according to firstmark's internet of everything landscape survey, energy, supply chain, robotics, and industrial wearables are all part of what dimension of the applications (verticals) segment? question 1 options:
Answers
The answer is industrial internet. The widespread use of smart gadgets has created new commercial prospects, automated work environments, and difficulties in comprehending the potential of these novel technology.
This network makes it possible to gather data, analyze it, and optimize manufacturing, which boosts productivity and lowers costs. It makes use of the data that conventional machines have generated in industrial settings over the past few years by leveraging the power of smart machines and real-time analytics. The IIoT is based on the idea that intelligent machines are better than people at gathering and processing data in real-time and communicating crucial information that can be used to make decisions about the business more quickly and accurately.
Learn more about network here-
https://brainly.com/question/29350844
#SPJ4
Related Questions
write a program to generate following series in qbasics 100,81,64,....1
Answers
Answer:
\(9 \times 9 = 81 \\ 8 \times 8 = 64 \\ 7 \times 7 = 49 \\ 6 \times 6 = 36 \)
it's square root number you multiple times by 2
Which of the variables have the value 50 after executing the code segment?
see the image below for reference
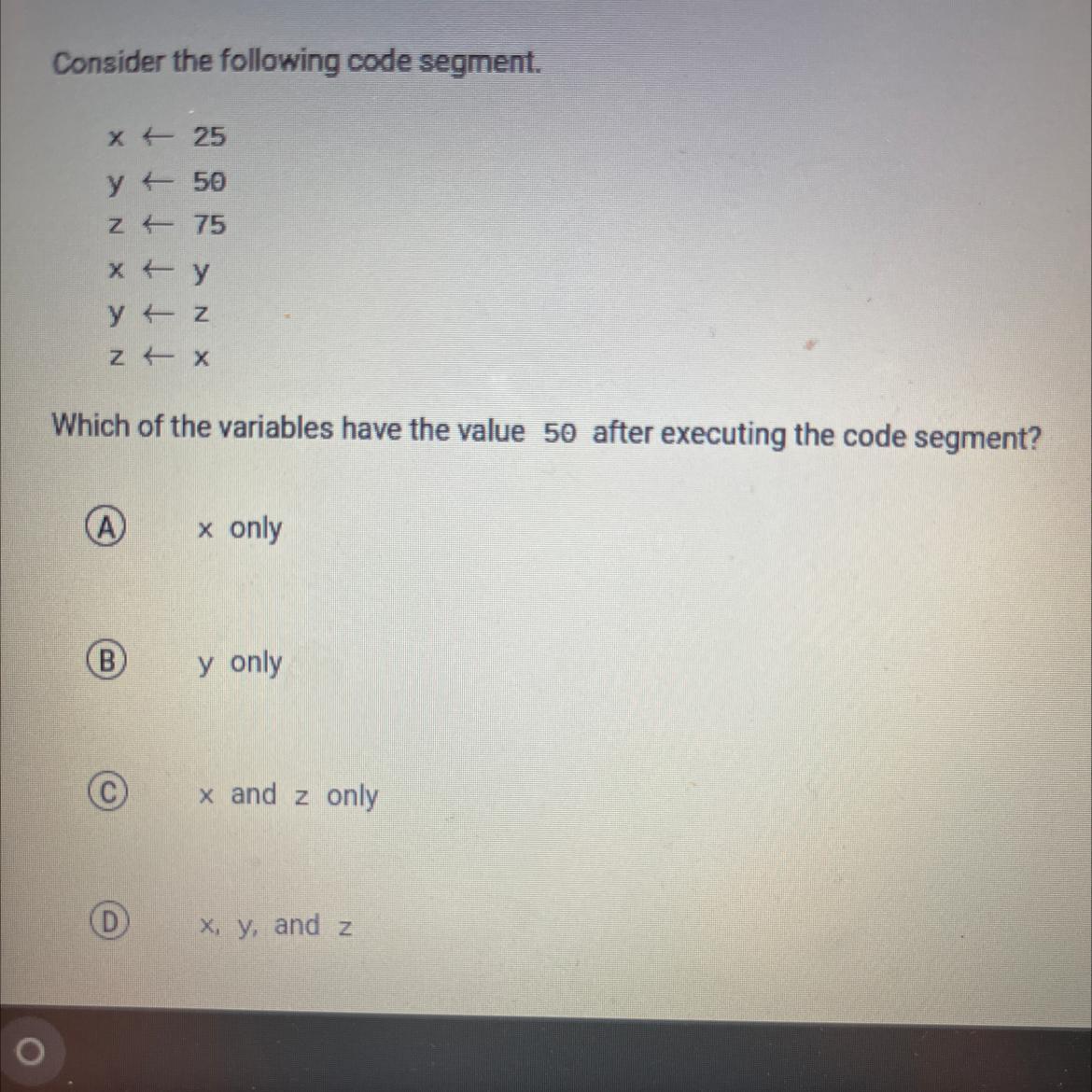
Answers
The segment of code that will have the value of 50 after executing the code segment is this:
C. X and Z only
What is the segment?A segment is a section of code that instructs the computer to take certain actions. In the above code, we can see that the y value is set to return the value of 50.
Also, in the fourth instruction, the x value is instructed to return the value of y. So, the segment of code that is meant to execute and return the number, 50 is option c which contains x and z.
Learn more about coding here:
https://brainly.com/question/22654163
#SPJ1
in a database for a health care clinic, a medical specialty is listed only once in the specialties table, but each specialty may be linked to many doctors in the doctors table. what type of relationship do the specialties and doctors tables have?
Answers
The specialties and doctors tables in the health care clinic database have a one-to-many relationship.
What is a one-to-many relationship?
Each area specialty from the specialties table can be linked to multiple doctors at the doctors table. This means that each record in the specialties table can be related to many records in the doctors table, but each record in the doctors table can only be related to one record in the specialties table. This relationship is established through a foreign key in the doctors table that references the primary key of the specialties table.
To know more about the primary key visit:
https://brainly.com/question/28272285
#SPJ11
SRFRAME RKMATE - people from nearby provinces come to buy livestock direct from raisers themselves.
Answers
Answer:
Farmers market.
Explanation:
Farmers market is a type of market (marketplace) where people from nearby provinces come to buy livestock direct from raisers themselves.
This ultimately implies that, the consumers go to farmers market to buy farm produce such as vegetables, fruits and livestock directly from the farmers.
Additionally, farmers market is devoid of middlemen such as wholesalers or retailers in the transactional process.
Which two contextual tabs help you change the look and feel of SmartArt?
Answers
What is the answer to 4.9 Code Practice: Question 2
Answers
Answer:
sum = 0
for i in range(20, 100, 10):
sum = sum + i
Print(sum)
Explanation:
The answer to 4.9 Code Practice: Question 2 is 200 of the total output.
What is the output?An output record that a laptop sends. Computers best paintings with virtual information. Any entry that a laptop gets have to be digitised. Often records must be transformed and returned to an analogue layout whilst it is output, as an instance the sound from a laptop's speakers.
The answer to 4.9 Code Practice: Question 2 is 200 output of all the total outputs this is the answer.
Read more about the Code :
https://brainly.com/question/3653791
#SPJ2
In every tool, how can you access that tool's presets?
Answers
The way to access a tool's presets may vary depending on the specific tool and software you are using. However, here are some common ways to access presets in different types of software:
Graphics editing software (e.g. Photoshop, Illustrator): Presets can typically be found in the tool options bar or the presets panel. In Photoshop, for example, the presets for a tool can be accessed by clicking on the tool options bar and selecting the preset dropdown menu.
Audio editing software (e.g. Audacity, Pro Tools): Presets can typically be found in the effect menu or plugin panel. In Audacity, for example, the presets for an effect can be accessed by selecting the effect and clicking on the preset dropdown menu.
3D modeling software (e.g. Blender, Maya): Presets can typically be found in the tool properties panel or the object properties panel.
learn more about Photoshop here :
https://brainly.com/question/31695367
#SPJ11
In the following scenario, which can a photo editor digitally do to photos that could not be done before?
A photo shoot for a new advertising campaign has just finished. The ad campaign is for a new line of makeup from an international beauty corporation. The photo spread includes several close-up shots of models wearing the different makeup products.
Add a soft focus to the image.
Remove freckles from the model’s face.
Add a warm glow to the entire photo.
Enhance the color of the makeup and tone down the color of the model’s skin.
Answers
Answer:
if you didn't yet already do the question think the answer is D
Explanation:
Which of the following is true regarding switched backbones?
Answers:
A. They place all network devices for one part of the building physically in the same room, often in a rack of equipment
B. They have an advantage of requiring less cable
C. They make it more difficult to move computers from one LAN to another
D. Network capacity is always tied to the physical location of the computers
E. They are harder to maintain and upgrade than a BN that is not rack-based
Answers
They place all network devices for one part of the building physically in the same room, often in a rack of equipment.
What is switched network?A computer network that uses only network switches, as opposed to Ethernet hubs on Ethernet networks, is referred to as a fully switched network.Switched Backbones are used in new construction, in the distribution layer, and occasionally in the core layer. They can be rack- or chassis-based. the numerous routers of other designs are replaced Backbone has fewer devices but more cables.Rack-Based Exchanged Backbones puts all network switch hardware in a single "rack" room. simple to upgrade and maintain. requires more cable, though this is typically a minor portion of the cost.switchable backbones based on a chassis Instead of using a rack, use a chassis switch that allows administrators to plug modules into it.To learn more about switched network refer :
https://brainly.com/question/12811608
#SPJ4
what is the molecular activity of mattern
Answers
Matter is made up of extremely tiny particles called atoms and molecules. Atoms and molecules make up the three common states of matter on Earth—solids, liquids, and gases. The particles of a liquid are attracted to one another, are in motion, and are able to move past one another.
- BRAINLIEST answerer
what is the type of software that locks your device until you pay a hacker to gain access again?
Answers
True or False: Using “OR” between search terms helps narrow down
Answers
Question 1
What type of server does your computer communicate with to find the location of a website
on the internet?
Both IPv4 and IPv6
IPv6
URL
DNS
IPv4
Answers
DNS
What is a DNS server?
The World Wide Web and the internet are uncharted territories that depend on computer languages and codes to locate and exchange data and information. The Domain Name System, or DNS, is one of the most essential tools used on the internet. (Despite the fact that many people mistakenly believe "DNS" to stand for "Domain Name Server," it actually stands for "Domain Name System. The TCP/IP protocol suite, which is a collection of rules for how computers exchange data over the internet and various private networks, includes the DNS system. It serves a crucial function by transforming easily recognizable domain names like "howstuffworks.com" into the Internet Protocol (IP) address 70.42.251.42 that computers use to recognize one another on the network. In a nutshell, it is a matching system.To learn more about DNS refer:
https://brainly.in/question/9910576
PLZ HELP!! How does HTML help solve the problem of telling a computer what a web page looks like, not just the content that is on it?
Use complete sentences (at least 4).
Answers
HTML provides information to your browser about the organization of your document, including the locations of headers, paragraphs, and language that need emphasis.
What is HTML?The preferred markup language for documents intended to be viewed in a web browser is HTML, or HyperText Markup Language.
Technologies like Cascading Style Sheets and scripting languages like JavaScript can help.
Your browser receives information from HTML about how your page is laid out, including the locations of headers, paragraphs, and material that needs to be highlighted.
Based on this knowledge, browsers have built-in default rules for how to display each of these elements. You are not obligated to select the default choices, though.
Thus, this way, HTML help solve the problem of telling a computer what a web page looks like.
For more details regarding HTML, visit:
https://brainly.com/question/15093505
#SPJ1
daniel wants to buy a computer to use for playing games after work. he loves racing games and wants to make sure his device has all the specifications needed to run them smoothly and efficiently. which of these factors should he consider?
Answers
The factors which should be considered by Daniel are the RAM capacity and the Processor Core of the computer.
Computer games especially racing and football games are usually memory intensive and as such will require a good amount of RAM in other to ensure that the game runs smoothly as the RAM provides a temporary storage required for applications or programs to run smoothly.
Also, the processor core has to be put into consideration, Daniel will need a multi - core processor in other to aid the smooth running of his racing game.
Therefore, the factors that should be considered are the RAM and processor core.
Learn more :https://brainly.com/question/25010930
briefly explain about five kinds of network topology
Answers
Answer:
The mapping of the LAN (local area network) is design called as Topology.
Explanation:
The network topology is to perform a arrangement of the network to the connect sender and receiver in the network connection, there is a five type of topology is there are:- (1) tree topology (2) star topology (3) ring topology (4) bus topology (5) mesh topology.
(1) Tree topology is the nodes are connecting to the hierarchical form it is called by the hierarchical topology its used in the wide area network, and they are manage and maintain the easily, they work in the group.(2) star topology is to the connected to the all computers in a single hub cable through, it is dedicated to the hub connection, star topology is the setup and modify to the network and nodes and low network, is to expensive to use.(3) Ring topology is tho perform it computer to connect by the another computer for each device, ring topology is the use large number and to star topology is to install and expand, troubleshooting is the difficult in the ring topology.(4) Bus topology is the contain computer network device is connected to the single cable, and this only one direction system, bus topology is used in small networks and bus topology is the cost effective, and the bus topology is the limited length cable.(5) Mesh topology is to perform point to point connection to computer devices, and to transmits data to two ways (1) routing (2) flooding.Mesh routing is network requirement and has information of the broken links.Mesh flooding is transmitted to the all computer network and leads to load over network.if an ipv4 address is not located on the same network as source host, what mac address will be used as the destination target mac address?
Answers
When an IPv4 address is not located on the same network as the source host, the destination target MAC address will be the MAC address of the default gateway or router.
The default gateway is the device on a network that serves as an entry or exit point for traffic to and from other networks or the internet. When a device on one network wants to communicate with a device on another network, it sends the data to the default gateway which then forwards it to the destination network.
In this case, the destination target MAC address will be the MAC address of the default gateway as it is the next hop for the data to reach its intended destination.
To know more about network visit:-
https://brainly.com/question/32339145
#SPJ11
At the arcade, what did mike do to remind bryan of Alex?
Answers
Answer:
uhhhh he kept mentioning him i dunno
Explanation:
En la época de la edad de piedra que uso se le daba al silex?
a)Realizar Herramientas y amas
B)Para fabricar platos
C)Para incendio fuego
D)Para poder cultivar
Answers
C is the correct answer hope it helped
Choose the answer. Janice's IT department found that her computer had a program on it that was collecting her personal information as she browsed the Web. What is this an example of?
spyware
pharming
spam
spoofing
Answers
Answer:
Spyware
Spam is just unwanted soliciation, spoofing is making links appear as something else, pharming is creating a fake website for victims to use.
hashim's windows 10 computer has slowed down and is not working as well as it once did. what can he do to reset his system without deleting any personal files or changing any settings?
Answers
He can refresh your computer on Windows 8 or later, all user files and settings are preserved but Windows is rebuilt.
When you reset your computer, Windows is installed from scratch and all apps, programs, user files, and settings are removed. When a program is active or inactive and operating on a computer, it requires varying quantities of memory. The application's packaging or website lists the least and recommended amount of memory that a machine should have in order to run the program. The program uses different amounts of memory depending on how it is used, though. The steps below can be used to find out how much memory a program is using right now.
You can see a list of all currently active processes together with their memory usage on the Processes page, as demonstrated in the sample image above. The highlighted firefox.exe, for instance, is consuming more than 1 GB of memory.
Know more about Windows here:
https://brainly.com/question/13502522
#SPJ4
to add background colour to the webpage – attribute is used in body tag
Answers
\(\mathfrak{\huge{\orange{\underline{\underline{AnSwEr:-}}}}}\)
Actually Welcome to the Concept of the HTML.
The tag that can give background color to the Web pages is :-
1.) <Body> bgcolor = "Orange"
</Body>
write a function that takes in a course we want ti avoid and a list of courses and their prerequisities, and return how many courses we can take before the course we want to avoid
Answers
Here's an implementation of the function you requested in Python:
python
def count_courses_to_take(course_to_avoid, course_list):
# Create a dictionary to store the prerequisites of each course
prereqs = {}
for course in course_list:
prereqs[course[0]] = course[1:]
# Create a set to store the courses we can take
available_courses = set(prereqs.keys())
# Create a set to store the courses we want to avoid
avoid_courses = set([course_to_avoid])
# Create a set to store the courses we can take before the course we want to avoid
can_take = set()
# Loop through each course
while available_courses:
# Find a course that has no prerequisites or whose prerequisites have all been taken
course = None
for c in available_courses:
if not set(prereqs[c]) - can_take:
course = c
break
# If we can't find such a course, we're stuck and we can't take any more courses
if course is None:
break
# Add the course to the set of courses we can take
can_take.add(course)
# If we've reached the course we want to avoid, we're done
if course == course_to_avoid:
break
# Remove the course from the set of available courses
available_courses.remove(course)
# Return the number of courses we can take before the course we want to avoid
return len(can_take)
This function takes in two arguments: course_to_avoid, which is the name of the course we want to avoid, and course_list, which is a list of tuples where each tuple contains the name of a course and its prerequisites. The function returns the number of courses we can take before the course we want to avoid.
The function works by first creating a dictionary prereqs that stores the prerequisites of each course. Then it creates a set available_courses that contains the names of all the courses, and a set avoid_courses that contains the name of the course we want to avoid. It also creates an empty set can_take to store the names of the courses we can take.
The function then enters a loop that continues until there are no more available courses or we have reached the course we want to avoid. In each iteration of the loop, the function looks for a course that has no prerequisites or whose prerequisites have all been taken. If such a course is found, it is added to the set can_take and removed from the set available_courses. If we have reached the course we want to avoid, the loop is terminated.
Finally, the function returns the number of courses in the set can_take.
To know more about Python, click here:
https://brainly.com/question/30427047
#SPJ11
Edmentum Plato Course - Learning in A Digital World: Strategies for Success
How can a student tell if a piece of research is current?
A.
The information was written recently or has been updated recently.
B.
The ideas fit with what is widely known about the topic now.
C.
The writer of the information is still writing other pieces.
D.
The website the information is from is up to date and still active.
Answers
Answer:
A
Explanation:
The information was written recently or has been updated recently.
Compute the discount factors for each of the 3 individuals:
Paolo’s discount rate = 5%
Chet’s discount rate = 18%
Jabari’s discount rate = 26%
2. In the Metropolitan City of Deep State there are 5 hospitals (DS1 to DS5)
DS1’s revenue is $1 billion
DS2’s revenue is $2 billion
DS3’s revenue is $4 billion
DS4’s share is 2X the share of DS5.
Total revenue of all 5 hospitals in Deep State is $25 billion
Compute the HH Index.
3. Given
IH = $5 m
IS ’ = $4 m
E(I) = $4.7 m
p = 10%
IH ’= $4 m
Describe this policy (full, partial,fair, unfair, combination?)
Solve for r
Solve for Is
Solve for q
4. ON the R-S graph describe the locations of
- Partial and Unfair
- Full and Unfair
5. Given starting point E on an R-S graph, assume both r and q increase with r change > q change.
What will be the location of the new point in relation to point E?
Ex. Left above E, Right below E, Left parallel to E, etc.
Answers
The HH File measures market concentration by considering the squared market offers of members, whereas a reasonable approach guarantees an impartial dispersion of assets among people.
How to compute the discount factors for each of the 3 individuals1. To compute the discount variables for each person, we utilize the equation: Rebate figure = 1 / (1 + rebate rate).
Paolo's rebate figure = 1 / (1 + 0.05) = 0.9524
Chet's markdown figure = 1 / (1 + 0.18) = 0.8475
Jabari's rebate calculate = 1 / (1 + 0.26) = 0.7937
2. To compute the HH Record (Herfindahl-Hirschman Record), we ought to calculate the marketing offers of each healing center and square them, at that point entirety them up.
DS4's share = 2 * DS5's share
DS1's share = $1 billion / $25 billion = 0.04
DS2's share = $2 billion / $25 billion = 0.08
DS3's share = $4 billion / $25 billion = 0.16
DS5's share = 1 / 2 + 1 = 0.3333 (since DS4's share is twice DS5's share)
HH List =\(((0.04^2 + 0.08^2 + 0.16^2 + (2 * 0.3333)^2 + 0.3333^2)) = 0.2629\)
3. The given approach can be portrayed as reasonable. Since E(I) is break even with the normal of IH and IS', it demonstrates an evenhanded dissemination of assets among people.
Tackling for r: r = (IH' - E(I)) / E(I) = ($4m - $4.7m) / $4.7m = -0.1489 or -14.89%
Understanding for Is: Is = IS' / (1 + p) = $4m / (1 + 0.10) = $3.636m
Fathoming for q: q = Is / IH = $3.636m / $5m = 0.7272 or 72.72%
4. On the R-S chart:
Partial and fair: This point speaks to a circumstance whereas it where fractional assets are designated, and the dispersion is considered unjustifiable.Full and fair: This point speaks to a circumstance where all assets are designated, but the conveyance is still considered unjustifiable.5. In case both r and q increment with a bigger alter in r compared to q, the modern point will be found to the cleared out of point E and underneath it on the R-S chart.
Learn more about discount factors here:
https://brainly.com/question/8691762
#SPJ4
meaning of mesh topology
Answers
The meaning of mesh topology is that it is a type of networking that is made up of the fact that all its nodes do work together to share data amongst each other.
What is meant by mesh topology?Mesh topology is a kind of networking that is said to be where the full nodes do act in a form of a cooperation so that they can be able to share or distribute data among themselves.
Note that this topology was said to be first seen or developed in about an approximate of about 30+ years ago and it is one that is often used in military applications and now it is seen to be used in home automation, smart HVAC control, and others.
Hence, The meaning of mesh topology is that it is a type of networking that is made up of the fact that all its nodes do work together to share data amongst each other.
Learn more about mesh topology from
https://brainly.com/question/14879489
#SPJ1
Which textual evidence best supports the conclusion that the knights are intimidated by the visitor?.
Answers
There are ways to know text that support a conclusion. The textual evidence best supports the conclusion is that "So that many of the noble knights were afraid to answer, And all were struck by his voice and stayed stone still".
How do one support a conclusion?One can support a conclusion using;
Topic sentence. Here, one can rephrase the thesis statement.Supporting sentences. Here, one can make a summary or conclude the key points in the body of the passage and also explain how the ideas did fit.Closing sentence. Here, one can use the final words. One can connects them back to the introduction.Learn more about this passage from
https://brainly.com/question/24813043
How do you organize and maintain system and software
records?
Answers
Answer:
To organize and maintain system and software you can use different tools and techniques like using a database management system.
Or u can use vs code
Compute the decimal representation for each of the following numbers.
(a) (1100110)2
(b) (346)7
(c) (3B2)16
(d) (120121)3
Answers
(a) (1100110)2 in decimal representation is 102.
(b) (346)7 in decimal representation is 181.
(c) (3B2)16 in decimal representation is 946.
(d) (120121)3 in decimal representation is 421.
To compute the decimal representation for each of the given numbers, you can use the positional notation system. Here's the decimal representation for each number:
(a) (1100110)2
To convert a binary number to decimal, you can multiply each digit by the corresponding power of 2 and sum them up.
(1100110)2 = (1 * 2^6) + (1 * 2^5) + (0 * 2^4) + (0 * 2^3) + (1 * 2^2) + (1 * 2^1) + (0 * 2^0) = 64 + 32 + 0 + 0 + 4 + 2 + 0 = 102.
Therefore, (1100110)2 in decimal representation is 102.
(b) (346)7
To convert a number from base 7 to decimal, you can multiply each digit by the corresponding power of 7 and sum them up.
(346)7 = (3 * 7^2) + (4 * 7^1) + (6 * 7^0) = 147 + 28 + 6 = 181.
Therefore, (346)7 in decimal representation is 181.
(c) (3B2)16
To convert a number from base 16 (hexadecimal) to decimal, you can multiply each digit by the corresponding power of 16 and sum them up.
(3B2)16 = (3 * 16^2) + (11 * 16^1) + (2 * 16^0) = 768 + 176 + 2 = 946.
Therefore, (3B2)16 in decimal representation is 946.
(d) (120121)3
To convert a number from base 3 to decimal, you can multiply each digit by the corresponding power of 3 and sum them up.
(120121)3 = (1 * 3^5) + (2 * 3^4) + (0 * 3^3) + (1 * 3^2) + (2 * 3^1) + (1 * 3^0) = 243 + 162 + 0 + 9 + 6 + 1 = 421.
Therefore, (120121)3 in decimal representation is 421.
Visit here to learn more about decimal representation brainly.com/question/29220229
#SPJ11
114. Flatten Binary Tree to Linked ListGiven a binary tree, flatten it to a linked list in-place.For example, given the following tree: 1 / \ 2 5 / \ \3 4 6look like: 1 -> 2 -> 3 -> 4 -> 5 -> 6
Answers
To flatten a binary tree to a linked list in-place, we can use a recursive approach.
We start by flattening the left and right subtrees of the current node, and then we move the flattened right subtree to the right of the flattened left subtree. Finally, we set the left child of the current node to null and the right child to the flattened subtree.
Here's an implementation in Python:
```
class Solution:
def flatten(self, root: TreeNode) -> None:
"""
Do not return anything, modify root in-place instead.
"""
if not root:
return
self.flatten(root.left)
self.flatten(root.right)
if root.left:
right_subtree = root.right
root.right = root.left
root.left = None
# Find the end of the flattened left subtree
end = root.right
while end.right:
end = end.right
# Append the flattened right subtree
end.right = right_subtree
```
In the example given, the binary tree would be flattened to the linked list: 1 -> 2 -> 3 -> 4 -> 5 -> 6.
To know more about linked list visit:
https://brainly.com/question/28938650
#SPJ11