15-2 Longest palindrome subsequence A palindrome is a nonempty string over some alphabet that reads the same forward and backward. Examples of palindromes are all strings of length 1, civic, racecar, and aibohphobia (fear of palindromes). Give an efficient algorithm to find the longest palindrome that is a subsequence of a given input string. For example, given the input character, your algorithm should return carac. What is the running time of your algorithm
Answers
A subsequence of a string is the sequence of characters that can be obtained from the string by deleting some characters without changing the order of the remaining characters. A palindrome is a string that reads the same way forward and backward.
A subsequence of a string is a palindrome if it reads the same way forward and backward as well. A brute-force algorithm for finding the longest palindrome subsequence of a string of length n would be to generate all 2n subsequences of the string and check each one for whether it is a palindrome. The running time of this algorithm is O(2n) since there are 2n subsequences and checking each subsequence for whether it is a palindrome takes O(n) time.
There is a more efficient algorithm for finding the longest palindrome subsequence of a string that runs in O(n2) time. This algorithm is based on dynamic programming. We define the length of the longest palindrome subsequence of a string S[i..j] to be P(i,j). The base case is P(i,i) = 1 since a string of length 1 is a palindrome.
To know more about palindrome visit:
https://brainly.com/question/13556227
#SPJ11
Related Questions
Adjust the code you wrote for the last problem to allow for sponsored olympic events. Add an amount of prize money for Olympians who won an event as a sponsored athlete.
The Get_Winnings(m, s) function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Sample Run 1
Enter Gold Medals Won: 1
For how many dollars was your event sponsored?: 5000
Your prize money is: 80000
Sample Run 2
Enter Gold Medals Won: 2
For how many dollars was your event sponsored?: 25000
Your prize money is: 175000
Sample Run 3
Enter Gold Medals Won: 3
For how many dollars was your event sponsored?: 15000
Your prize money is: 240000
Sample Run 4
Enter Gold Medals Won: 4
For how many dollars was your event sponsored?: 1
Your prize money is: 300001
Answers
Here's the adjusted code that takes into account sponsored Olympic events and prize money for Olympians who won an event as a sponsored athlete:
The Program
d. ef G e t _ W i n ni n gs(m, s):
if n o t m . i s d i gi t ( ) o r in t ( m) < 0:
return "Invalid"
else:
nu m _ m e d a l s = i n t ( m )
prize_money = 80 00 0 *n u m _ m e dals
if n u m _ m e da l s > 1:
prize_money += 40 0 0 0 * ( n um _ medals-1)
prize_money += s
return prize_money
medals = input("Enter Gold Medals Won: ")
sponsored_amount = int(input("For how many dollars was your event sponsored?: "))
print("Your prize money is:", Get_Winnings(medals, sponsored_amount))
In this adjusted code, the Get_Winnings function takes two parameters: m for the number of gold medals won, and s for the number of dollars sponsored for the event. The prize money is calculated based on the number of medals won and the sponsored amount, using the same formula as in the previous problem.
To include the sponsored amount, the prize_money variable is increased by s. This assumes that the sponsored amount is added to the total prize money won by the athlete, rather than being a separate prize.
The main code block prompts the user for the number of gold medals won and the sponsored amount and then calls the Get_Winnings function with those values. The resulting prize money is printed on the console.
Note that in the sample runs, the prize money seems to be calculated based on the number of gold medals won, rather than the total number of medals won. If that is not the desired behavior, the prize money calculation can be adjusted accordingly.
Read more about programs here:
https://brainly.com/question/26134656
#SPJ1
When checking for a no-start concern, you notice that an engine has no spark. Technician A says to turn on the ignition (engine off) and, using a DMM, find out how much battery voltage is available at the negative terminal of the ignition coil. Technician B says the DMM reading should fluctuate, indicating that the primary coil current is being turned on and off. Who is correct?
A. Neither Technician A nor B
B. Both Technicians A and B
C. Technician B
D. Technician A
Answers
Answer:
Option(C) is the correct answer to the given question.
Explanation:
Since overall the On-Board Diagnostics of the level 2 the computer systems need to evaluate the cause of the engine failures .The malfunction significantly increases in the fuel consumption, so that we can detecting the error code in the vehicle.
If we starting the engine as well as by using the DMM, we'll see how much battery voltage it is at the negative ignition coil node.If the spark module is faulty and no ignition coils can fire so all the engines are working that's why all the other option are incorrect .Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
All the following statements are true EXCEPT: A) Both SUMIF and SUMIFS Functions consider the conditions first. B) SUMIFS allows SUMRANGE first whereas SUMIF allows sum range last. C) SUMIFS considers conditions last whereas SUMIF considers conditions first D) SUMIFS allows multiple conditions a. A b. B c. C d. D
Answers
All the following statements are true EXCEPT for the statement "Both SUMIF and SUMIFS Functions consider the conditions first."
What is the difference between SUMIF and SUMIFS functions?
SUMIF and SUMIFS are two different functions that are used in Excel. Both functions are used to add up the values in a range of cells that meet specific conditions. But, there is a difference between these two functions. The primary difference is that SUMIF only allows one condition to be checked. While SUMIFS allows multiple conditions to be checked.
For example: SUMIF: =SUMIF(A1:A5, "Apples", B1:B5) - This formula will only sum the values in column B if the corresponding cell in column A is "Apples".SUMIFS: =SUMIFS(B1:B5, A1:A5, "Apples", C1:C5, ">0") - This formula will sum the values in column B if the corresponding cell in column A is "Apples" AND the corresponding cell in column C is greater than 0.
Another difference is that in SUMIFS, the sum_range comes first, while in SUMIF, it comes last. In other words, SUMIFS allows sum_range first, whereas SUMIF allows sum_range last.
All the other options that are mentioned in the question are true. Option A) Both SUMIF and SUMIFS Functions consider the conditions first. Option C) SUMIFS considers conditions last whereas SUMIF considers conditions first Option D) SUMIFS allows multiple conditions to be true.
To learn about the SUMIF function here:
https://brainly.com/question/29848364
#SPJ11
Hay give me some funny but good zombie movies and I will give 100 points
Ps I will have to do it on private thing so ya y’all get Brainly and 100 points
Answers
Explanation:
okay, you said funny but I wodner if this is funny.
and said some, I dont think I've watched much
Train to busan?
how about Transylvania? lol
I'm sorry but cant think of anything from those I've watched. T~T
enter a valid email address to use as your apple id
Answers
When creating your Apple ID, it's important to use a valid email address that you have access to.
This is necessary to verify your account and receive important updates about your Apple products and services. You should also use a reliable email address that you won't lose access to, as losing access to your email could result in being locked out of your Apple devices or losing important data. To ensure a valid and reliable email address, use an email address that you regularly use and consider setting up two-factor authentication on your account for added security.
To know more about email address visit:
brainly.com/question/8771496
#SPJ11
Help please! i don’t know how to do this.
H2 should be:
-Blue
-Times New Roman or Arial
-Align to the right
2. Strong should be:
-Teal
-32pt
-Boldness of 700
3. P should be:
-All in uppercase
-Overlined
-Word space of 10em

Answers
Answer:
Make sure to create and link a css file with the following:
<link rel="stylesheet" href="./styles.css">
In your css file, enter these styles:
h2 {
color: blue;
font-family: 'Times New Roman', Times, serif;
text-align: right;
}
strong {
color: teal;
font-size: 32pt;
font-weight: 700;
}
p {
text-transform: uppercase;
text-decoration: overline;
word-spacing: 10em;
}
Explanation:
In order for the html file to know where your styles are located, you have to link it to the css file with the code given above. In this file, you will enter some css to change the styles of the elements you have created in your html file.
To alter the style of an element, you first have to enter the name of the element itself, its class or its id. In this case, we have used the element itself, meaning that all the same elements in the html file will have the same style. The styles you wish to use are entered in between the curly brackets.
In your specific problem, we are trying to change the h2, strong and p elements, so that is what we have done. For the h2, you wanted it blue, therefore we use the color property to change the color. For the font, we use the font-family and finally we use text-align to align it to the right. The same pretty much applies for the other two elements. Your strong element needs to be teal,32pt and 700 bold. Therefore we use the color, font-size and font-weight properties respectively. And finally for the p element, we will use the text-transform, text-decoration and word-spacing properties respectively.
When you dont know the name of the property you want to change, I suggest googling it. You will definitely find the property name you are looking for. W3schools.com is a good source to use.
Ballet was originally created for the wedding celebration of Louis XVI and Marie Antoinette. (True or False)
Answers
Answer:
true
Explanation:
8 grades, help please!!!!

Answers
Answer: can you take a clearer picture its really blurry then I can help Thx! :)
Explanation:
5. Computer files A,B and C occupies 31240 kb,1267000 bytes and 1.317 GB of memory respectively. Calculate in megabytes, the amount of storage space left after moving all the three files into a 2gb capacity storage device.
Answers
The amount of storage space left in megabytes after moving all three files into a 2GB capacity storage device is 697.83 MB.
Given information: Size of file A = 31240 KB Size of file B = 1267000 bytesSize of file C = 1.317 GBIn order to calculate the total size of all three files, we need to convert the units to a common unit such as bytes or kilobytes. Let's convert all units to bytes: Size of file A = 31240 KB = 31240 x 1024 bytes = 320,71680 bytesSize of file B = 1267000 bytesSize of file C = 1.317 GB = 1.317 x 1024 x 1024 x 1024 bytes = 1,413,408,512 bytesTotal size of all three files = 320,71680 bytes + 1267000 bytes + 1,413,408,512 bytes= 1,416,020,192 bytesTo calculate the remaining space left on a 2GB storage device, we need to convert 2GB to bytes:2GB = 2 x 1024 x 1024 x 1024 bytes = 2,147,483,648 bytes
Therefore, the remaining space left after moving all three files into a 2GB capacity storage device is:2,147,483,648 bytes - 1,416,020,192 bytes = 731,463,456 bytesTo convert bytes to megabytes, we divide by 1024 x 1024 bytes per megabyte:731,463,456 bytes / (1024 x 1024 bytes/MB) = 697.83 MB (rounded to two decimal places)Therefore, the amount of storage space left in megabytes after moving all three files into a 2GB capacity storage device is 697.83 MB.
Learn more about kilobytes :
https://brainly.com/question/24397941
#SPJ11
write the home cell of MS Excel.
Answers
Answer:
MS Excel
Explanation:
program that shows if it's an integer or not
Answers
you are not sure if a certain word has an"e"at the end
Answers
how do I fix this? It stopped adding up my points when i did one of the challenges.

Answers
Answer:
Maybe try resetting if that doesn't work ask one of the devs but if you do that you might need proof of the points that you earned.
Taylor, Catherine, and Naomi all made
inventions that improved people's
. They all protected.
their inventions by getting a

Answers
Taylor, Catherine, and Naomie all invented things that helped people's health.They all protected their inventions by getting a solution.
What do you mean by an invention?
A unique or novel device, method, composition, idea, or process is defined as an invention. An invention can be an enhancement to a machine, product, or process that increases efficiency or reduces costs. It is possible to patent an idea if it is distinct enough, either as a stand-alone invention or as a significant improvement over the work of others. If granted, a patent grants the inventor a proprietary interest in the patent for a set period of time, which can be licenced for monetary gain.
To learn more about invention
https://brainly.com/question/17931211
#SPJ13
A well-known production is making a documentary film titled “The Dwindling Population of Grizzly Bears in the United States.” Which objective is most likely the primary objective for making the film? A. getting recognition B. telling a story C. spreading awareness D. earning profits
Answers
Answer:
C. spreading awareness
Explanation:
According to the given question, the most likely primary objective of a well-known production company making a documentary film titled “The Dwindling Population of Grizzly Bears in the United States" is to generate and spread awareness of the possible extinction of the grizzly bears in America.
With their production, they would expose the dangers facing the grizzly bears and also educate the general public so they could save the grizzly bears.
which of the hash table collision-handling schemes could tolerate a load factor above 1 and which could not?
Answers
The hash table collision-handling schemes could tolerate a load factor above 1 and which could not is option A: Hash Tables need to deal with collisions. Which of the hash table collision- handling schemes could tolerate a load factor above 1 and which could not a. Hint: Think about which of the schemes use the array supporting the hash table exclusively and which of the schemes use additional storage external to the hash table
What purposes serve hash tables?A hash table is a type of data structure that allows for constant-time direct access to its components while storing data in key-value format. Associative hash tables are those where each key only appears once in the data, thus the name.
Therefore, one can say that It is a type of abstract data that associates values with keys. An array of buckets or slots are used in a hash table to provide an index, also known as a hash code, from which the requested data can be retrieved. The key is hashed during lookup, and the resulting hash shows where the relevant value is kept.
Learn more about hash table from
https://brainly.com/question/29510384
#SPJ1
See full question below
Hash Tables need to deal with collisions. Which of the hash table collision- handling schemes could tolerate a load factor above 1 and which could not? a. Hint: Think about which of the schemes use the array supporting the hash table exclusively and which of the schemes use additional storage external to the hash table. b. Assume you want to hash the keys 12, 44, 13, 88, 23, 94, 11, 39, 20, 16, 5 and store them in a hash table. Implement linear probing, and double hashing to handle collision. Print out the positions of keys stored. Hash functions for linear probing and double hashing as described as follows. Linear probing: h(k) (3k+5) mod 11 Double hashing: hi(k) (3k+5) mod 11, h2(k)-7 (k mod 7)

help teacher said with complete explanation

Answers
Answer:
use the first graph to help you find out
7.2 code practice edhesive. I need help!!
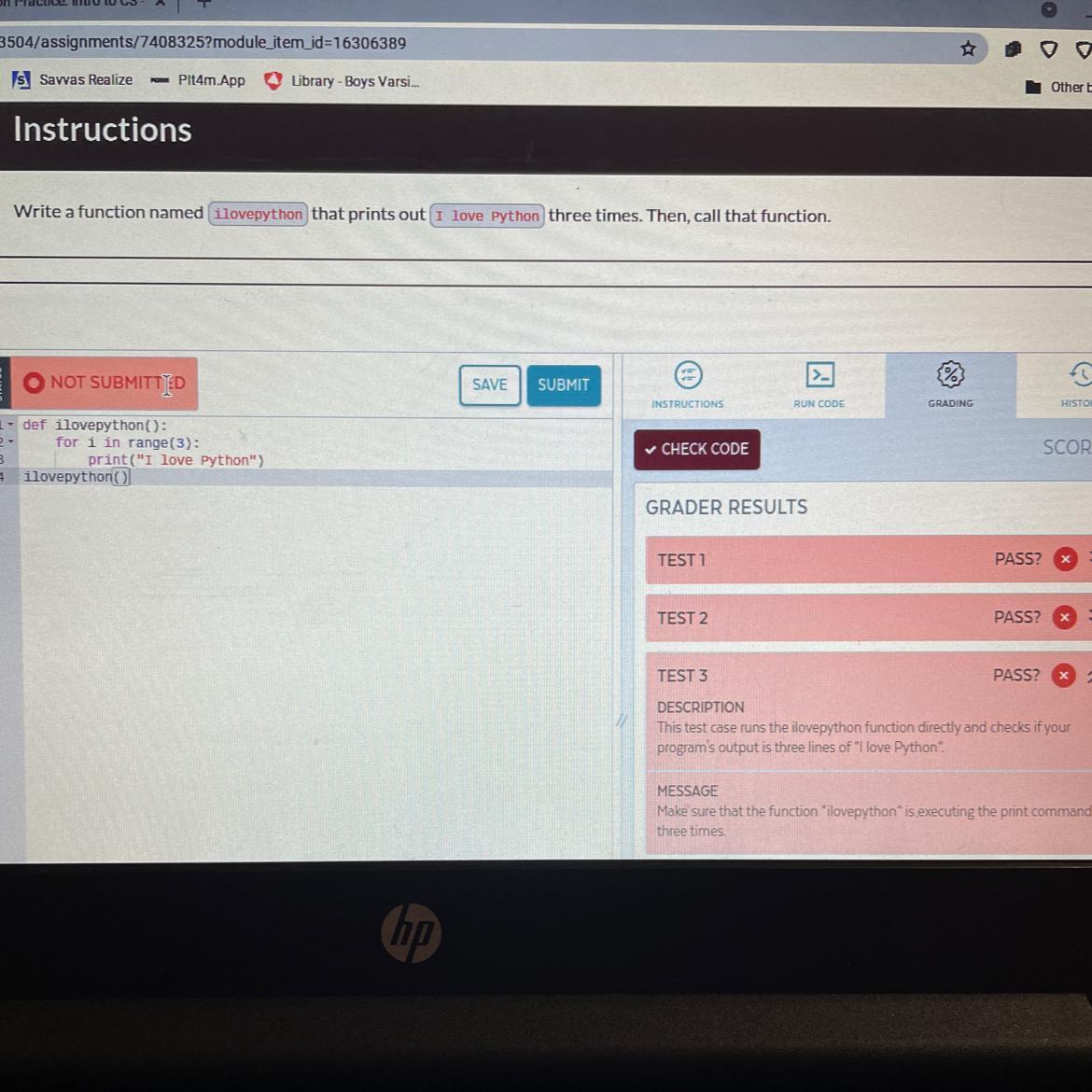
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
Download the Excel spreadsheet Fructus_data.xls from Blackboard.
This file contains production statistics between 2000-2020 for the
country "Fructus," which only produces Apples, Bananas and
Cherr
Answers
The Excel spreadsheet "Fructus_data.xls" from Blackboard provides production statistics for the country "Fructus" from 2000 to 2020.
The data includes information on the production of Apples, Bananas, and Cherries. Analyzing the data in the spreadsheet can provide valuable insights into the production trends of these fruits in Fructus over the past two decades. The spreadsheet likely contains information such as the yearly production quantities, growth rates, and market shares of each fruit. By examining this data, one can identify patterns, seasonal variations, and any notable changes in production levels. This analysis can be beneficial for understanding the country's agricultural sector, making informed business decisions, and developing strategies for future fruit production in Fructus.
Learn more about Excel spreadsheet here:
https://brainly.com/question/30450507
#SPJ11
Which one of the following CPU registers holds the address of the instructions (instructions in the program stored in memory) to be executed next?
A.MBR (Memory Buffer Register)
B.ALU (Arithmetic Logic Unit)
C.IR (Instruction Register)
D.PC (Program Counter)
Answers
Program counter: A programme counter is used to monitor how a programme is being run. It has the memory location of the following instruction that needs to be fetched.
Which of the following registers houses an instruction's address?Program counter is the proper response. Program Counter: The location of the following instruction to be executed from memory is stored in a CPU register called a programme counter (PC) in the computer processor.
Which of the following registers is used to store the address of the memory where the von Nuumann model instruction is available?Memory Data Register (MDR): The MDR is used to hold information that needs to be transmitted to and stored in memory as well as instructions that are fetched from memory.
To know more about programme visit:-
https://brainly.com/question/30307771
#SPJ4
Drag the system component on the left to the device or program that fits with the system component.
Answers
Answer:
A. Back up software - Utility software
B. Printer - Device drivers
C. Camera - Firmware
D. Television - Firmware
E. Games console - Firmware
F. Antivirus software - Utility software
G. Disk Cleaner - Utility software
H. Video Card - Device drivers
Explanation:
Computer system components are the physical or hardware and software parts of the device. It is a combination of system software like utility software, device drivers and firmware, application software, and the hardware components and kernel.
You learned that "The CPU interacts with memory in a process that is known as
the fetch-decode-execute cycle. An instruction gets fetched (brought up) from
memory, decoded (analyzed) in the control unit, and then executed (put into
action) by the ALU." Can you think of a comparison to something that happens in
real life that would make this process easier to understand and remember?
Answers
Answer:
okay this is going to be weird but hopefully it helps you go to a restaurant you use the menu to place an order the waiter analyzes the order and then it brings it to you
Explanation:
so in other words the menu is bringing up what you want
the waiter is the person who analyzes the order
and then to put it to action is when you receive the order and eat it.
I know this is a weird analogy but I hope it helps
Write a paragraph of 7-10 sentence explaining how a user can navigate throughout ms excel
Answers
The paragraph of 7-10 sentence explaining how a user can navigate throughout MS excel is:
In an an spreadsheet, click on View > Navigation. The Navigation view will open on the right side of the window. The Navigation view can also be opened from the status bar under the screen.
How do you navigate in Excel?To move about in between the key areas or places in Excel for the web, the key to press is Ctrl+F6 (forward) and also Ctrl+Shift+F6 (backward).
Therefore, The paragraph of 7-10 sentence explaining how a user can navigate throughout MS excel is: In an an spreadsheet, click on View > Navigation. The Navigation view will open on the right side of the window. The Navigation view can also be opened from the status bar under the screen.
Learn more about MS excel from
https://brainly.com/question/25879801
#SPJ1
Plant Roots are strong enough to break rock.
False
True
Answers
Answer:
True
Explanation:
Plants and animals can be agents of mechanical weathering. The seed of a tree may sprout in soil that has collected in a cracked rock. As the roots grow, they widen the cracks, eventually breaking the rock into pieces.
Write about the history of computer.
Answers
Answer:
Charles Babbage, an English mechanical engineer and polymath, originated the concept of a programmable computer. Considered the "father of the computer", he conceptualized and invented the first mechanical computer in the early 19th century. ... The machine was about a century ahead of its time.
Explanation:
Hope it is helpful...
What will the following code display? int x = 0; for (int count = 0; count < 3; count ) x = count; cout << x << endl;
Answers
The code will display the value of "x" as 2.The given code will display the value of the variable "x" as 2.
Let's break down the code step by step:
1. Initialize the variable "x" with a value of 0: int x = 0;
2. Start a for loop with the variable "count" initialized as 0: for (int count = 0; count < 3; count )
3. Check if "count" is less than 3. If it is, execute the loop body; otherwise, exit the loop.
4. Inside the loop, assign the value of "count" to "x": x = count;
5. Increment the value of "count" by 1: count++
6. Repeat steps 3-5 until "count" is no longer less than 3.
7. After the loop ends, the value of "x" will be the last assigned value of "count" which is 2.
8. Print the value of "x" followed by an endline: cout << x << endl;
Therefore, the code will display the value of "x" as 2.
To know more about variable, visit:
https://brainly.com/question/15078630
#SPJ11
in a von neumann-architecture computer, the program counter:
Answers
In a Von Neumann architecture computer, the program counter is a crucial component that stores the address of the next instruction to be fetched and executed.
The program counter (PC) is a register in the central processing unit (CPU) of a Von Neumann architecture computer. Its main function is to keep track of the address of the next instruction to be fetched and executed from the memory. The PC is incremented after each instruction is executed, allowing the CPU to fetch the subsequent instruction from the memory. It plays a vital role in the sequential execution of instructions in a program.
When the CPU starts executing a program, the PC is initially set to the address of the first instruction. As the instructions are fetched and executed one by one, the PC is updated to point to the next instruction's address. This process continues until the program completes or encounters a branch or jump instruction that modifies the PC value. In such cases, the PC is redirected to a different address, enabling control flow within the program.
Overall, the program counter is a fundamental component in a Von Neumann architecture computer, enabling the sequential execution of instructions and facilitating the control flow of a program.
learn more about Von Neumann architecture here:
https://brainly.com/question/30898544
#SPJ11
Captions are used to identify or give information about
O books
O magazines
O authors
O images
Answers
Answer:
images
Explanation: i know this because i read magazines all the time specially rollingstone
Plz help:(!!!!
Type the correct answer in the box. Spell all words correctly.
Claire wants to use a filter to ensure quality in the software development process and product. What can Claire use for this purpose?
Claire should use_________
as a filter to ensure quality in the software development process and product.
Answers
Answer:
Defect filters
Explanation:
Answer:
"a quality gate" is the correct answer :D
Explanation: