= \frac{30*1000000s}{900}\)
\(Time= \frac{1000000s}{30}\)
\(Time= \frac{100000}{3}s\)
Convert to hours
\(Time= \frac{100000}{3*3600}hr\)
\(Time= \frac{1000}{3*36}hr\)
\(Time= \frac{1000}{108}hr\)
\(Time= 9.26\ hr\)
Answer:
(a)
(b)
Explanation:
Given
Required
Download time
Solving (a): When Speed =4.2Mb/s
Speed is calculated as:
Make Time the subject:
Substitute values for File Size and Speed
Convert Gb to Mb
Convert to minutes
When converted, it is approximately 2 hours
Solving (a): When Speed =900Kb/s
Substitute values for File Size and Speed
Convert Gb to Kb
Convert to hours
How to protect data in transit Vs rest?
Answers
Implement robust network security controls to help protect data in transit. Network security solutions like firewalls and network access control will help secure the networks used to transmit data against malware attacks or intrusions.
If this helps Brainliest please :)
To specify your preferred colors, fonts, and effects for a document, which of the following should be done?
1.Create custom theme fonts
2.Create custom theme
3.Create a custom paragraph style
4.Create a custom character style
Answers
Answer:
2. Create custom theme.
Explanation:
The theme stays through the entire document. Custom paragraph style only changes the theme for that paragraph, and for the custom character style, it only changes the style of that character but throughout the entire document. i.e. I want the color of the character E to be green. the custom character style will cover that. Also, the custom theme fonts will only change the theme for that certain font...
To specify your preferred colors, fonts, as well as effects for documentation, will have to create a custom theme.
A customized theme seems to be the simplest method to give your existing applications a unique aesthetic appeal or appearance. Themes represent bundles of overall coding or website that have previously been written for customers.The templates subdirectory could hold many customization options or the themes, preferably with its respective or individual sub-folder.
Thus the response above i.e., option 2. is appropriate.
Learn more about Custom themes here:
https://brainly.com/question/20006021
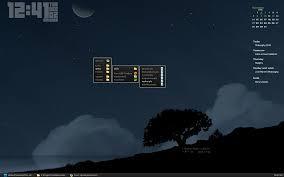
How many passes will it take to find the 20 in this list? (python)
10, 12, 14, 16, 18, 19, 20
3
1
2
4
Answers
Answer:
1
Explanation:
What do you mean by a pass? A pass through each number in the list?
for x in numLst:
if x == 20:
return True
This would run through the list once, as you're just checking if each element is 20 in this loop.
Answer:
2
Explanation:
on edge right
Robyn needs to ensure that a command she frequently uses is added to the Quick Access toolbar. This command is not found in the available options under the More button for the Quick Access toolbar. What should Robyn do?
Access Outlook options in Backstage view.
Access Outlook options from the Home tab.
Access Quick Access commands using the More button.
This cannot be done.
Answers
let m be a positive integer with n bit binary representation an-1 an-2 ... a1a0 with an-1=1 what are the smallest and largest values that m could have
Answers
Answer:
Explanation:
From the given information:
\(a_{n-1} , a_{n-2}...a_o\) in binary is:
\(a_{n-1}\times 2^{n-1} + a_{n-2}}\times 2^{n-2}+ ...+a_o\)
So, the largest number posses all \(a_{n-1} , a_{n-2}...a_o\) nonzero, however, the smallest number has \(a_{n-2} , a_{n-3}...a_o\) all zero.
∴
The largest = 11111. . .1 in n times and the smallest = 1000. . .0 in n -1 times
i.e.
\((11111111...1)_2 = ( 1 \times 2^{n-1} + 1\times 2^{n-2} + ... + 1 )_{10}\)
\(= \dfrac{1(2^n-1)}{2-1}\)
\(\mathbf{=2^n -1}\)
\((1000...0)_2 = (1 \times 2^{n-1} + 0 \times 2^{n-2} + 0 \times 2^{n-3} + ... + 0)_{10}\)
\(\mathbf {= 2 ^{n-1}}\)
Hence, the smallest value is \(\mathbf{2^{n-1}}\) and the largest value is \(\mathbf{2^{n}-1}\)
write principles of information technology
Answers
Here are some principles of information technology:
Data is a valuable resourceSecurity and privacyOther principles of information technologyData is a valuable resource: In information technology, data is considered a valuable resource that must be collected, stored, processed, and analyzed effectively to generate useful insights and support decision-making.
Security and privacy: Ensuring the security and privacy of data is essential in information technology. This includes protecting data from unauthorized access, theft, and manipulation.
Efficiency: Information technology is all about making processes more efficient. This includes automating tasks, reducing redundancy, and minimizing errors.
Interoperability: The ability for different systems to communicate and work together is essential in information technology. Interoperability ensures that data can be shared and used effectively between different systems.
Usability: Information technology systems should be designed with usability in mind. This means that they should be intuitive, easy to use, and accessible to all users.
Scalability: Information technology systems must be able to grow and expand to meet the changing needs of an organization. This includes the ability to handle larger amounts of data, more users, and increased functionality.
Innovation: Information technology is constantly evolving, and new technologies and solutions are emerging all the time. Keeping up with these changes and being open to innovation is essential in information technology.
Sustainability: Information technology has an impact on the environment, and sustainability must be considered when designing and implementing IT systems. This includes reducing energy consumption, minimizing waste, and using environmentally friendly materials.
Learn more about information technology at
https://brainly.com/question/4903788
#SPJ!
help
Which applications are considered to be word processing software?
A) Docs and Acrobat
B) Excel and Sheets
C) Access and OpenOffice Base
D) Keynote and Prezi
Answers
Changing the color of the text in your document is an example of
Answers
Answer:
???????????uhhh text change..?
Explanation:
Answer:
being creative
Explanation:
cause y not?
8. What is the order of growth execution time of the push operation when using the LinkedStack class, assuming a stack size of N?
Answers
The order of growth execution time of the push operation when using the LinkedStack class, assuming a stack size of N is; O(1)
Understanding Computer Programming LanguageLet Top be the position of last element inserted in Array.
For Push operation, the process is as follows;
if(Top == last index of Array) {
Printf(“Stack Overflow”)
} else {
Top = Top + 1
a[Top] = element you want to insert
}
Read more about Computer Programming at; https://brainly.com/question/22654163
Each slide in a presentation has a layout that includes placeholders for certain types of content?
True
False
Answers
Answer:
True
Explaination:
It has layouts that includes placeholders for images, text and lot more
Each slide in a presentation contains a layout that includes placeholders for certain types of content: True.
What is a slide?A slide simply refers to a single page of a presentation that comprises text-based information or images, which can be used to teach, instruct and educate the audience on a subject matter, topic, event or idea.
In Computer technology, each slide in a presentation contains a layout that includes placeholders for certain types of content such as:
ImagesTextsVideoRead more on slides here: https://brainly.com/question/26187618
#SPJ2
What would game programmers do when decomposing a task in a modular program?
Answers
1. Identify the overall task or feature: Game programmers start by identifying the larger task or feature they want to implement, such as player movement, enemy AI, or collision detection.
2. Analyze the task: They analyze the task to understand its requirements, inputs, and desired outputs. This helps them determine the necessary functionality and behavior.
3. Identify subtasks or components: They identify the subtasks or components that make up the larger task. For example, in the case of player movement, this could involve input handling, character animation, physics simulation, and rendering.
4. Break down the subtasks further: Each subtask can be further decomposed into smaller, more specific functions or modules. For example, input handling might involve separate functions for keyboard input, mouse input, or touch input.
5. Define interfaces: They define clear interfaces between the modules, specifying how they interact and communicate with each other. This helps ensure modularity and maintainability of the code.
6. Implement and test modules: Game programmers then proceed to implement each module or function, focusing on their specific responsibilities. They can test and iterate on these smaller units of functionality independently.
7. Integrate and test the modules: Finally, they integrate the modules together, ensuring they work harmoniously and produce the desired outcome. Thorough testing is conducted to verify that the overall task or feature functions correctly.
By decomposing tasks in this manner, game programmers can effectively manage the complexity of game development, promote code reusability, enhance collaboration, and facilitate the maintenance and future expansion of the game.
When decomposing a task in a modular program, game programmers follow a structured approach to break down the task into smaller, more manageable components.
This process is crucial for code organization, maintainability, and reusability. Here's an outline of what game programmers typically do:
1. Identify the task: The programmer begins by understanding the task at hand, whether it's implementing a specific game feature, optimizing performance, or fixing a bug.
2. Break it down: The task is broken down into smaller subtasks or functions that can be handled independently. Each subtask focuses on a specific aspect of the overall goal.
3. Determine dependencies: The programmer analyzes the dependencies between different subtasks and identifies any order or logical flow required.
4. Design modules: Modules are created for each subtask, encapsulating related code and functionality. These modules should have well-defined interfaces and be independent of each other to ensure reusability.
5. Implement and test: The programmer then implements the modules by writing the necessary code and tests their functionality to ensure they work correctly.
6. Integrate modules: Once individual modules are tested and verified, they are integrated into the larger game program, ensuring that they work together seamlessly.
By decomposing tasks into modules, game programmers promote code organization, readability, and ease of maintenance. It also enables parallel development by allowing different team members to work on separate modules simultaneously, fostering efficient collaboration.
For more such questions on programmers,click on
https://brainly.com/question/30130277
#SPJ8
List at least three kinds of harm a company could experience from electronic espionage or unauthorized viewing of confidential company materials.
Answers
The three kinds of harm a company could experience from electronic espionage or unauthorized viewing of confidential company materials are:
Embarrassment and also the loss of customers as a result of data loss.The loss of what we call a proprietary information.The loss of what we call the sensitive business strategy information (such as planned acquisitions, and other.).What is E-espionage?This term e-Espionage is known to be a form of an unauthorized and it is often seen as a criminal access to a lot of confidential systems and information and it is one whose purpose is that they have or gain a lot of commercial or political advantage.
Hence, the types of espionage are:
Clandestine cell system.Counterintelligence, etc.Therefore, The three kinds of harm a company could experience from electronic espionage or unauthorized viewing of confidential company materials are:
Embarrassment and also the loss of customers as a result of data loss.The loss of what we call a proprietary information.The loss of what we call the sensitive business strategy information (such as planned acquisitions, and other.).Learn more about electronic espionage from
https://brainly.com/question/312313
#SPJ1
You are a systems analyst. Many a time have you heard friends and colleagues complaining that their jobs and businesses are being negatively impacted by e-commerce. As a systems analyst, you decide to research whether this is true or not. Examine the impact of e-commerce on trade and employment/unemployment, and present your findings as a research essay.
Answers
E-commerce, the online buying and selling of goods and services, has significantly impacted trade, employment, and unemployment. This research essay provides a comprehensive analysis of its effects.
What happens with e-commerceContrary to popular belief, e-commerce has led to the growth and expansion of trade by breaking down geographical barriers and providing access to global markets for businesses, particularly SMEs. It has also created job opportunities in areas such as operations, logistics, customer service, web development, and digital marketing.
While certain sectors have experienced disruption, traditional businesses can adapt and benefit from e-commerce by adopting omni-channel strategies. The retail industry, in particular, has undergone significant transformation. E-commerce has empowered small businesses, allowing them to compete with larger enterprises and fostered entrepreneurial growth and innovation. However, there have been job displacements in some areas, necessitating individuals to transition and acquire new skills.
Read mroe on e-commerce here https://brainly.com/question/29115983
#SPJ1
In which country is edx located in
Answers
Answer:
Explanation:
edX es una plataforma de cursos abiertos masivos en línea, conocidos por sus siglas en inglés como MOOC (Massive Online Open Course), basada en software de código abierto. Fue fundada por el Instituto Tecnológico de Massachusetts y la Universidad de Harvard en mayo de 2012 para hospedar cursos en línea de nivel universitario de un amplio rango de disciplinas, para todo el mundo sin costos para propiciar la investigación y el aprendizaje.3 Cada una de estas dos instituciones contribuyen con 30 millones de dólares de recursos para este proyecto sin ánimo de lucro. El curso prototipo con el cuál empezó el programa fue Circuitos y Electrónica, que comenzó en diciembre de 2011, a través de MITx, el programa en línea y masivo del MIT.4
EdX tiene más de 10 millones de usuarios registrados y es considerado el segundo proveedor más grande de MOOC en el mundo, después de Coursera que cuenta con 23 millones de usuarios registrados.5
A finales de 2016, edX ofrecía 1300 cursos de los cuales 500 fueron lanzados en 2016. Del total de cursos que ofrece, 53 son pagados, conocidos como cursos de educación profesional, y 13 son elegibles para créditos universitarios. De acuerdo a una investigación realizada por Class Central, el costo promedio de un certificado de edX es de USD$53.6
Actualmente hay más de 130 colaboradores entre institutos, organizaciones sin ánimo de lucro, corporaciones y organizaciones internacionales que ofrecen o planean ofrecer más de 500 cursos en el sitio web de edX.7
problem description IT
Answers
In IT, a problem description refers to a clear and concise explanation of an issue or challenge that needs to be resolved within a technology system or application.
How is this so?It involves providing relevant details about the symptoms, impact, and context of the problem.
A well-written problem description outlines the specific errors, failures, or undesired behavior observed and provides enough information for IT professionals to analyze and identify potential solutions.
A comprehensive problem description is crucial for effective troubleshooting and problem-solving in the IT field.
Learn more about Problem Description at:
https://brainly.com/question/25923602
#SPJ1
Windows hard disks can now use a variety of file systems, including FAT16, FAT32, ____, and Resilient File System.
Answers
Answer:
NTFS.
Explanation:
how to view a pivate acont on Intagam
Answers
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
Which tool, first introduced in Windows Server 2008 but remains in Windows Server 2019, provides one location to set up, deploy, and manage servers and server roles
Answers
Answer:
Server Manager
Explanation:
An operating system is a system software pre-installed on a computing device to manage or control software application, computer hardware and user processes.
This ultimately implies that, an operating system acts as an interface or intermediary between the computer end user and the hardware portion of the computer system (computer hardware) in the processing and execution of instructions.
Some examples of an operating system on computers are QNX, Linux, OpenVMS, MacOS, Microsoft windows, IBM, Solaris, VM, Windows Server 2008, Windows Server 2009, etc.
Windows Server 2008 is a Microsoft Windows Server operating system and released to the general public on the 27th of February, 2008, as part of the Windows NT family.
Server Manager is a tool that was first introduced in Windows Server 2008 (OS) but remains in Windows Server 2019 (OS). It was designed and developed by Microsoft to provide end users with one location to set up, deploy, and manage servers and server roles.
On the 14th of January, 2020, Microsoft stopped providing online technical content update, free support options, non-security and free security updates on-premises for Windows Server 2008 and Windows Server 2008 R2, as they have reached the end of their support lifecycle.
what hand glove is used to prevent electric shock and why
Answers
Answer:
Insulated gloves because their made of synthetic rubber.
Explanation: