a user receives an e-mail warning of a dangerous computer virus and instructs the user to delete files it claims were put there by the virus. however, in reality the files named are actually critical windows system files that should never be deleted. which term best describes this scenario?
Answers
Answer:
The scenario you described, in which a user receives an email warning of a dangerous computer virus and is instructed to delete critical system files, is an example of a hoax. A hoax is a false or deceptive message that is designed to trick or deceive the recipient.
Explanation:
In this case, the email warning of a dangerous virus is likely a hoax, as deleting critical system files can cause serious problems with the operating system and can render the computer inoperable. It is important to be cautious when receiving emails that contain warning messages or instructions to delete files, and to verify the information before taking any action.
Other examples of hoaxes include false alerts about security vulnerabilities or threats, false reports of celebrity deaths, and false offers or promotions. It is important to be aware of these types of hoaxes and to verify the information before taking any action or sharing it with others.
Related Questions
what is the main theme of The hundred dresses
Answers
Explanation:
The main theme of The hundred dresses is about the act of forgiving someone's mistake. i hope so
The main theme of The Hundred Dresses is that we should never judge someone by their name, looks or status. This theme is presented through a Polish immigrant in America, who is bulied by the other girls of her class because she had a "strange" name and she was poor, but then she surprises everyone by her drawing skills.
Define a method printFeetInchShort, with int parameters numFeet and numInches, that prints using ' and " shorthand. End with a newline. Ex: printFeetInchShort(5, 8) prints: 5' 8"
Answers
Answer:
Follows are the progrm to this question:
#include <iostream>//defining header file
using namespace std;
void printFeetInchShort (int numFeet , int numInches)//defining a method printFeetInchShort
{
cout<<numFeet <<"'"<<numInches<< " \" ";//print value with ' and "
}
int main()//defining main method
{
printFeetInchShort(5,8);//call method by pssaing integer value
return 0;
}
Output:
5'8 "
Explanation:
In the above-given program, a method "printFeetInchShort" is defined, that accepts two integer variable, that is "numFeet and numInches" in its parameters.
Inside the method, a print method is used that prints integer variable value with " ' and " " value. At the last step, the main method is defined, which calls the above-given method by passing integer value in its parameters.Cho 1 biến x thuộc kiểu dữ liệu Integer , hãy cho biết biến x dùng để làm gì?
Answers
Answer:
???
Explanation:
Within a word processing program, predesigned files that have layout and some page elements already completed are called
text boxes
templates.
frames
typography
Answers
Answer:
I think it's B) templates
Sorry if it's wrong I'm not sure!!
Explanation:
Within a word processing program, predesigned files that have layout and some page elements already completed are called: B. templates.
In Computers and Technology, word processor can be defined as a processing software program that is typically designed for typing and formatting text-based documents. Thus, it is an application software that avail end users the ability to type, format and save text-based documents such as .docx, .txt, and .doc files.
A template refers to a predesigned file or sample in which some of its page elements and layout have already completed by the software developer.
In this context, predesigned files in a word processing program, that have layout and some page elements already completed by the software developer is referred to as a template.
Read more on template here: https://brainly.com/question/13859569
Ideally, a chain network should be used when .
A) accuracy of information is most important
B) high speed of information transfer is desired
C) the network is expected to facilitate emergence of a leader
D) the teams using the chain network are self-managed teams
E) high member satisfaction is desired
Answers
A chain network should ideally be used when the accuracy of information is most important and when high speed of information transfer is desired.
A chain network is a communication structure where information flows sequentially from one member to another in a linear fashion. In such a network, each member is connected to the next member, forming a chain-like structure.
When accuracy of information is most important, a chain network can be beneficial. Since information is passed from one member to the next in a linear manner, there is a reduced risk of distortion or misinterpretation of information. This ensures that accurate information is conveyed consistently throughout the network.
Additionally, a chain network can facilitate high-speed information transfer. As information flows in a linear fashion, it can be quickly relayed from one member to another without the need for complex routing or decision-making processes. This enables efficient and rapid communication within the network.
While the other options mentioned, such as the facilitation of emergence of a leader, self-managed teams, and high member satisfaction, may not be directly related to the characteristics of a chain network, they can still be influenced by the communication structure to some extent. However, the primary strengths of a chain network lie in its ability to ensure accuracy of information and enable high-speed information transfer.
Learn more about information transfer here:
https://brainly.com/question/30625702
#SPJ11
make a story that ends in ´ I have never found such a kind person ever since´
Answers
Lol I know this isn’t that good , but you can change it up or add stuff.
Which two protocols operate at the highest layer of the TCP/IP protocol stack? (Choose two.)
DNS
Ethernet
IP
POP
TCP
UDP
Answers
The TCP/IP protocol stack consists of four layers: the application layer, transport layer, internet layer, and network access layer.
The highest layer is the application layer, which includes protocols that operate directly on behalf of a particular application. The two protocols that operate at the highest layer of the TCP/IP protocol stack are DNS and POP.
DNS (Domain Name System) is a protocol used for translating domain names (such as www.example.com) into IP addresses that computers can understand.
POP (Post Office Protocol) is a protocol used for retrieving email from a mail server.
Ethernet, IP, TCP, and UDP are protocols that operate at lower layers of the TCP/IP protocol stack. Ethernet operates at the network access layer, while IP, TCP, and UDP operate at the internet and transport layers.
Learn more about TCP/IP here:
https://brainly.com/question/27742993?
#SPJ11
Please help I have errors codes and don’t know that they are.
Please help thank You.

Answers
Do know who is in my dp?
Answers
Answer:
wut dat mean i dont understand
Explanation:
Answer:
Interested.... :-):-):-):-):-):-)
Define function print_popcorn_time() with parameter bag_ounces. If bag_ounces is less than 3, print "Too small". If greater than 10, print "Too large". Otherwise, compute and print 6 * bag_ounces followed by "seconds". End with a newline. Remember that print() automatically adds a newline.
Answers
Answer:
In Python:
def print_popcorn_time(bag_ounces):
if bag_ounces < 3:
print("Too small")
if bag_ounces > 10:
print("Too large")
else:
print(str(6 * bag_ounces)+" seconds")
Explanation:
This defines the function
def print_popcorn_time(bag_ounces):
This checks if bag_ounces < 3
if bag_ounces < 3:
If yes, it prints too small
print("Too small")
This checks if bag_ounces > 10
if bag_ounces > 10:
If yes, it prints too big
print("Too large")
If otherwise,
else:
Multiply bag_ounces by 6 and print the outcome
print(str(6 * bag_ounces)+" seconds")
Answer:
Explanation:
def print_popcorn_time(bag_ounces):
if bag_ounces < 3:
print("Too small")
elif bag_ounces > 10:
# Use of 'if' for this portion, will only yield a test aborted for secondary tests
print("Too large")
else:
print(str(6 * bag_ounces)+" seconds")
user_ounces = int(input())
print_popcorn_time(user_ounces)
help quickly please ,due today
• Complete the activity on Page: 149, design a logo, and slogan for your business.
• Write notes on MS Word about the products you want to sell, make notes for 5 products.
• You design logos on paper or you can also use online tools.
Answers
In terms of Logo Design, the ways to start the designs are:
Begin by problem-solving plans related to your trade, allure principles, and allure target hearing.Sketch coarse ideas on paper to anticipate various trademark designs.Note shapes, letters, typography, and color blueprints that show your trade effectively.Refine the preferred idea by establishing a more particularized sketch or use online forms for mathematical design etc.How do one design a logo?In terms of Slogan Creation:
Summarize the key meaning or singular transfer proposition of your trade.Keep the slogan short, significant, and impressive.Consider utilizing rhymes, poetry in which lines end with like sounds, or humorous ambiguous use of word or phrase to manage addictive.Ensure the slogan joins accompanying your brand's voice and pitch.Lastly, Test the slogan accompanying a limited group of society to draw feedback and clarify if inevitable.
Learn more about logo from
https://brainly.com/question/26631819
#SPJ1
What is the purpose of the Lookup Wizard?
to create a yes/no field quickly
to reference data from another table
to combine more than one field in a table
to generate a random number automatically
Answers
Answer:
The answer is B. To reference data from another table
Explanation:
I just got it right in Edg
(9 pts) what are the cidr addresses for a network if all its addresses start with 145.98? and if this network has exactly two subnets, what are the cidr addresses for each of its subnets?
Answers
The cidr addresses for each of its subnets are 145.98.0.1 to 145.98.127.255 and 145.98.128.1 to 145.98.255.255.
What is a network?A network is a collection of two or more computers or other electronic devices that are linked together to exchange data and share resources.
It should be noted that 145.98 = 10010001.01100010
Then there are 2^(32-16) = 2^16 addresses possible. The range of addresses is from 145.98.0.1 to 145.98.255.255
If there are 2 subnets, 1 bit will be used for the subnet. So each subnet will have 2^32-17 = 2^15 addresses.
For subnet 1 range of IP shall be 145.98.0.1 to 145.98.127.255
For subnet 2, the range of IP shall be 145.98.128.1 to 145.98.255.255
Learn more about network on:
https://brainly.com/question/1326000
#SPJ1
Engine blocks have water chambers that help heat up the engine when it gets too cold.
False
True
Answers
Answer:True
Explanation:
[Plato] In A Soccer Game, You Want To Finish The First Half In Five Minutes. So, You Set The Match Duration To Ten Minutes. This Is An Example Of What Kind
Of Time Element?
A)Altered
B)Variable
C)Authentic
D)Player Adjusted
Answers
Answer: D. Player Adjusted
Explanation: The reason why the answer is player adjusted is because a player in the game is changing the time to 10 minutes.
Have a nice day!
Check the attached pdf. Don't try searching up the internet, it's no use. Write a code which satisfies all requirements in the question inside the attached pdf file.
Answers
Coding: In the txt. file below
Explanation:
This is my coding and I need to improve it to display a receipt of items purchased , the total amount need to be paid and allow the user to enter the cash amount they are going to pay and calculate the balance for them.
Please have a great day <3
!WILL GIVE BRAINLIEST!
Write a Python program that prompts the user for a word. If the word comes between the words apple
and pear alphabetically, print a message that tells the user that the word is valid, otherwise, tell
the user the word is out of range.
Answers
Answer:
word = input()
if word > "apple" and word < "pear":
print("Word is valid.")
else:
print("Word is out of range.")
What happened when the disk you inserted is not readable by this computer?
Answers
When the disk you have inserted is not readable by the computer, it means that the computer is unable to access or retrieve any data from the disk.
This can happen due to several reasons. One possibility is that the disk is corrupted or damaged. In such cases, the computer may display an error message stating that the disk is unreadable or cannot be recognized. Another possibility is that the disk format is not supported by the computer's operating system. Different operating systems have different file systems, and if the disk is formatted in a file system that is not compatible with the computer, it won't be readable. Additionally, if the disk is encrypted or password-protected, the computer won't be able to read it without the correct credentials. In conclusion, when the disk you inserted is not readable by the computer, it could be due to disk corruption, incompatible file system, or encryption/ password protection.
To know more about Operating system , Visit:
https://brainly.com/question/29532405
#SPJ11
________________ is access to the internet through your tv connection.
Answers
Answer:
Cable Modem
Explanation:
Why is a service level agreement (sla) important?
1.it documents expectations of rising costs.
2.it documents expectations of future resource availability.
it documents expectations of availability, uptime, and security.
3.it documents expectations of usage.
Answers
Service level agreement (SLA) important for "It documents expectations of availability, uptime, and security."
A Service Level Agreement (SLA) is a contract between a service provider and its customers that outlines the level of service and support that the provider is committed to delivering. The SLA documents the expectations of availability, uptime, and security, which are critical factors in determining the quality of service a customer receives. By setting clear expectations and defining metrics for service delivery, an SLA helps to ensure that both the provider and the customer are on the same page, reducing the risk of misunderstandings or disputes. Additionally, an SLA can help to establish a foundation for ongoing communication and collaboration between the provider and the customer.
To learn more about (SLA) visit;
https://brainly.com/question/15269079
#SPJ4
what is a possible hardware upgrade that can be used to add more storage space to a modern smartphone?
Answers
One possible hardware upgrade of smartphone is a microSD card.
One possible hardware upgrade that can be used to add more storage space to a modern smartphone is a microSD card. Many smartphones have a microSD card slot that allows users to insert a memory card to expand the storage capacity of the device. MicroSD cards are available in various sizes, typically ranging from 4GB to 1TB, and can be purchased from most electronics stores or online retailers. Once inserted, the phone will recognize the added storage space, and users can move apps, photos, videos, and other files to the microSD card to free up space on the phone's internal storage. It's important to note, however, that not all smartphones support microSD cards, so it's essential to check the phone's specifications before purchasing one.
Learn more about microSD card here:
https://brainly.com/question/14697099
#SPJ4
PLEASE HELP LAST QUESTION: Which of the following tags is used to anchor a link (options are anchor, link, id, none of the answers)
Answers
IN C++ PROGRAM THE FOLLOWING:A former president wanted to make their mark by transforming the way we determine the importance of words by emphasizing vowels including 'y'!When comparing two words, each word is given a weight.A word receives three points every time a vowel is compared to a consonant.A word receives one point when comparing two vowels or two consonants if its character is greater than the other in the traditional sense.If one word has a vowel and the other has no character, then the word gets two points.If one word has a consonant and the other has no character, then one point is added.If both words have the same character, then no points are assigned. The word with the most points is more important.Write a function that takes in two C-Strings and returns 1 if the first word is more important than the second and returns 2 if the second word is more important and returns 0 otherwise.ExamplesmoreImportant('eel', 'the') returns 1.moreImportnat('the', 'eel') returns 2.moreImportant('angelic', 'mistrust') returns 2.moreImportant('spy', 'ill') returns 1.moreImportant('ill', 'spy') returns 2.moreImportant('trust', 'silly') returns 2.moreImportant(âseeâ, âseaâ) returns 1.Note: this is case insensitive comparison. The toupper() and tolower() functions can help.
Answers
Implementation of the moreImportant function in C++: and there may be alternative approaches to solve the problem.
#include <cstring>
#include <cctype>
int moreImportant(const char* word1, const char* word2) {
int points1 = 0;
int points2 = 0;
while (*word1 && *word2) {
char c1 = std::tolower(*word1);
char c2 = std::tolower(*word2);
if (std::isalpha(c1) && std::isalpha(c2)) {
if (c1 == c2) {
// Same character, no points assigned
} else if (std::strchr("aeiouy", c1) && !std::strchr("aeiouy", c2)) {
points1 += 3;
} else if (!std::strchr("aeiouy", c1) && std::strchr("aeiouy", c2)) {
points2 += 3;
} else if (std::strchr("aeiouy", c1) && std::strchr("aeiouy", c2)) {
points1 += 1;
points2 += 1;
} else if (c1 > c2) {
points1 += 1;
} else {
points2 += 1;
}
} else if (std::isalpha(c1)) {
points2 += 2;
} else if (std::isalpha(c2)) {
points1 += 2;
}
++word1;
++word2;
}
if (*word1 && !*word2) {
points1 += 2;
} else if (*word2 && !*word1) {
points2 += 2;
}
if (points1 > points2) {
return 1;
} else if (points2 > points1) {
return 2;
} else {
return 0;
}
}
Please note that this is just one possible implementation, and there may be alternative approaches to solve the problem.
To know more about function click the link below:
brainly.com/question/29911729
#SPJ11
Match each storyboarding technique with its appropriate description.

Answers
Answer:
Hierarchical – Option C
Linear – Option D
Webbed - Option A
Wheel - Option B
Explanation:
Hierarchical means something that follows the order from general to specific .
Hierarchical – Option C
Linear means something that follows the order from general to specific .
Linear – Option D
Webbed – There is no order in flow of information or it is inconsequential. Hence, option A
Wheel - means the flow is sequential i.e as per the sequence
Wheel – Option B
Which ribbon tab is not a default in Outlook 2016's main interface?
Home
Send/Receive
Folder
Review
Answers
Answer:
Review
Explanation:
The ribbon tab is not a default in Outlook 2016's main interface is Review.
What is ribbon tab?The Ribbon tab in outlook has the options or commands used to do the tasks. Like creating new email, deleting emails, opening a new meeting request, defining category to an item. However, The Ribbon takes up a lot of space on Outlook 2016 screen.
It has Home, Send/Receive mails and Folder options on the ribbon tab except Review.
Thus, the ribbon tab is not a default in Outlook 2016's main interface is Review.
Learn more about ribbon tab.
https://brainly.com/question/24481253
#SPJ2
Assignment: Blues Progression
Blues is a sub-genre of jazz that follows some specific guidelines: specifically, the Blues scale and the Blues chord progression.
In this assignment, you’ll write out a 12-bar Blues chord progression. This assignment is a MuseScore assignment. Do not turn in this document for grading.
Directions:
1. Create a new document in MuseScore
a. For the title, write “MuseScore Assignment: Blues”.
b. For the composer, write your name., then click "next".
c. Under "general", choose “Grand Staff”, then click “Next”.
d. Choose G major for your key signature (1 sharp), then click next.
e. Choose “Piano” (in the Keyboards section) for your instrument. (This step may or may not show for you. It's ok either way!)
f. Choose 4/4 for your Time Signature and 12 measures for number of measure.
g. Click “Finish”.
2. In the Bass Clef, write out a 12-bar Blues Chord Progression.
a. Use whole notes for your chords
b. I – I – I – I – IV – IV – I – I – V7 – IV – I – V7
Save your assignment (with your name!) and submit it to the Composition: Blues Progression Dropbox basket. Turn in the MuseScore file only.
Answers
Explanation:
I can provide you with the 12-bar Blues chord progression as you requested:
In the key of G major:
I (G) – I (G) – I (G) – I (G)
IV (C) – IV (C) – I (G) – I (G)
V7 (D7) – IV (C) – I (G) – V7 (D7)
The Roman numerals in parentheses represent the chords to play in each measure, and the chord names outside the parentheses indicate the actual chords to play in the key of G major.
Which statement about programming languages is true?
1) Lisp was designed for artificial intelligence research.
2) BASIC was the first high-level programming language.
3) FORTRAN was an early programming language designed for business use.
4) Pascal was the first programming language for personal computers.
Answers
Answer:
2
Explanation:
plz make me brainliest
Option A: Lisp was designed for artificial intelligence research.
The acronym Lisp stands for List Programming is a computer programming language developed about 1960 by John McCarthy.Lisp is the second-oldest high-level programming language which has a widespread use today.LISP has a very simple syntax in which a parenthesized list is used to give operations and their operands.This Language was designed for manipulating data strings with convenience.Lisp includes all the working as the function of any object.Lisp uses symbolic functions which are easy to use with AI applications.Originally Lisp was created as a practical mathematical notation used in computer programs.Lisp pioneered many revolutions in the field of computer science such as tree data structures, automatic storage management etc.
What is the maximal number of swap operations performed during the process of selecting consecutive minima during the execution of the heap-sort algorithm
Answers
The maximal number of swap operations during the process of selecting consecutive minima in heap-sort is equal to the number of elements minus one.
How many swaps in heap-sort?During the execution of the heap-sort algorithm, the process of selecting consecutive minima involves building a binary heap from the input array and repeatedly extracting the minimum element. Each extraction of the minimum element involves swapping it with the last element in the heap and reducing the size of the heap.
The maximal number of swap operations that occur during this process can be determined by considering the number of elements in the input array. Since the heap-sort algorithm iterates over the elements, extracting the minimum element, the number of swaps will be equal to the number of elements minus one.
This can be understood by recognizing that each iteration involves swapping the minimum element with the last element in the heap. As the heap size reduces with each extraction, the number of swaps decreases until all elements are sorted.
Therefore, the maximal number of swap operations performed during the process of selecting consecutive minima in the heap-sort algorithm is equal to the number of elements in the input array minus one.
Learn more about heap-sort
brainly.com/question/30024950
#SPJ11
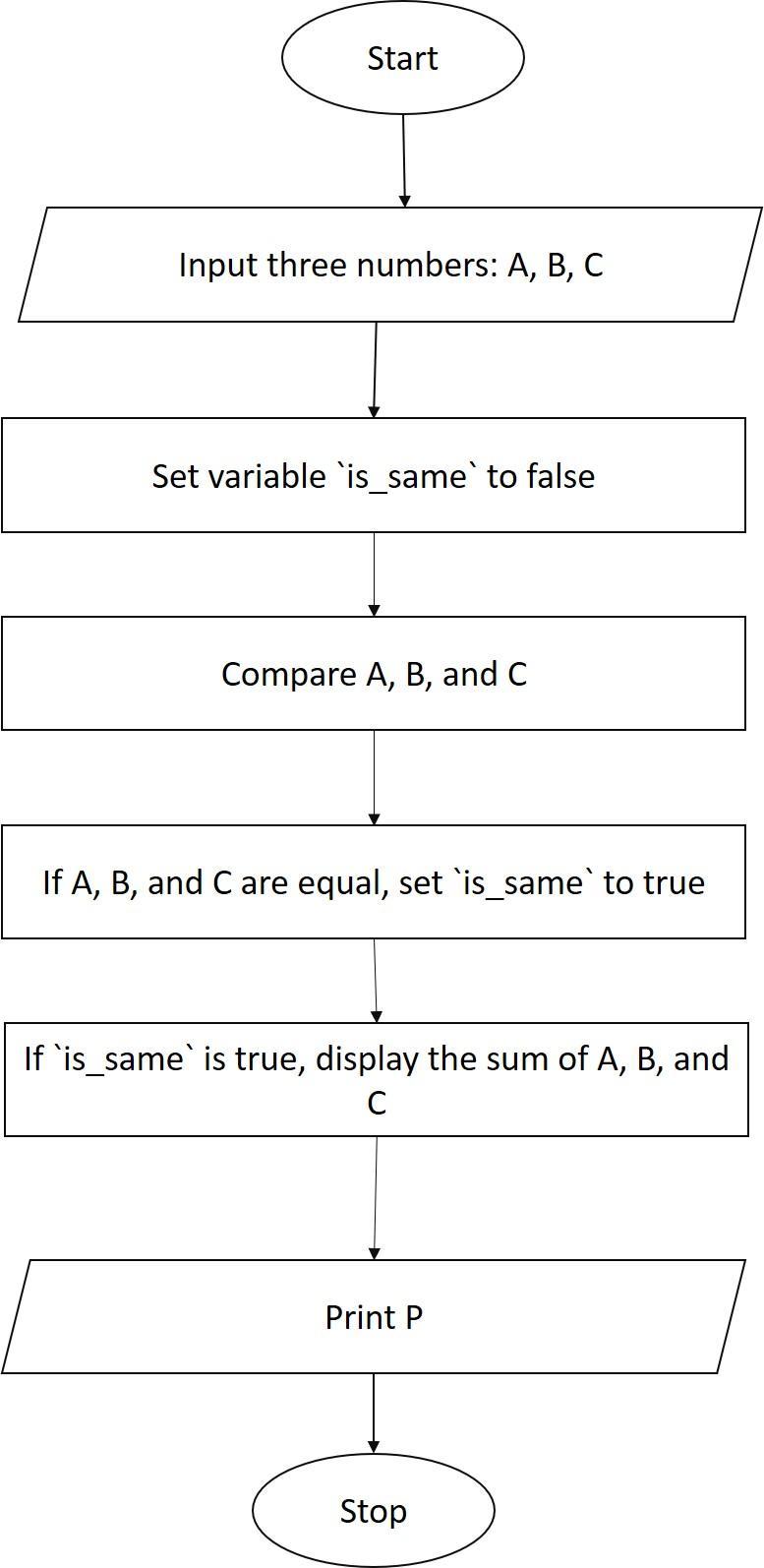
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
NEED THIS ASAP!!) What makes open source software different from closed source software? A It is made specifically for the Linux operating system. B It allows users to view the underlying code. C It is always developed by teams of professional programmers. D It is programmed directly in 1s and 0s instead of using a programming language.
Answers
Answer: B
Explanation: Open Source software is "open" by nature, meaning collaborative. Developers share code, knowledge, and related insight in order to for others to use it and innovate together over time. It is differentiated from commercial software, which is not "open" or generally free to use.