Clicking the Find button in the Editing group opens the Navigation pane.
true or false
Answers
False. Clicking the Find button in the Editing group does not open the Navigation pane.
The statement is false. Clicking the Find button in the Editing group does not open the Navigation pane. The Find button is typically used to search for specific text within a document, allowing users to locate and replace words or phrases. It does not trigger the opening of the Navigation pane.
The Navigation pane, on the other hand, is a separate feature in Microsoft Office applications such as Word, Excel, and PowerPoint. It provides a visual representation of the document's structure, including headings, pages, and other elements. The Navigation pane allows users to quickly navigate through the document by clicking on the desired section or heading.
To open the Navigation pane in Microsoft Word, for example, you can go to the View tab on the ribbon and check the "Navigation Pane" option in the "Show" group. Alternatively, you can use the shortcut key combination of Ctrl + F to open the Navigation pane directly. The Find button, however, does not have any direct relationship with the Navigation pane and serves a different purpose of searching and replacing text within the document.
Learn more about Navigation pane here:
https://brainly.com/question/29910888
#SPJ11
Related Questions
In the game Badland, how do you get to the next level?
A.
If you get close enough to the exit pipe, it sucks you up and spits you out in the next level.
B.
If you shoot enough enemies, you automatically advance to the next level.
C.
If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
D.
If you answer enough puzzles correctly, you advance to the next level.
Answers
In the game Badland, the way a person get to the next level is option C: If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
What is the story of BADLAND game?
The story occurs throughout the span of two distinct days, at various times during each day's dawn, noon, dusk, and night. Giant egg-shaped robots start to emerge from the water and background and take over the forest as your character is soaring through this already quite scary environment.
Over 30 million people have played the side-scrolling action-adventure game BADLAND, which has won numerous awards. The physics-based gameplay in BADLAND has been hailed for being novel, as have the game's cunningly inventive stages and breathtakingly moody sounds and visuals.
Therefore, in playing this game, the player's controller in Badland is a mobile device's touchscreen. The player's Clone will be raised aloft and briefly become airborne by tapping anywhere on the screen.ult for In the game Badland, the way a person get to the next level.
Learn more about game from
https://brainly.com/question/908343
#SPJ1
A ______________ is enough memory to store a letter of the alphabet or a small number.
Answers
A bit is enough memory to store a letter of the alphabet or a small number. Its binary nature allows us to encode and represent various characters and digits using specific bit patterns.
A bit, short for binary digit, is the smallest unit of information in computing. It can represent two possible states, usually denoted as 0 or 1. With just one bit, we can store a single binary value. In the context of storing a letter of the alphabet or a small number, we can assign a specific bit pattern to each character or digit. For example, let's consider the English alphabet. With 26 letters, we can represent them using 5 bits (2^5 = 32). A through Z can be mapped to 00000 through 11001 in binary, respectively. Similarly, for small numbers, we can assign specific bit patterns to represent them.
In summary, a bit, the smallest unit of memory, is sufficient to store a letter of the alphabet or a small number.
To know more about binary visit:
https://brainly.com/question/33333942
#SPJ11
____ is the order of arrangement of files and folders
Answers
Answer:
Organization is the order of arrangement of files and folders.
The most common delimiter is a
-forward slash
-period
-semicolon
-comma
Answers
Answer:
comma
Explanation:
trust me bro
The most common delimiter is a comma. The correct option is d.
What is a delimiter?
Programming languages employ delimiters to define code set characters or data strings, operate as data and code boundaries, and make it easier to comprehend code and divide up distinct implemented data sets and functions.
The values may be separated by any character, however, the comma, tab, and colon are the most often used delimiters. Space and the vertical bar, which is sometimes known as pipe, are occasionally utilized.
With one entry per row, data is organized in rows and columns in a delimited text file. Field separator characters are used to divide each column from the one after it. According to Comma Separated Value, one of the most popular delimiters is the comma.
Therefore, the correct option is d, comma.
To learn more about delimeter, refer to the link:
https://brainly.com/question/14970564
#SPJ2
.Complexity analysis helps in avoiding algorithms with _____.
Group of answer choices low runtime low memory usage high computational efficiency high memory usage
Answers
Complexity analysis helps in avoiding algorithms with high memory usage.
Complexity analysis is the method of determining how well an algorithm works. In other words, it's a method for determining the performance of an algorithm, and it's used to figure out the computational complexity of a problem. When developing algorithms, time and space complexity play an important role. While developing algorithms, the computational efficiency of an algorithm, which is primarily determined by the computational time and memory usage, is critical.
It's necessary to optimize both aspects of the algorithm to improve performance. The goal of complexity analysis is to create a low runtime, low memory usage, and high computational efficiency algorithm. The most effective way to achieve these objectives is through complexity analysis. A complexity analysis identifies and helps to optimize critical areas of an algorithm. To maximize the computational efficiency of an algorithm, one must pay close attention to time and space complexities in the early stages of development.
know more about algorithms here
https://brainly.com/question/22984934#
#SPJ11
please help me with this question pt.1

Answers
Answer:
First answer: A
Second answer: A
Explanation:
I don't know how to explain it.
But I hope it's correct!
I need help I did not mean to do that to my computer

Answers
Answer:
Man...I don't think you can fix that yourself..
i need help how do i fix this????
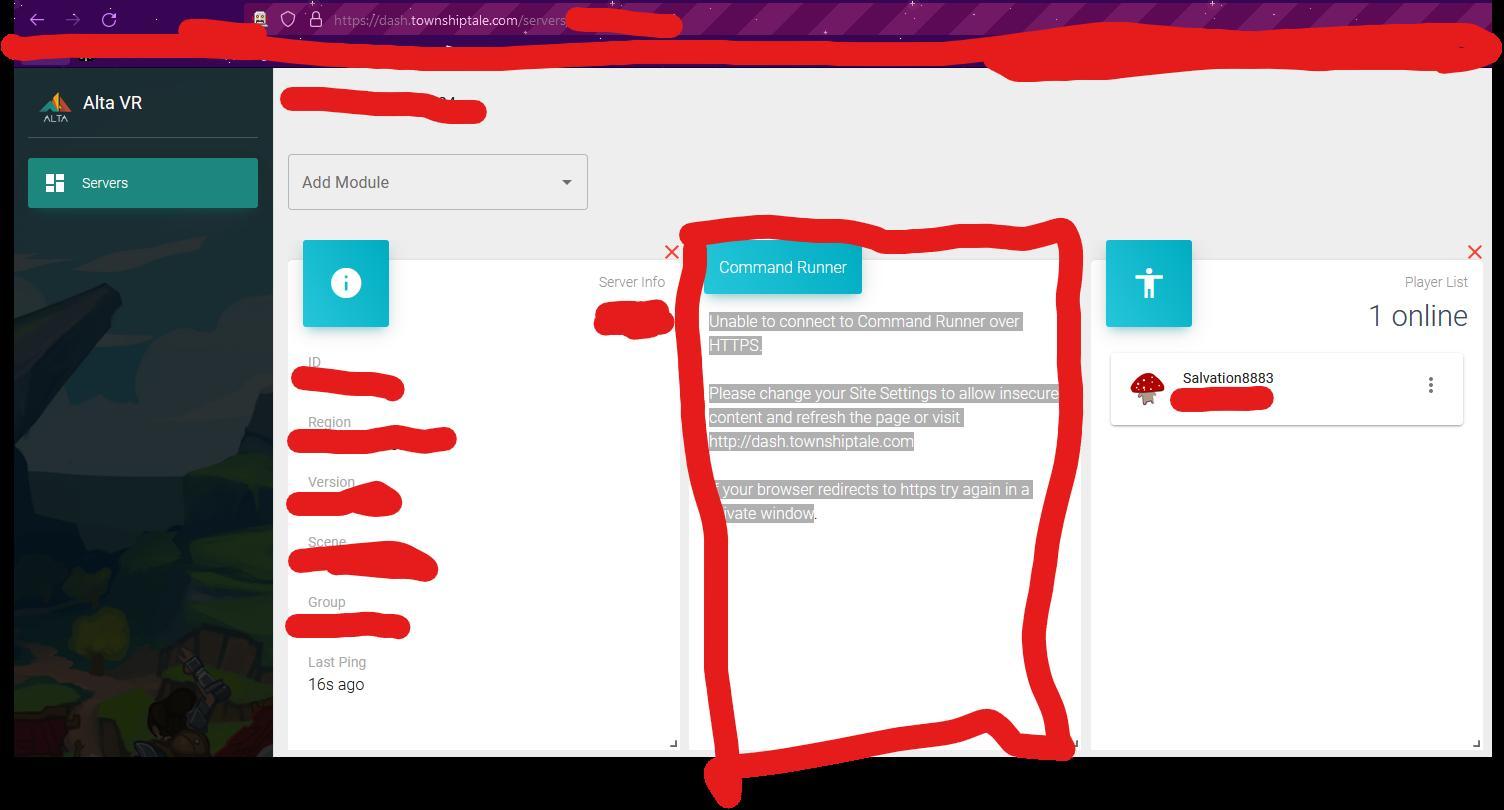
Answers
The error suggests enabling insecure content in the site settings or accessing the URL in a private window. Refreshing the page may also help.
What is a private window?A private window, also known as incognito mode, is a browsing mode that does not save any browsing history, cookies, or site data.
It is important to avoid insecure sites because they can be vulnerable to cyberattacks and put your personal information at risk. Insecure sites do not have a secure connection, which means that the data you enter on these sites, such as passwords or credit card information, can be intercepted by hackers. Browsing in a private window can help protect your online privacy and prevent your personal information from being exposed.
Also, using a trusted antivirus and firewall software can also help to protect against cyber threats.
Learn more about browsers at:
https://brainly.com/question/28504444
#SPJ1
1. What is the recommended cryptosystem to secure data at rest in the cloud?
2. What are centralized logical routed hubs in the cloud the enable consumers to connect their virtual networks and on-premises networks to a single component?
Answers
1. The recommended cryptosystem to secure data at rest in the cloud is AES (Advanced Encryption Standard). 2. Virtual private clouds (VPCs).
1. AES, also known as Rijndael, is a symmetric encryption algorithm that is widely recognized as the standard for securing data at rest in the cloud. It offers a high level of security and efficiency in encrypting and decrypting data. AES operates on fixed-size blocks of data and supports key sizes of 128, 192, and 256 bits.
When storing data in the cloud, it is crucial to ensure its confidentiality and integrity. AES provides strong encryption capabilities, making it difficult for unauthorized individuals to access or decipher the encrypted data. It uses a symmetric key, meaning the same key is used for both encryption and decryption processes.
To enhance security, AES is often combined with other cryptographic measures such as key management practices, secure key storage, and secure access controls. These additional measures help protect the encryption keys and ensure that only authorized individuals have access to the decrypted data.
Overall, AES is recommended cryptosystem for securing data at rest in the cloud due to its proven security, efficiency, and compatibility with various platforms and systems.
2. Virtual private clouds (VPCs) are network environments within the cloud infrastructure that allows consumers to have control over their virtual network settings and connections. VPCs act as centralized logical routed hubs, facilitating the connection between virtual networks and on-premises networks to a single component.
VPCs provide a range of networking features, including virtual private networks (VPNs), subnets, route tables, and security groups. With VPCs, consumers can define their own IP address ranges, configure network gateways, and establish secure communication channels between their virtual networks and external networks.
By using VPCs, consumers can extend their on-premises networks to the cloud, enabling seamless integration and connectivity between different network environments. This allows for hybrid cloud architectures, where applications and resources can be distributed across both on-premises and cloud environments.
VPCs offer scalability, flexibility, and control over network configurations, enabling consumers to tailor their network setups to meet their specific requirements. They provide a secure and isolated environment for running applications and services, ensuring data privacy and network segregation.
In summary, virtual private clouds serve as centralized logical routed hubs in the cloud, enabling consumers to connect their virtual networks and on-premises networks to a single component while maintaining security, control, and flexibility over their network configurations.
To learn more about cryptosystems visit:
brainly.com/question/30564489
#SPJ11
To represent 9 different colours, what is the minimum
colour depth needed? Give your answer in bits.
Pls help!!
Answers
Answer:
4 bits
Explanation:
3 bits gives you 8 combinations, which is not enough.
4 bits gives you 16 combinations.
n bits gives you 2ⁿ combinations in general.
To represent 9 different colors, the minimum color depth needed is 4 bits.
A bit is the smallest unit of digital information, representing either a 0 or a 1 in binary code.
In computing, bits form the foundation of data storage and processing, enabling the representation of complex information through combinations of 0s and 1s.
To represent "n" different colors, there is a need to find the smallest "k" such that \(2^k\) is greater than or equal to "n."
For this case, n = 9 (since there are 9 different colors).
Now, we find the smallest "k" such that \(2^k \le 9\):
\(2^k = 2^3 \\\)
= 8 (with 3 bits, we can represent 8 different colors)
\(2^4\) = 16 (with 4 bits, we can represent 16 different colors)
Since 4 bits (\(2^4\)) is the smallest power of 2 that is greater than or equal to 9, the minimum color depth needed to represent 9 different colors is 4 bits.
Learn more about bit here:
https://brainly.com/question/13014227
#SPJ7
briefly describe each of the two approaches when writing such specifications. give an example to show the difference between the approaches that use a specification for a queue data structure.
Answers
The functional approach focuses on the external behavior and properties of the data structure, while the operational approach delves into the internal implementation details.
When writing specifications for a data structure like a queue, there are two common approaches: the functional approach and the operational approach. These approaches differ in their focus and level of detail.
1. Functional Approach:
The functional approach emphasizes the abstract behavior and properties of the data structure without specifying the internal workings or implementation details. It describes what the data structure does and the properties it should satisfy. This approach is more high-level and concentrates on the external interface.
Example functional specification for a queue:
- The queue supports two operations: enqueue(element) and dequeue().
- Enqueue adds an element to the end of the queue.
- Dequeue removes and returns the element from the front of the queue.
- The queue follows a first-in, first-out (FIFO) order, ensuring that elements are processed in the order they were added.
2. Operational Approach:
The operational approach, in contrast, focuses on the internal details and implementation of the data structure. It describes the specific algorithms, data organization, and steps involved in each operation. This approach is more low-level and provides a detailed blueprint for how the data structure should be implemented.
Example operational specification for a queue:
- The queue is implemented using a linked list data structure.
- The queue maintains a reference to both the front and rear nodes of the list.
- Enqueue operation:
- Create a new node with the provided element.
- If the queue is empty, set both the front and rear references to the new node.
- Otherwise, set the next reference of the current rear node to the new node and update the rear reference to the new node.
- Dequeue operation:
- If the queue is empty, return an error.
- Otherwise, store the element in the front node.
- Set the front reference to the next node.
- If the front reference becomes null (indicating an empty queue), also update the rear reference to null.
In summary, the functional approach focuses on the external behavior and properties of the data structure, while the operational approach delves into the internal implementation details. The functional approach is often used for higher-level design and abstraction, while the operational approach provides a more precise specification for implementation.
To know more about data click-
https://brainly.com/question/24027204
#SPJ11
You will watch the short film Figueroa (2019) written, produced, and directed by Victor Hugo Duran. Then answer the following questions:
1. What kind of choices does Duran make in how he covers the scenes? Do you notice a pattern in the kinds of shots he uses?
2. Why do you think he uses the 2.4:1 aspect ratio? What does it do for his story?
3. Why do you think he holds the final shot for so long? How do you think the ending would be different if the shot was only half as long (before the credits come on).
Answers
The kind of choices that Duran makes in how he covers the scenes is
What is a Movie Synopsis?This refers to the brief summary of a screenplay's core content that shows its plot points, conflict, resolution and protagonist's development, etc.
The reason why I think he uses the 2.4:1 aspect ratio is that he wants to cover the action from a wider angle to capture all the actions and activities of the characters.
The reason why I think he holds the final shot for so long is to show the empty room after the two boys had run off.
The ending would have been different if it was half as long because some other story element could have been displayed.
Read more about movie synopsis here:
https://brainly.com/question/1661803
#SPJ1
To read encrypted data, the recipient must decipher it into a readable form. What is the term for this process?.
Answers
Answer:
Decryption.
Explanation:
which of the following creates a virtual machine within a host os?
Answers
Answer: A hypervisor.
Explanation: Known as a virtual machine monitor or VMM, is software that creates and runs virtual machines (VMs). A hypervisor allows one host computer to support multiple guest VMs by virtually sharing its resources, such as memory and processing.
A virtual machine is an independent and complete environment where you can run a guest operating system within a host operating system. The Virtual Machine can run in a window, in full-screen mode, or even remotely.
Several tools create a virtual machine within a host operating system, including the following:VirtualBox: Oracle VirtualBox is a hypervisor that can run on macOS, Windows, and Linux, allowing users to create virtual machines and run them on their operating systems.VMware Workstation: VMware Workstation is a virtualization software that allows you to create virtual machines on your computer and install any operating system as a guest operating system. It's a virtualization software package that can be used to build and manage virtual machines on a single Windows or Linux machine.Microsoft Virtual PC:
Microsoft Virtual PC is a software that allows you to create virtual machines on Windows computers and run a different operating system on top of it. It is a Microsoft product that is widely used by people to create virtual machines.Oracle VM VirtualBox: Oracle VM VirtualBox is a free and open-source hypervisor that can run on a variety of platforms, including Windows, macOS, Linux, and Solaris. It allows users to create virtual machines on their host operating systems and run any operating system as a guest operating system.
To know more about independent visit:
https://brainly.com/question/27765350
#SPJ11
How has music changed with the use of technology?
Musicians can now share their music on the World Wide Web.
Music can easily be created and edited with different applications.
Developers can include music in the background of their websites.
all of the above
please help
Answers
Answer: All of the above
Explanation:
Music like most other things, has been changed by its interaction with technology. Music for instance can now be shared on the internet to people far away from each other with services like Apple music and Tidal benefitting from this.
Different applications have also been created that can help make music from being able to create instrumentals to changing the voices of singers.
Developers are now even able to include their music in their website background as way to market their product, proof of another way music has changed due to technology.
Answer:
all of the above
Explanation:
What value will RAX contain after the following instructions execute?
.data
dwordVal DWORD 84326732h
.code
mov rax,0FFFFFFFF00000000h
mov rax,dwordVal
Will the answer be rax = FFFFFFFF84326732h or rax = 0000000084326732h? And why???
When removing a 32-bit memory operand into rax, will cause the upper 32 bits in RAX to be cleared?
Answers
After the given instructions execute, the value of RAX will be 0000000084326732h. When moving a 32-bit memory operand into RAX, the upper 32 bits of RAX are cleared.
The first instruction, `mov rax, 0 F F F F F F F F 0 0 0 0 0 0 0 0 h`, loads the value 0 F F F F F F F F 0 0 0 0 0 0 0 0 h into RAX. This means that all 64 bits of RAX are set to 1. However, the subsequent instruction, `mov rax, dwordVal`, moves the 32-bit value stored at the memory address `dwordVal` into RAX. Since a 32-bit value is being moved, the upper 32 bits of RAX are cleared, and only the lower 32 bits contain the value from `dwordVal`. Therefore, the final value of RAX is 0000000084326732h.
Learn more about memory address here: brainly.com/question/29044480
#SPJ11
how to know if someone blocked you on imessage without texting them
Answers
There isn't a way to know this that I know of, but you can go to apple support, or a tech website. Contacting your cellular provider can also provide insight into the problem.
Which of the following are a primary cloud computing service model? SaaS, PaaS, IaaS.
Answers
A primary cloud computing service model consists of three main types: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
So, the correct answer is A, B and C.
SaaS provides users access to software applications over the internet, eliminating the need for local installation and maintenance.
PaaS offers a platform that allows developers to create, test, and deploy applications without managing underlying infrastructure.
IaaS provides virtualized computing resources, such as virtual machines, storage, and networking, which users can manage and configure to meet their specific needs.
All three models deliver scalable, flexible, and cost-effective solutions to meet diverse business requirements.
Hence, the answer of the question is A, B and C.
Learn more about cloud computing at https://brainly.com/question/15077275
#SPJ11
Please Help me to find the solution
Answers
i dont have an answer bout this
Help me plz!! I need help

Answers
Answer:
350
Explanation:
Answer:
$350 per month for 2 years
Explanation:
antigen sampling by intestinal m cells is the principal pathway initiating mucosal iga production to commensal enteric bacteria.
Answers
The primary inductive sites where naive B lymphocytes that are specific for bacterial antigens contact their cognate antigens are germinal centers (GCs) in Peyer's patches (PPs).
We created animals whose RANKL-dependent M-cell differentiation was abolished by conditional deletion of Tnfrsf11a in the intestinal epithelium in order to study the role of antigen sampling by intestinal M cells in triggering the SIgA response to gut bacteria. Mice lacking intestinal M cells experienced significant delays in the development of lamina propria IgA plasma cells and the maturation of the PP GC, which led to lower levels of fecal SIgA that remained into adulthood. After weaning, the mammalian mucosal immune system can achieve homeostasis with the commensal gut microbiota thanks to secretory IgA (SIgA) directed against gut resident bacteria.
Learn more about system here-
https://brainly.com/question/14253652
#SPJ4
How can we solve mental stress?
Hello can anyone answer
Answers
Answer:
Please don't delete it. Because other people did!
Explanation:
Use guided meditation, Practice deep breathing, Maintain physical exercise and good nutrition!
By making yourself comfortable around your environment.I know it can be hard but try making yourself feel distracted from stress.Have a break from what you are doing and take your time to heal.
Explanation:
address on the internet
Answers
A device on the internet or a local network can be identified by its IP address, which is a special address.The rules defining the format of data delivered over the internet or a local network are known as "Internet Protocol," or IP.
Which two kinds of Internet addresses are there?
picture of an address found online Internet Protocol (IP) addresses are used to connect your network with the Internet.IP addresses come in two varieties: static and dynamic.In order to help you choose between static and dynamic IP addresses, this article compares their main characteristics. Using one of the several IP lookup programs that are readily available online is the quickest approach to start learning someone's IP address.There are tools available to enter an IP address and search for its free public registry results on websites A network address and a host (or local) address are the components of an internet address.With this two-part address, a sender can identify both the network and a particular host on the network.Each network that connects to another Internet network receives a distinct, official network address. While IP addresses do identify your whereabouts, they do not provide as much detail as a home address.Additionally, IP addresses will never disclose your name, phone number, or any other specific personal details. "Internet protocol" is referred to as IP.For any device connected to your network, your router IP serves as an identification number.For the router to recognize it and send data packets to it, a device (such as a computer or smartphone) needs to have an IP address.Your internet is what it is because of the data packets.To learn more about IP address refer
https://brainly.com/question/21864346
#SPJ1
consider the typical mips pipelined processor with 5 stages: if, id, ex, mem, wb. match each control signal below to the stage in which the signal is used.
Answers
The control signals and the corresponding stages they are used in are PCSrc: IF stage, RegDst: ID stage, ALUSrc: ID stage, RegWrite: WB stage, MemRead: MEM stage, MemWrite: MEM stage, MemToReg: WB stage, Branch: EX stage, ALUOp: EX stage
These control signals are part of the control unit in a computer's processor and are used to coordinate and control the execution of instructions in the different stages of the instruction pipeline.
- PCSrc (Program Counter Source): This control signal is used in the Instruction Fetch (IF) stage. It determines the source of the next instruction address, which can be either the incremented program counter (PC) or the target address of a branch instruction.- RegDst (Register Destination): This control signal is used in the Instruction Decode (ID) stage. It determines whether the destination register for the result of an ALU operation comes from the instruction's immediate field or from the instruction's register field.- ALUSrc (ALU Source): This control signal is also used in the ID stage. It determines the second operand for the ALU operation, which can be either a register value or an immediate value from the instruction.- RegWrite: This control signal is used in the Write Back (WB) stage. It determines whether the result of an operation should be written back to a register.- MemRead: This control signal is used in the Memory Access (MEM) stage. It indicates whether a memory read operation should be performed.- MemWrite: This control signal is also used in the MEM stage. It indicates whether a memory write operation should be performed.- MemToReg: This control signal is used in the WB stage. It determines whether the data to be written back to a register comes from the ALU result or from memory.- Branch: This control signal is used in the Execute (EX) stage. It indicates whether a branch instruction is being executed, and if so, it controls the branch logic.- ALUOp: This control signal is also used in the EX stage.It specifies the operation to be performed, such as addition, subtraction, or bitwise logical operations.
To know more about control signals visit: https://brainly.com/question/29689933
#SPJ11
Explain the simliparities or difference between a workbook , worksheet and spread sheet
Answers
Answer:
Spreadsheet vs Workbook. Summary: Difference Between Spreadsheet and Workbook is that Spreadsheet software allows users to organize data in rows and columns and perform calculations on the data. ... While Workbook is consider as whole file that can contain bundle of worksheets in it.
Explanation:
mark brainlyist
questions about the data policy and privacy policy of YT
the questions are in the picture attached below!

Answers
Answer:
I'm confused
Explanation:
What term is defined as software that allows users to use and adapt it for any purpose, often allowing the public to participate in further development? open well open well open use open use open pit open pit open source
Answers
A terminology which is defined as software that allows users to use and adapt it for any purpose, often allowing the public to participate in further development is: open source.
The types of software license.In Computer technology, there are four (4) main types of software programs based on usage rights and these include the following:
Freeware softwarePurchased licenseShareware softwareOpen source softwareWhat is an open source software?In Computer technology, an open source software can be defined as a terminology which is used to describe a type of software that all end users can use and adapt it for any purpose or modify it for free without paying any license fee (money).
Read more on software here: brainly.com/question/25703767
#SPJ1
structured application development usually involves a(n) , which proceeds from a general design to a detailed structure. group of answer choices
Answers
Structured application development typically involves a top-down approach, which proceeds from a general design to a detailed structure.
In this methodology, the overall system is initially defined, and then it is broken down into smaller, more manageable components or modules. Each module is then further refined and developed, gradually becoming more detailed and specific.
The top-down approach promotes clarity and organization by allowing developers to focus on high-level concepts before diving into the minutiae. It helps in understanding the overall system architecture and the relationships between components. Additionally, it encourages effective communication among team members, as everyone works from a shared, big-picture perspective.
During the process, tools such as flowcharts, data flow diagrams, and pseudocode may be used to represent the system's structure and functionality. These visual aids help developers identify any issues or potential bottlenecks in the design early on, making it easier to address them before moving further into development.
Structured application development also emphasizes the use of modular programming, wherein each module has a specific function and can be tested independently. This modularity not only makes the code easier to understand, maintain, and troubleshoot, but also promotes reusability, as modules can be shared across different applications.
In summary, structured application development's top-down approach fosters organization, efficiency, and communication, resulting in more robust and maintainable software systems.
Learn more about top-down approach here: https://brainly.com/question/18996262
#SPJ11
which analysis is a process of detecting patterns within a dataset over time and using those patterns to make predictions
Answers
Time series analysis is a process of detecting patterns within a dataset over time and using those patterns to make predictions
What are some common applications of time series analysis?Time series analysis is used in a wide range of fields, including finance, economics, engineering, and environmental science. Some common applications include forecasting stock prices, predicting future sales trends, analyzing weather patterns, and monitoring industrial processes.
What are some techniques used in time series analysis?
Time series analysis involves a range of techniques for analyzing and modeling time-dependent data. Some common techniques include statistical methods such as regression analysis and time series decomposition, machine learning algorithms such as neural networks and decision trees, and signal processing techniques such as filtering and spectral analysis. The choice of technique will depend on the specific characteristics of the dataset and the research question being addressed.
Learn more about Time series analysis here:
brainly.com/question/29988157
#SPJ4
router_a is currently the ospf designated router (dr). when will an election occur for a new dr?
Answers
In an OSPF network, the election of a designated router (DR) and backup designated router (BDR) occurs to ensure efficient and reliable routing. The DR is responsible for communicating with other routers in the network, while the BDR takes over if the DR fails.
The election process for a new DR occurs when there is a change in the network topology or when the current DR fails. If router_a is currently the DR, an election will occur if one of the following situations arises:
1. The DR fails: If router_a fails, the BDR will take over as the DR, and a new BDR will be elected.
2. A new router joins the network: If a new router is added to the network, the existing DR and BDR will hold an election to determine the new DR and BDR.
3. The priority of the DR changes: The OSPF protocol allows administrators to assign a priority value to each router in the network. The router with the highest priority becomes the DR. If the priority of router_a is lowered or another router with a higher priority joins the network, an election will occur.
In summary, an election for a new DR will occur when there is a change in the network topology, the current DR fails, or the priority of the DR changes.
Learn more about router here:
https://brainly.com/question/31845903
#SPJ11