Comprehensively discuss with examples how robotics and learning systems can be used in improving patients service in a hospital
Answers
The integration of robotics and learning systems in hospitals can enhance patient services by automating tasks, improving accuracy and precision during surgeries, and providing personalized care.
Robotics and learning systems can play a crucial role in improving patient services in hospitals. For instance, robotics can be used to automate mundane tasks such as cleaning, sanitization, and restocking, which can free up healthcare professionals to focus on more critical tasks. For example, the Xenex robot uses ultraviolet light to kill germs and pathogens, which is critical in reducing the spread of infections in hospitals.
Furthermore, robotics can be used to aid surgeries and other medical procedures, making them less invasive and more precise. For instance, the da Vinci Surgical System can perform complex surgeries with a high degree of accuracy, reducing patient recovery time and increasing success rates.
Learning systems, on the other hand, can be used to improve patient outcomes by analyzing patient data to provide personalized care. For example, the IBM Watson system can analyze patient data and suggest treatment options based on previous successful treatments and patient history.
To learn more about Robotics :
https://brainly.com/question/31351016
#SPJ11
Related Questions
3. What is an example of a Digital Age Invention?
Answers
What is the problem with my python code?

Answers
import math
class TripleAndHalve:
def __init__(self, number):
self.__number = number
def triple(self):
return self.__number * 3
def halve(self):
return self.__number / 2
def print_number(self):
return self.__number
t1 = TripleAndHalve(4)
print(t1.triple())
print(t1.halve())
print(t1.print_number())
Question 16 2.5 pts When is it OK to use the less-precise "fast_normalize()" call instead of the full-precision "normalize()" call? Always Never When using it for scientific computing O When using it for computer graphics
Answers
It is not appropriate to use the less-precise "fast_ normalize()" call instead of the full-precision "normalize()" call in any scenario. The purpose of the "normalize()" function is to ensure accurate and precise normalization of data, which is essential in various fields such as scientific computing and computer graphics.
The "normalize()" function typically calculates the precise normalization of a given set of data, which involves dividing each data point by the magnitude or sum of all data points. This process ensures that the resulting normalized values maintain their original proportions and accurately represent the data.
On the other hand, the "fast_normalize()" function suggests a less-precise or approximate normalization approach. While it may provide faster computation, it sacrifices accuracy and reliability, which are crucial in many applications.
In scientific computing, accurate results are of utmost importance. Researchers and scientists rely on precise calculations to obtain reliable outcomes and draw meaningful conclusions. Using a less-precise normalization method can introduce errors and inaccuracies in the data, leading to flawed analyses and potentially misleading results.
Similarly, in computer graphics, maintaining precision is vital for generating realistic and visually appealing graphics. Any compromise on accuracy can result in distorted images or incorrect rendering, compromising the quality of the graphics.
Therefore, it is never acceptable to use the less-precise "fast_ normalize()" call instead of the full-precision "normalize()" call. It is essential to prioritize accuracy and reliability in scientific computing, computer graphics, and any other field where precise normalization is required.
for more questions on computer
https://brainly.com/question/24540334
#SPJ8
Top/Bottom Rules allow a user to apply conditional formatting to cells that fall within the top or bottom numbers or percentile. How many items will it allow the user to include in the rule?
the top or bottom 10 items or top or bottom 10% only
the top 10 items and top 10% only
the top or bottom 100 items only
any logical number of items or percentages in top or bottom value frames
Answers
The numbers of items that the user can include in the rule is the top or bottom 100 items only.
What is Top/Bottom Rules?Top/Bottom Rules is known to be a rule where there is a premade form of conditional formatting which is often used in Excel to alter the set up of cells in a range.
Note that the Top/Bottom Rules will allow a user to make changes to the top or bottom 100 items only as it only pertains to things that are up and those that are at the bottom.
Learn more about Top/Bottom Rules from
https://brainly.com/question/1862654
which blocks of code will properly navigate the robot to the final destination of the grey square in the bottom right corner of the grid without making it run into the wall or a black square?
Answers
The robot will correctly move to the gray square in Grid I even though the program won't move it to the gray square in Grid II.
What are the main parts of a robot?A robot's body/frame, control system, manipulators, and drivetrain are its constituent parts. The body or the frame may be any size and shape. In essence, the body/frame serves as the robot's framework.For years 1 through 5, the number of registered users almost quadrupled each year, and then it grew at a roughly consistent rate after that.The Action Your robot may move forward, backward, turn, or stop by using the steering block.The components of the robot that carry out the work are called effectors. Any tool that you can mount on your robot and operate with its computer is an effector. The effectors are typically tailored to the jobs that you want your robot to perform.To learn more about parts of a robot refer to:
https://brainly.com/question/19584695
#SPJ4
What is a hole note in word form
Answers
Answer:
4 beats
Explanation:
Explain three major concerns in database systems.
Answers
Answer:
Slow Read-Write Speeds. Performance slowdowns can occur due to high latency for disk read/writes. ...Scaling Problems. ...Incorrect Virtual Machine Setup. ...Lack of Backup and Monitoring. ...Query Performance. ...User and Query Conflicts. ...Configuration. ...Capacity.
Which of the following are commonly used examples that implement symmetric key encryption?Select one or more:a. Blowfishb. Pretty Good Privacyc. Data Encryption Standard or DESd. Secure Socket Layer (SSL)e. Digital signatures
Answers
The commonly used examples that implement symmetric key encryption are: a. Blowfishc.
Data Encryption Standard or DESd. Secure Socket Layer (SSL)Symmetric key encryption algorithms, such as Blowfish and DES, use the same key for both encryption and decryption. SSL is a protocol that utilizes symmetric key encryption for secure communication over the internet. Digital signatures, on the other hand, are used for authentication and integrity verification, but they do not directly implement symmetric key encryption. Pretty Good Privacy (PGP) is an example of an asymmetric encryption system.
learn more about implement symmetric here:
https://brainly.com/question/32272338
#SPJ11
When developing an output control system, it is important to implement output standards that: (Choose all that apply.)
Answers
When creating an output control system, it is important to implement output standards or targets that managers think will have good measure efficiency, quality, etc.
What is this system about?In an output control system, it is important for managers to first make sure that they set of goals or output performance standards or targets that they believe will best measure in terms of efficiency, quality, etc., for their firm.
Note that this system often acts as a behavior control systems that helps in providing methods that can be used to ensure that workers do well in ways that make the work to be efficient.
Learn more about control system from
https://brainly.com/question/27334060
about how many smart devices are active today coinbase
Answers
Considering the latest information released by Statisticà, the number of active smart devices in the world today is 21.5 billion.
What is Smart Device?Smart Device are generally known as electronic devices, that have the capacity to connect with other device or networks through wireless servers like Bluetooth, Zigbée, NFC, Wi-Fi, LiFi, 5G, etc.
Examples of Smart DevicesSmart devices generally include the following:
SmartphonesSmart cars Smart doorbellsSmart refrigeratorsTabletsPCSmart watches, etc.Hence, in this case, it is concluded that the correct answer is 21.5 billion.
Learn more about Smart Device here: https://brainly.com/question/24803254
how should a security analyst review system generated events for signs of intrusion or other problems on the network?
Answers
A software program called an intrusion detection system (IDS) automates the intrusion detection procedure. Software that combines all the features of an intrusion detection system with the ability to try to thwart potential events is known as an intrusion prevention system (IPS).
What security analyst review system generated events?Through the client-side injection of malicious scripts, XSS vulnerabilities give attackers the ability to manipulate user interactions with web applications, plan impersonations, and/or launch phishing campaigns.
Therefore, A network intrusion detection system (NIDS) is installed at one or more strategic locations so that it can keep track of all incoming and outgoing traffic between all networked devices.
Learn more about security here:
https://brainly.com/question/16354463
#SPJ1
please help me i will award brainliest
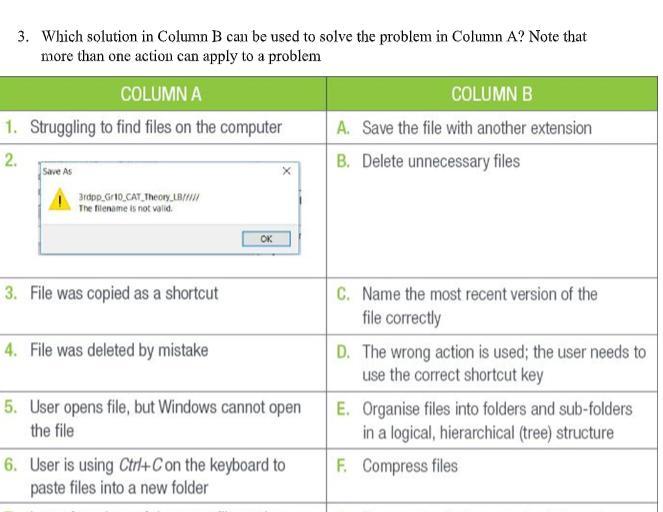

Answers
Answer: It would be option C.
Explanation: The file name is invalid, so therefore it would make sense to rename the most recent version correctly.
Which option lists the computer components in order from oldest to newest?.
Answers
Answer:
Transistors, vacuum tubes, integrated circuits, personal computers, microprocessors.
Explanation:
These are the computer components in order from oldest to newest
The correct option is B. Transistors, vacuum tubes, integrated circuits, personal computers, and microprocessors which is an option that lists the computer components in order from oldest to newest.
Why are components are important for a computer?
The central processing unit (CPU), often known as a microprocessor, serves as the "brain" of your computer and is the most crucial of these parts. Random access memory (RAM) is an additional component that serves as a short-term data storage for the CPU while the machine is running.
Vacuum tubes are used in vacuum tube computers, often known as first-generation computers, to power their logic circuitry. Although second-generation transistorized computers took their place, vacuum-tube computers were still produced throughout the 1960s. Most of these computers had unique designs.
Thus, the ideal selection is B.
Learn more about computer components here:
https://brainly.com/question/14680998
#SJ2
Your Question seems to be incomplete, Most probably your full Question was:
Which option lists the computer components in order from oldest to newest?
Choose correct answer/s
A
integrated circuits, microprocessors, vacuum tubes, transistors, personal computers
B
transistors, vacuum tubes, integrated circuits, personal computers, microprocessors
C
vacuum tubes, transistors, integrated circuits, microprocessors, personal computers
D
microprocessors, vacuum tubes, transistors, personal computers, integrated circuits
add an if branch to complete double_pennies()'s base case. sample output with inputs: 1 10 number of pennies after 10 days: 1024
Answers
The given function is incomplete and needs to be modified to get the correct output. The function name is `double_pennies()` and it is missing an if-else statement.
It takes in two arguments, `num_of_pennies` and `num_of_days`.The function doubles the number of pennies every day and returns the total number of pennies at the end of the given days.
The base case of the function has to be added to get the correct output for lower values of days, so the function looks like this:```def double_pennies(num_of_pennies, num_of_days):
if num_of_days == 0:
return num_of_pennies else:
return double_pennies(num_of_pennies * 2, num_of_days - 1)``
The above code will return the correct output for the given input of 1 and 10 which is:```number of pennies after 10 days: 1024```
To know more about statement visit:-
https://brainly.com/question/31655355
#SPJ11
You have been managing a $5 million portfolio that has a beta of 1.45 and a required rate of return of 10.975%. The current risk-free rate is 3%. Assume that you receive another $500,000. If you invest the money in a stock with a beta of 1.75, what will be the required return on your $5.5 million portfolio? Do not round intermediate calculations.
Round your answer to two decimal places.
%
Answers
The required return on the $5.5 million portfolio would be 12.18%.
1. To calculate the required return on the $5.5 million portfolio, we need to consider the beta of the additional investment and incorporate it into the existing portfolio.
2. The beta of a stock measures its sensitivity to market movements. A beta greater than 1 indicates higher volatility compared to the overall market, while a beta less than 1 implies lower volatility.
Given that the initial portfolio has a beta of 1.45 and a required rate of return of 10.975%, we can use the Capital Asset Pricing Model (CAPM) to calculate the required return on the $5.5 million portfolio. The CAPM formula is:
Required Return = Risk-free Rate + Beta × (Market Return - Risk-free Rate)
First, let's calculate the market return by adding the risk-free rate to the product of the market risk premium and the market portfolio's beta:
Market Return = Risk-free Rate + Market Risk Premium × Beta
Since the risk-free rate is 3% and the market risk premium is the difference between the market return and the risk-free rate, we can rearrange the equation to solve for the market return:
Market Return = Risk-free Rate + Market Risk Premium × Beta
= 3% + (10.975% - 3%) × 1.45
= 3% + 7.975% × 1.45
= 3% + 11.56175%
= 14.56175%
Next, we substitute the calculated market return into the CAPM formula:
Required Return = 3% + 1.75 × (14.56175% - 3%)
= 3% + 1.75 × 11.56175%
= 3% + 20.229%
= 23.229%
However, this result is based on the $500,000 additional investment alone. To find the required return on the $5.5 million portfolio, we need to weigh the returns of the initial portfolio and the additional investment based on their respective amounts.
3. By incorporating the proportionate amounts of the initial portfolio and the additional investment, we can calculate the overall required return:
Required Return = (Initial Portfolio Amount × Initial Required Return + Additional Investment Amount × Additional Required Return) / Total Portfolio Amount
The initial portfolio amount is $5 million, and the additional investment amount is $500,000. The initial required return is 10.975%, and the additional required return is 23.229%. Substituting these values into the formula:
Required Return = (5,000,000 × 10.975% + 500,000 × 23.229%) / 5,500,000
= (548,750 + 116,145.45) / 5,500,000
= 664,895.45 / 5,500,000
≈ 0.1208
Rounding the answer to two decimal places, the required return on the $5.5 million portfolio is approximately 12.18%.
Learn more about portfolio
brainly.com/question/17165367
#SPJ11
The last-in, first-out (LIFO) property is found in the ADT ______.
a) list
b) stack
c) queue
d) tree
Answers
The last-in, first-out (LIFO) property is found in the abstract data type (ADT) known as a stack. A stack is a fundamental data structure that follows the LIFO principle, meaning that the last element added to the stack is the first one to be removed.
It operates on two main operations: "push" and "pop". The "push" operation adds an element to the top of the stack, while the "pop" operation removes the topmost element from the stack. The LIFO behavior of a stack makes it useful in various scenarios. For example, when dealing with function calls, a stack is commonly used to keep track of the order of function invocations. As each function is called, its context is pushed onto the stack, and when a function completes, its context is popped from the stack, allowing the program to return to the previous function.
Stacks also find application in parsing expressions, undo/redo operations, backtracking algorithms, and managing memory in a computer system.
In contrast, the other options mentioned are as follows:
a) A list is a linear data structure where elements are stored in a particular order, but it does not inherently possess the LIFO property.
c) A queue is another ADT but operates on the first-in, first-out (FIFO) principle, where the element added first is the first one to be removed.
d) A tree is a hierarchical data structure that does not exhibit the LIFO property either. It organizes elements in a branching structure, allowing for efficient searching and data representation.
Therefore, the correct answer is b) stack when referring to the ADT that possesses the last-in, first-out (LIFO) property.
Learn more about stack here:
https://brainly.com/question/32337058
#SPJ11
What is the last step of the ethical decision-making process?
Answers
Answer:
The last stage of this process is the adaptation stage.
Explanation:
In this stage, the clinician will look to adapt the selection or solution of the ethical dilemma by refining it, or by returning to the evaluation and selection stages to find and choose a better solution.
Understand different customer types and analyze how customers make buying decisions.
Answers
There are several types of customers, such as individual consumers, businesses, government agencies, and non-profit organizations.
What are their characteristics?Each customer type has unique characteristics and factors that influence their buying decisions. Individual consumers often make buying decisions based on personal preferences, brand reputation, and price.
Businesses focus on the quality, cost, and reliability of products and services, as well as the potential return on investment.
Government agencies consider factors such as budget constraints, regulations, and the ability to meet specific needs.
Non-profit organizations often prioritize the impact and social responsibility of their purchasing decisions.
Ultimately, customers make buying decisions based on a combination of rational and emotional factors that align with their goals and values.
Read more about customers here:
https://brainly.com/question/26313265
#SPJ1
what is data? why is it important to collect data ? explain the points.
Answers
Answer:
so i dont know if u mean like science or math but like there similar. so data is the results and information you get when you do experiments. It is important to collect it so it can back up your reasons and points. It also helps us advance and become smarter.
Explanation:
Seeing the bank robber jump into his vehicle and speed away, Super
Megan quickly spun into her costume and took off flying into the air to
catch the thief. This is an example of
sounds
dialogue
exciting action
description
Answers
An organisation can utilise the PaaS cloud service model to deploy and run arbitrary software and in addition can also request operating systems and some network components.
Select one:
True
False
Question 2
Not yet answered
Marked out of 1
Flag question
Question text
SaaS offers applications which the user does not have control over of which an example is Dropbox.
Select one:
True
False
Question 3
Not yet answered
Marked out of 1
Flag question
Question text
The minimum requirement for protecting data confidentiality in a public cloud scenario is to use …
Select one:
a.
hash functions.
b.
an industry-standard symmetric encryption algorithm.
c.
two-factor authentication.
d.
public and private key encryption.
Clear my choice
Question 4
Not yet answered
Marked out of 1
Flag question
Question text
Security Assertion Markup Language (SAML) is an privacy standard.
Select one:
True
False
Question 5
Not yet answered
Marked out of 1
Flag question
Question text
In a/an … attack the user tries to determine values of sensitive fields by seeking them directly with queries that yield few records.
Select one:
a.
count
b.
inference
c.
sum
d.
direct attack
Clear my choice
Question 6
Not yet answered
Marked out of 1
Flag question
Question text
When duplicates are made of attributes or entire databases and used for an immediate replacement of the data if an error is detected, it is called a duplicate.
Select one:
True
False
Question 7
Not yet answered
Marked out of 1
Flag question
Question text
OAuth does not exchange identity information, just authorisation as well as allows users to give third-party applications access to only the account resources they need.
Select one:
True
False
Question 8
Not yet answered
Marked out of 1
Flag question
Question text
In a SaaS cloud service module an organisation is able to access logs which applications generate.
Select one:
True
False
Question 9
Not yet answered
Marked out of 1
Flag question
Question text
A change log contains both original and modified values.
Select one:
True
False
Question 10
Not yet answered
Marked out of 1
Flag question
Question text
Suppression and concealment is used to address inference in aggregation and geotracking.
Select one:
True
False
Question 11
Not yet answered
Marked out of 1
Flag question
Question text
Routers achieve integrity through their structure and individual elements.
Select one:
True
False
Question 12
Not yet answered
Marked out of 1
Flag question
Question text
An internal cloud is a cloud that has an infrastructure that is operated exclusively by and for the organisation that owns it, but the management may be contracted out to a third party.
Select one:
True
False
Question 13
Not yet answered
Marked out of 1
Flag question
Question text
Anonymized data can also be revealing and lead to privacy concerns when data is correlated by aggregation.
Select one:
True
False
Question 14
Not yet answered
Marked out of 1
Flag question
Question text
In a hybrid cloud the customer is given access to applications with no control over the infrastructure or even most of the application capabilities
Select one:
True
False
Answers
Question 1 - True An organization can utilize the PaaS cloud service model to deploy and run arbitrary software and in addition can also request operating systems and some network components. The given statement is True. Question 2 - FalseSaaS offers applications that the user does not have control over of which an example is Dropbox. The given statement is False.
Question 3 - b.The minimum requirement for protecting confidentiality data in a public cloud scenario is to use an industry-standard symmetric encryption algorithm.
Question 4 - FalseSecurity Assertion Markup Language (SAML) is a privacy standard. The given statement is False.
Question 5 - b.In an inference attack, the user tries to determine the values of sensitive fields by seeking them directly with queries that yield few records.
Question 6 - TrueWhen duplicates are made of attributes or entire databases and used for immediate replacement of the data if an error is detected, it is called a duplicate. The given statement is True.
Question 7 - TrueOAuth does not exchange identity information, just authorization, and allows users to give third-party applications access to only the account resources they need. The given statement is True.
Question 8 - TrueIn a SaaS cloud service module, an organization can access logs that applications generate. The given statement is True.
Question 9 - True A change log contains both original and modified values. The given statement is True.
Question 10 - True Suppression and concealment are used to address inference in aggregation and tracking. The given statement is True.
Question 11 - True Routers achieve integrity through their structure and individual elements. The given statement is True.
Question 12 - True An internal cloud is a cloud that has an infrastructure that is operated exclusively by and for the organization that owns it, but the management may be contracted out to a third party. The given statement is True
.Question 13 - Truly anonymized data can also be revealing and lead to privacy concerns when data is correlated by aggregation. The given statement is True.
Question 14 - FalseIn a hybrid cloud, the customer is given access to applications with no control over the infrastructure or even most of the application capabilities. The given statement is False.
To know more about infrastructure
https://brainly.com/question/869476
#SPJ11
Need the answer ASAP!!!!
Select the correct answer.
Which software development team member would make the most use of the tool, Load Runner?
O A.
software engineer
OB.
programmer
OC.
business analyst
OD.
tester
Answers
Answer:
software engineer is the answer
One who endorses and lends political support for the completion of a specific project is known as the?
Answers
The person that lends political support for the completion of a specific project is known as the sponsor.
How is the position called?This is the rol of what we call sponsors (in coding and in other areas).
A sponsor is someone who provides financial or other support to a project or activity.
In the case of a coding project (for example making an app), a sponsor may be an individual, organization, or company that provides funding, resources, or other types of support to the project's developers, with the final objective of making some kind of profit from it.
Learn moer about sponsors at:
https://brainly.com/question/27993489
#SPJ1
Click to review the online content. Then answer the question(s) below. using complete sentences. Scroll down to view additional
questions.
Memory Matters
Explain the difference between occasional forgetfulness and Alzheimer's disease.
Answers
Answer:
The answer is below
Explanation:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.
Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.
Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Answer:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Explanation:
got 100% on edg
Which online note-taking device allows students to clip a page from a website and reuse it later?
web clipping tools
electronic sticky notes
offline data storage sites
online data storage sites
Answers
Answer:
The answer is A.) web clipping tools.
Explanation:
Cuz like yeah
Answer: WEB CLIPPING TOOLS
Explanation:
In a distributed database system, the data placement alternative with the highest reliability and availability is Group of answer choices
Answers
Answer:
fully replicated
Explanation:
In a distributed database system, the data placement alternative with the highest reliability and availability is fully replicated. Hence, option B is correct.
What is a distributed database system?A distributed database (DDB) is an organized group of databases that are geographically dispersed among locations in a computer network. A distributed database management system (DDBMS) is a piece of software that controls a distributed database while making the users unaware of the distribution characteristics.
A distributed database is essentially a database that is dispersed across numerous sites, i.e., on various computers or over a network of computers, and is not restricted to a single system. A distributed database system is spread across numerous locations with distinct physical components.
In data warehousing, where enormous volumes of data are processed and accessed by several users or database clients at once, DDBMS is frequently utilized. To manage data in this database system,
Thus, option B is correct.
For more information about distributed database system, click here:
https://brainly.com/question/29896580
#SPJ5
The options were missing-
A. centralized
B. fully replicated
C. strictly partitioned
D. hybrid
ITS A VOTE I NEED HELP
IS THE ANSWER B OR C
IT COULD BE SOMETHING ELSE CORRECT ME
Which element always appears to start on a new line in the browser window
a. class type
b. ID
c. method
d. block level
Answers
Answer: A block-level element is any element that starts a new line.
(a) Code C++ below is a script to display sensors data using for loop technique for every even record in an array. Fill in the blank in code to produce an output as shown in Figure Q2(a). [C3, SP1] int sensor [10] (1) for (int i=0; { } (2)______; (3)_____) distance [i] = sensor[i] * sensor[i] / 5.5; if(_ (4)) { } else { = {12, 12, 10, 10, 8, 8, 6, 6, 4, 4); distance [10]; } cout << "Distance in cm^2 is: //no statement. Console Output Distance in cm^2 is: 26.1818 Distance in cm^2 is: 18.1818 Distance in cm^2 is: 11.6364 Distance in cm^2 is: 6.54545 Distance in cm^2 is: 2.90909 Figure Q2(a): Output sample (5) << endl;
Answers
The given program below displays sensor data using for loop technique for every even record in an array. You need to fill in the blank in the code to produce an output as shown in Figure Q2(a). Here is the solution for this problem:
Code:
#include <iostream>
int main() {
int sensor[10] = {12, 12, 10, 10, 8, 8, 6, 6, 4, 4};
double distance[10];
for (int i = 0; i < 10; i += 2) {
distance[i] = sensor[i] * sensor[i] / 5.5;
if (i == 0) {
std::cout << "Distance in cm^2 is: ";
}
std::cout << distance[i] << std::endl;
}
return 0;
}
In the given program above, the output can be generated using the following code statements: The int array sensor is assigned with the 10 integer values. It contains the values of 12, 12, 10, 10, 8, 8, 6, 6, 4, and 4. The double array distance with 10 double values is declared. It will be used to store the distance calculated using sensor data.The for loop iterates for i=0 to 10 with an increment of 2. For each value of i, distance is calculated using sensor data and stored in distance[i]. If the value of i is 0, the statement "Distance in \(cm^2\) is: " is displayed.
The distance value is displayed for each even record. The distance is calculated as distance[i] = sensor[i] * sensor[i] / 5.5;The output that is generated using this code statements:Distance in \(cm^2\) is: 26.1818 Distance in \(cm^2\) is: 18.1818 Distance in \(cm^2\) is: 11.6364 Distance in \(cm^2\) is: 6.54545 Distance in \(cm^2\) is: 2.90909 Therefore, the blank in the code can be filled with the given code below:
i+=2;
\(distance[i] = sensor[i] * sensor[i] / 5.5;\)
To know more about technique visit :
https://brainly.com/question/31609703
#SPJ11
If you want to remove the autocorrect options button from the screen, you can press the ____ key.
Answers
Answer:
ESC
Explanation:
It allows the user to abort, cancel, or close an operation.
For the athehed netwroth. the numbar of critieal patis is the prajectis the Data-Date on Primavera points to the date of the 1st day of project is a thick blue line pointing at the date of last update is a thin line separates the screen into two areas a thick red line pointing at the date of current day
Answers
The Data-Date on Primavera points to the date of the first day of the project.
In Primavera, the Data-Date represents the reference point in time for tracking and analyzing project progress. It is typically set to the date of the project's first day, indicating the starting point from which the project's schedule and activities are monitored. The Data-Date is important for assessing project performance and determining the critical path, which is the sequence of activities that directly impacts the project's duration. It helps project managers identify any deviations from the planned schedule and make necessary adjustments to ensure the project stays on track. The thick blue line pointing at the Data-Date signifies the start of the project, while the thin line separates the screen into two areas, indicating the progression of time. The thick red line pointing at the date of the current day allows for quick visual reference of the project's progress in relation to the planned schedule.
To know more about Primavera click here,
https://brainly.com/question/30397148
#SPJ11